WeChat unlocking method
A technology for unlocking passwords and locks, applied in the field of WeChat unlocking, can solve the problems of high cost, not widely used, difficult to popularize, etc., and achieve the effect of improving password level, improving security protection, and good confidentiality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
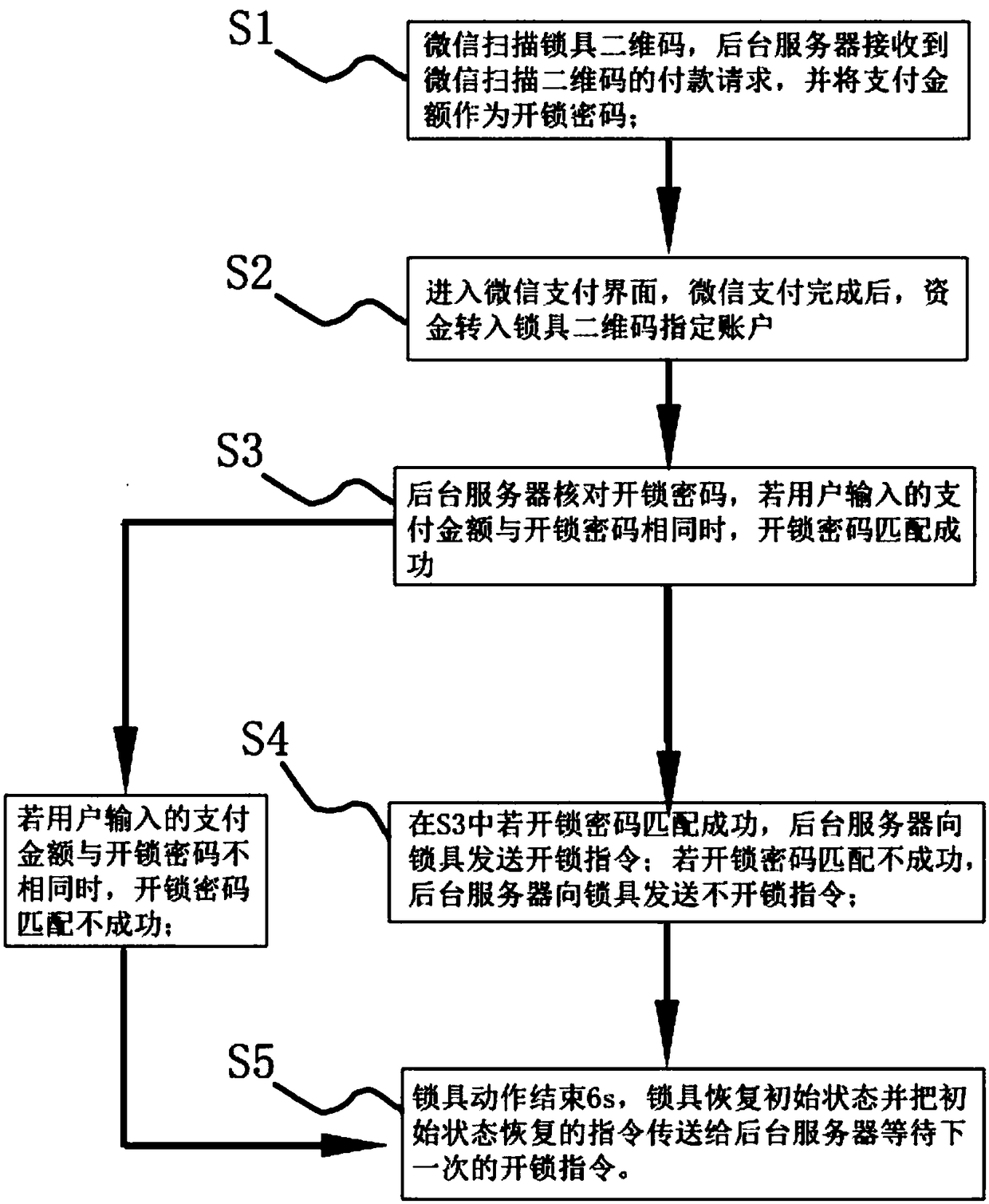
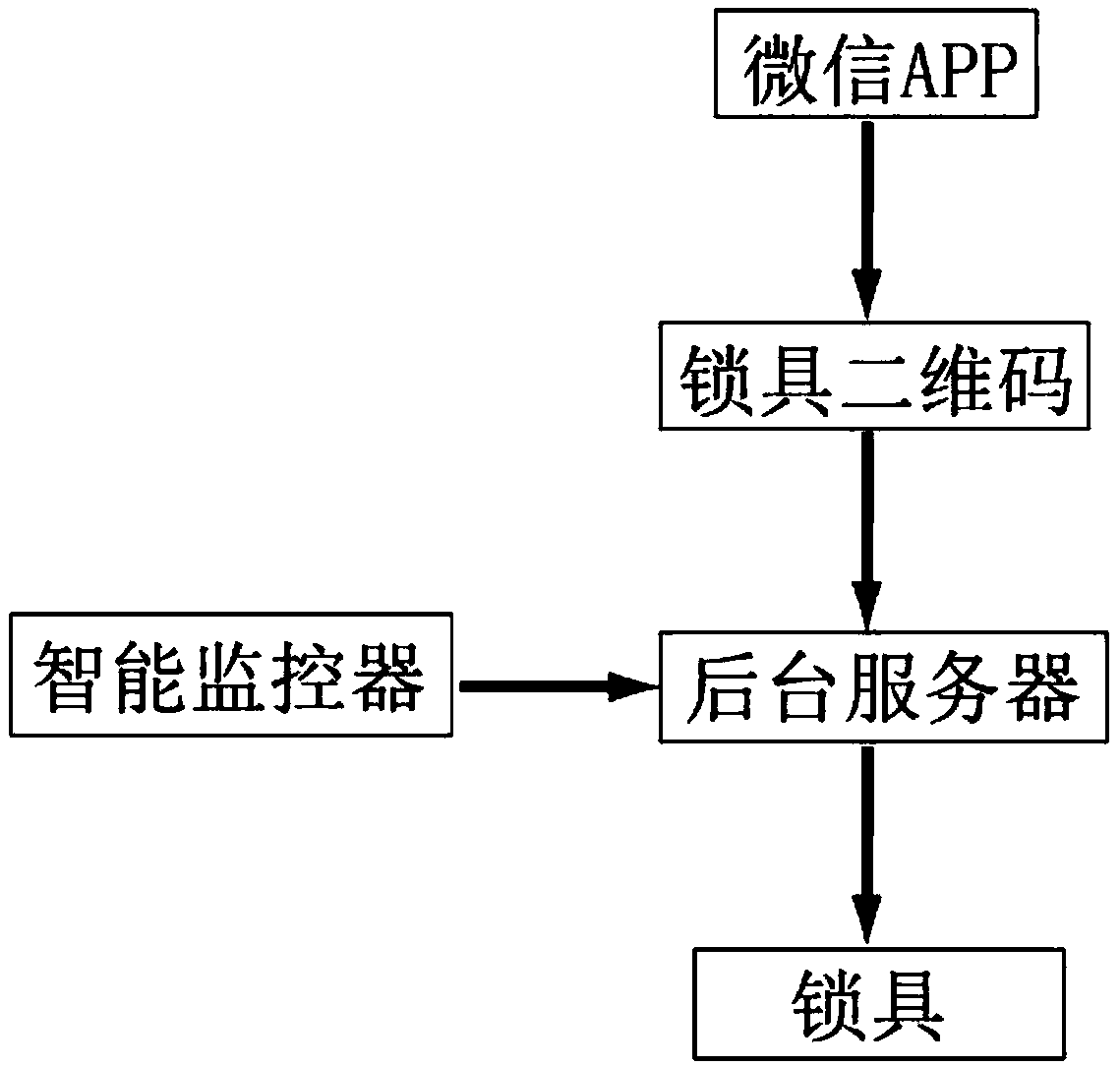
[0035] The hardware facility of the present invention comprises WeChat APP, lockset two-dimensional code, background server and lockset, and described lockset comprises communication module, central control module, power supply and electromechanical lock; Described background server receives the scanning lockset two-dimensional code of WeChat APP After the payment request and agree to use the payment amount as the unlock password request, if the paid amount matches the unlock password, the background server will transmit the unlock command to the communication module of the lock through the GPRS wireless network, and the communication module will transmit the unlock command of the wireless signal Convert it into an electric frequency signal and transmit it to the central control module; if the amount paid does not match the unlock password, the background server will issue an instruction not to unlock.
[0036] WeChat unlocking method of the present invention comprises:
[003...
