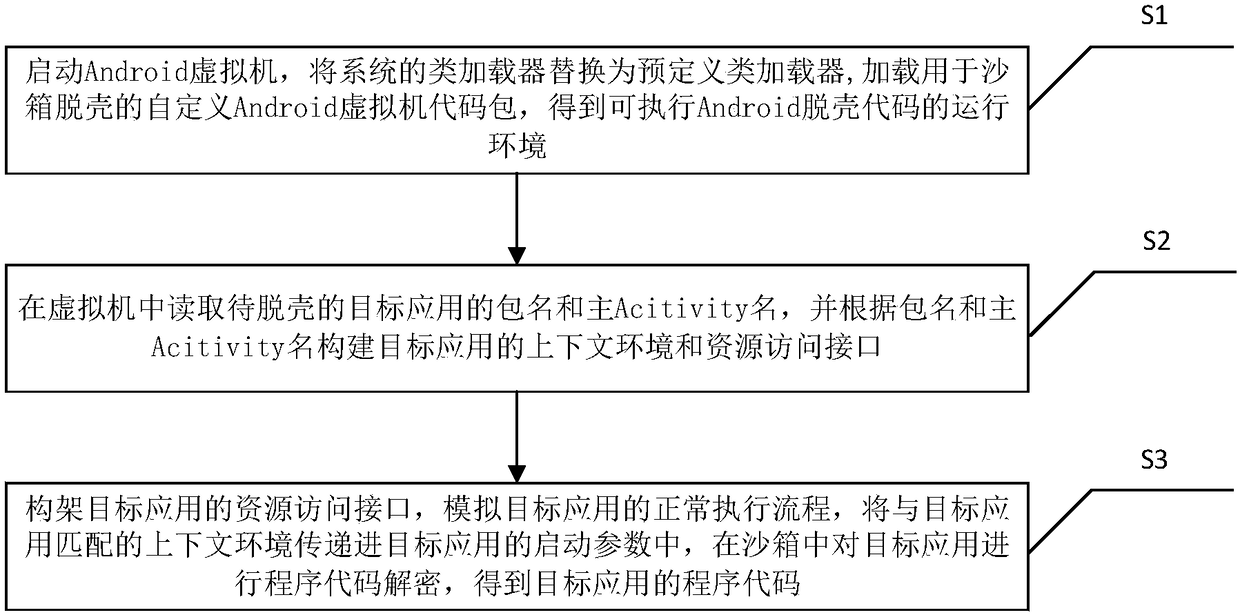
Sandbox shelling method and system based on Android virtual machine
A virtual machine and sandbox technology, applied in the field of information security, can solve problems such as system crashes, security risks, mobile phone sensitive information theft, etc., and achieve the effect of simple use, high efficiency, and ensuring the security of the equipment environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
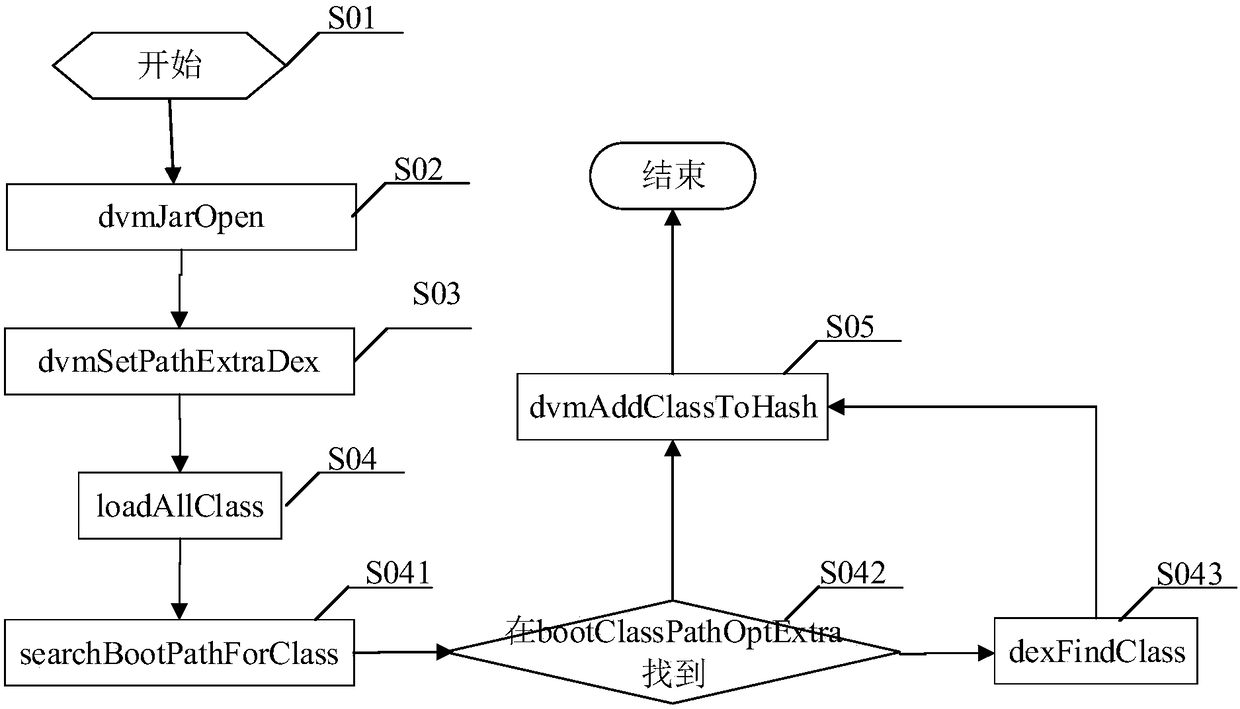
[0097] combine image 3 As shown, the present invention provides a function of modifying the framework code of the Android system based on the principles of the Android system. The functional steps are as follows:
[0098] S01, start the Android virtual machine until the system framework code is loaded.
