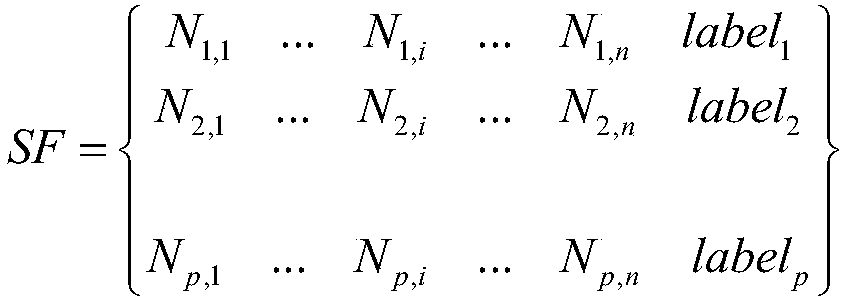Efficient detection method for massive malicious codes
A detection method and malicious code technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems affecting analysis efficiency, low efficiency of serial processing process, difficulty in making quick response, etc., to achieve improvement Efficiency, guarantee the effect of timely security protection of the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be described in detail below with reference to the accompanying drawings and examples.
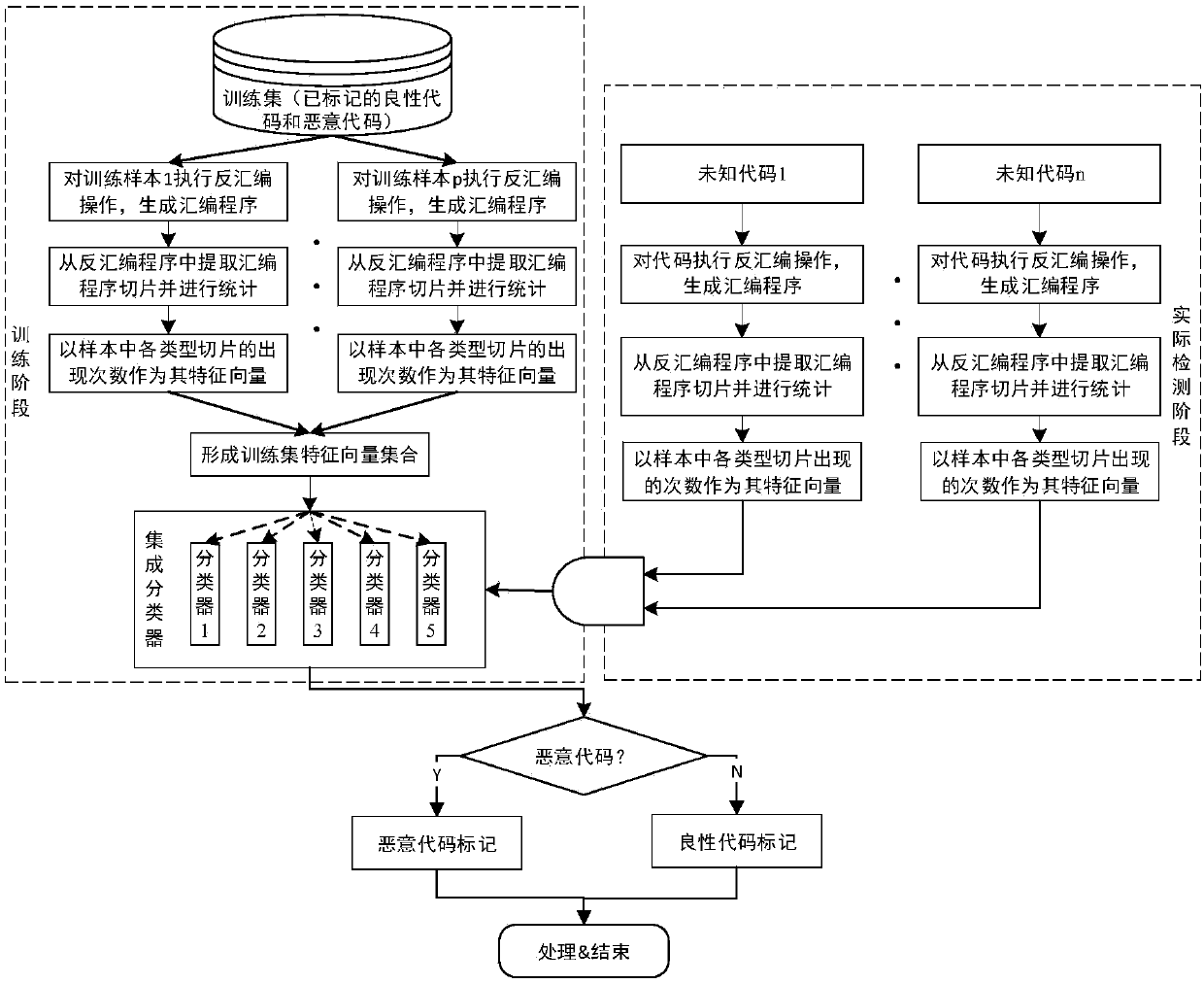
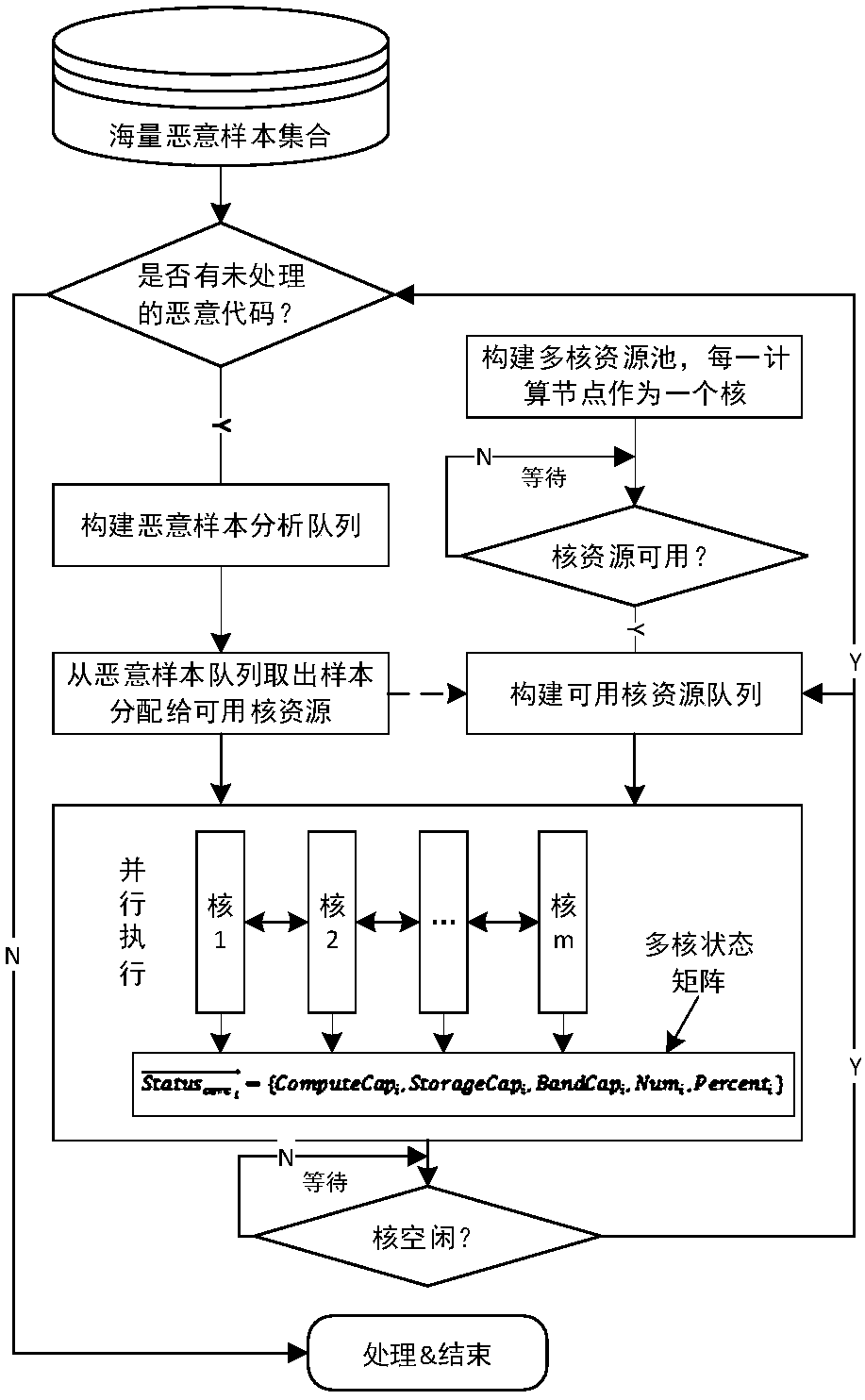
[0060] An embodiment of the present invention provides a method for efficiently detecting massive malicious codes. The detection method of the method detects malicious codes for assembler samples. The method uses multi-core computing resources to perform the assembler sample identification steps in parallel. The assembler sample identification steps are as follows: figure 1 As shown, specifically:
[0061] S1. Extracting an assembler slice, where the assembler slice is a statement or an expression that affects a specified variable in the assembler sample.
[0062] In the embodiment of the present invention, the specified variable may be a variable specified by the user, or may directly use a variable that affects the performance of the assembly program running subject. Specifically, through Fenix (analysis), the statements that can affect the performanc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com