Internet of Things weak resource terminal key security management method
A terminal key and security management technology, applied in the field of IoT weak resource terminal key security management, can solve the problems of unencrypted channel, replay attack, not using correct verification, etc., to achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
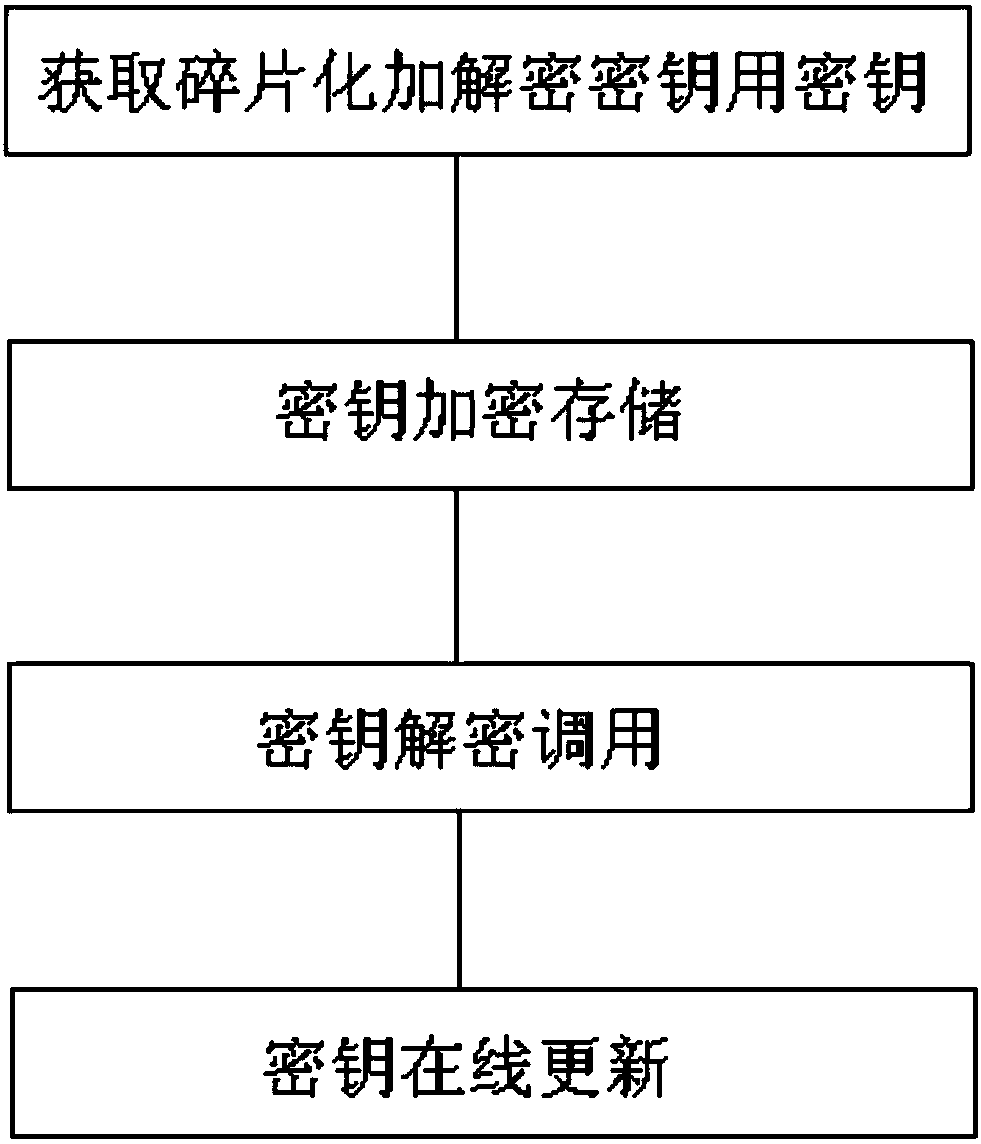
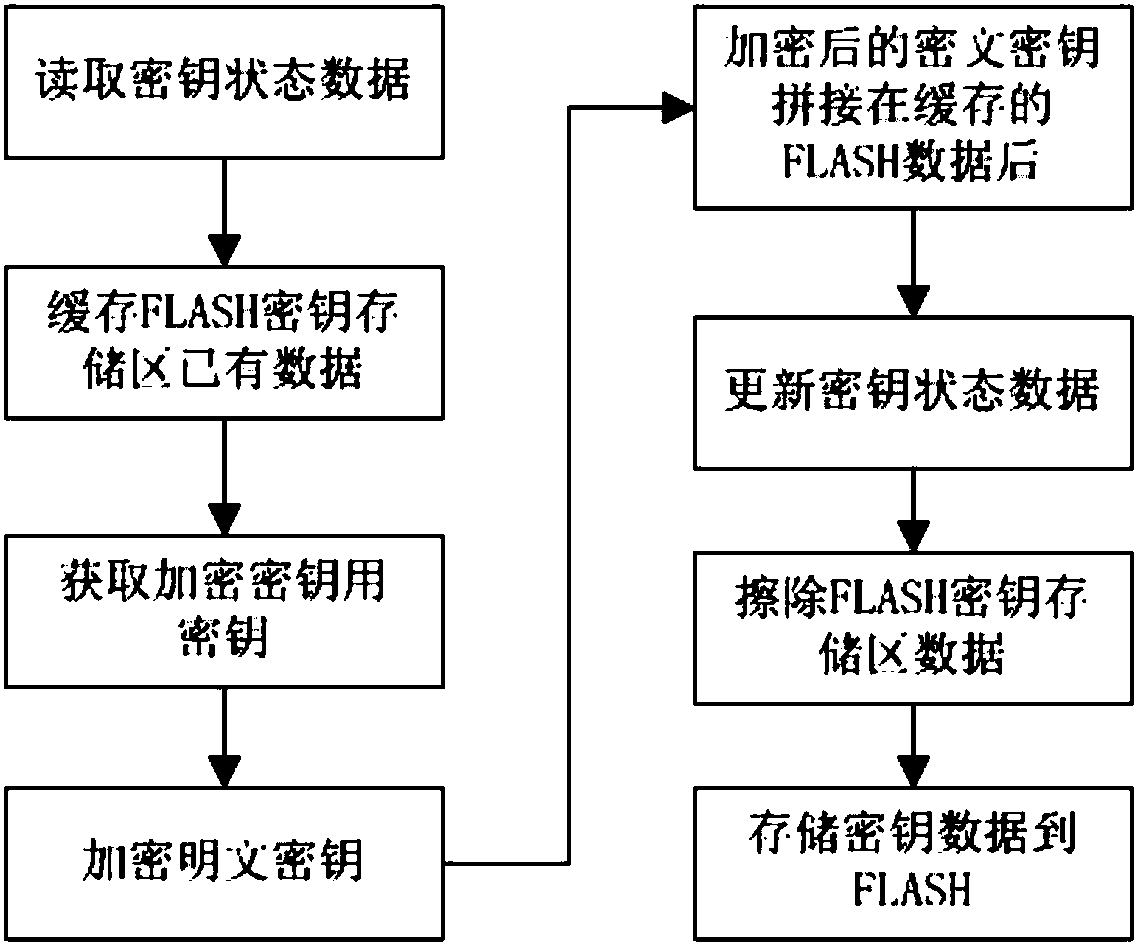
[0052] Such as figure 1 As shown, a method for effectively using limited hardware resources to ensure channel key security includes the steps of obtaining the key for fragmented encryption and decryption keys, encrypting and storing the key, invoking the key for decryption, and updating the key online.
