Method and device for preventing traffic hijacking of advertisement operator, equipment and storage medium
A traffic hijacking and operator technology, applied in the field of network security, can solve the problems of traffic advertising hijacking, achieve the effect of good traffic advertising hijacking and prevent traffic advertising hijacking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
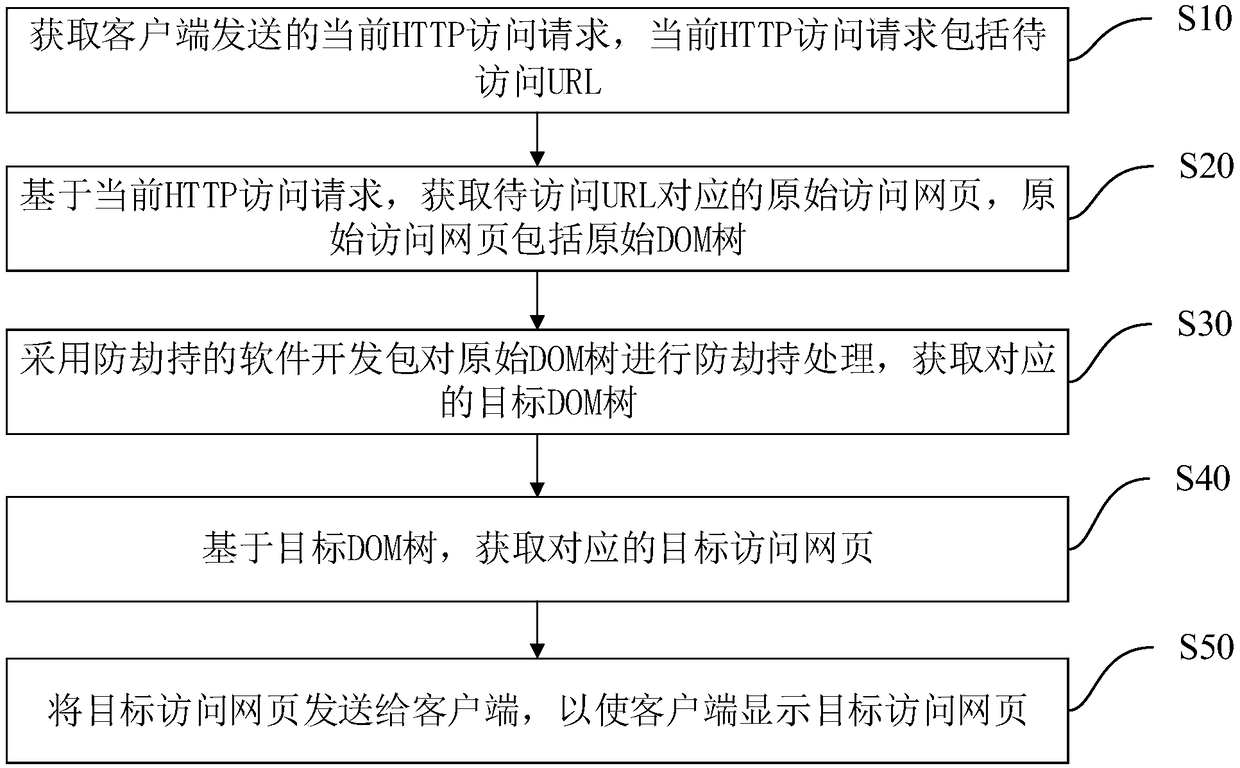
[0031] figure 1 A flow chart showing the method for preventing traffic hijacking by advertising operators in this embodiment. The method for preventing traffic hijacking by advertising operators is applied in the server, and the server and the client interact with each other through the network, which can prevent advertising operators from inserting network advertising resource information into normal webpage resource information when users visit webpages, so as to achieve The purpose of preventing traffic advertisement hijacking by advertising operators. Such as figure 1 As shown, the method for preventing traffic hijacking by advertising operators includes the following steps:
[0032] S10: Obtain the current HTTP access request sent by the client, where the current HTTP access request includes the URL to be accessed.
[0033] Wherein, the URL to be accessed refers to the address of the webpage that the user needs to visit. Specifically, the server communicating with the...
