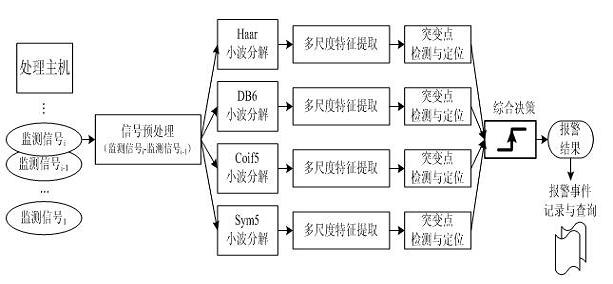
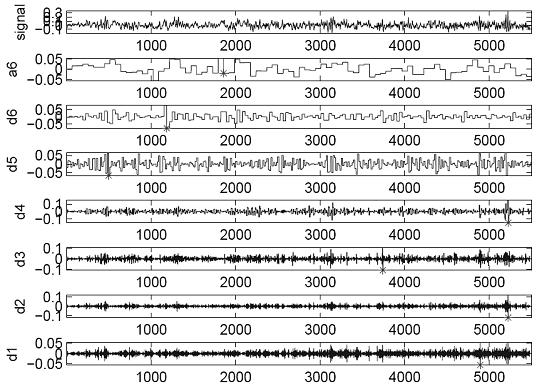
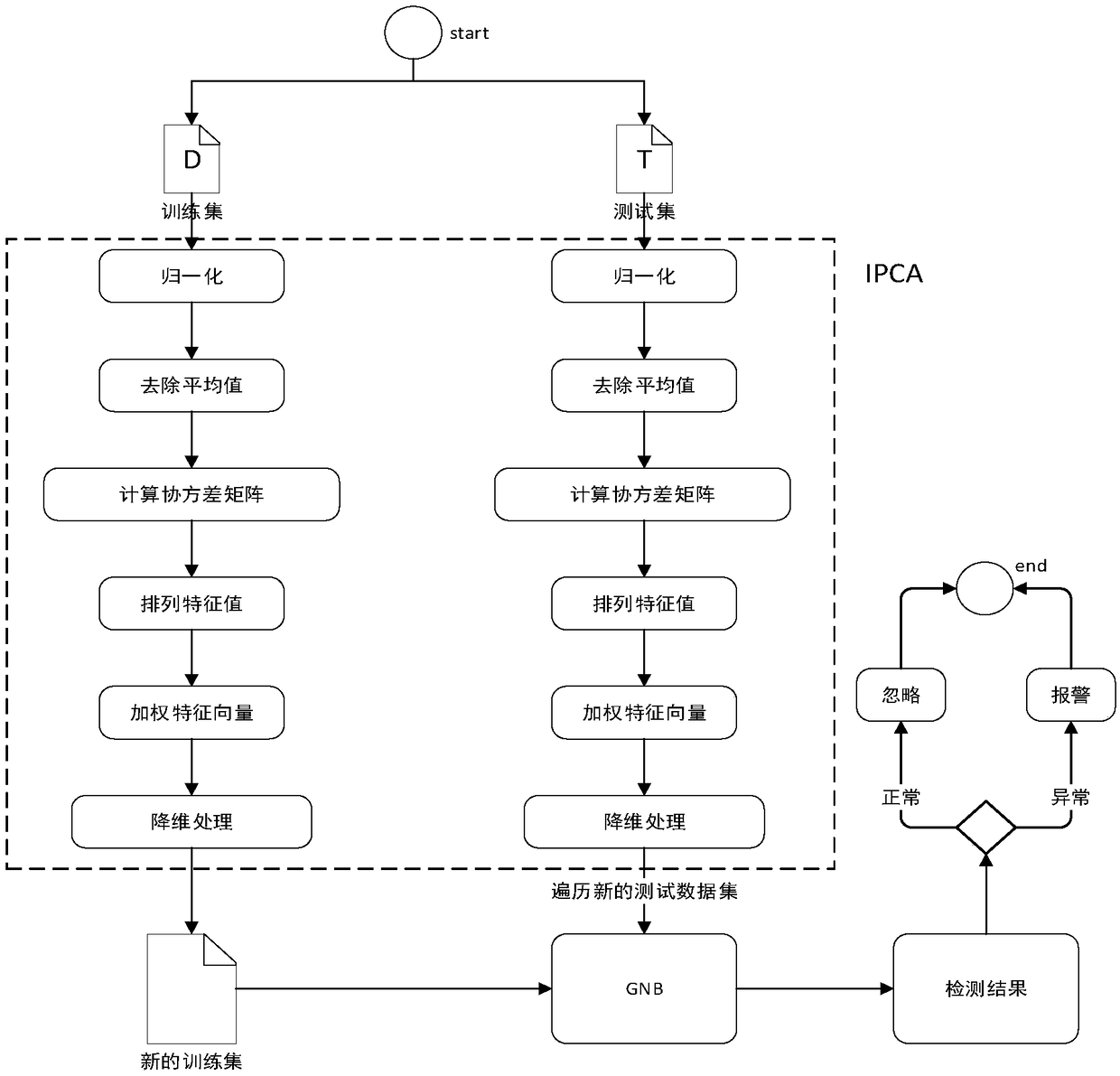
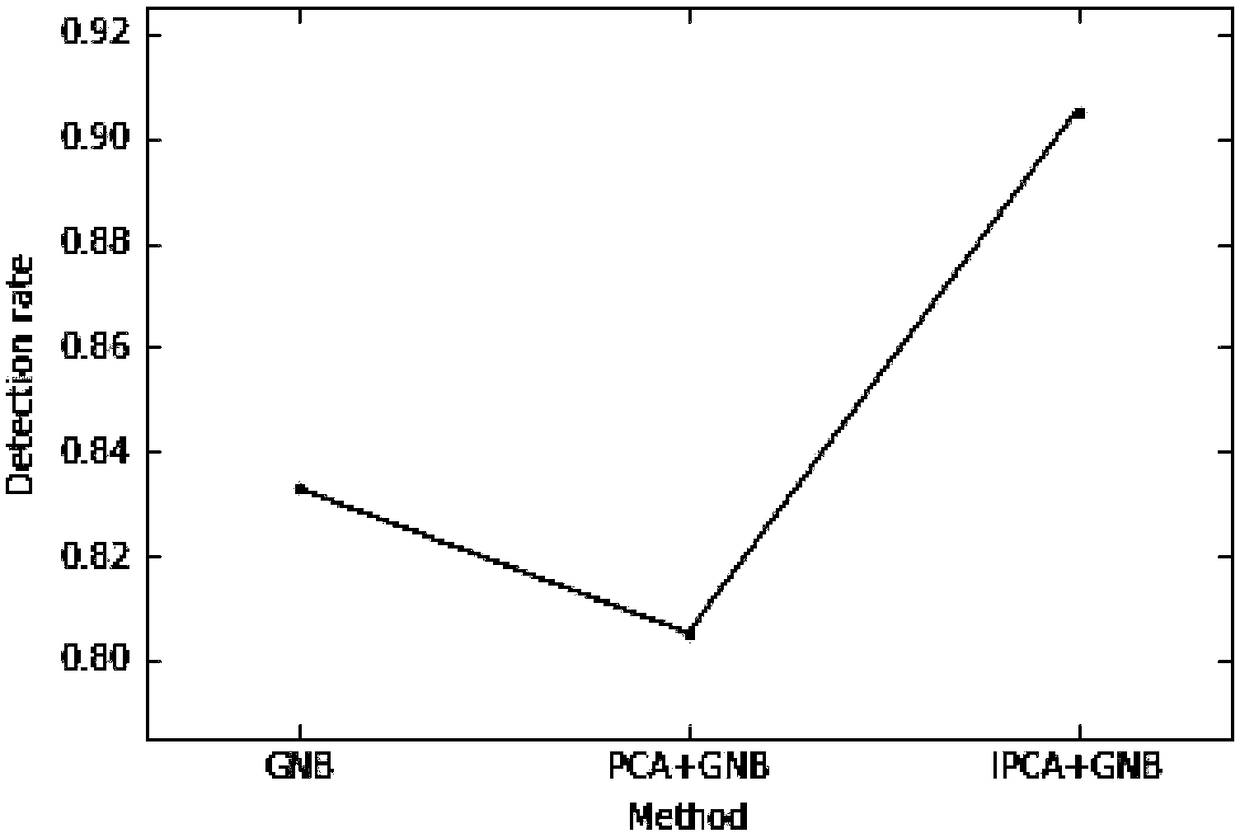
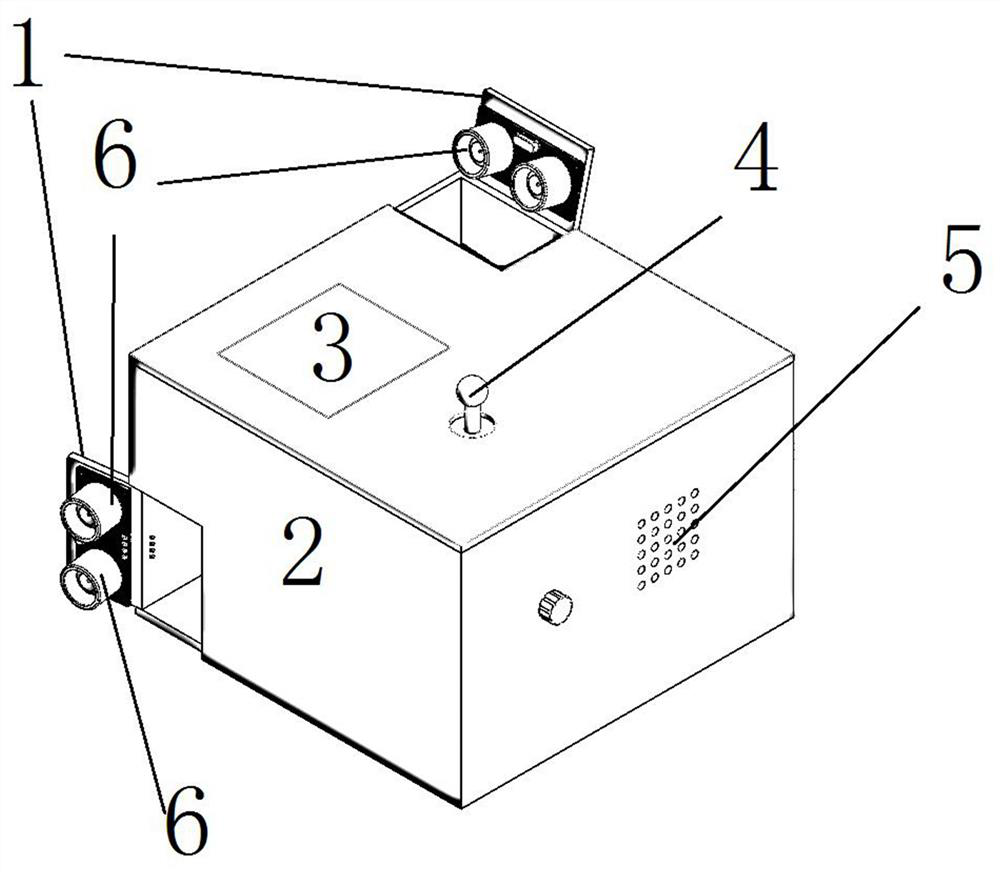
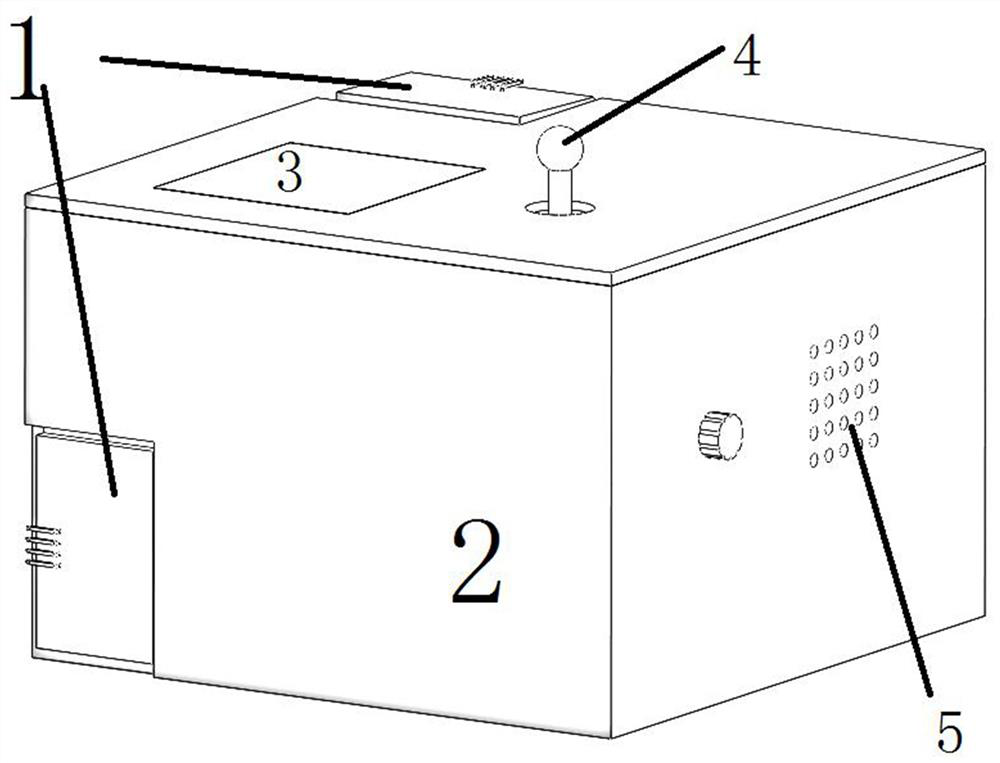
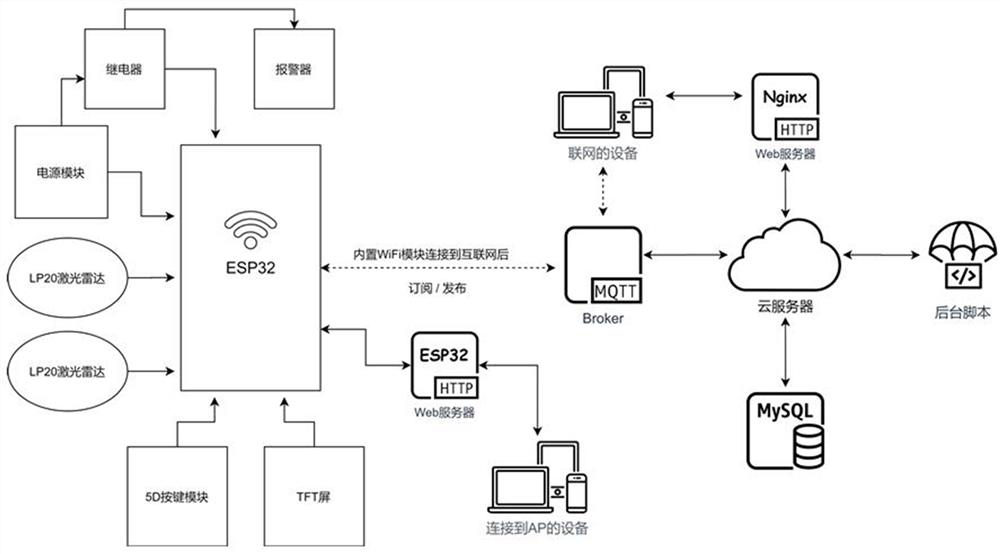
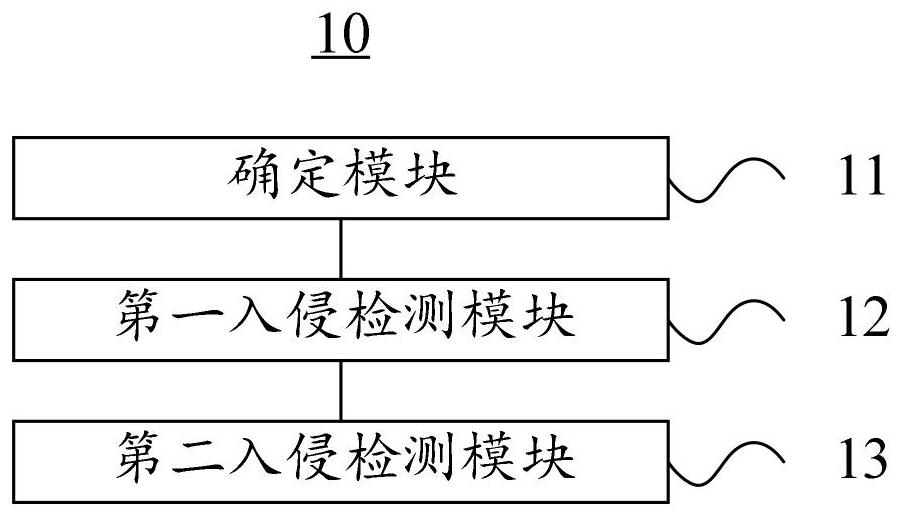
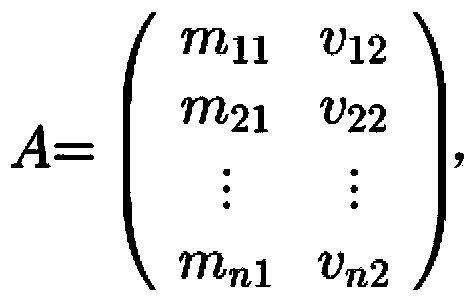Patents
Literature
49results about How to "Implement intrusion detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
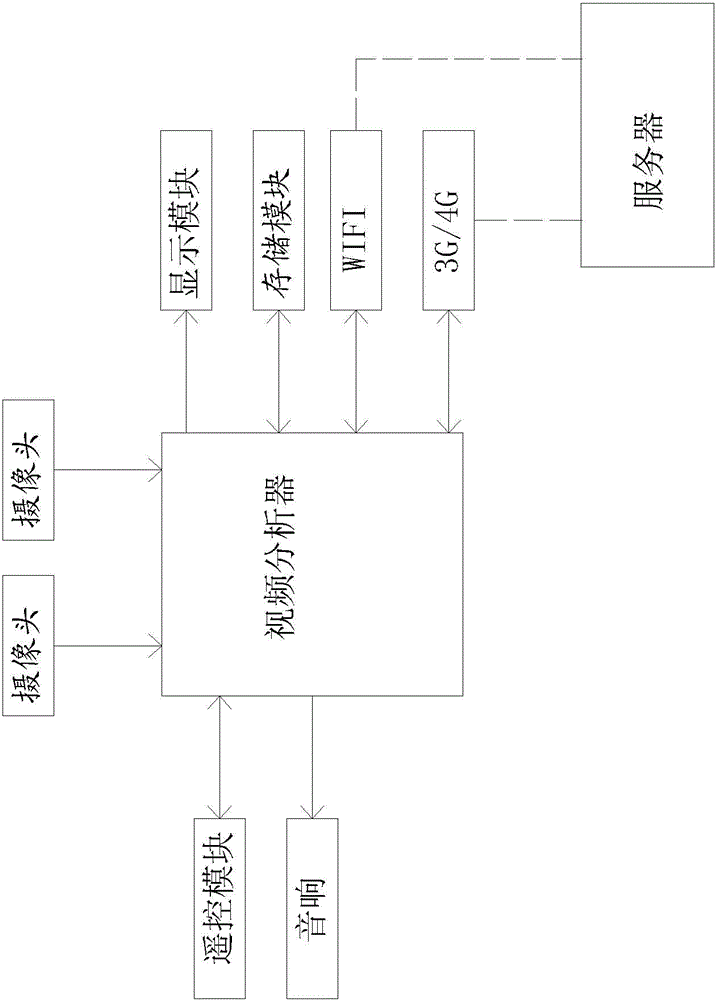
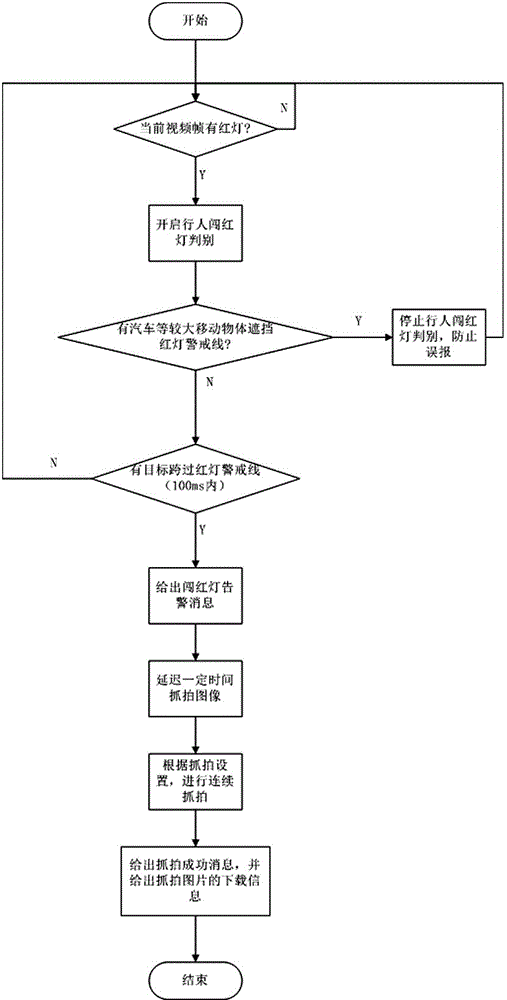
Intelligent video analyzing method for pedestrians crossing zebra stripes
InactiveCN104091446AStrong deterrenceEliminate the herd mentalityControl with pedestrian guidance indicatorDetection of traffic movementGreen-lightAnalysis method
The invention discloses an intelligent video analyzing method for pedestrians crossing zebra stripes. The intelligent video analyzing method comprises the following steps that (1) a video analyzing system is arranged near the zebra stripes and is started regularly at preset time points, and cameras collect video information data in real time and transmit the video information data to a video analyzer; (2) the video analyzer analyzes the video information data and judges states of traffic lights, the intruder alarming function of an intelligent alarming module is started if the red light is turned on, and the prompt information playing function of the intelligent alarming module is started if the green light or the yellow light is turned on; (3) the video analyzing system is closed at preset time points, and the video information data of the day are stored before the video analyzing system is closed. By means of the scheme, the unique intelligent video analyzing method for the urban zebra stripe traffic lights and the moving pedestrians is achieved, the intrusion on the pedestrians crossing the zebra stripes is detected when the red light is turned on, and intelligent audio and video alarming is conducted according to detecting results.