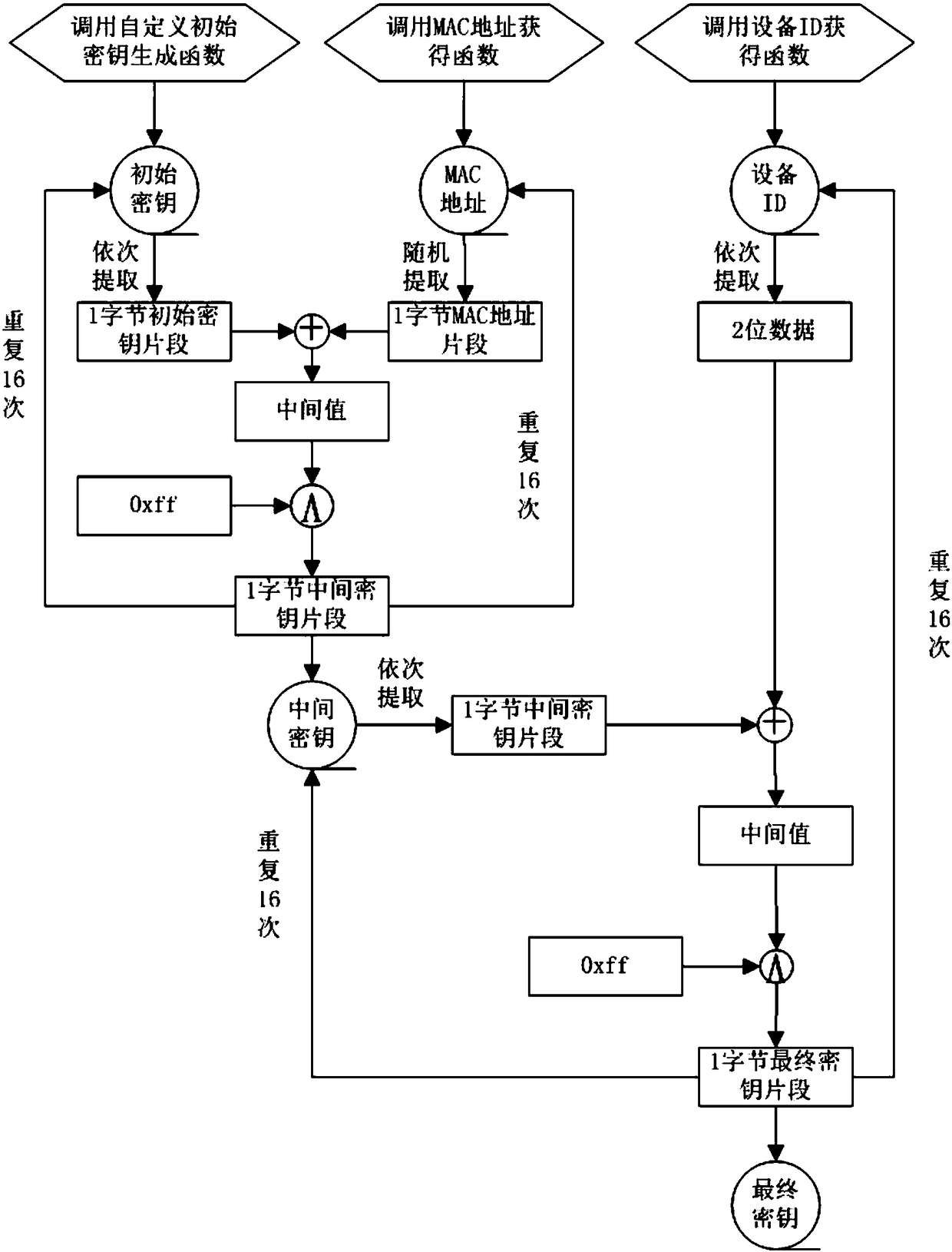
[0053] Specifically, in the process of obtaining the fragmented encryption and decryption key, the purpose of key fragmentation is to prevent the terminal device program (source program, compiled program, etc.) After decompiling and compiling, the program gets the key.
[0054]Key fragmentation can use firmware data such as MAC address, device ID number, etc. that do not appear directly in the program as parameters, and then combine some self-defined methods to obtain a set of keys. The characteristic of this key is that different terminals use the same method to obtain different keys. Since the key acquisition process contains parameters that do not appear directly in the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com