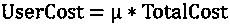Typification resource oriented information privacy protection method under IoT (Internet of things) environment
A privacy protection and resource technology, applied in the intersection of distributed computing and software engineering technology, can solve problems such as storage and computing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
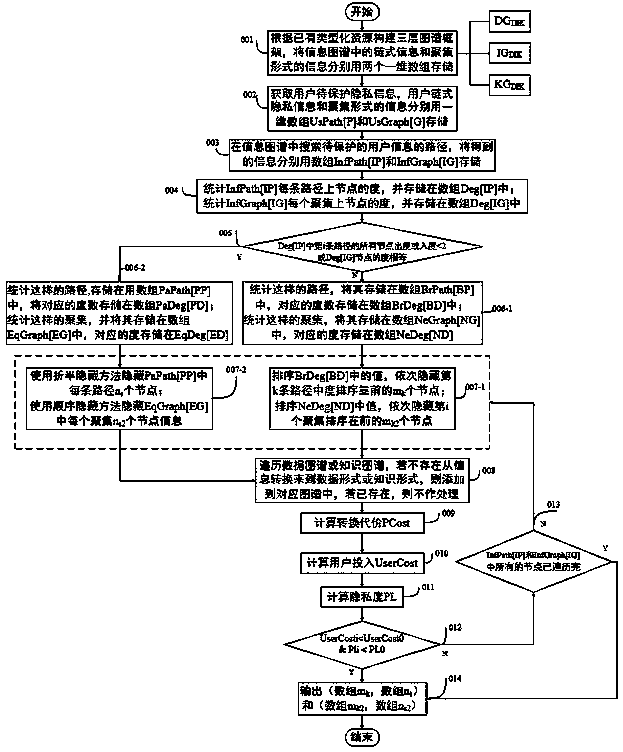
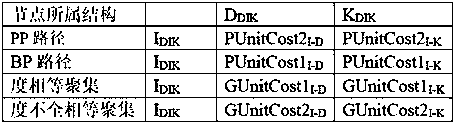
[0021]The present invention is an information privacy protection method for typed resources in an IoT environment, which is characterized in that in the provided information privacy protection method, user information privacy resources are distinguished as information in the form of links, information in the form of aggregation, and information in the form of links The characteristic is that there is a complete path, including the information characterized by no branch path and the information characterized by branch path. For the privacy protection of user information in the form of links and aggregation, the fusion solution has the following steps:
[0022] Step 1) corresponds to figure 1 In 001, according to the existing typed privacy resources, construct a data map, information map and knowledge map processing framework, and store the link form information and the aggregate form information in the information map in one-dimensional arrays;
[0023] Step 2) corresponds to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com