Embodiment 2
[0118]图8示出与实施例1中防止广告运营商流量劫持的方法一一对应的防止广告运营商流量劫持的装置的原理框图。如图2所示,该防止广告运营商流量劫持的装置包括访问请求获取模块10、原始访问网页获取模块20、目标DOM树获取模块30、目标访问网页获取模块40和客户端显示模块50。其中,访问请求获取模块10、原始访问网页获取模块20、目标DOM树获取模块30、目标访问网页获取模块40和客户端显示模块50的实现功能与实施例中防止广告运营商流量劫持的方法对应的步骤一一对应,为避免赘述,本实施例不一一详述。
[0119]访问请求获取模块10,用于获取客户端发送的当前HTTP访问请求,当前HTTP访问请求包括待访问URL。
[0120]原始访问网页获取模块20,用于基于当前HTTP访问请求,获取待访问URL对应的原始访问网页,原始访问网页包括原始DOM树。
[0121]目标DOM树获取模块30,用于采用防劫持的软件开发包对原始DOM树进行防劫持处理,获取对应的目标DOM树。
[0122]目标访问网页获取模块40,用于基于目标DOM树,获取对应的目标访问网页。
[0123]客户端显示模块50,用于将目标访问网页发送给客户端,以使客户端显示目标访问网页。
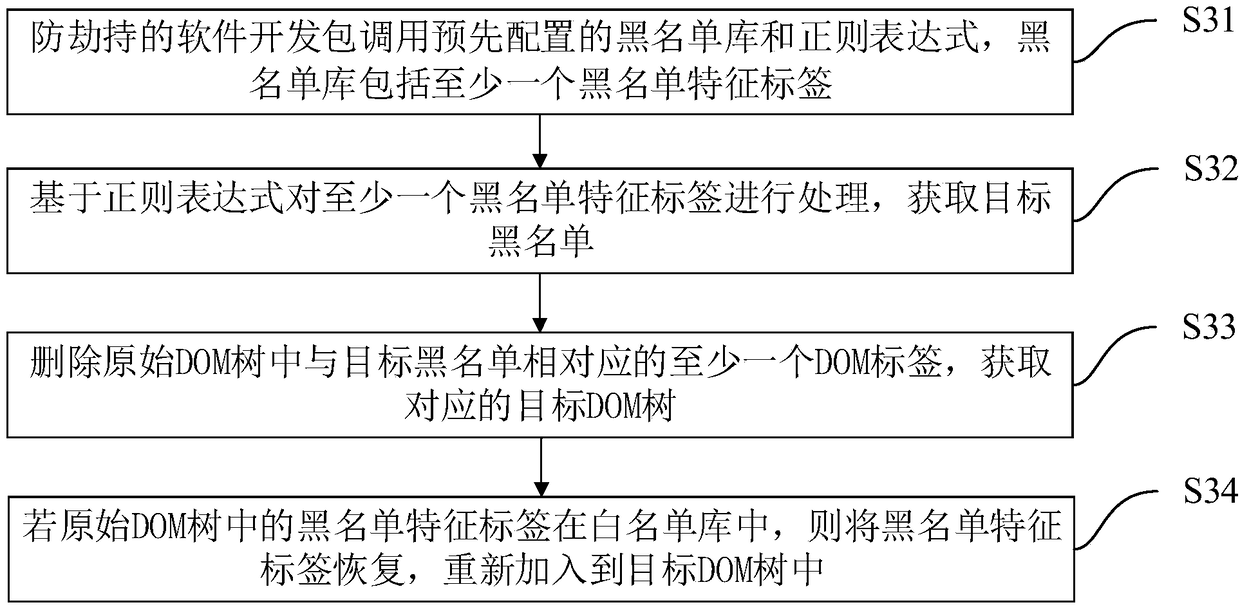
[0124]优选地,目标DOM树获取模块30包括调用单元31、目标黑名单获取单元32、目标DOM树获取单元33和黑名单特征标签恢复单元34。