Owner:厦门磐联科技有限公司
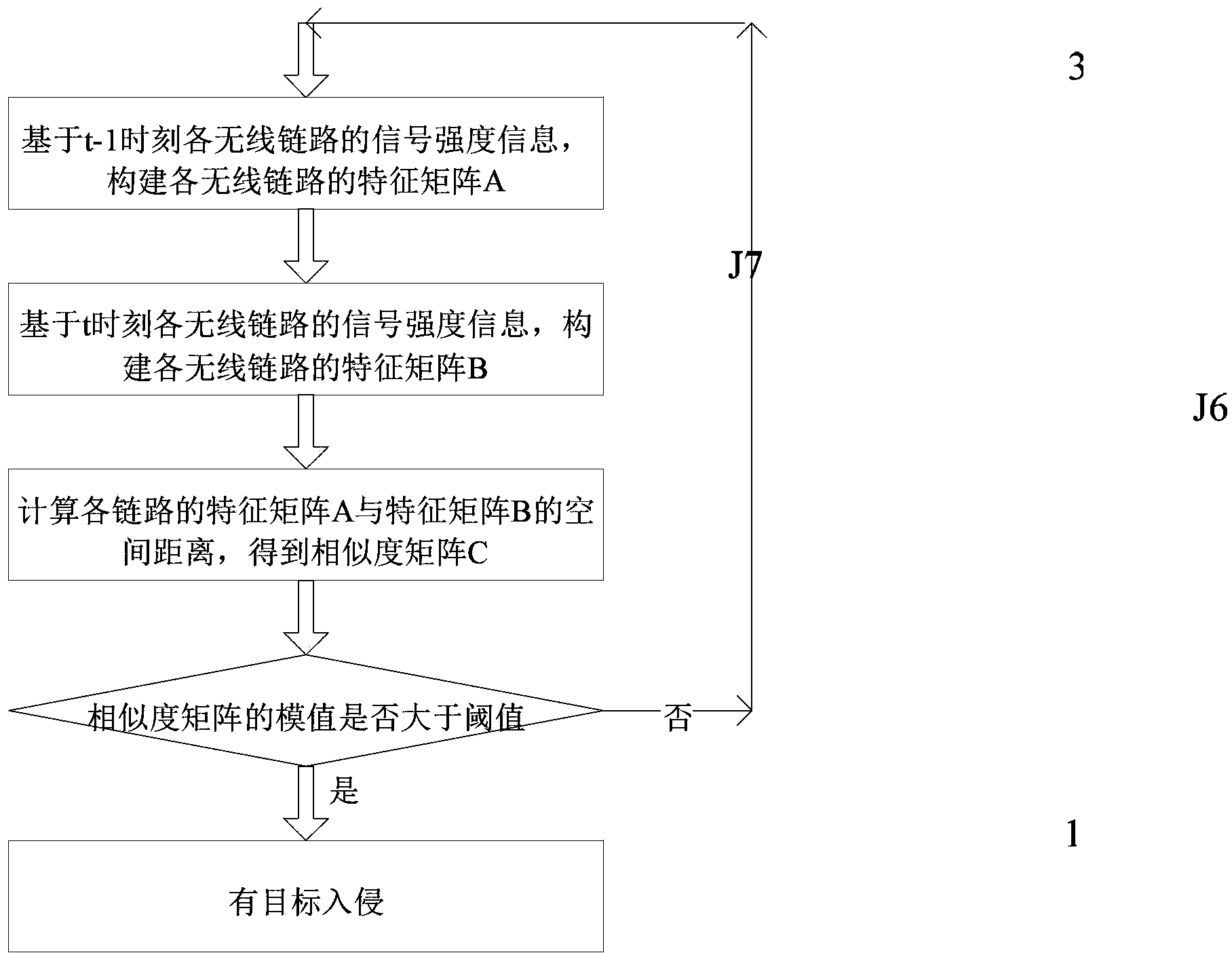
Method for intrusion detection based on wireless signal characters
PendingCN103458413AImplement intrusion detectionImprove robustnessSecurity arrangementIntrusion detection systemSignal strength
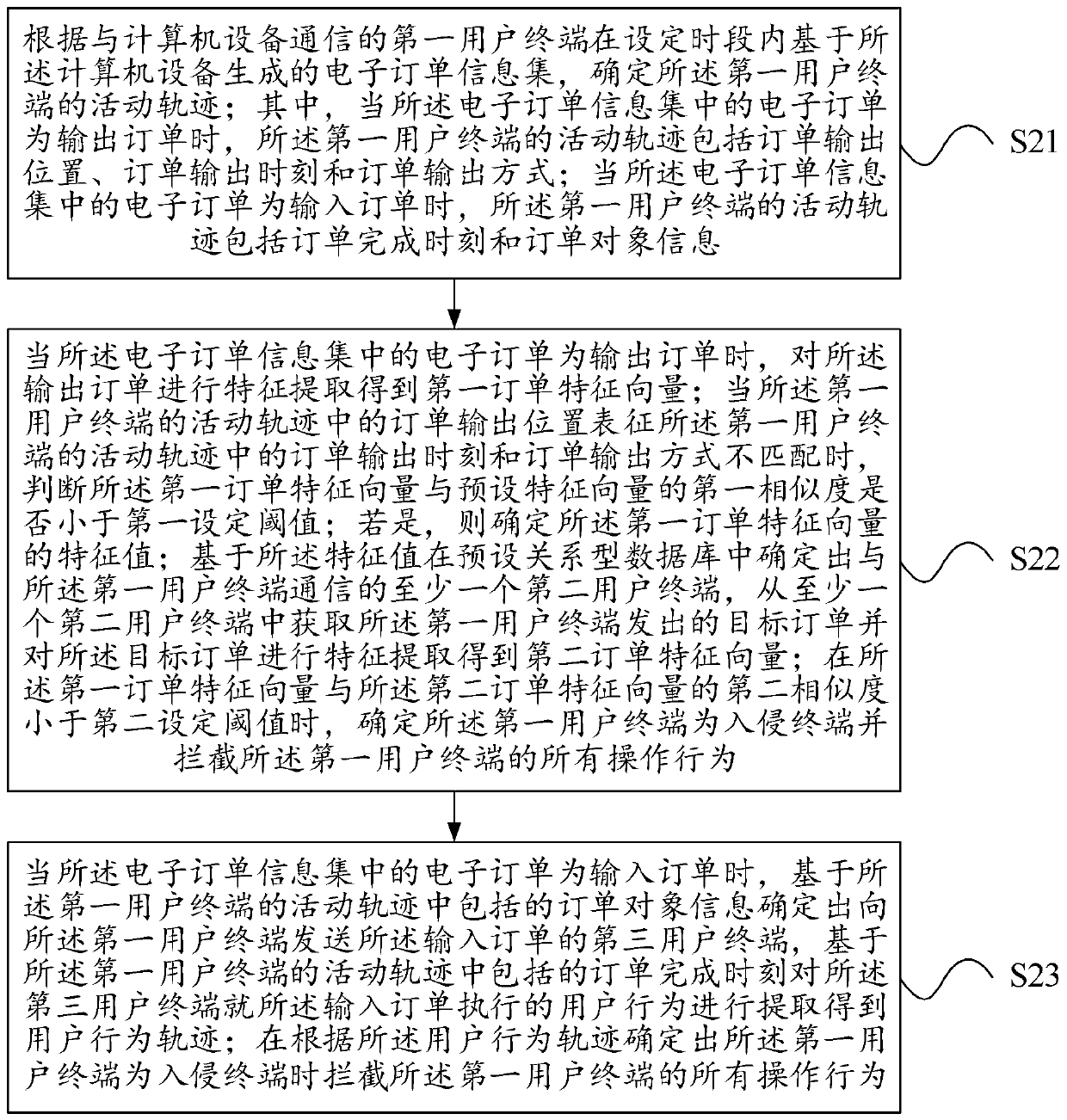
The invention relates to a method for intrusion detection based on wireless signal characters, and belongs to the field of security and protection technology and wireless network application. According to the method for the intrusion detection, the state that whether object intrusion exists or not can be detected through the influence on the wireless link signal strength from an intrusion object. According to the intrusion detection algorithm, the signal strength information of all wireless links serves as input information, whether intrusion exists or not can be detected through the two-dimensional statistical properties of the mean value and the variance of the signal strength information. A system in which the method is adopted is composed of wireless scanning nodes, a wireless aggregation node, a general PC and the intrusion detection algorithm. The intrusion detection algorithm is installed in the general PC, and the wireless scanning nodes, the wireless aggregation node and the general PC are communicated wirelessly. The method is suitable for intrusion detection at wall shielding, dark environment and other severe environments. Whether a target intrudes or not can be detected through the change, caused by the fact that the intrusion object shields a wireless signal, of the wireless link signal strength.
