Method and system for remotely logging in vehicle-mounted system on the basis of user permission
An in-vehicle system and remote login technology, applied in the field of smart cars, can solve the problems of smart car safety impact and low safety factor of smart cars.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to explain in detail the technical content, structural features, achieved goals and effects of the technical solution, the following will be described in detail in conjunction with specific embodiments and accompanying drawings.
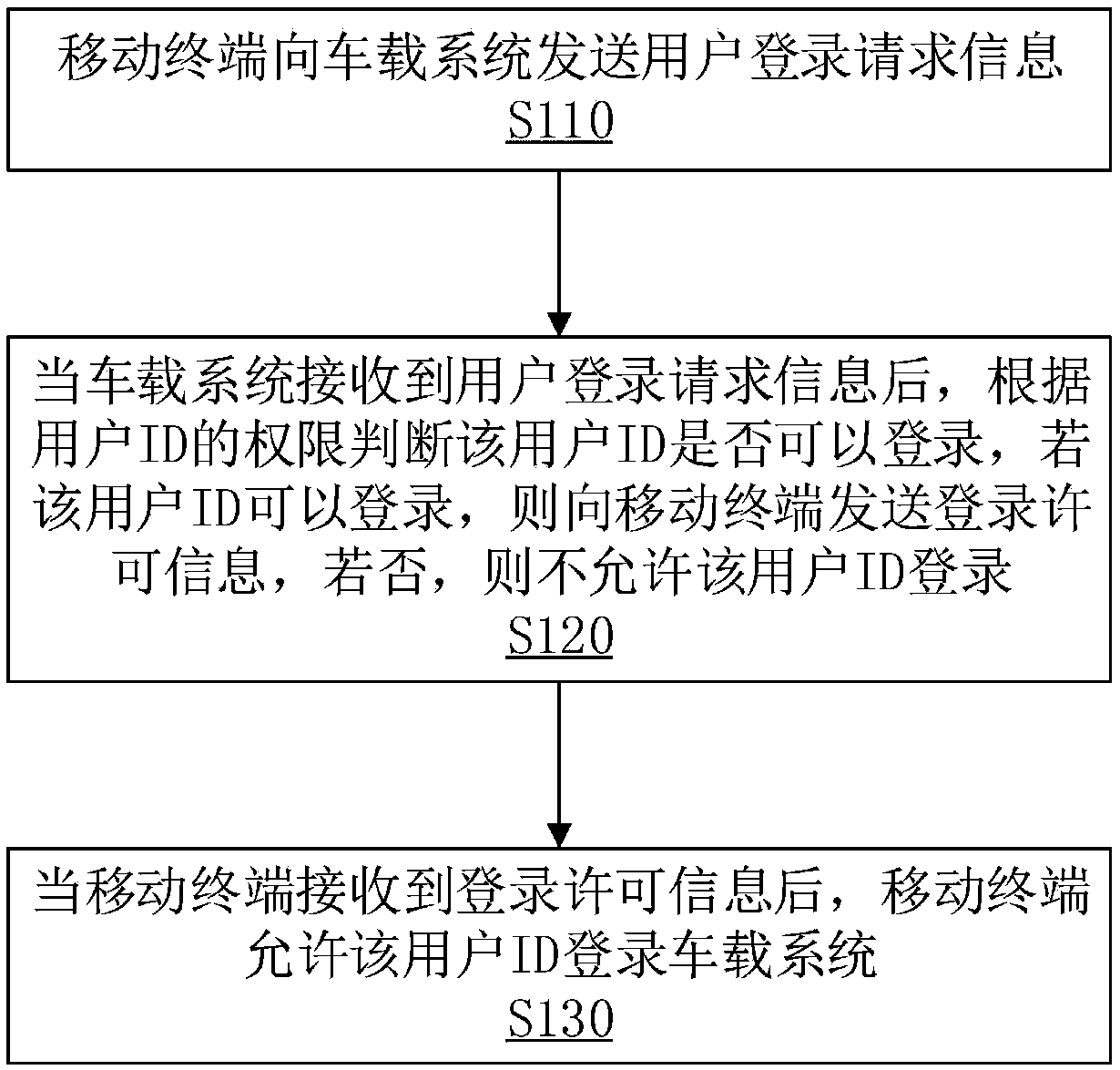
[0032] Please refer to 1, the method for remotely logging into the vehicle-mounted system based on user authority in this embodiment includes the following steps:
[0033] Step S110: The mobile terminal sends user login request information to the vehicle-mounted system, and the user login request information includes a user ID; The user login request information requests the vehicle-mounted system to log in, wherein the user login request information includes a user ID.
[0034] Step S120: After the vehicle-mounted system receives the user login request information, it judges whether the user ID can log in according to the authority of the user ID. If the user ID can log in, it sends login permission information to the mobile terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com