Embodiment 2
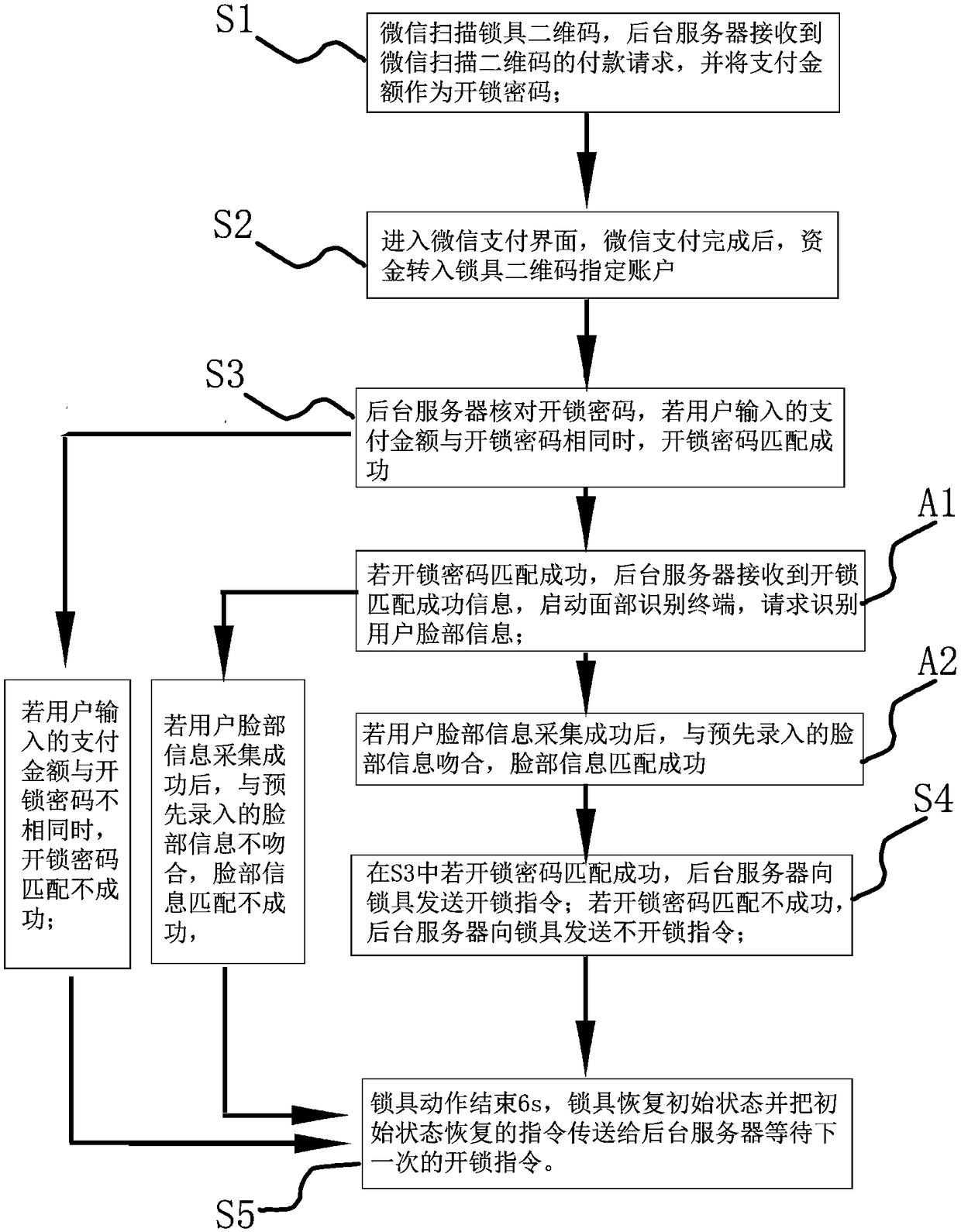
[0049] The difference between the second embodiment and the first embodiment is that the following steps are also included between the step S3 and the step S4:
[0050] A1. If the unlock password matching is successful, the background server receives the successful unlock matching information, and the background server will control the smart monitor to start the facial recognition terminal, requesting to identify the user's face information; if the unlock password matching is unsuccessful, directly enter S5;
[0051] A2. If the user's facial information is successfully collected, it matches the pre-registered facial information, and the facial information is successfully matched, and enters S4; if the user's facial information is successfully collected, it does not match the pre-registered facial information, If the information matching is unsuccessful, go directly to S5.
[0052] In S4, the background server will send an unlock command to the lock only after the matching of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com