Owner:DALIAN UNIV OF TECH
Perimeter defense system based on wireless sensor network
ActiveCN103093563AImplement intrusion detectionNode cost is lowBurglar alarmMonitoring statusMobile wireless sensor network
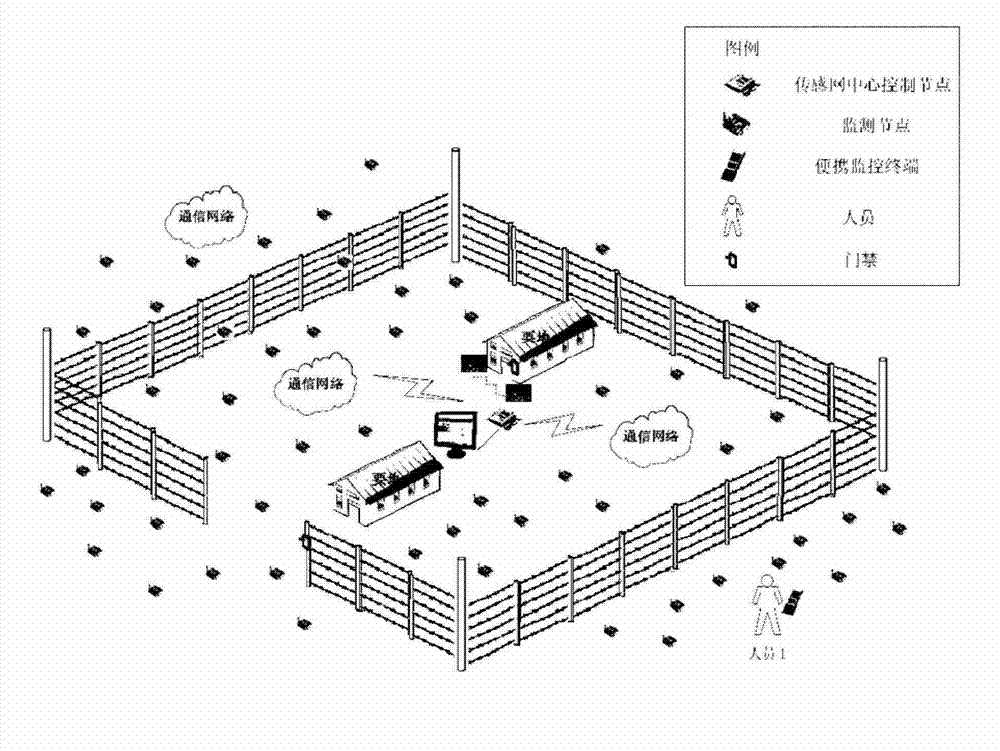
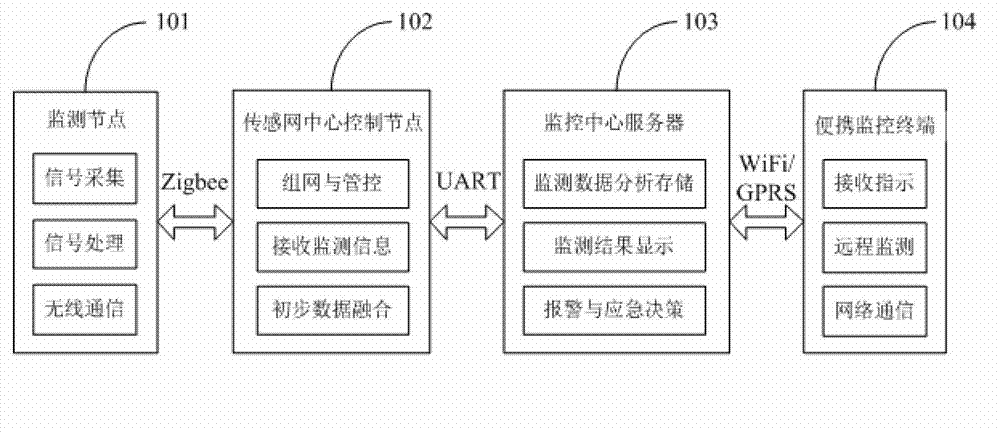
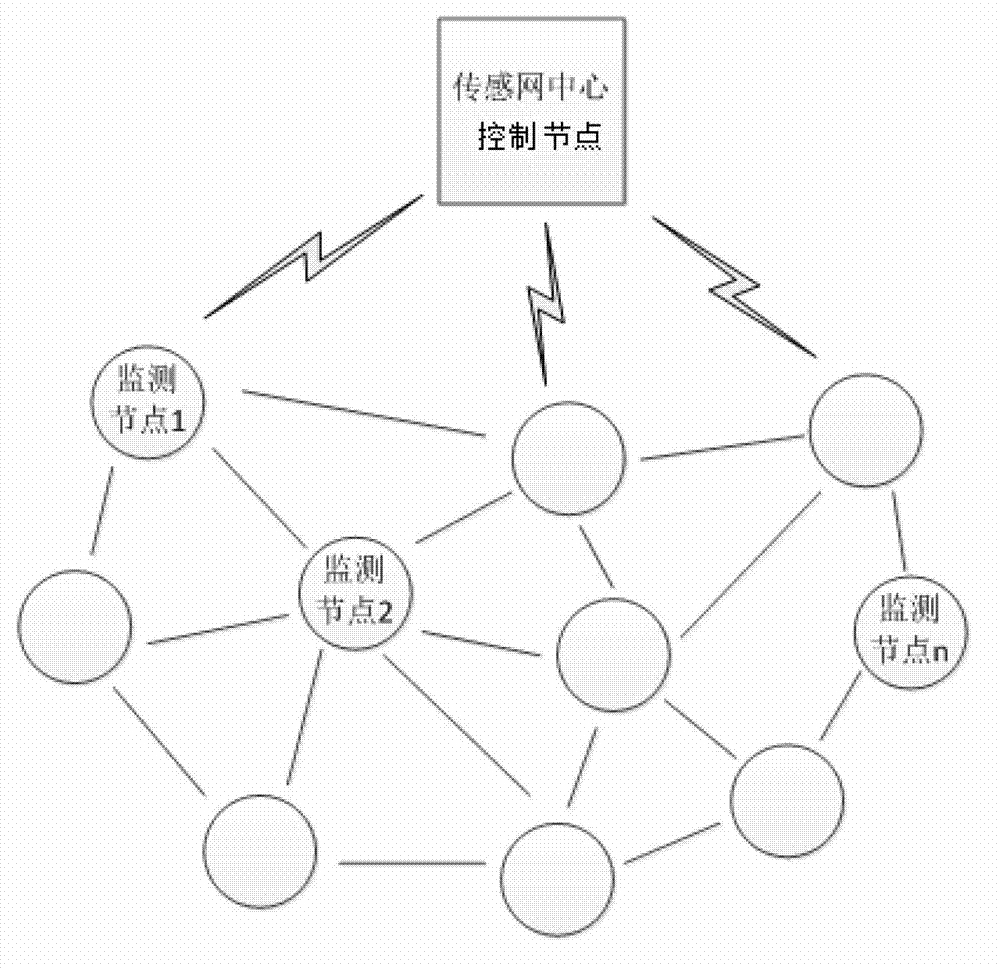
The invention discloses a perimeter defense system based on a wireless sensor network. The perimeter defense system comprises a wireless monitoring node, a sensor network central control node, a monitoring central server and a portable monitoring terminal. Information collected by the wireless monitoring node through an external expanded sensor and the collected information is sent to the sensor network central control node by the wireless monitoring node in a wireless mode; the sensor network central control node is used for building wireless communication networks, receiving the information sent by the wireless monitoring node and processing the information by utilizing a data diffusion method, and transmitting the processed monitoring data to the monitoring central server in a wired mode; the monitoring central server is used for storing and analyzing the monitoring data and displaying monitoring information, when a defended object is invaded, the monitoring central server alarms and sends the monitoring information and alarm information to the portable monitoring terminal in the wireless mode; and the portable monitoring terminal visits data in the monitoring central server in the wireless mode. The perimeter defense system based on the wireless sensor network has the advantages of being low in cost, low in power consumption, flexible in arrangement, wide in monitoring surface and good in applicability.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Sensor network safety system based on delaminated intrusion detection
InactiveCN102625312AImprove performanceGuaranteed uptimeSecurity arrangementMoving averageNetwork management
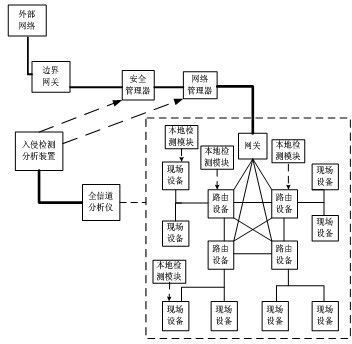
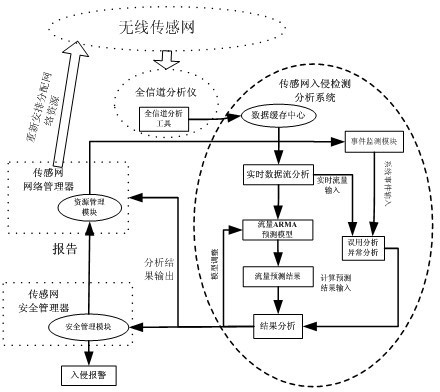
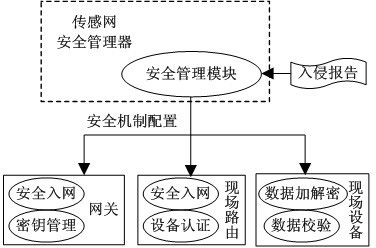
The invention discloses a sensor network safety system based on delaminated intrusion detection, which comprises a safety manager, a network manager, a gateway, a route device and a field device. The sensor network safety system also comprises a local intrusion detection module, an analyzer intrusion detection device and an all-channel analyzer. A user can regulate sleep time duty cycle of the device in the network according to the demand of the local intrusion detection rate to ensure that the local intrusion detection rate meets the demands; a third party detection module based on the all-channel analyzer is used for detecting and analyzing network flow, thus system resource consumption can be reduced; and in a further technical scheme, the flow in the network is predicted through a simple linear prediction algorithm ARMA (Autoregressive Moving Average) model, thus excessive resource consumption caused by local detection in a wireless sensor network can be effectively avoided. Network resources can be more reasonably utilized, network performance is improved, intrusion detection of network accessing equipment is effectively realized, communication treatment of network safety is supported, and normal operation of the network is guaranteed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
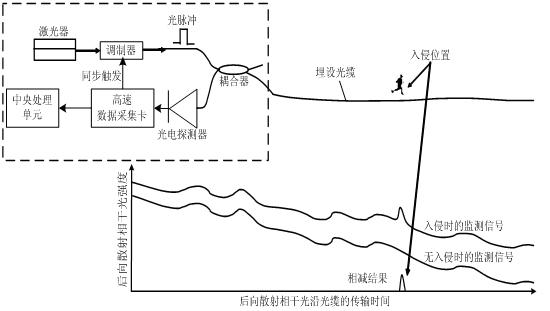
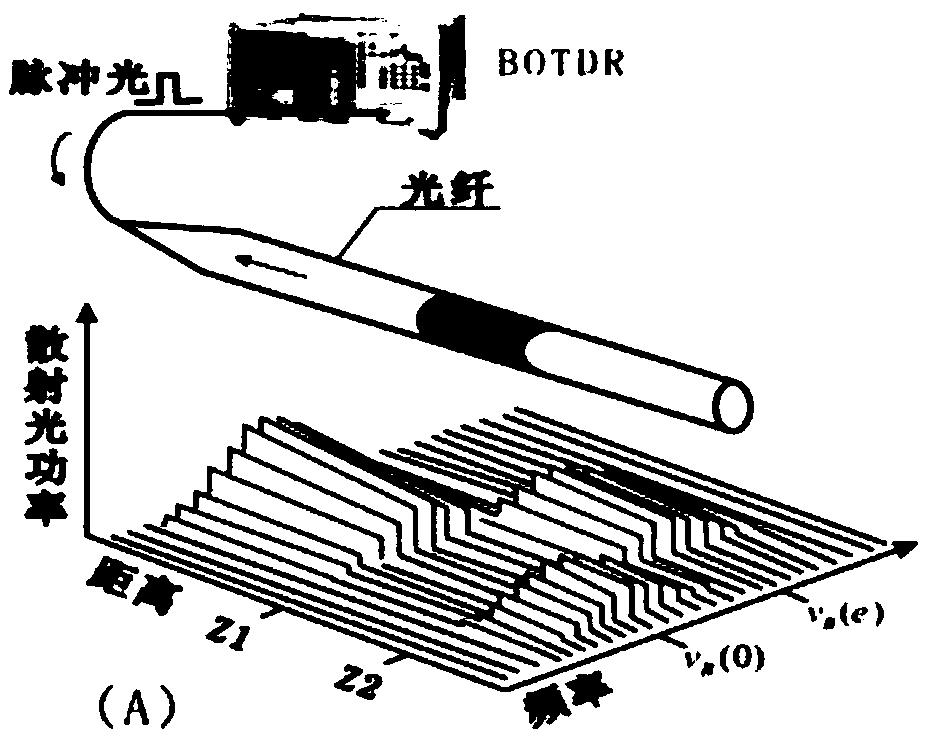
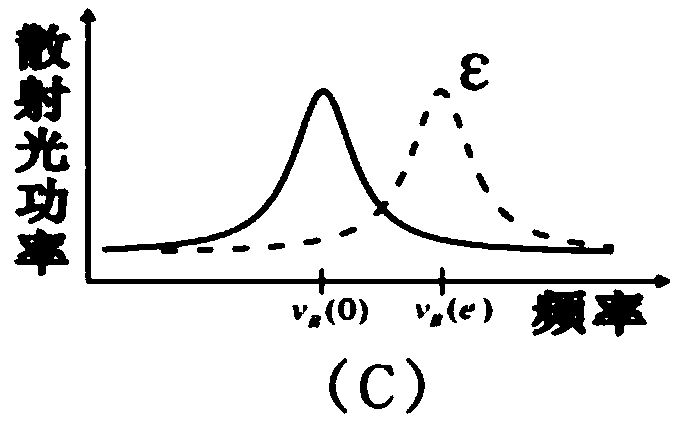
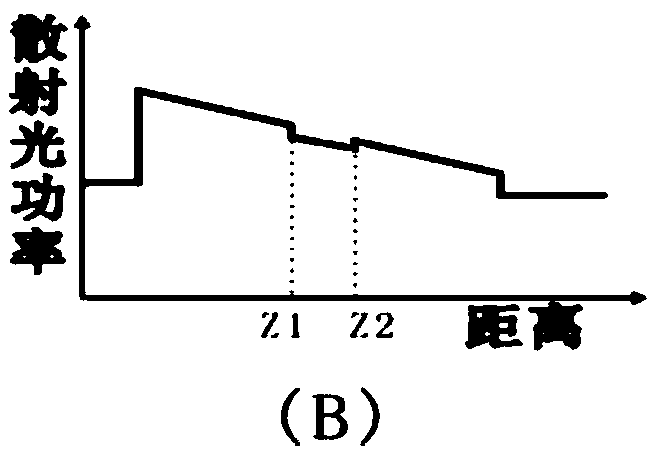
Intrusion detection and location method of distributed fiber optic fence based on φ-otdr
