Network intrusion detection method on the basis of combining PCA and Bayesian
A network intrusion detection and combination technology, which is applied in the field of network intrusion detection based on the combination of PCA and Bayesian, can solve the problems of long detection time and ineffective attack technology, and achieve the goal of improving detection accuracy and improving detection time Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in detail below with reference to the accompanying drawings and examples.
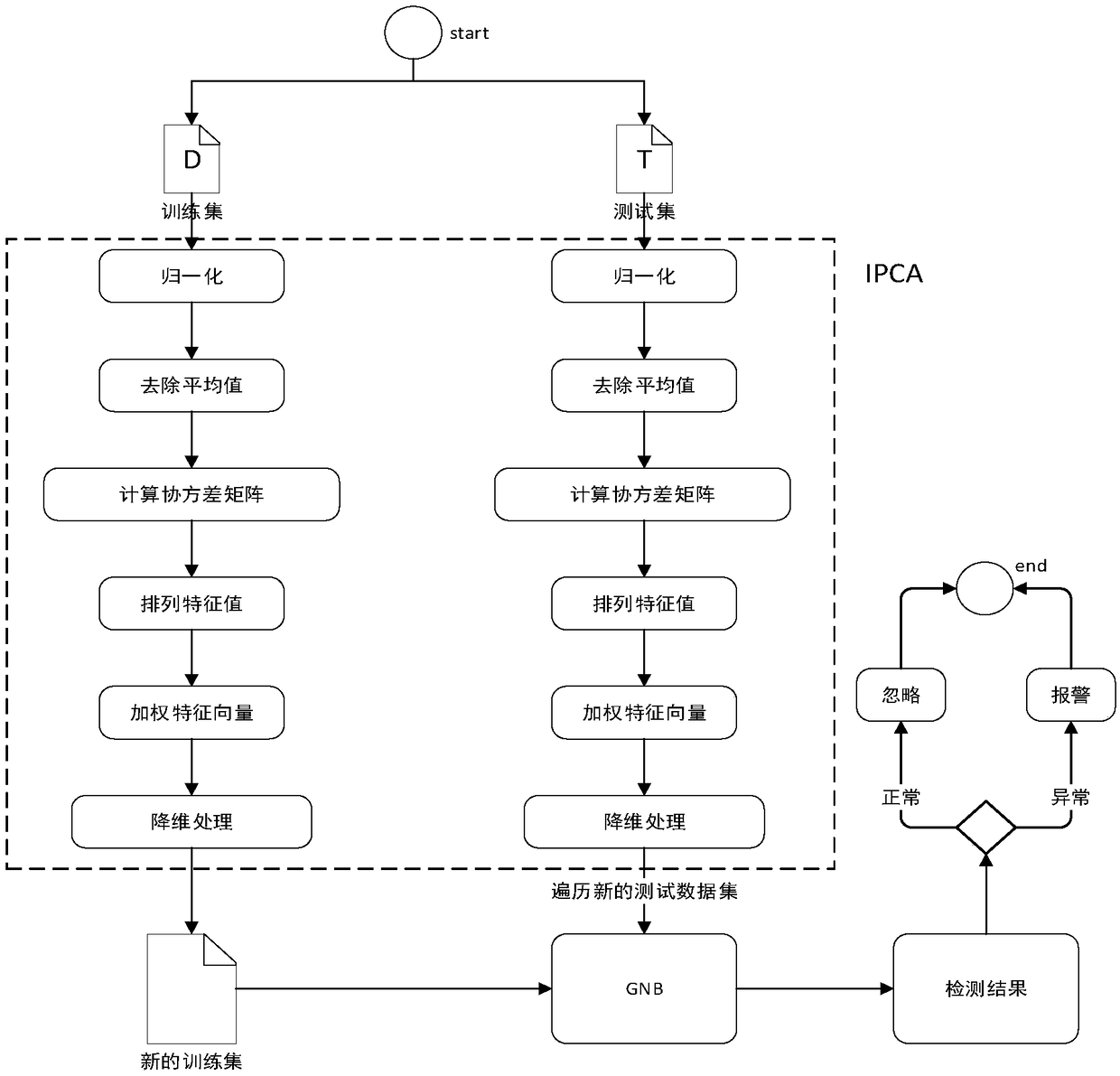
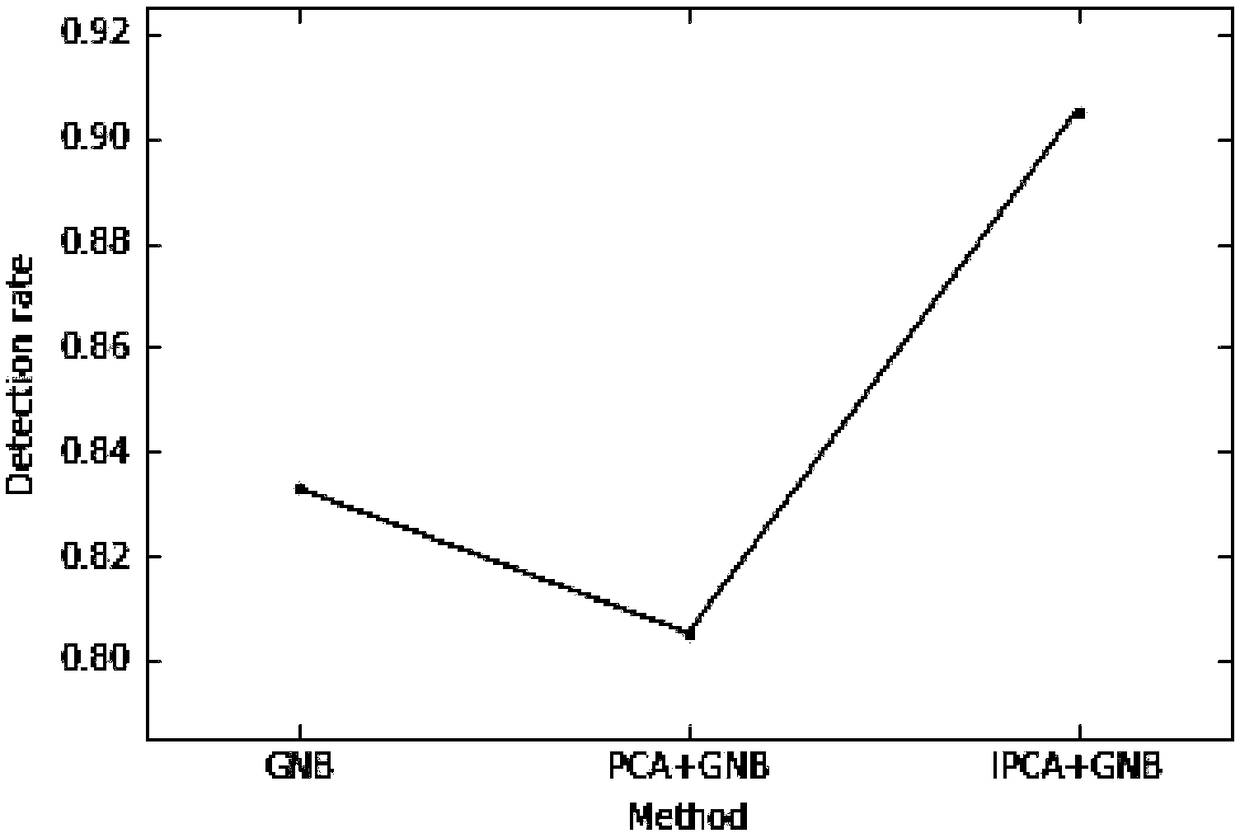
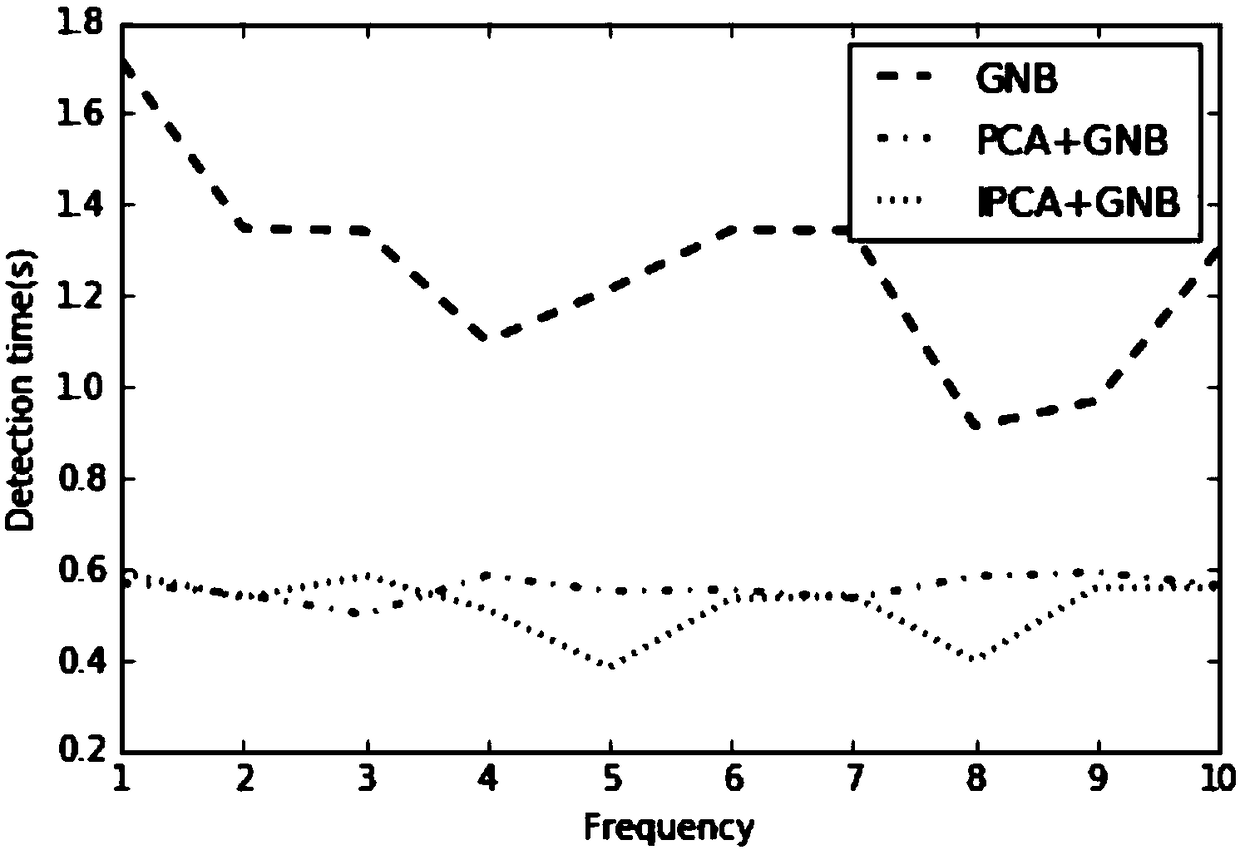
[0023] With the continuous change of network intrusion attack means, new attack types are constantly generated, and the traditional detection method based on rule files cannot adapt to the new attack type. Therefore, the present invention chooses an intrusion detection method based on data mining. However, most of the existing intrusion detection methods in data mining have the problem that the detection time is too long and cannot be detected in time. Therefore, the present invention provides a network intrusion detection method based on the combination of PCA and Bayesian , first apply PCA to the training data set D and the test data set T to obtain the training data and test data after dimensionality reduction, which reduces the model training time of the Bayesian classifier and greatly shortens the detection time, and then adopts the fastest detection t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com