[0099] S02, use the system dvmJarOpen to load the custom Android virtual machine code package of the present invention to obtain a DexFile object.
[0100] S03, calling dvmSetBootPathExtraDex to store the above-mentioned DexFile object in bootClassPathOptExtra.
[0101] S04, call loadAllClass, search for the classes in the above-mentioned DexFile in a loop, and add them all to the hashTable for subsequent use.
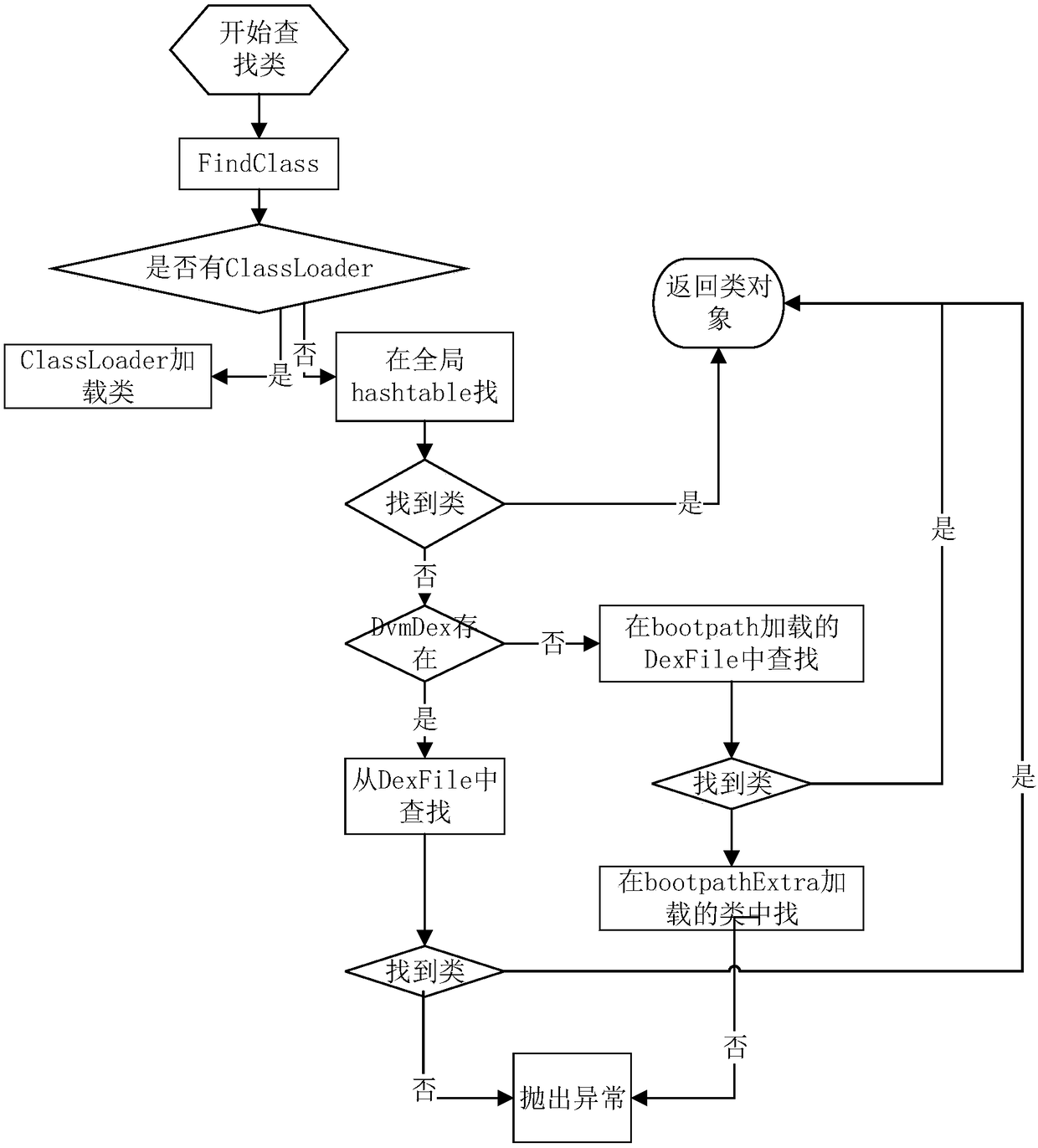
[0102] S041, classloader and DvmDex are not provided here for class search, use dvmFindSystemClassNoInit to search from bootclass.
[0103] S042, use dexFindClass to directly search from bootClassPathOptExtra, return if found, otherwise go to the next step.
[01...
specific Embodiment 2
[0106] This system refers to the operating principle of the Android system, and realizes the interface from Activity, Application to ActivityThread, etc., which can be directly called by the application. Also implemented ApplicationInfo, LoadedApk, Context and other classes related to the environment and resources. Since many system principles are involved, this embodiment only describes the reference steps.
[0107] S01, the control module starts the dalvik virtual machine.
[0108] S02, the control module uses the function of Embodiment 1 to load the system framework jar package.
[0109] S03, pass in the app path of the target application, analyze and obtain the Application name and the main Activity name.
[0110] S04, use the Jni interface FindClass to find the target Application class, and call The initialization function calls NewObject to generate an object.
[0111] S05, use the Jni interface FindClass to find the ActivityThread, and the ActivityThread is the Ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com