The invention discloses a distributed optical fiber fence intrusion detection and location method based on a phi-OTDR (Optical Time Domain Reflectometer), and the method comprises the following steps of: firstly, subtracting an acquired ith signal by an acquired (i-1)th signal to obtain a preprocessing monitoring signal; secondly, carrying out at least four-layer wavelet decomposition on the preprocessing monitoring signal by adopting a plurality of wavelet functions; thirdly, judging whether actual intrusion exists according to the consistency of distribution positions of maximum-wavelet mode maximums in all scale signals; fourthly, judging that the actual intrusion exists if the distribution positions of the maximum-wavelet mode maximums in at least three scale signals are consistent; fifthly, corresponding multiplying the scale signals in which the intrusion exists and the distribution positions of the maximum-wavelet mode maximums are consistent to obtain a composite signal of which pseudo maximums are inhibited and mode maximums at a catastrophe point are enhanced, using a position corresponding to the maximum-mode maximum in the composite signal as a position of the determined intrusion point, determining the intrusion generation and the intrusion position by combining various composite signal judgment results of wavelet multi-scale analysis according to the majority voting criterion.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
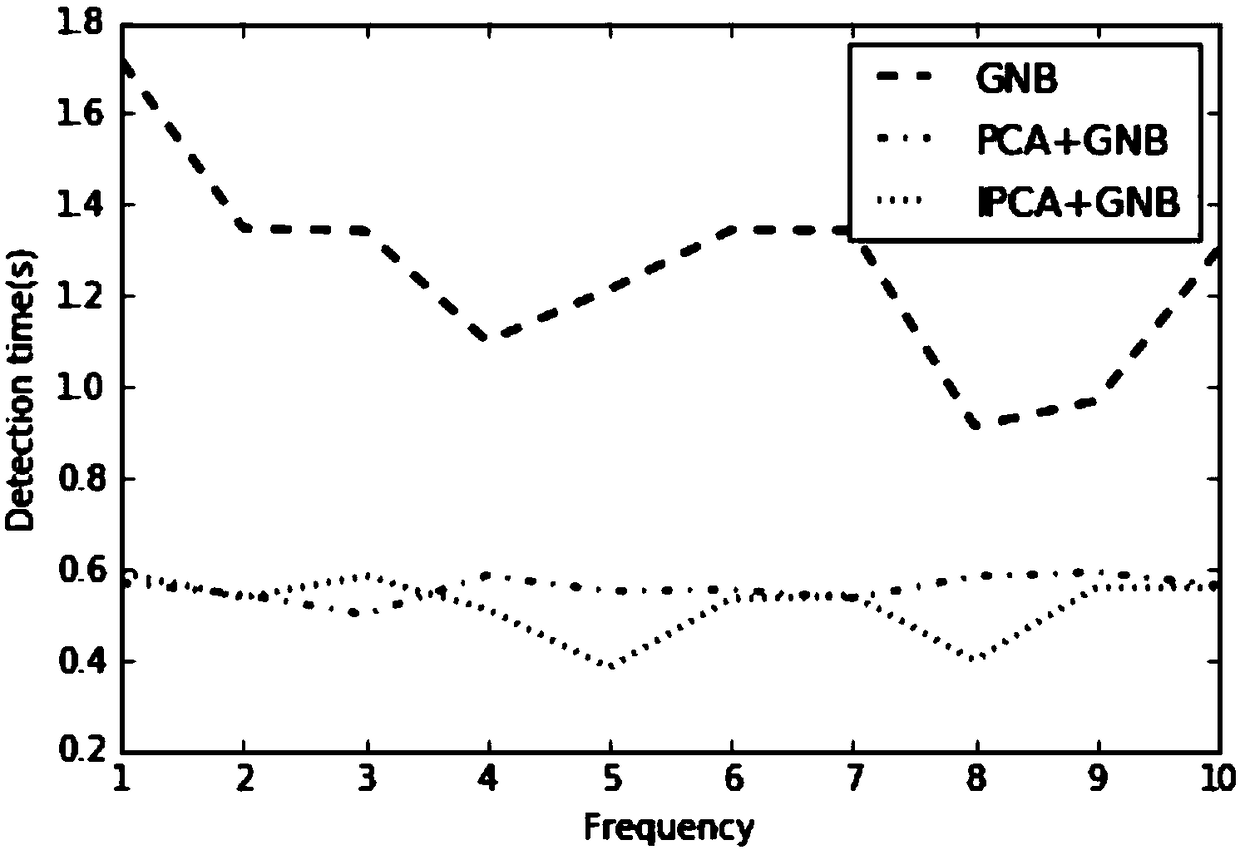
Network intrusion detection method on the basis of combining PCA and Bayesian
InactiveCN108632278ARapid Intrusion DetectionImplement intrusion detectionTransmissionData setDimensionality reduction
The invention discloses a network intrusion detection method on the basis of combining PCA and Bayesian. The invention is capable of realizing fast and effective detection of common and conventional types of attacks and new types of attacks, and the detection time is short and the correct rate is high. The invention firstly applies PCA to the training data set and the test data set to obtain the dimension-reduced training data and test data so as to reduce the model training time and detection time of the Bayesian classifier, and then adopts the Bayesian classifier with the fastest detection time for intrusion detection to achieve rapid detection. At the same time, the invention also improves the PCA, and improves the correct rate of detection, so that the method provided by the inventionis efficient in both detection time and detection accuracy.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
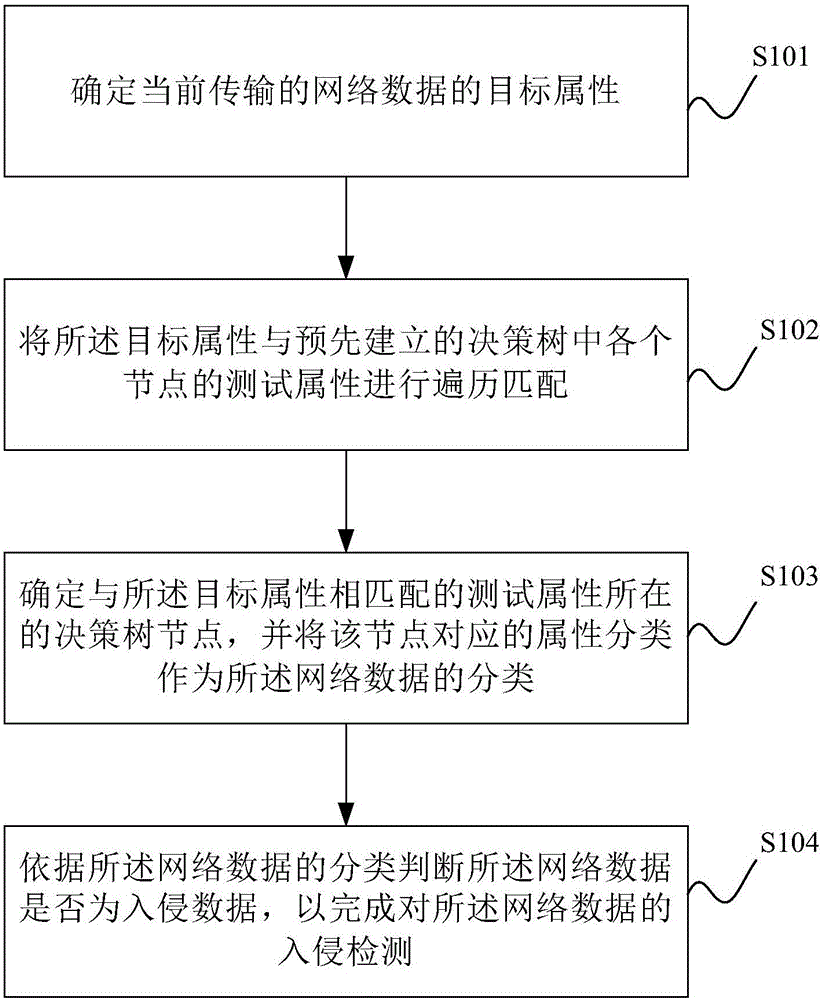
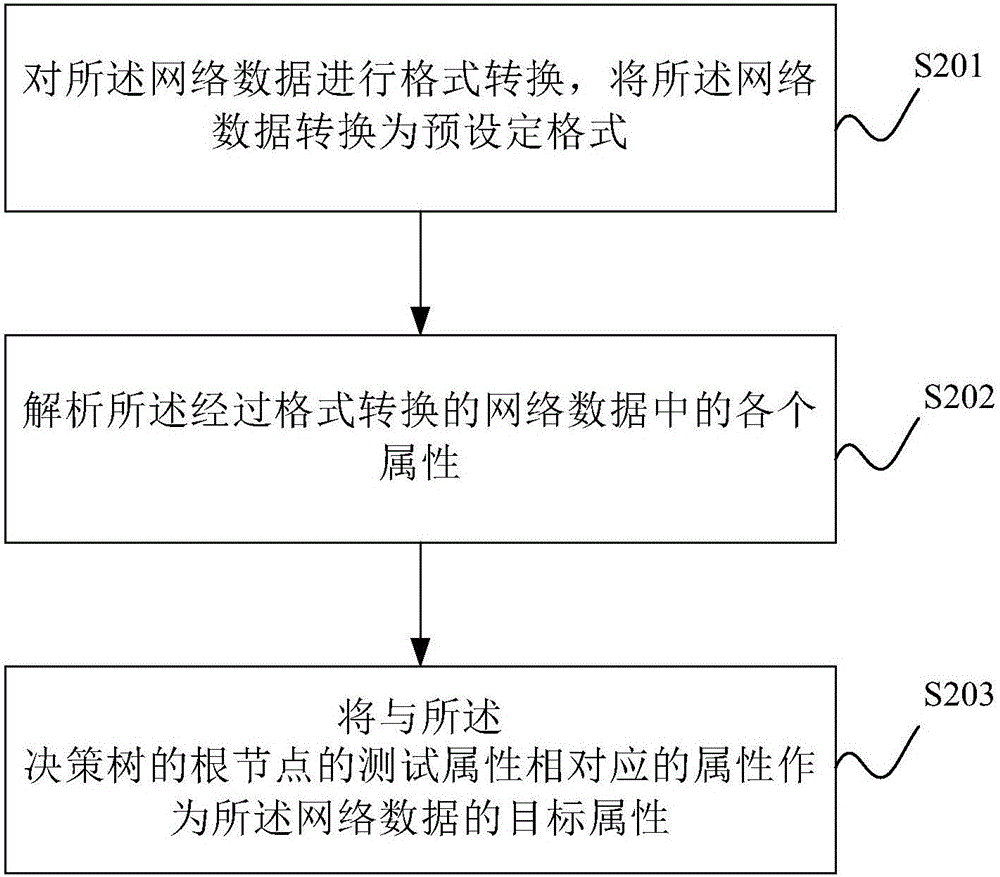
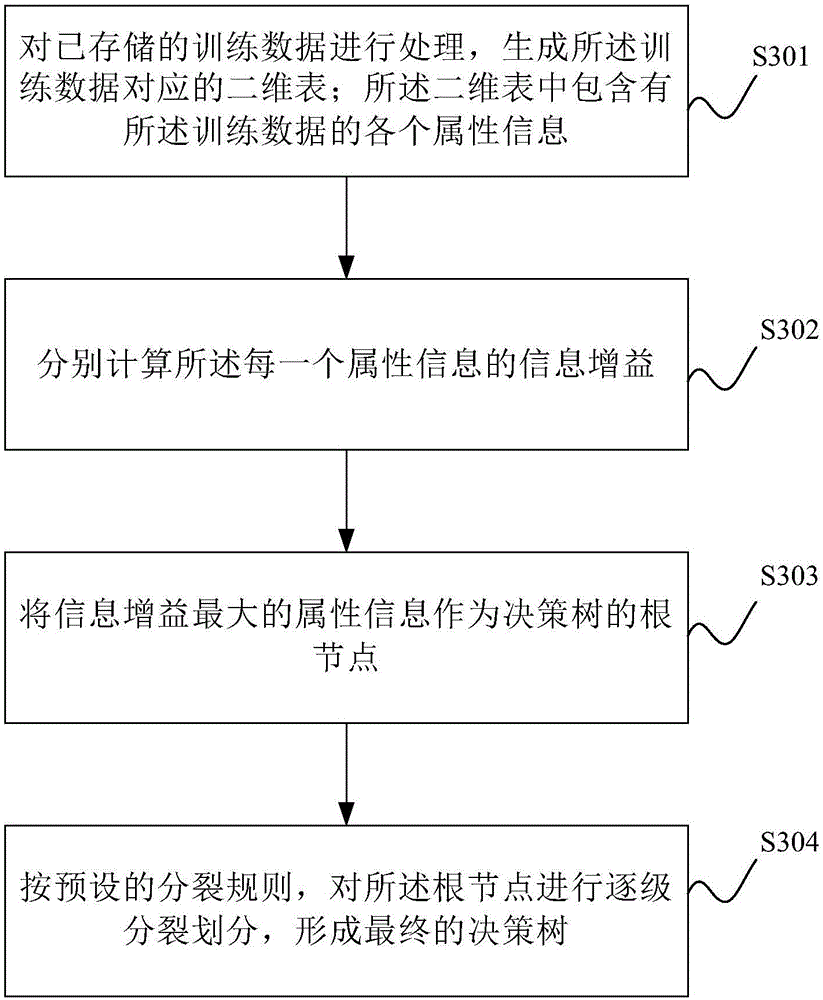
Invasion detection method and system
InactiveCN106603538AImplement intrusion detectionImprove protectionTransmissionNetwork dataDecision tree
The invention provides an invasion detection method. For network data presently transmitted to a user computer network, traversal matching for target attributes of the network data and test attributes of each node of a pre-established decision tree is firstly carried out, classification of the network data is determined, the pre-established decision tree is generated through processing training data of the network invasion data, and categories corresponding to nodes correspond to different invasion types. The method is advantaged in that whether the classification network data is invasion data is determined, network data invasion detection is realized, a detection process is more effective, and protection on a computer network of the user can be better realized.
Owner:BEIJING AN XIN TIAN XING TECH CO LTD
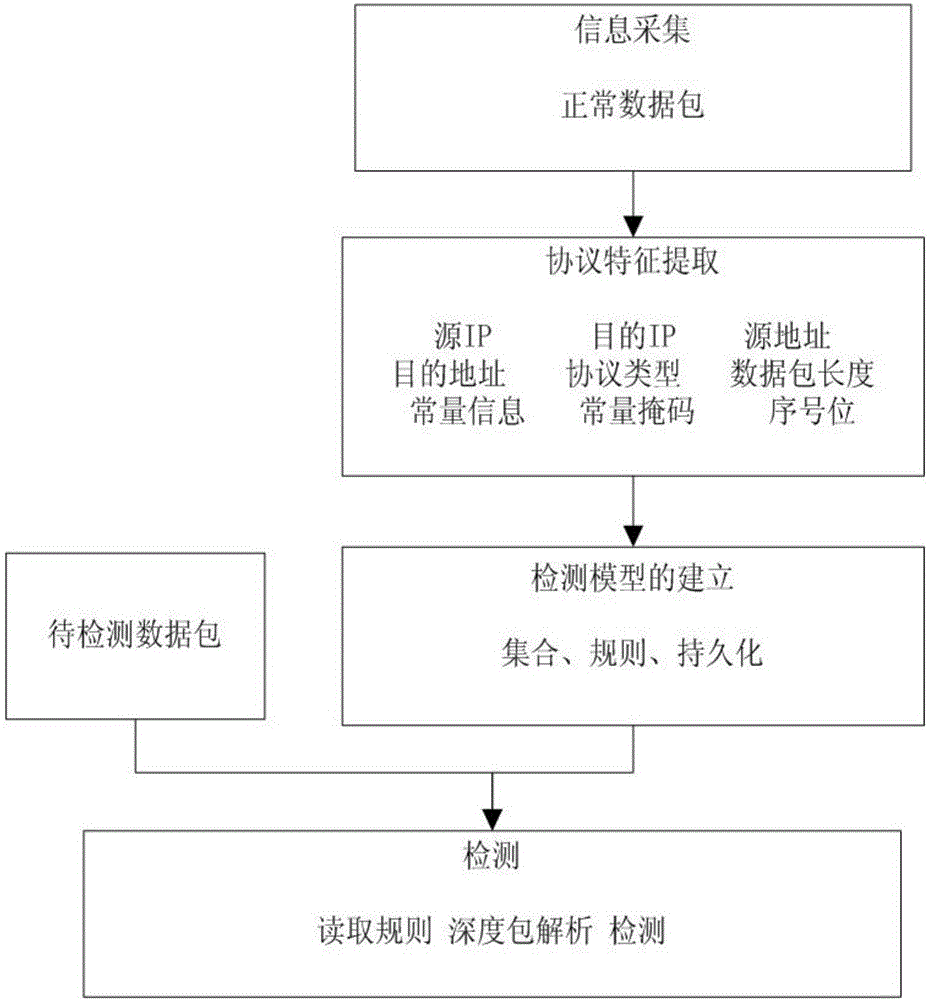
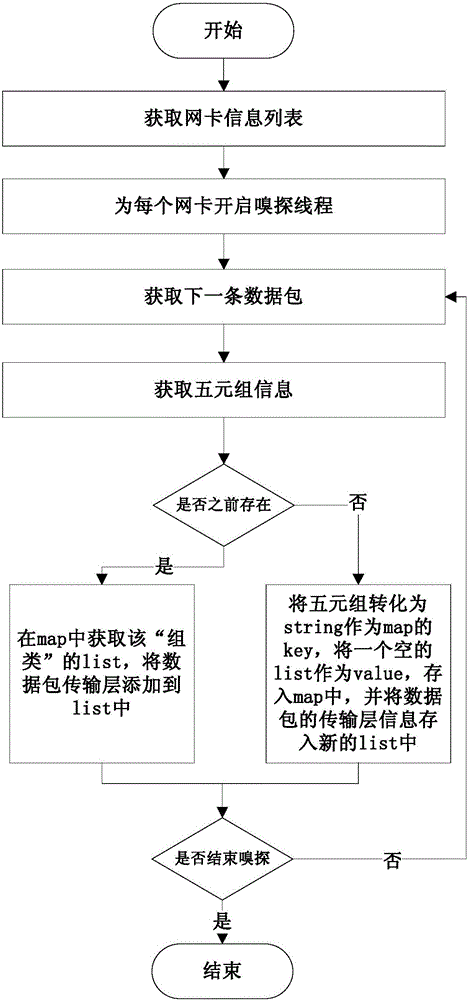
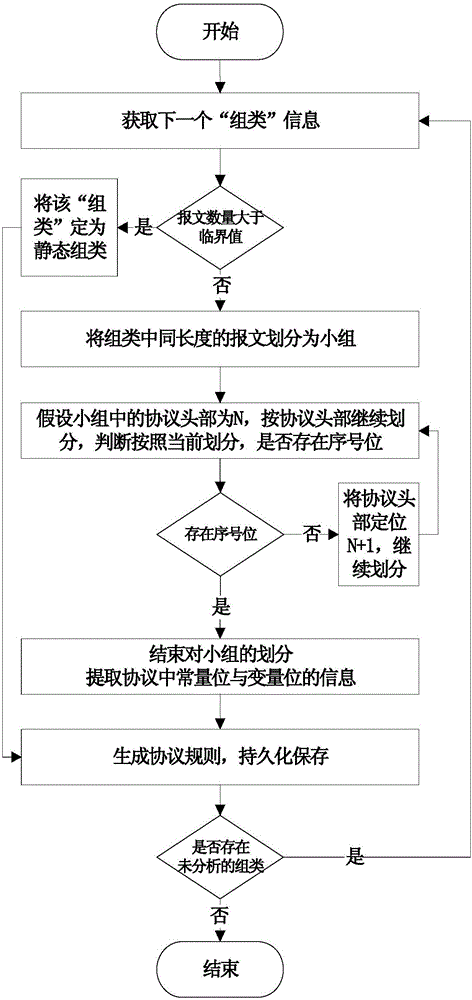
Intrusion detection method for self-learning protocol rule
The invention relates to an intrusion detection method for a self-learning protocol rule. The method mainly comprises the steps that normal data flow is collected, divided, clustered and subjected to protocol format extraction. A quintuple protocol rule is generated and stored permanently. In the detecting process, rule information is read, a quintuple rule mapping table is generated, a data package is compared with all rules in sequence, and data package and depth package analysis is carried out. Compared with the prior art, the method does not depend on a specific protocol, the protocol format needing to be detected can be obtained through self learning, depth package analysis is carried out, high accuracy is achieved, the technology is simple, and popularization is easy.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
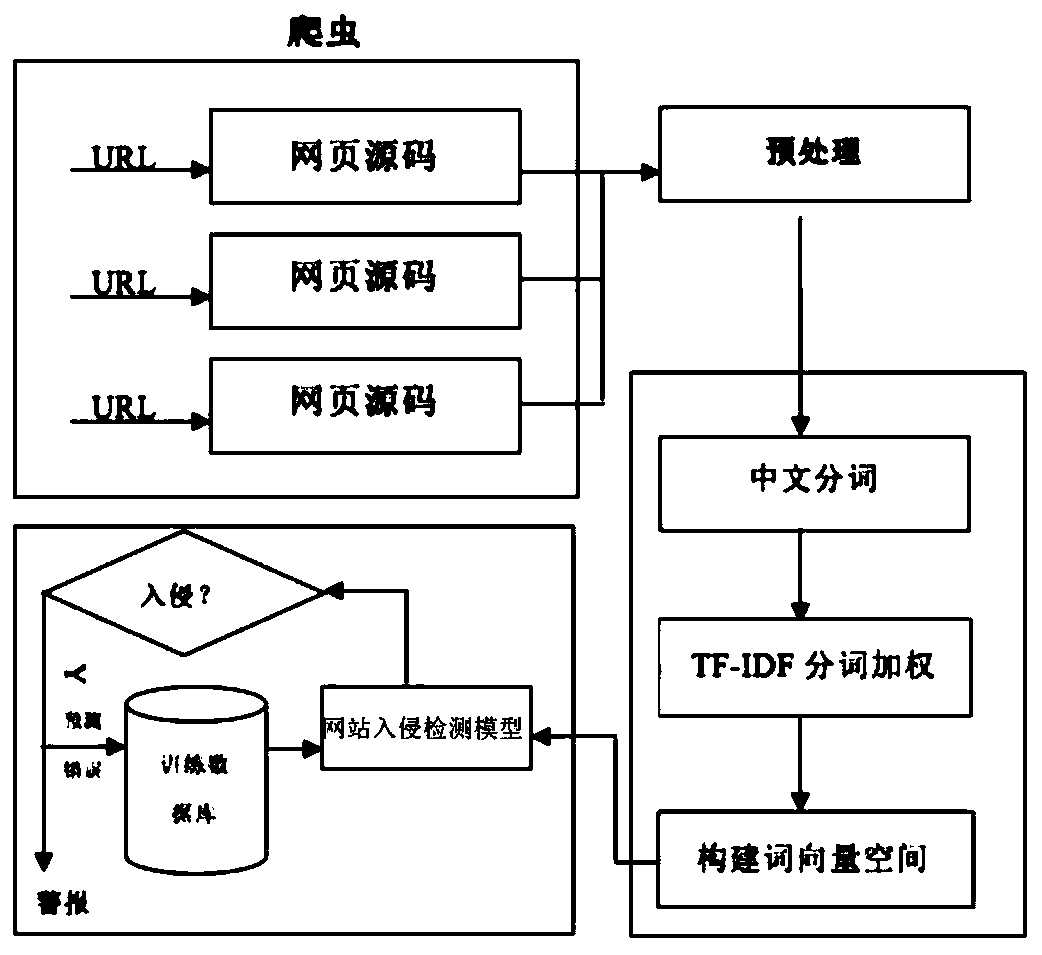
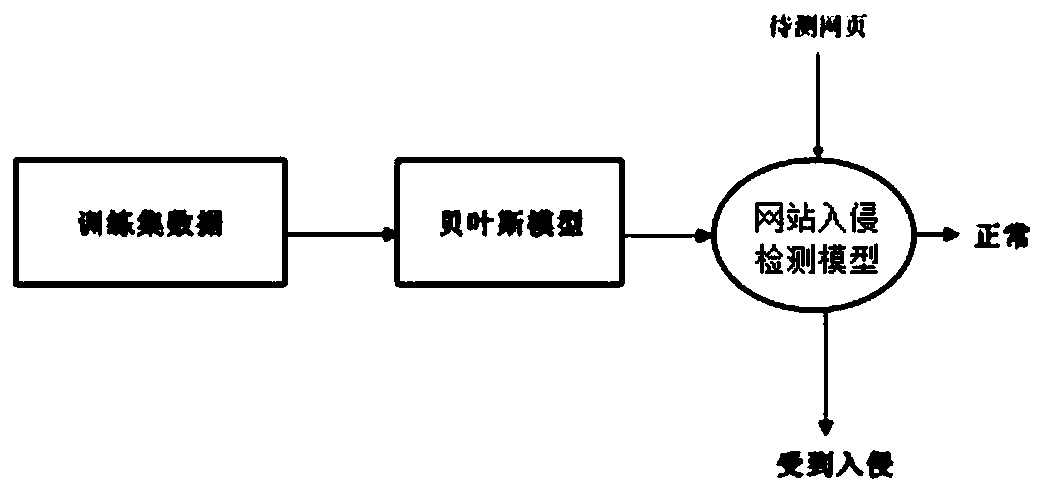
Word vector webpage intrusion detection method based on semantic analysis
PendingCN110191096AImprove relevanceImprove recognition accuracyWeb data indexingSemantic analysisTf–idfAlgorithm
