Random access response method and device
A random access response and random access technology, applied in the field of communication, can solve the problem that the random access response message is no longer applicable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0279] Embodiment 1: Fixed-length MAC RAR method 1-1, UE only sends preamble code (four-step random access)
[0280]In fixed-length MAC RAR method 1-1, the MAC PDU format includes the following MAC subheader ( Figure 14a ) and MAC RAR ( Figure 14b ~ Figure 14d ).
[0281] UE side:
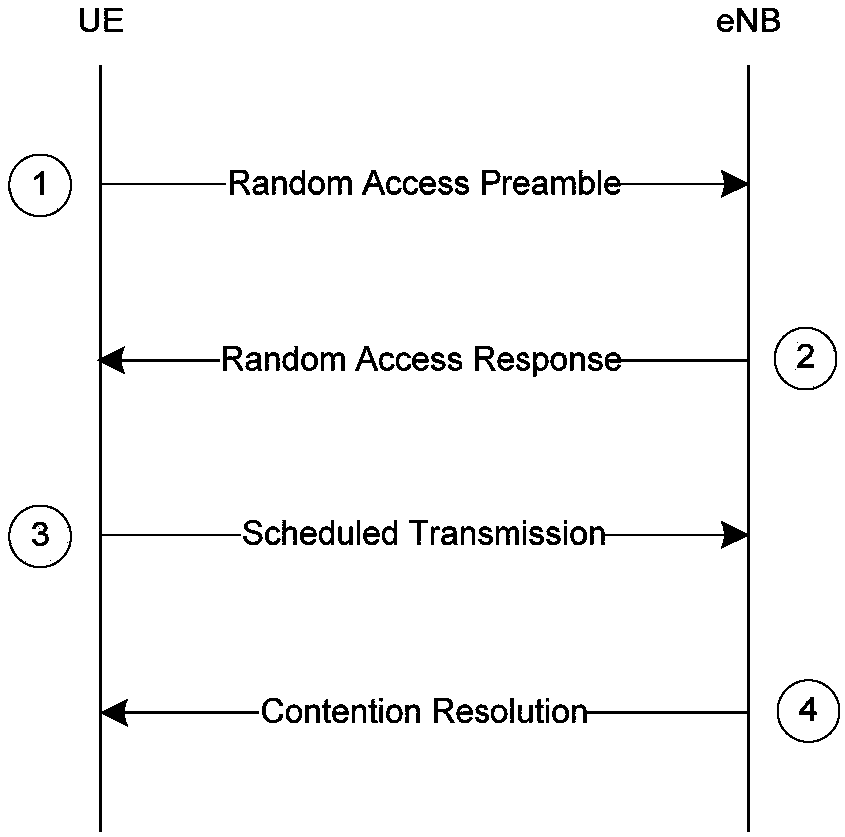
[0282] Step 1: Send random access request preamble code;
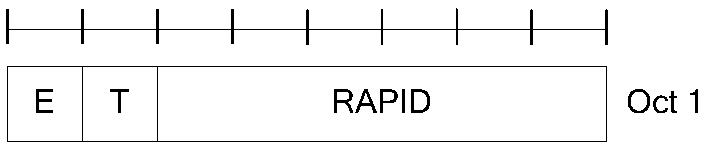
[0283] Step 2: Receive the random access response, determine the same number as the preamble code sent by yourself according to the RAPID field in the MAC subheader, and interpret the corresponding MAC RAR;
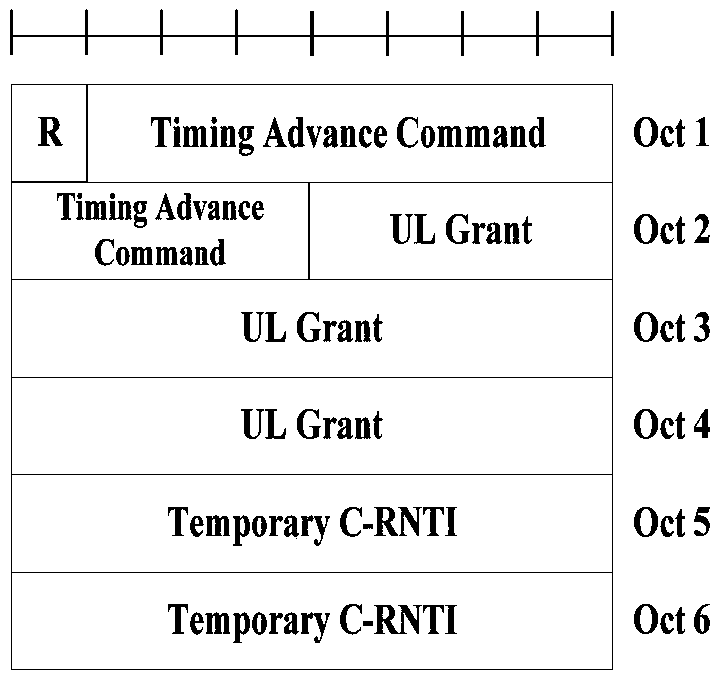
[0284] Step 3: Obtain MAC RAR(1), the format is as follows Figure 14b , if T1=0, read the follow-up fields, and perform relevant operations according to the instructions of each field, including uplink timing adjustment, sending uplink data transmission according to the UL Grant, obtaining the allocated Temporary C-RNTI, etc., and completing the follow-up random access process; if T1=1, it is determined that the random access r...
Embodiment 2
[0289] Embodiment 2: Fixed-length MAC RAR method 1-1, UE sends preamble code and UE ID (two-step random access)
[0290] The MAC PDU format is the same as that of Embodiment 1, and is still Figure 14a ~ Figure 14b .
[0291] UE side:
[0292] Step 1: Send a random access request, including the preamble code, UE ID and other uplink transmissions (such as BSR, PHR, uplink data). In the random access request, it is necessary to distinguish whether the UE sends a long UE ID or a short UE ID. You can Use different LCID fields in the MAC subheader to distinguish between long UE ID and short UE ID;
[0293] Step 2: Receive the random access response, determine the same number as the preamble code sent by yourself according to the RAPID field in the MAC subheader, and interpret the corresponding MAC RAR;
[0294] Step 3: Analyze T1, which has the following branches:
[0295] -3-1: If T1=0, get MAC RAR(1), the format is as follows Figure 14b , the UE determines that the network ...
Embodiment 3
[0310] Embodiment 3: Fixed-length MAC RAR method 1-2, UE only sends preamble code (four-step random access)
[0311] In fixed-length MAC RAR method 1-2, the MAC PDU format includes the following MAC subheader ( Figure 15a ) and MAC RAR ( Figure 15b ).
[0312] UE side:
[0313] Step 1: Send random access request preamble code;
[0314] Step 2: Receive the random access response, determine the same number as the preamble code sent by yourself according to the RAPID field in the MAC subheader, and interpret the corresponding MAC RAR;
[0315] Step 3: Get MAC RAR, the format is as follows Figure 15b , parse T1=0, read the follow-up fields, and perform relevant operations according to the instructions of each field, including uplink timing adjustment, sending uplink data transmission according to the UL Grant, obtaining the allocated Temporary C-RNTI, etc., and completing the follow-up random access process; if T1=1, it is determined that the random access response is not ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com