[0125]调用单元31,用于防劫持的软件开发包调用预先配置的黑名单库和正则表达式,黑名单库包括至少一个黑名单特征标签。
[0126]目标黑名单获取单元32,用于基于正则表达式对至少一个黑名单特征标签进行处理,获取目标黑名单。
[0127]目标DOM树获取单元33,用于删除原始DOM树中与目标黑名单相对应的至少一个DOM标签,获取对应的目标DOM树。
[0128]黑名单特征标签恢复单元34,用于在原始DOM树中的黑名单特征标签在白名单库中时,将黑名单特征标签恢复,重新加入到目标DOM树中。
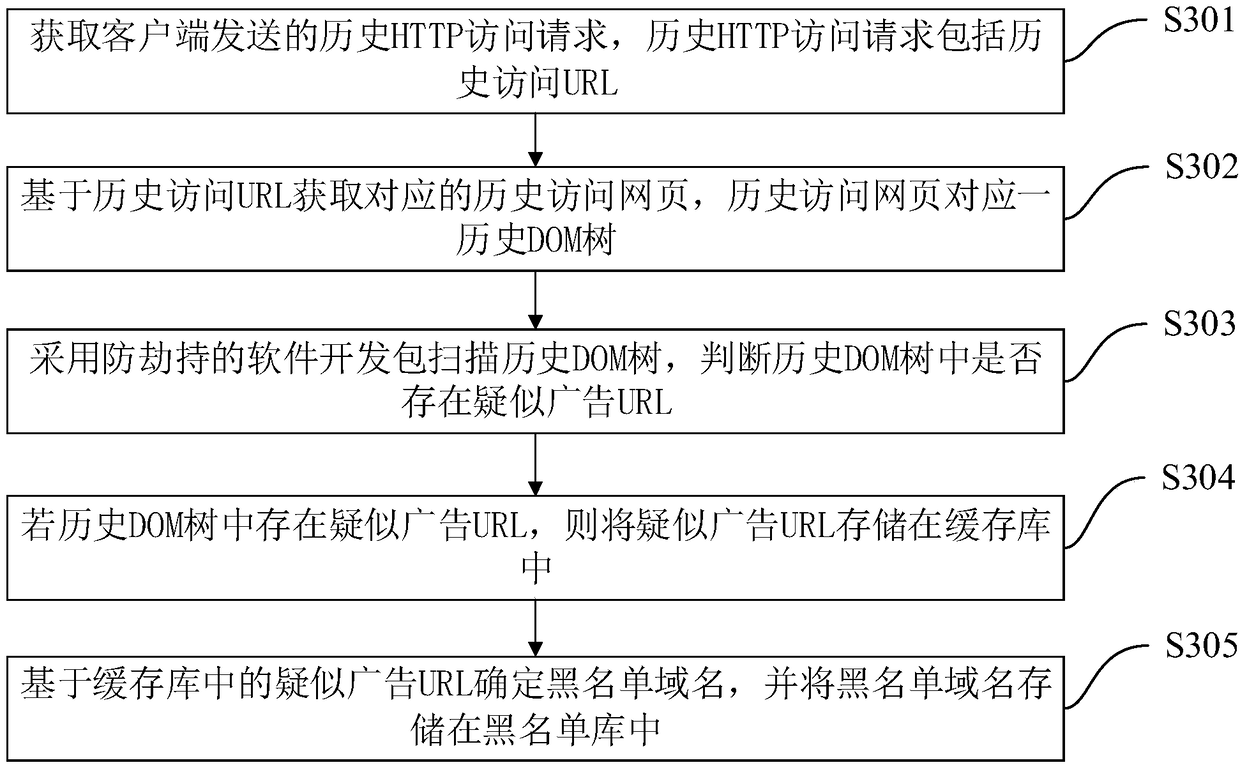
[0129]优选地,在采用防劫持的软件开发包对原始DOM树进行防劫持处理的步骤之前,防止广告运营商流量劫持的装置还包括:历史HTTP访问请求获取模块301、历史访问网页获取模块302、疑似广告URL判断模块303、缓存库存储模块304和黑名单域名获取模块305。
[0130]历史HTTP访问请求获取模块301,用于获取客户端...
Embodiment 3
[0151]本实施例提供一计算机可读存储介质,该计算机可读存储介质上存储有计算机程序,该计算机程序被处理器执行时实现实施例1中防止广告运营商流量劫持的方法,为避免重复,这里不再赘述。或者,该计算机程序被处理器执行时实现实施例2中防止广告运营商流量劫持的装置中各模块 / 单元的功能,为避免重复,这里不再赘述。
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com