The invention provides a word vector webpage intrusion detection method based on semantic analysis, which relates to the field of webpage attack detection, and comprises the following steps: 1) crawling webpage source codes corresponding to URLs of websites, screening and classifying the webpage source codes and taking the webpage source codes as a training set; 2) extracting Chinese character strings of all webpage source codes in the training set to perform word segmentation processing; 3) respectively carrying out keyword screening on word segmentation processing results and constructing akeyword library; 4) constructing a word vector of the keyword, and performing normalization processing; 5) calculating the weight in combination with the normalized TF-IDF to establish a weight word vector space, 6) training a webpage intrusion detection model, 7) judging whether the webpage to be detected is invaded or not through the model. The invention provides a webpage intrusion detection method for judging whether a webpage is maliciously invaded by vocabularies by utilizing a model.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY
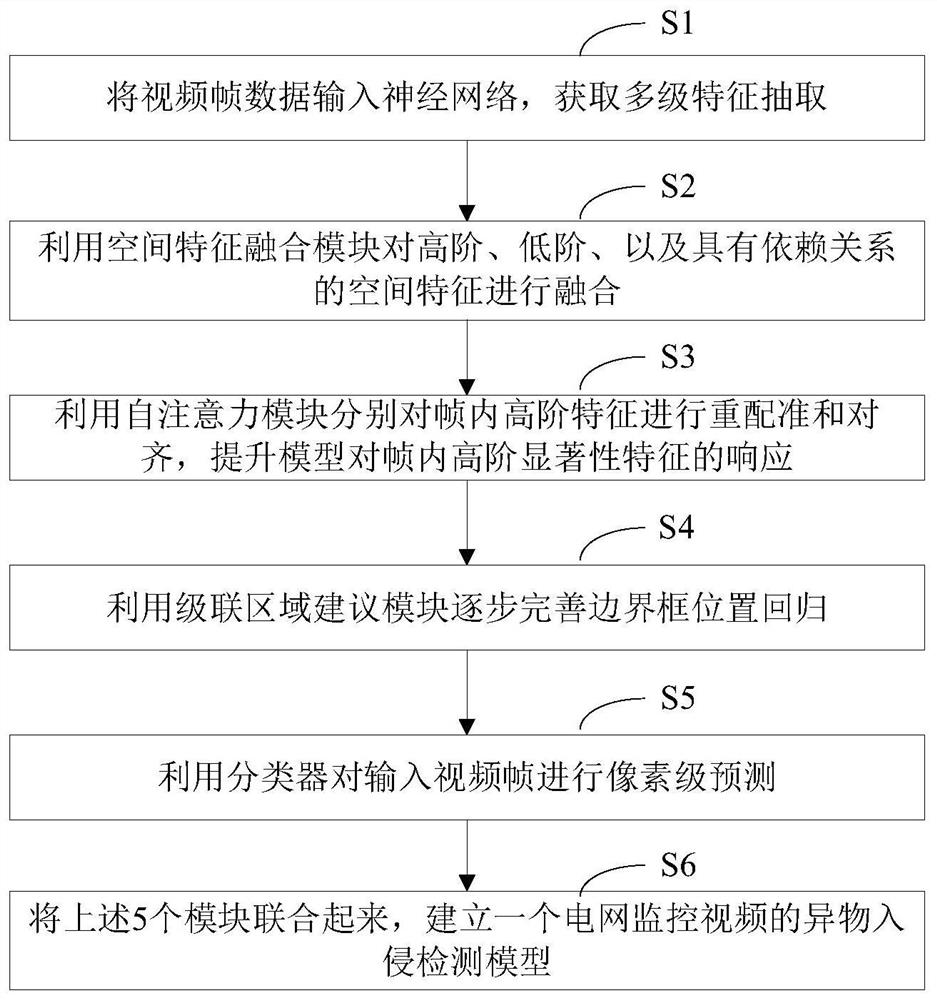
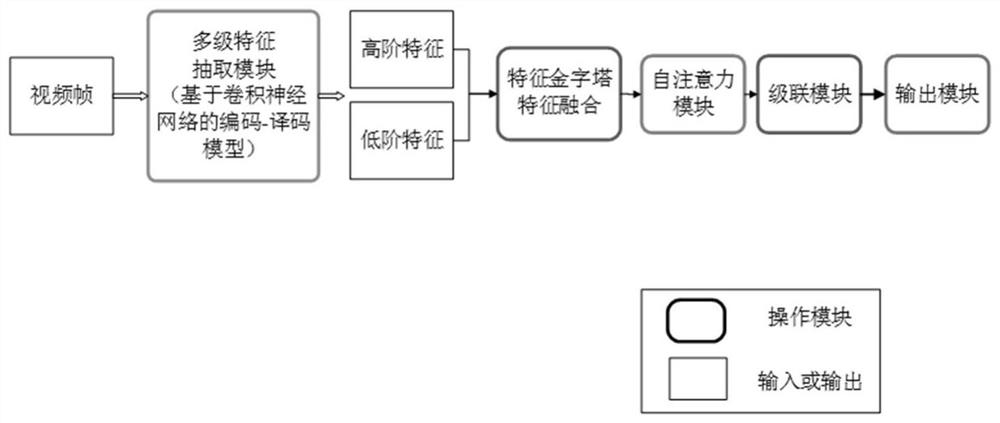
Intelligent power grid foreign matter intrusion detection method and system based on visual perception
PendingCN112464851AImplement intrusion detectionSolve technical problems of precisionCharacter and pattern recognitionNeural architecturesVideo monitoringPower grid
The invention discloses an intelligent power grid foreign matter intrusion detection method and system based on visual perception. According to the method, intelligent power grid foreign matter intrusion detection is completed based on intelligent power grid video monitoring data and an intrusion object detection model; the construction method of the intrusion object detection model comprises thefollowing steps: step 1, carrying out multi-level feature extraction on input video frames with a sequential relationship to generate a high-order feature map and a low-order feature map; step 2, performing feature fusion by utilizing the up-sampling of the feature map and the cascade operation of the feature map along the channel dimension direction; 3, using a self-attention mechanism, and obtaining processed features; 4, obtaining a binary classification result and a coordinate position of the object belonging to the target or the background through a cascade module; and step 5, outputtinga pixel-level classification result by using a classifier to realize pixel-level detection. According to the invention, the pixel-level classification task of foreign matter intrusion detection of thesmart power grid can be completed, and the technical problem of model precision in the prior art can be solved.
Owner:STATE GRID SHAANXI ELECTRIC POWER RES INST +2
Multilayer internal and external network data interaction system applied to television station
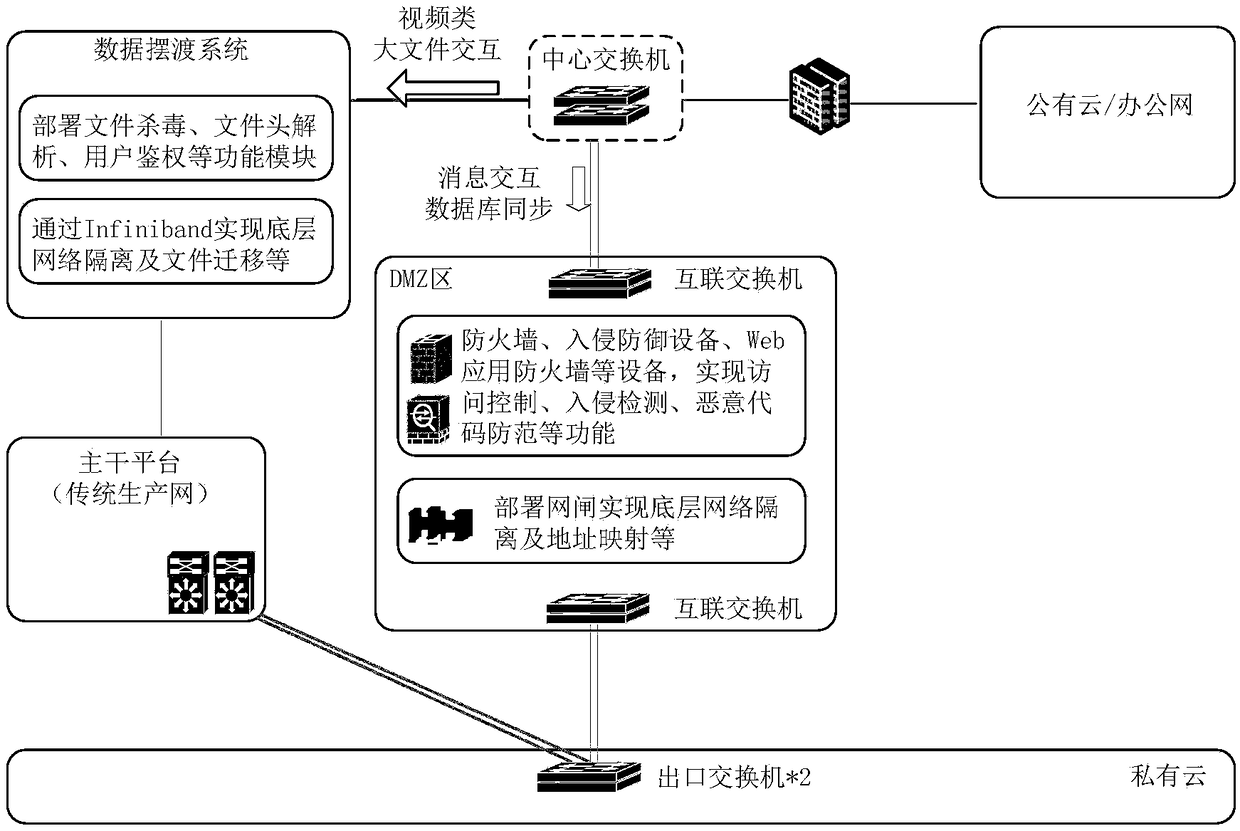
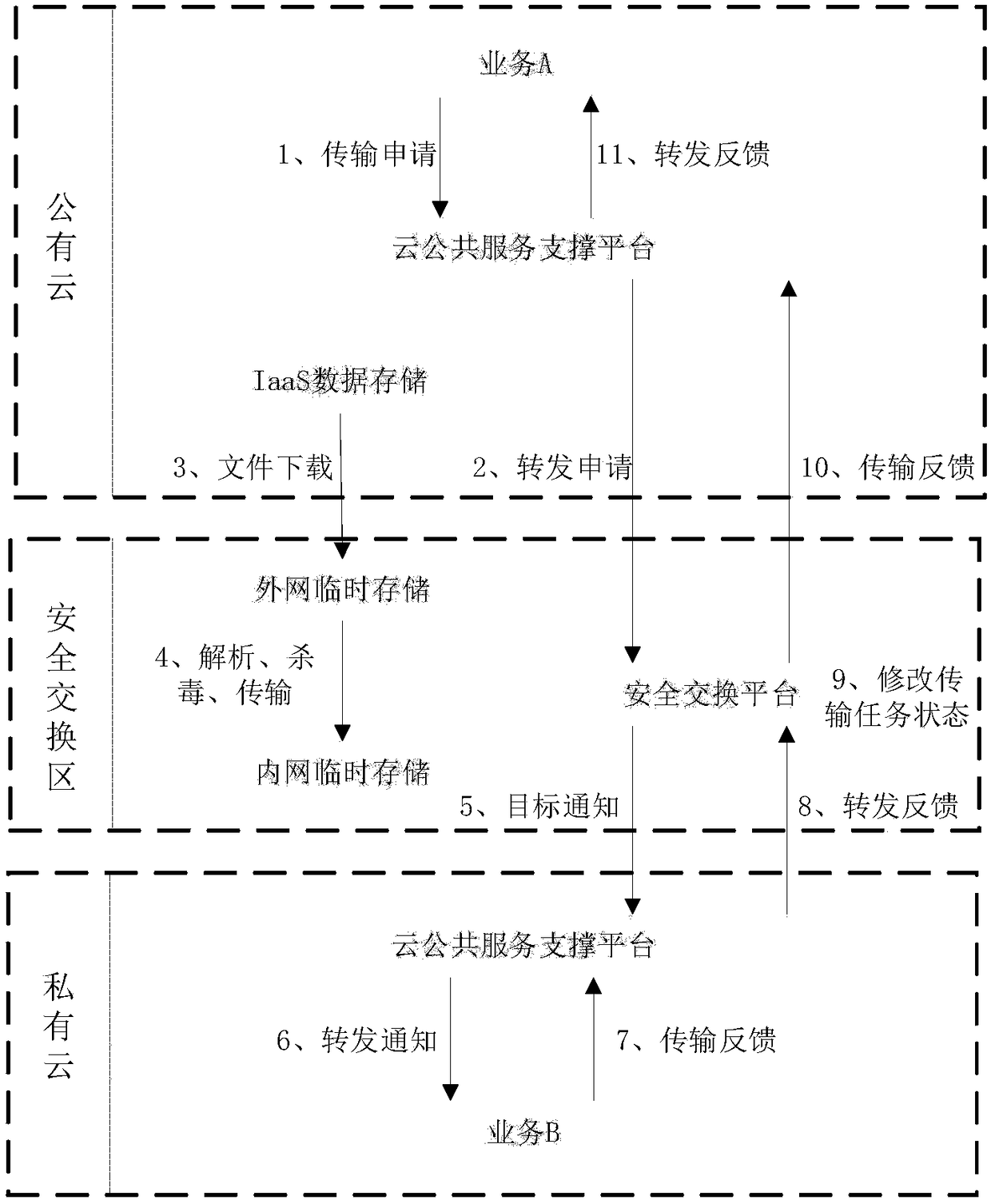
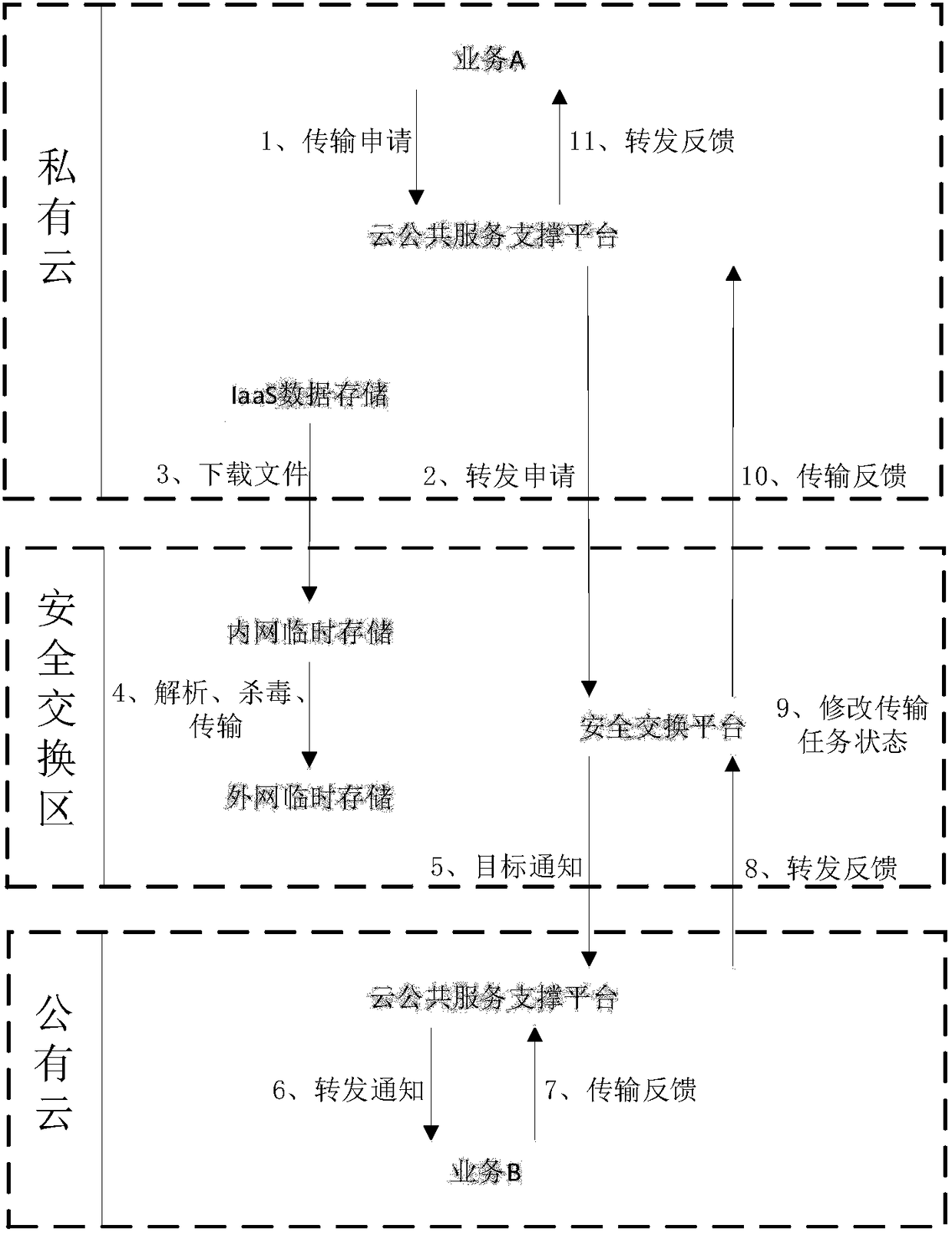
ActiveCN108234523AAchieve isolationImplement access controlTransmissionInteraction systemsTelevision station
The invention discloses a multilayer internal and external network data interaction system applied to a television station. The following structure is set between a private cloud and a public cloud. The structure comprises the fact that exit switches connected with the private cloud are connected with a central switch through a backbone platform of the television station and a data ferry system, and then the central switch is connected with the public cloud. A private cloud and public cloud message interaction database synchronization structure comprises the fact that the private cloud is connected with the central switch through the data ferry system of a DMZ, wherein the DMZ comprises interconnection switches and a gateway, and the data ferry system comprises a file virus kill module, afile header analysis module and a user authentication module consistent with an infiniband protocol. The internal and external network media data interaction is realized through the secure ferry system. The internal and external network message interaction is realized through the DMZ.
