Mobile encrypted hard disk with electronic fence function, and encryption method
An encryption method, technology with electronics, applied in the direction of electrical digital data processing, internal/peripheral computer component protection, digital data protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
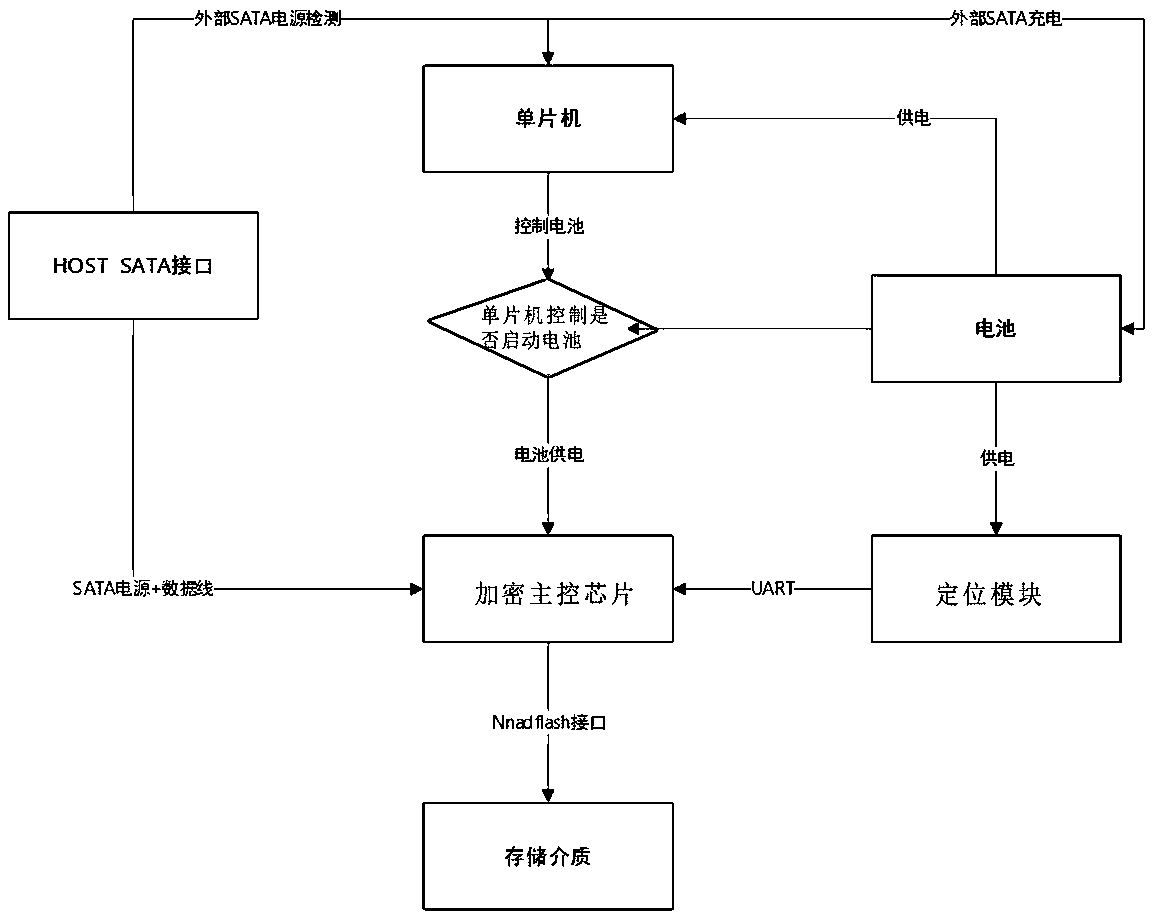
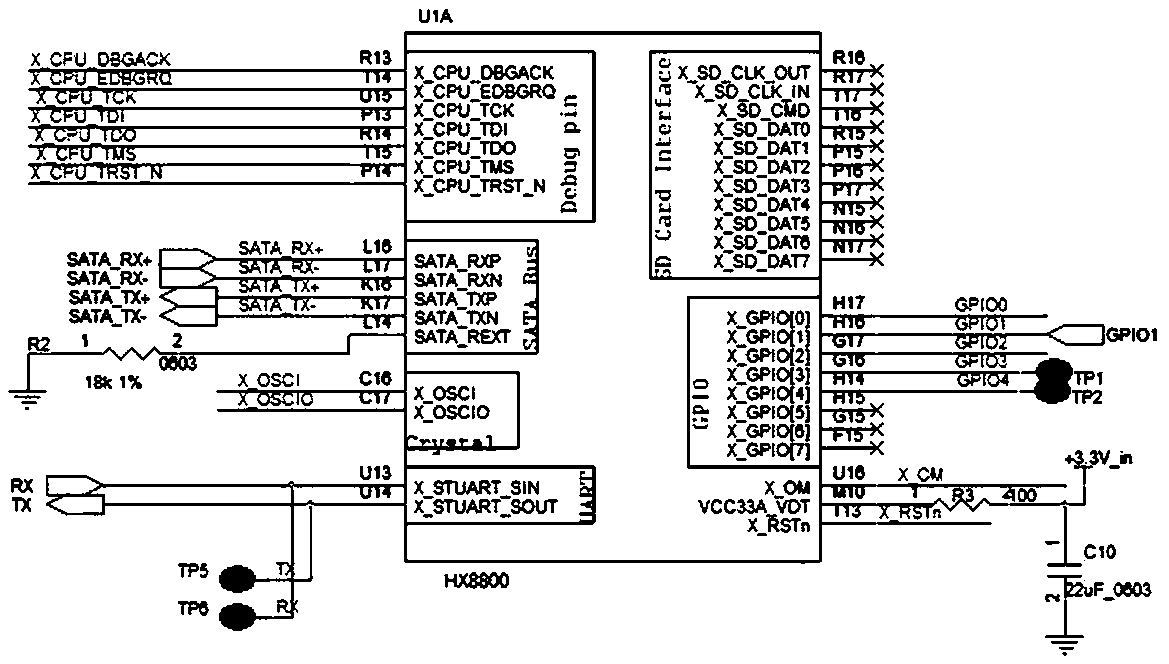
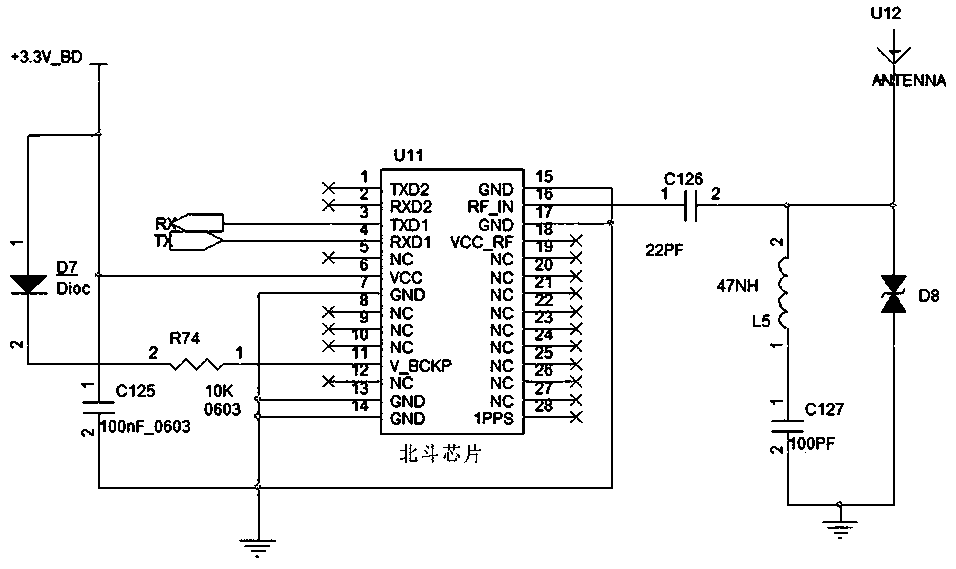
[0022] This embodiment discloses a mobile encrypted hard disk with electronic fence function, such as figure 1 As shown in the principle block diagram, the mobile encrypted hard disk includes an encrypted main control chip and a storage medium connected to the encrypted main control chip. The encrypted main control chip is provided with a trusted area and / or an illegal area, and the encrypted main control chip is connected with The positioning module that detects the location of the mobile encrypted hard disk, and the encryption main control chip performs regular inspections on the positioning module to obtain the position information of the mobile encrypted hard disk, so as to determine whether the mobile encrypted hard disk is located in a trusted area or an illegal area.
[0023] The mobile encrypted hard disk in this embodiment also includes an offline power supply module. The offline power supply module includes a battery, a battery management chip, and a single-chip microcomp...
Embodiment 2
[0029] This embodiment discloses an encryption method for a mobile encrypted hard disk with electronic fence function, such as Figure 5 As shown, it includes the following steps: S01). Set a trusted area and / or illegal area in the encrypted master chip. The mobile encrypted hard disk will have a position mark written into the storage space inside the chip during the distribution stage, based on a certain center The distance between the point and the set radius is used to set the credible area, which is the fenced area. The mobile encrypted hard disk is allowed to be used in the trusted area. The main control encryption chip will periodically inspect the Beidou module to obtain location information to monitor whether the module is in the trusted area; illegal areas can also be set, such as an enemy-occupied area on the battlefield , To ensure that once the mobile encrypted hard disk enters the illegal area, the protection mechanism is triggered immediately to ensure the securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com