Method and system for querying ciphertext database based on vertical division
A query method and technology of a query system, applied in database query, based on the field of vertically divided ciphertext database query, can solve problems such as inability to support multi-granularity authorization strategies, and achieve the effects of convenient implementation, simple algorithm, and optimized storage method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
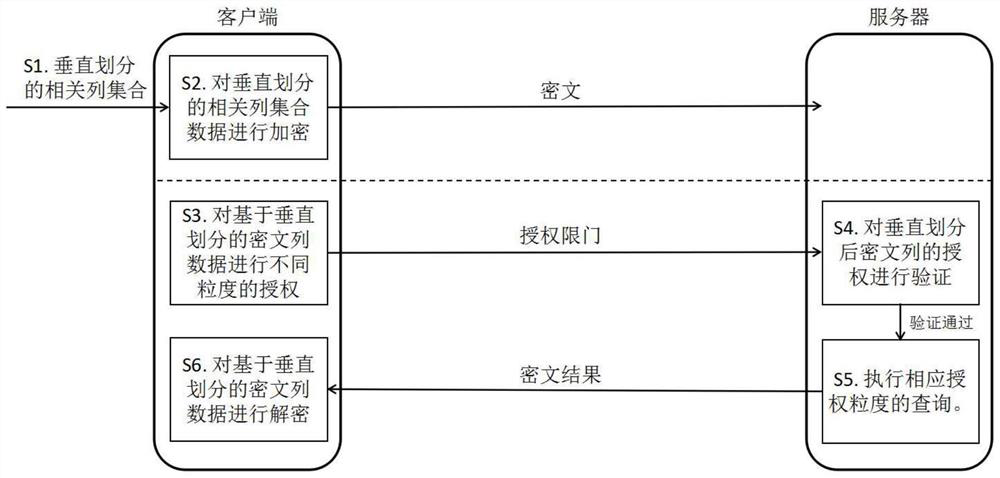
[0094] like figure 1 As shown, this embodiment provides a ciphertext database query method based on vertical division, and the method includes the following steps:
[0095] S1. For each table in the database, perform vertical division according to the structure and characteristics of the column data and the characteristics of the data application obtained from the statistical user query to obtain a vertically divided set of related columns.
[0096] S2, encrypting the vertically divided related column set data to obtain ciphertext column data based on the vertical division;
[0097] S3. Authorize the ciphertext column data based on vertical division with different granularities;
[0098] S4, verifying the authorization of the ciphertext column data based on the vertical division;
[0099] S5, query the corresponding authorization granularity for the ciphertext column data based on vertical division that has passed the verification;
[0100] S6. Decrypt the ciphertext column...
Embodiment 2
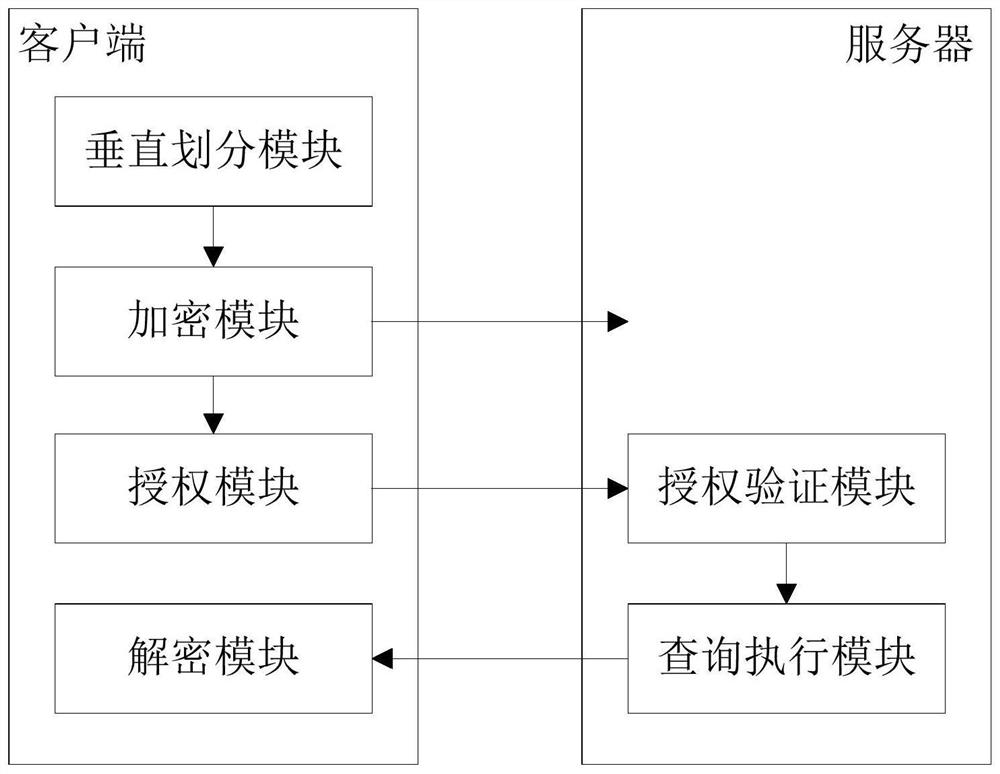
[0150] like figure 2 As shown, this embodiment provides a ciphertext database query system based on vertical division, the system corresponds to the method of Embodiment 1, and mainly includes a vertical division module, an encryption module, an authorization module, an authorization verification module, a query execution module and The decryption module, wherein the vertical division module, the encryption module, the authorization module and the decryption module are deployed on the client side, that is, the vertical division module, the encryption module, the authorization module and the decryption module are used as the functional modules of the first processor, the authorization verification module and the query execution module Deployed on the server, that is, the authorization verification module and the query execution module are the functional modules of the second processor.
[0151] The specific functions of each module are as follows:
[0152] A. The vertical div...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com