Owner:JIANGSU BROADCASTING CORPORATION
Full-tunnel safety monitoring system and implementation method
InactiveCN110686609AReal time monitoringImprove securityHeight/levelling measurementUsing optical meansEnvironmental geologyReal-time computing
The invention relates to a full-tunnel safety monitoring system. The system comprises a GPS system and an optical fiber strain monitoring system which are electrically connected with a data acquisition center, and a strain monitoring optical cable which is electrically connected with the optical fiber strain monitoring system and is buried below a tunnel monitoring area. The optical fiber strain monitoring system is an optical fiber analyzer, and the GPS system is used for monitoring the overall settlement of a tunnel. The optical fiber strain monitoring system realizes tunnel omnibearing strain monitoring through continuous optical cables and provides accurate positioning, the measured deformation is relative deformation, and deformation quantities can be accumulated. The system has highmonitoring precision, the early warning of large accident deformation of the tunnel can be achieved, the tunnel deformation direction can be judged, the intelligent degree is high, an abnormal condition can be accurately positioned, various means for alarming can be realized, the monitoring service life is long, the monitoring in the whole life cycle of the tunnel can be realized, the maintenancecost is low, and the later maintenance is nearly zero.
Owner:LASER RES INST OF SHANDONG ACAD OF SCI
Vehicle-mounted intrusion detection method and system based on ECU signal characteristic identifiers
ActiveCN110636048AImplement intrusion detectionData switching networksIn vehicleElectronic properties
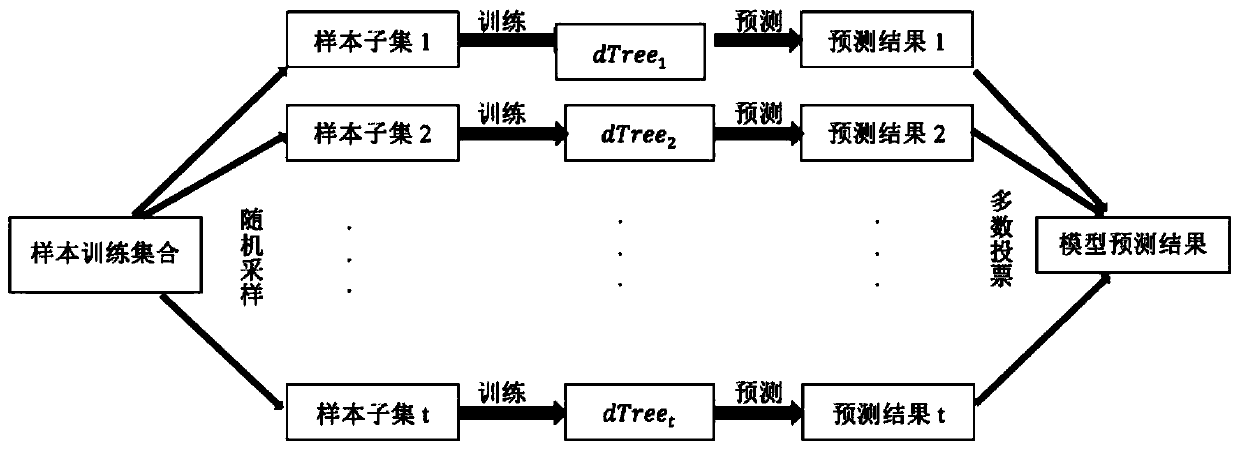
The invention provides a vehicle-mounted intrusion detection method based on ECU signal characteristic identifiers, in-vehicle electronic control unit (ECU) communication enables level changes to be generated in a CAN bus, and the level changes imply electronic characteristics which cannot be copied by an ECU. According to the method, inconsistent characteristics of signals generated by the ECU due to hardware inconsistency are considered, and the ECU is identified by utilizing the characteristics. The intrusion detection system capable of positioning and identifying the malicious ECU is realized by filling an extended identifier domain of a data extended frame with a section of fixed and same bit stream, analyzing signal characteristics in the bit stream, extracting entropy and other characteristics and message IDs, and learning by using a bagging decision tree algorithm.
Owner:EAST CHINA NORMAL UNIV +1
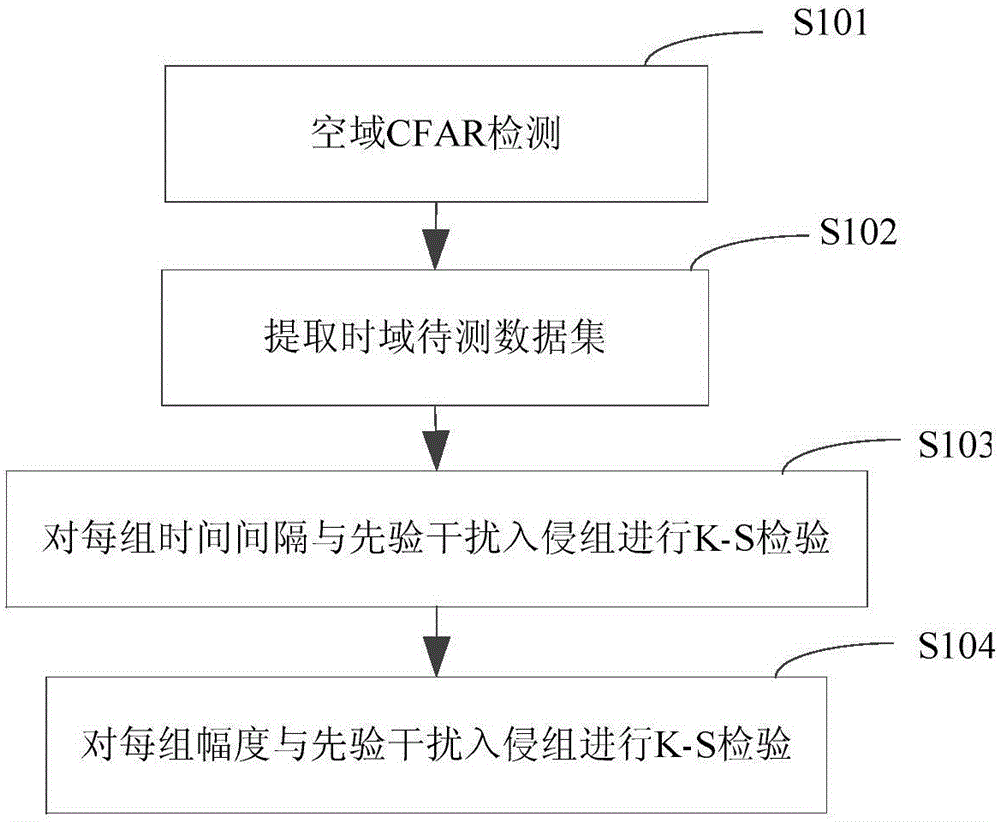
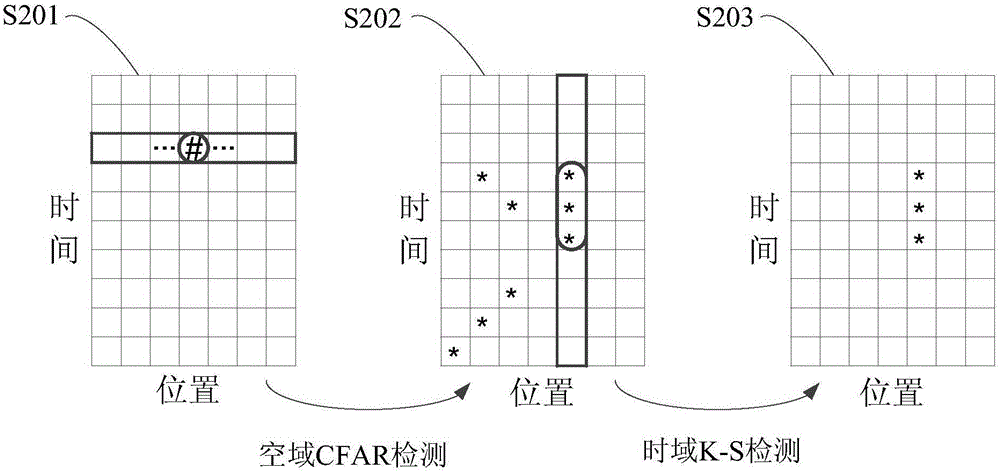
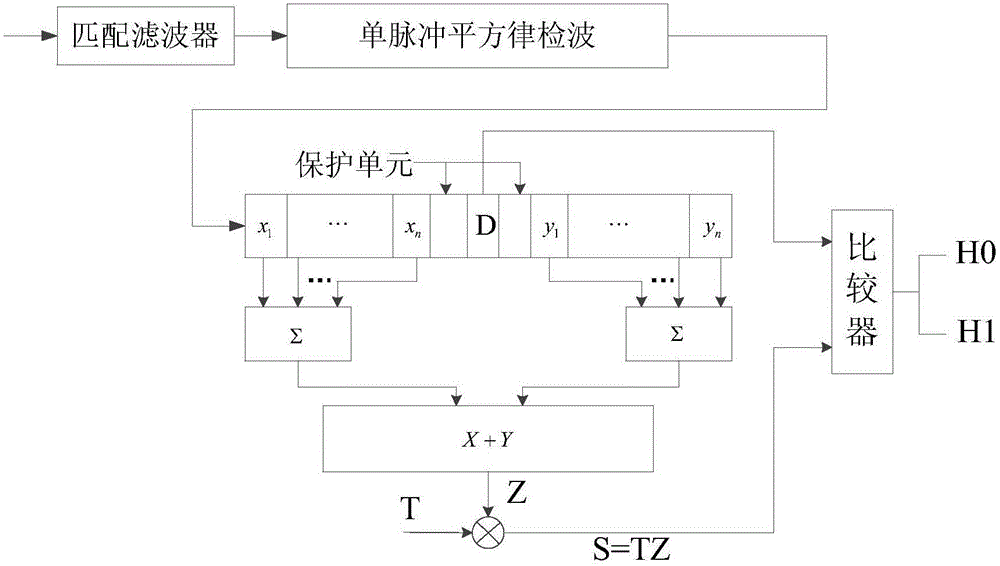
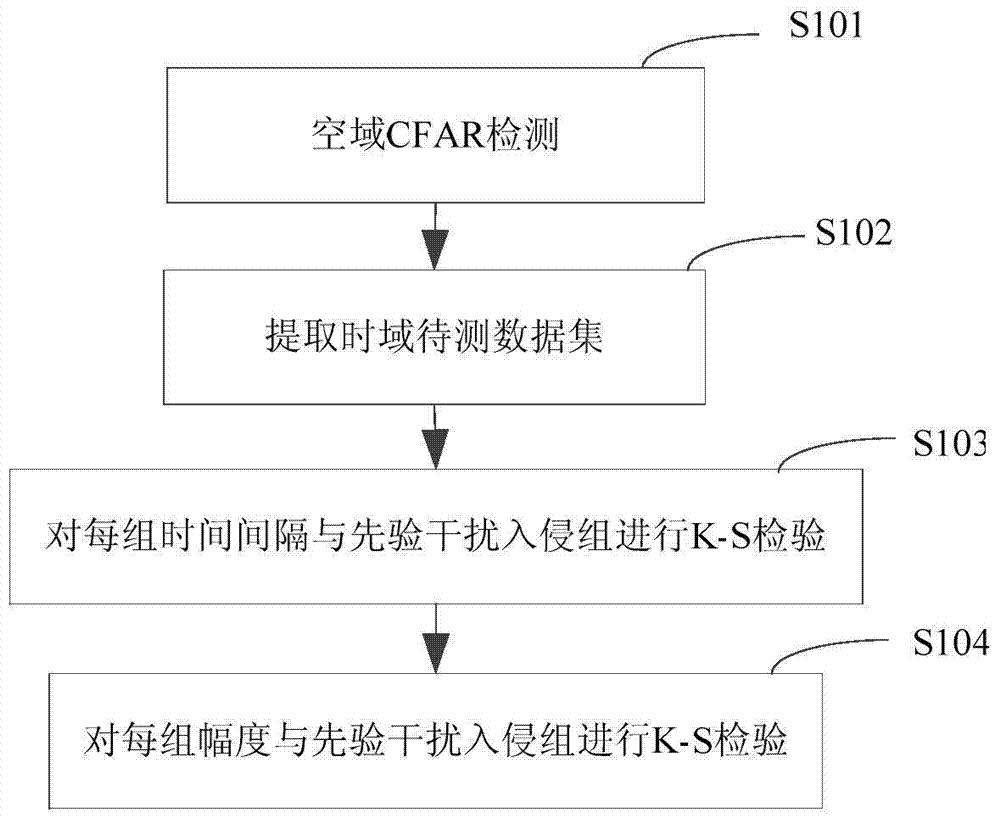
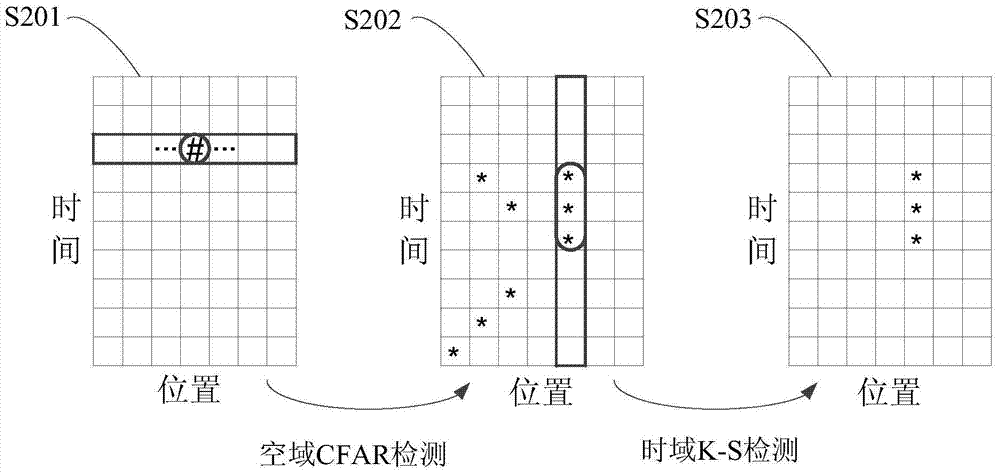
Fiber intrusion detection method using time-space 2D sparseness of vibration signals to represent K-S test
The invention provides a fiber intrusion detection method using time-space 2D sparseness of vibration signals to represent K-S test, and aims at a fiber intrusion early-warning system. The method comprises CFAR (Constant False Alarm Rate) detection is carried out on signals of different positions via the CFAR, time-domain K-S test is carried out on data, over-threshold CFAR data is grouped to obtain time-domain to-be-tested data sets, the time interval between data in each time-domain to-be-tested data set is compared with that of prior interference intrusion signals via K-S test, if distribution of the time interval is the same, the detected data set includes interference intrusion signals, and if distribution is different, amplitude K-S test is carried out, namely, the amplitude of data in each time-domain to-be-tested data set is compared with that of the prior interference intrusion signals via K-S test, if distribution of the amplitude is the same, the detected data set is an interference intrusion group, and otherwise, the set is a potential harmful intrusion group. The method detects the intrusion signals in the space-time 2D manner, influence of interference intrusion can rejected, and potential harmful intrusion information is obtained.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY +1
Internet-based e-commerce platform intrusion detection method and computer equipment
ActiveCN111324883AEnsure the effect of intrusion detectionImplement intrusion detectionDigital data protectionDigital data authenticationComputer networkThe Internet
The invention provides an internet-based e-commerce platform intrusion detection method and computer equipment, which can judge whether a first user terminal is an intrusion terminal or not based on afirst order feature vector of an output order and a second order feature vector of a target order when an electronic order in an electronic order information set is the output order. When an electronic order in an electronic order information set is an input order, whether a first user terminal is an intrusion terminal or not can be judged based on a user behavior track of a third user terminal interacting with the first user terminal. Thus, the intrusion terminal of the first user terminal can be judged based on the electronic order information, intrusion detection on the online e-commerce platform provided by the computer equipment is further realized, the intrusion detection effect on the online e-commerce platform is ensured, and the security of the privacy information of the user terminal interacting with the online e-commerce platform is ensured.
