Confidentiality input equipment for financial industry
An input device and industry technology, applied in the input/output of user/computer interaction, the input/output process of data processing, the protection of internal/peripheral computer components, etc., can solve problems such as hardware encryption, and achieve the effect of meeting input requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
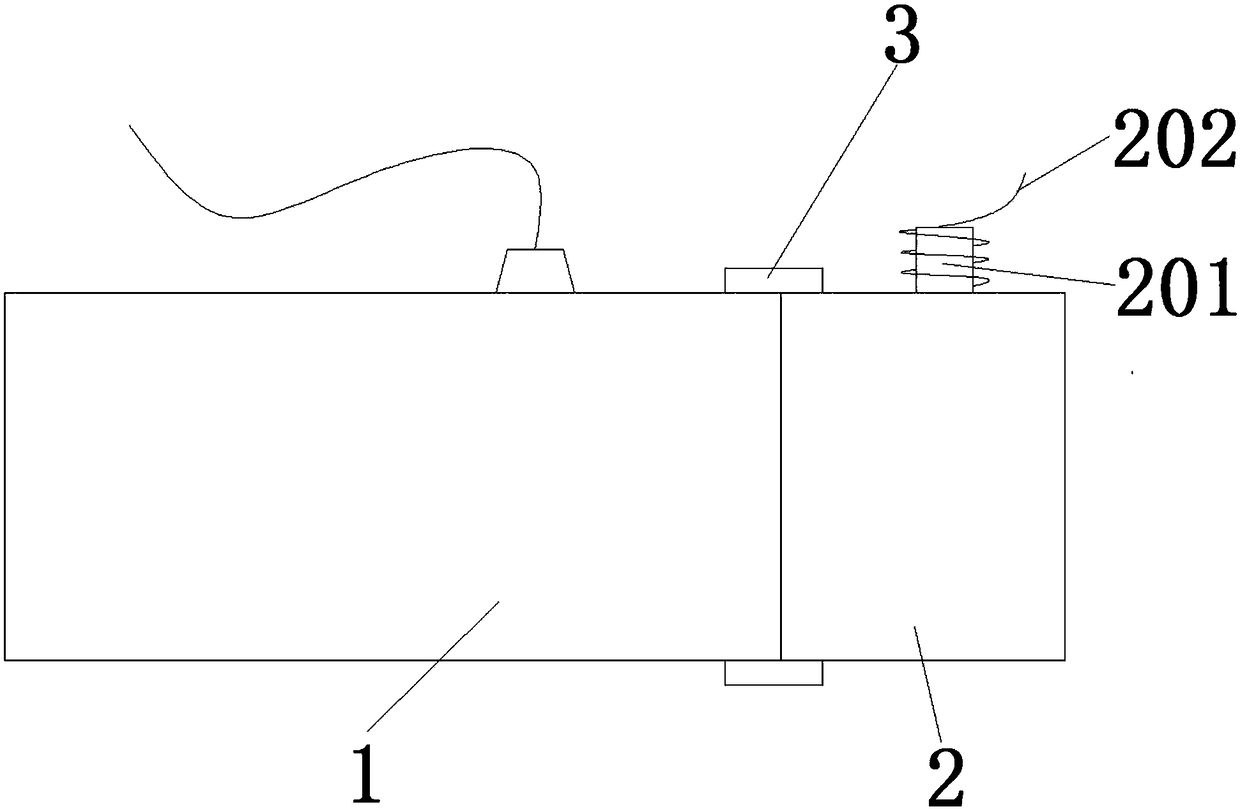
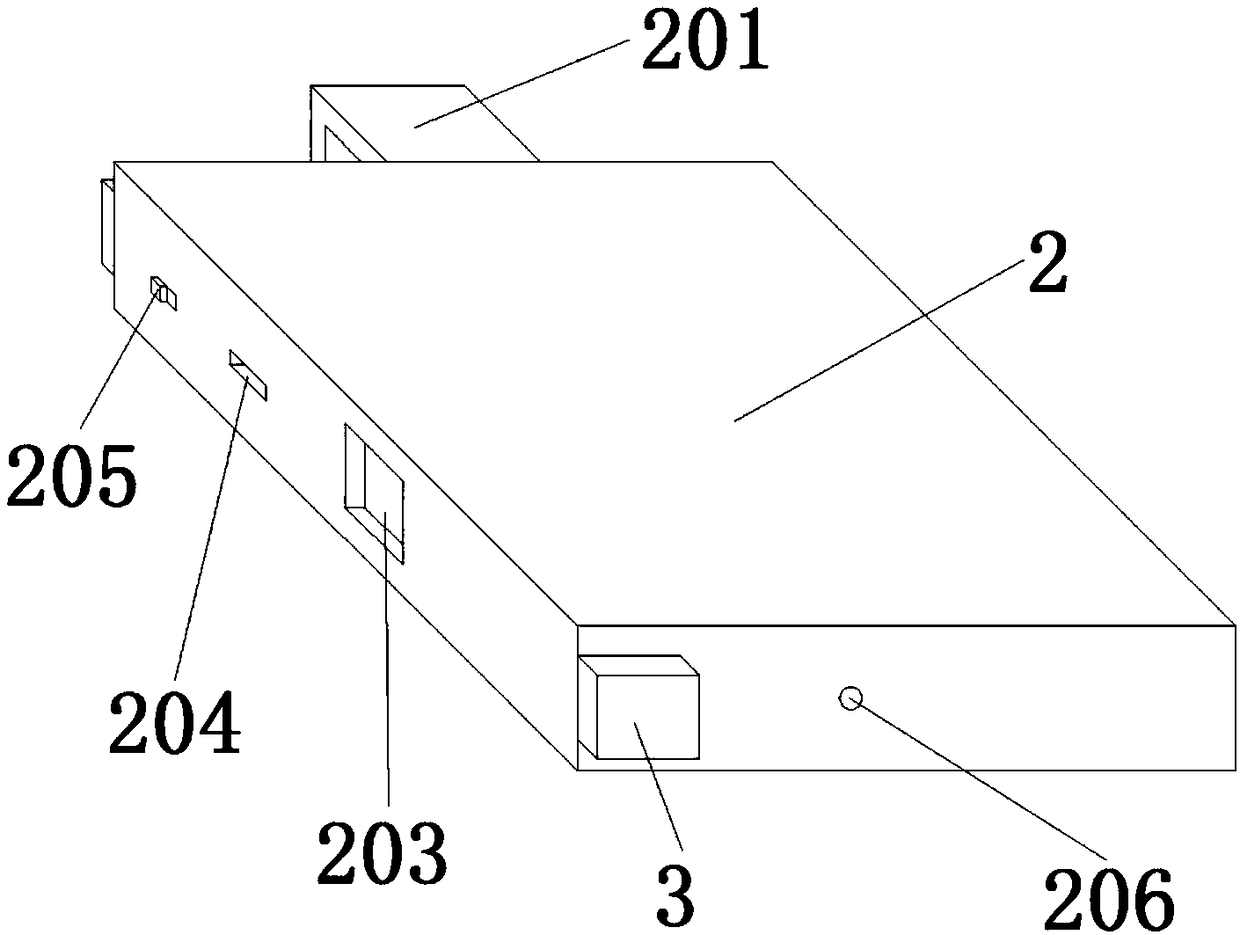
[0022] Such as figure 1 , 2 As shown, the security input device used in the financial industry of the present invention includes a keyboard body 1 of Filco 87 keys, and also includes a small keyboard 2 connected to the left side of the keyboard body 1 through a buckle assembly 3, and the small keyboard 2 is connected to the keyboard body 1. A communication interface 203 and a TF card chip interface 204 are provided on the connection side, and the small keyboard 2 communicates with the keyboard body 1 through the communication interface 203. The keyboard body 1 and the keypad 2 are connected together through the detachable buckle assembly 3. When data needs to be input to the encryption system, the buckle assembly 3 is first opened, and the decryption chip corresponding to the system is inserted into the chip interface 204, and then the The combination of the keyboard body 1 and the small keyboard 2 solves the problem that most of the existing encryptions rely on programs to c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com