Owner:成都我行我数科技有限公司
Sequence attack detection method and device
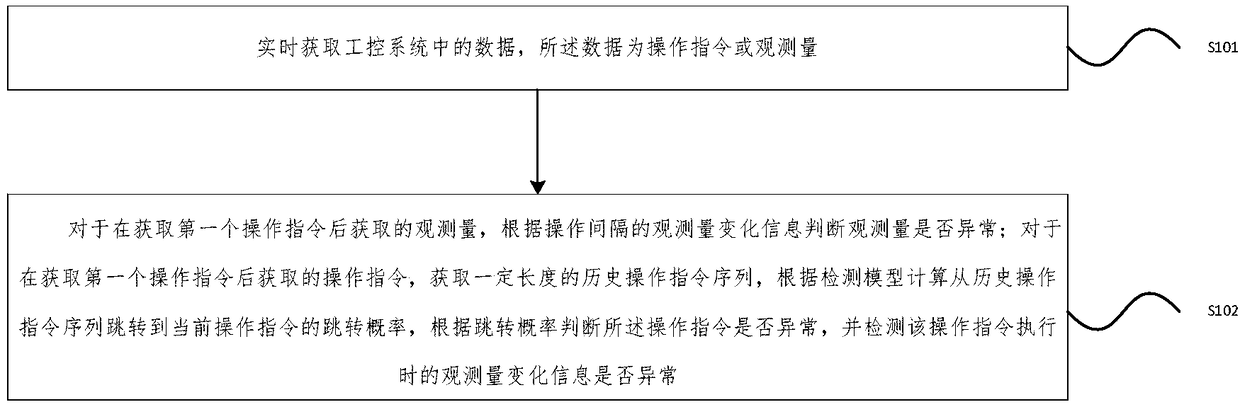
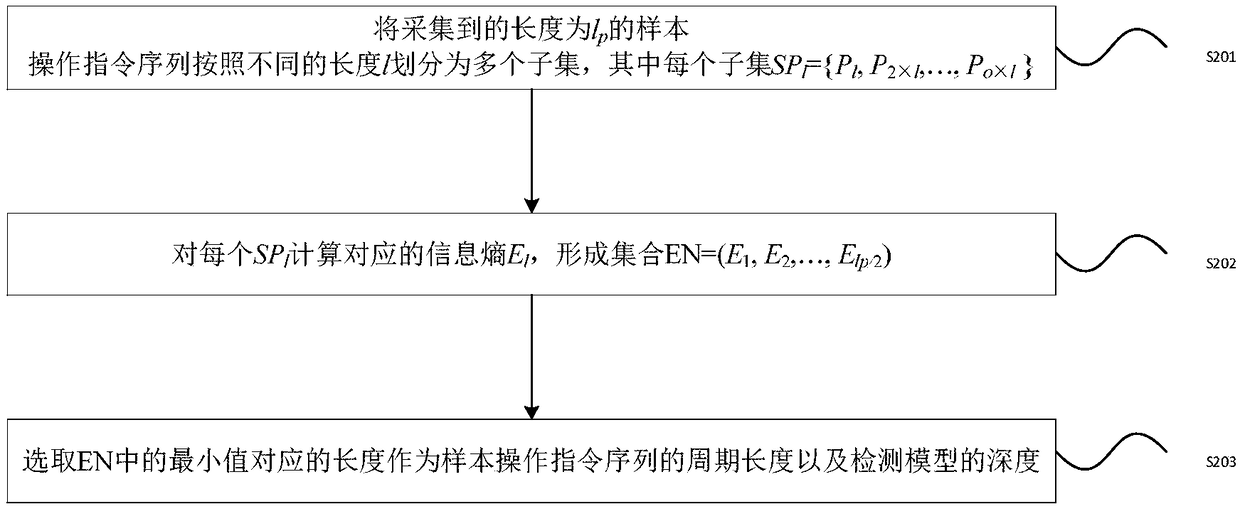
ActiveCN109344610AEfficient identificationHigh precisionPlatform integrity maintainanceControl flowInstruction sequence
The invention provides a detecting party and a device of a sequence attack, wherein the method comprises the following steps of: acquiring data in an industrial control system in real time; Whether the observed quantity is abnormal or not is judged according to the observed quantity change information of the operation interval for the observed quantity obtained after the first operation instruction is obtained. For an operation instruction obtained after the first operation instruction is obtained, obtaining a history operation instruction sequence of a certain length, calculating a jump probability of jumping from the history operation instruction sequence to the current operation instruction according to the detection model, judging whether the operation instruction is abnormal accordingto the jump probability, and detecting whether the observation quantity change information when the operation instruction is executed is abnormal. The embodiment of the invention effectively solves the problems that the operation sequence cannot be detected and the detection failure is caused by the false control flow data, improves the accuracy of the sequence attack detection, and realizes theintrusion detection of the whole operation flow.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method, device and system for network intrusion detection
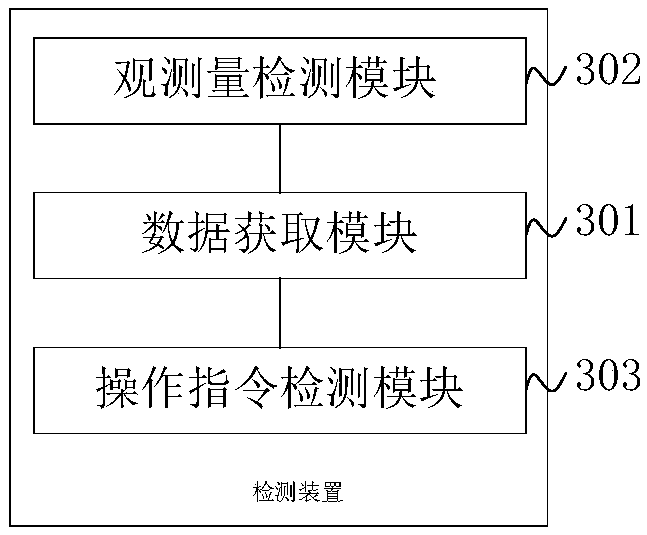
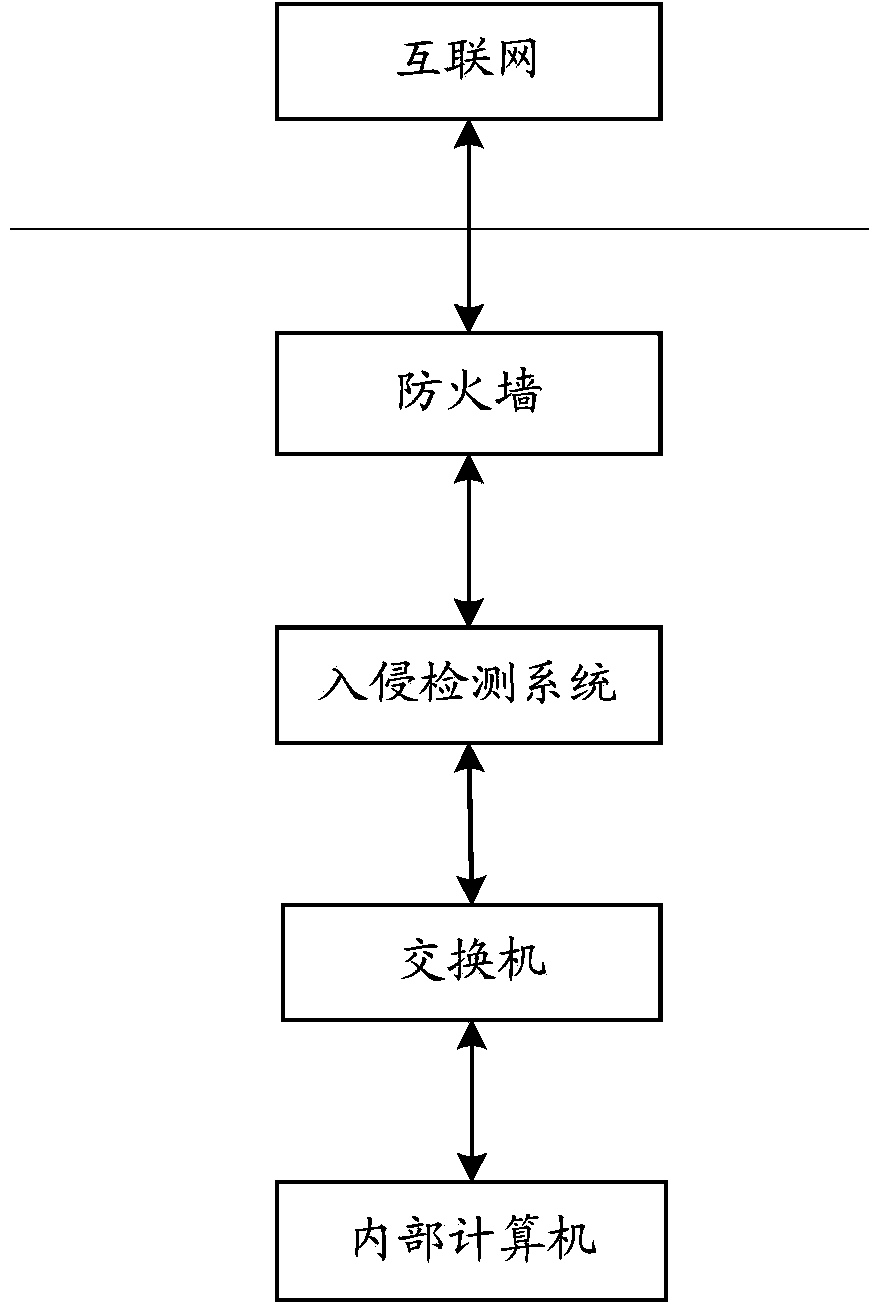
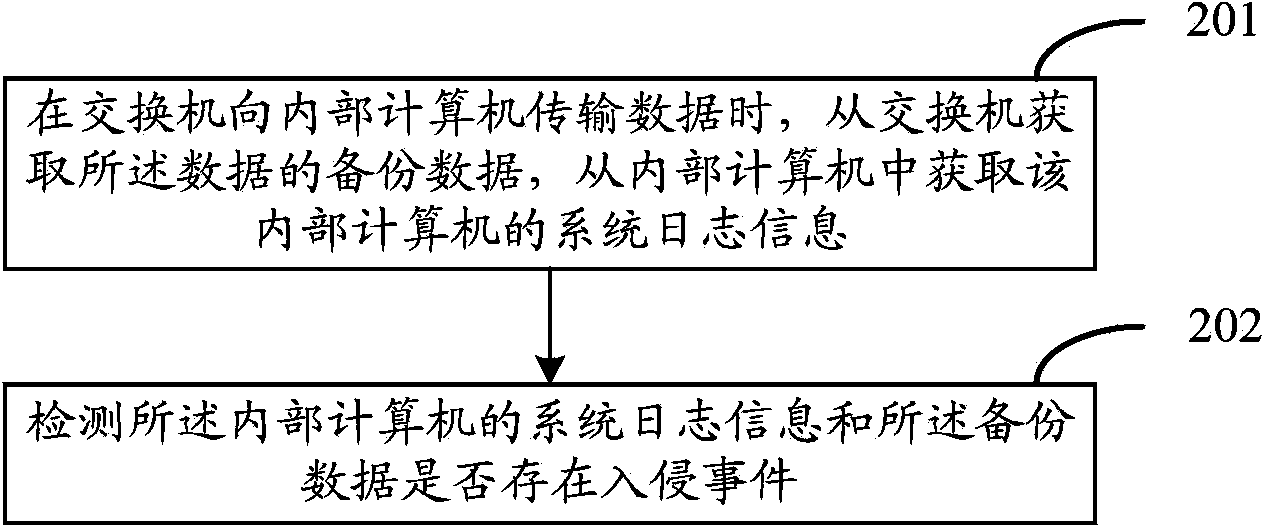
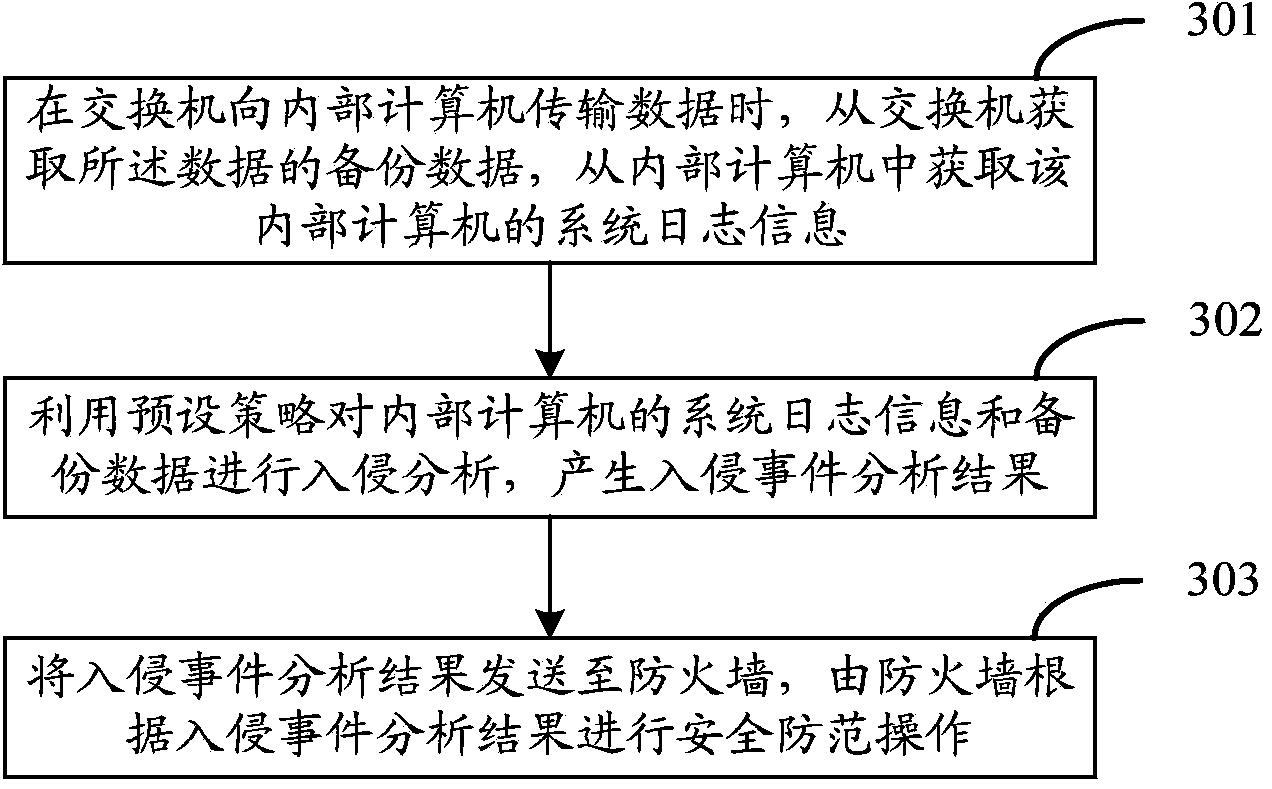
InactiveCN103618689AImprove efficiencyEnsure safetyData switching networksNetwork dataData transmission
The invention discloses a method, device and system for network intrusion detection. The method comprises the following steps: when a switch transmits data to an internal computer, backup data of the data is acquired from the switch, and system log information of the internal computer is acquired from the internal computer; and the system log information of the internal computer and the backup data are detected whether an intrusion event exists therein. According to the embodiment of the invention, the system log information of the internal computer and the network data are comprehensively utilized to carry out the network intrusion detection, and the accuracy and comprehensiveness of the network intrusion detection are improved. At the same time, according to the embodiment of the invention, the network intrusion detection method changes a convention method which progresses from the detection to the data transmission, and the network intrusion detection is realized while the timely transmission of the network data to the internal computer is ensure.
Owner:TVMINING BEIJING MEDIA TECH
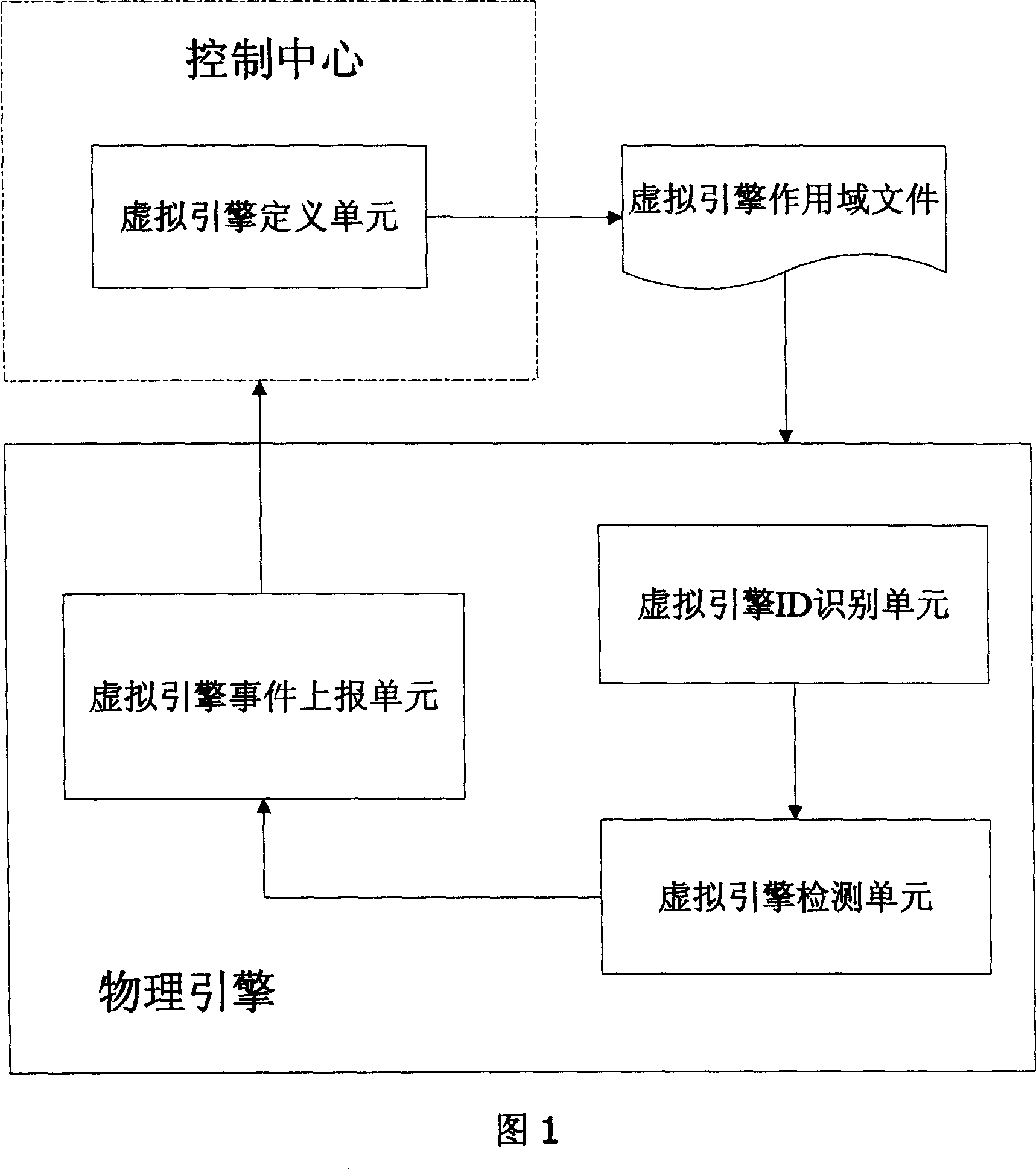
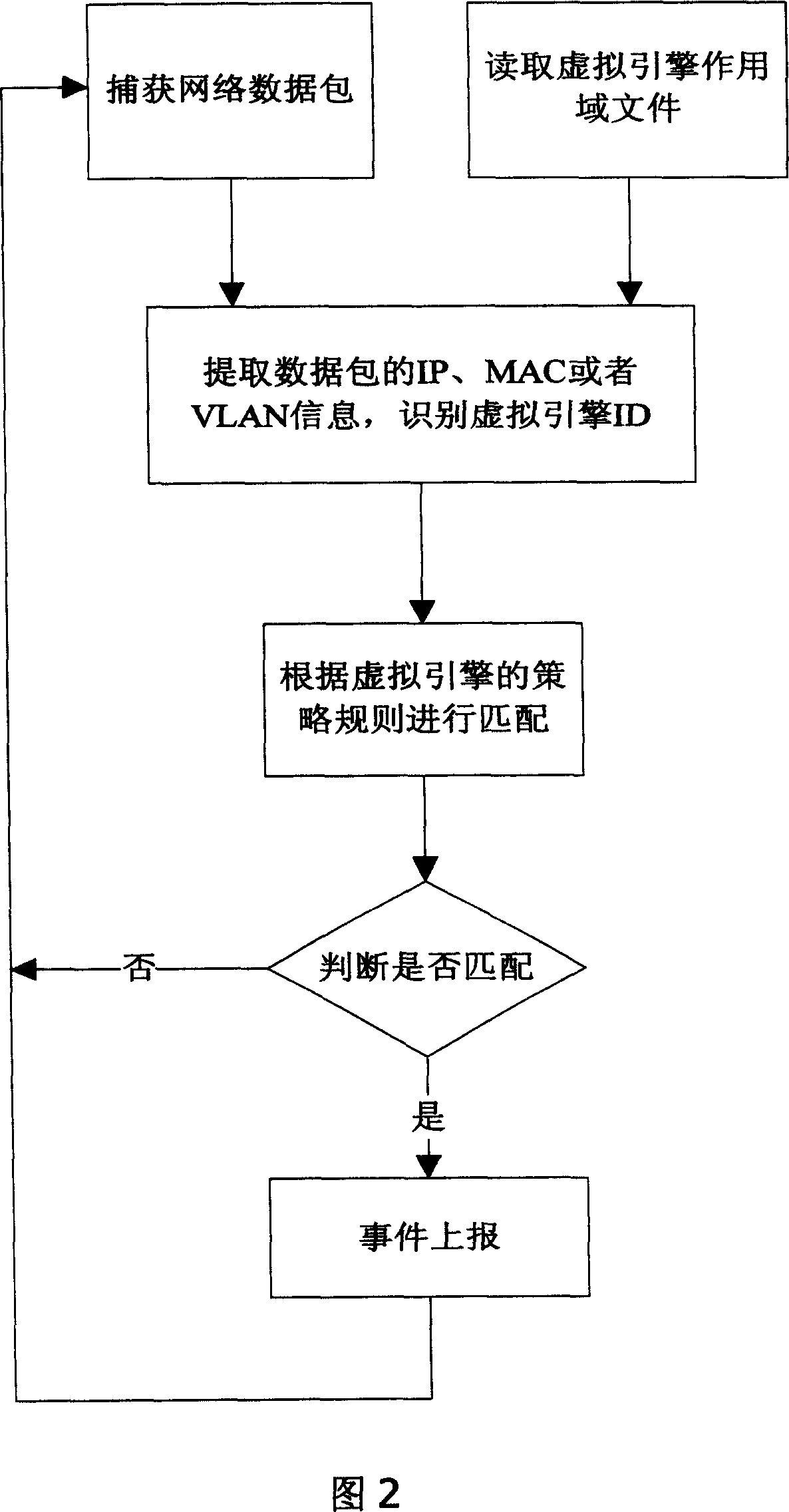
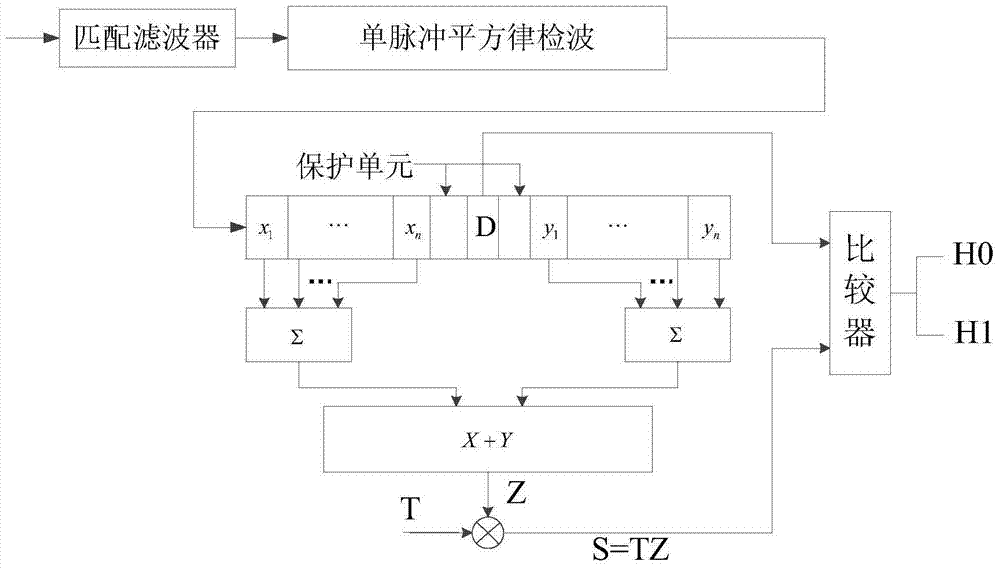
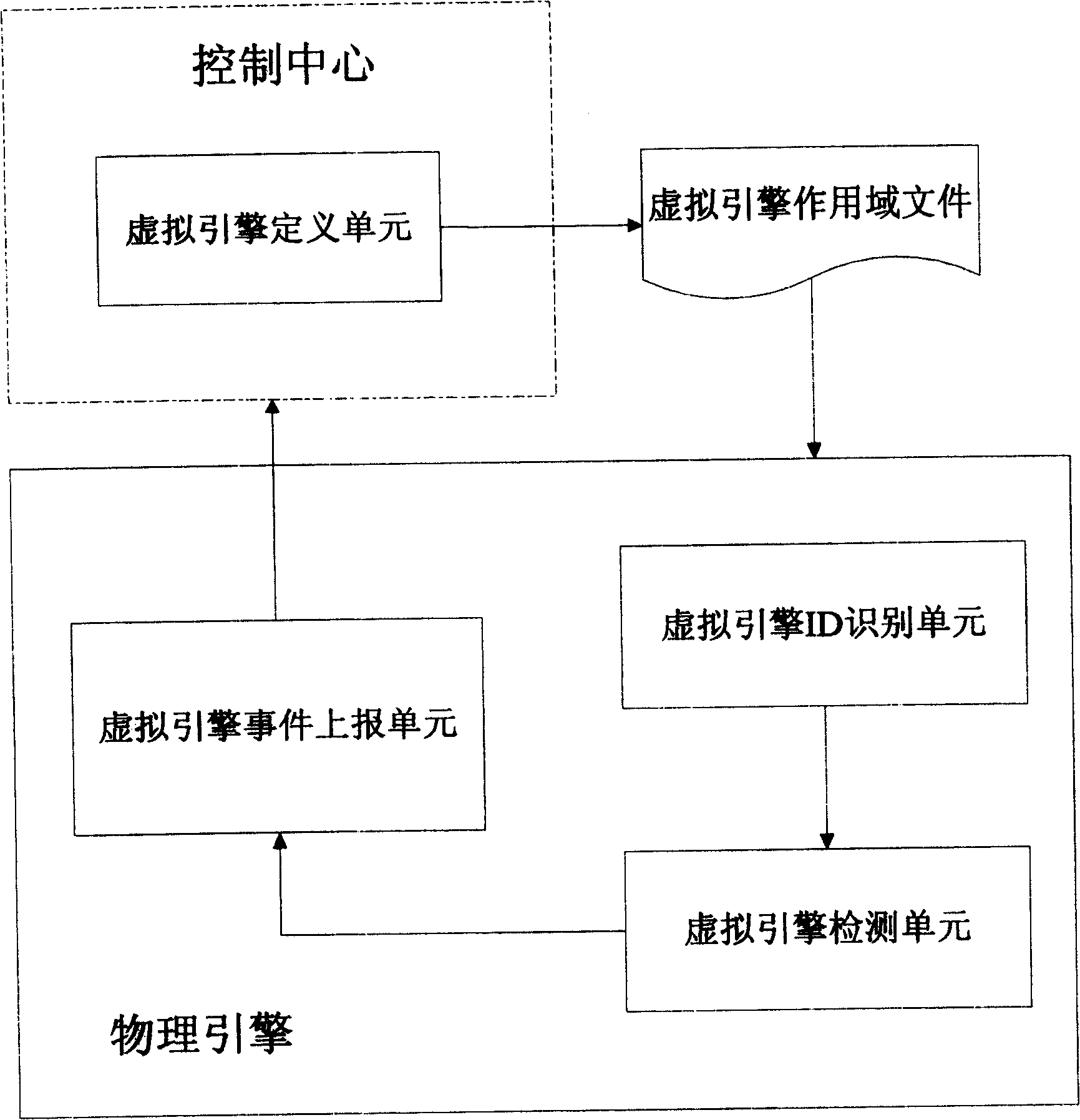
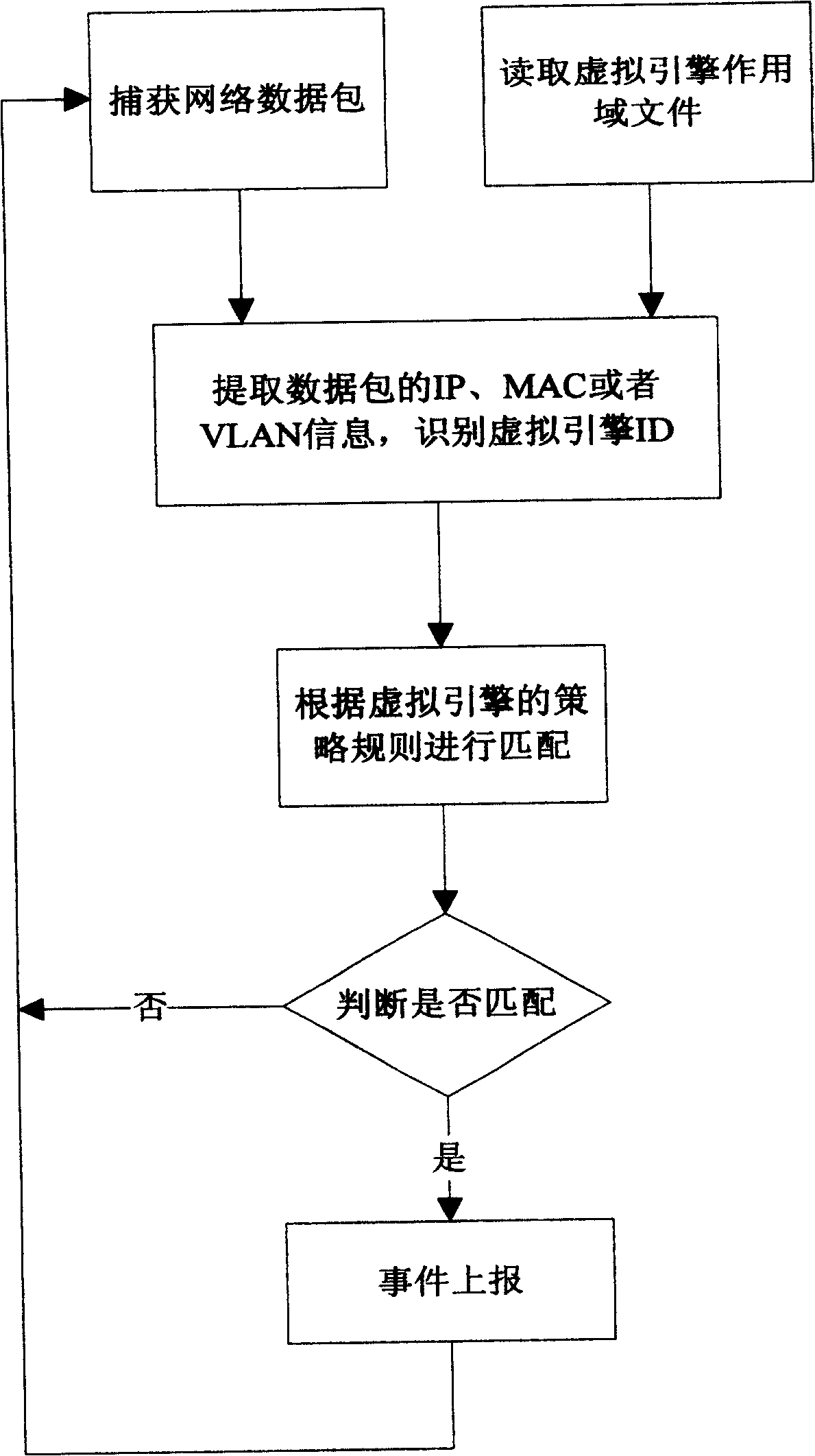
Method for implementing virtual engine technique for intrusion detection
InactiveCN1960293ALittle impact on performanceImplement intrusion detectionUser identity/authority verificationHardware monitoringPhysics engineIp address
The invention features the physical engine of an Intrusion Detection System that virtualizes multi engines, by which the classified protection can be made according to the network condition of client, VLAN TAG information, IP address information or MAC address information. On each virtual engine, different detection strategy and security strategy standard can be executed and set in order to implement the object-oriented intrusion detection.
Owner:BEIJING VENUS INFORMATION TECH +1
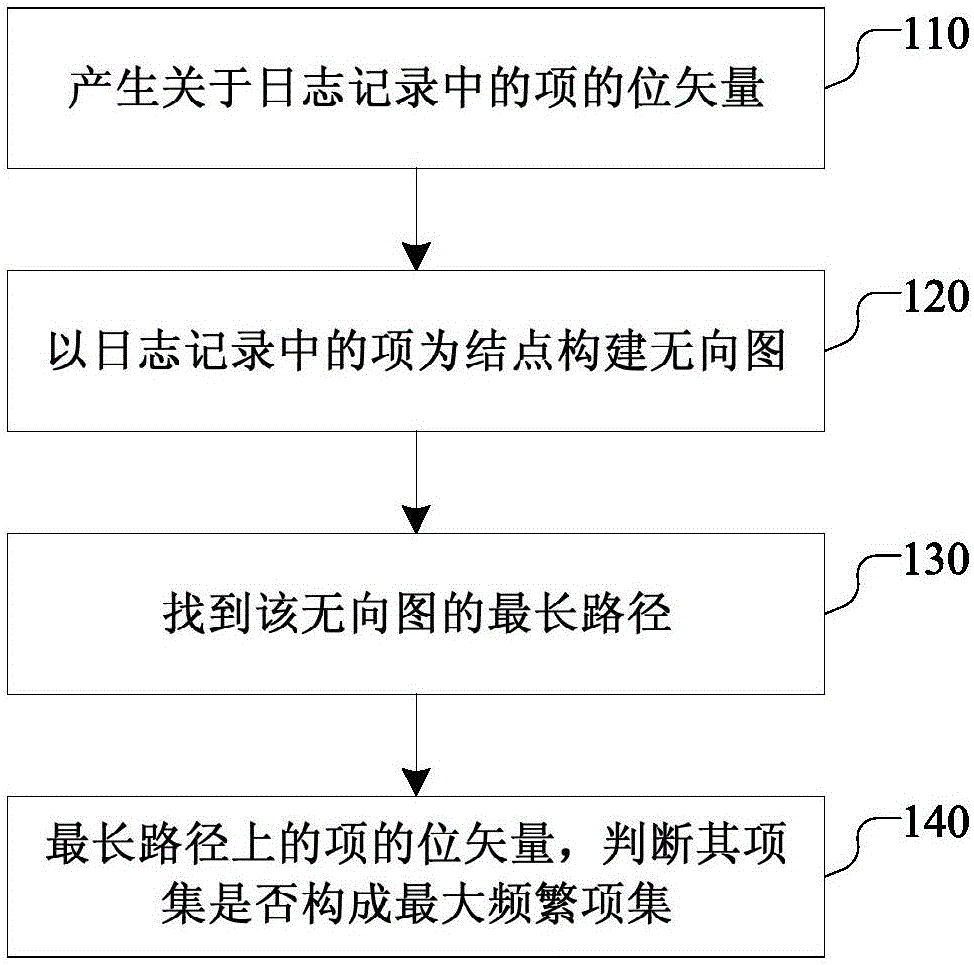
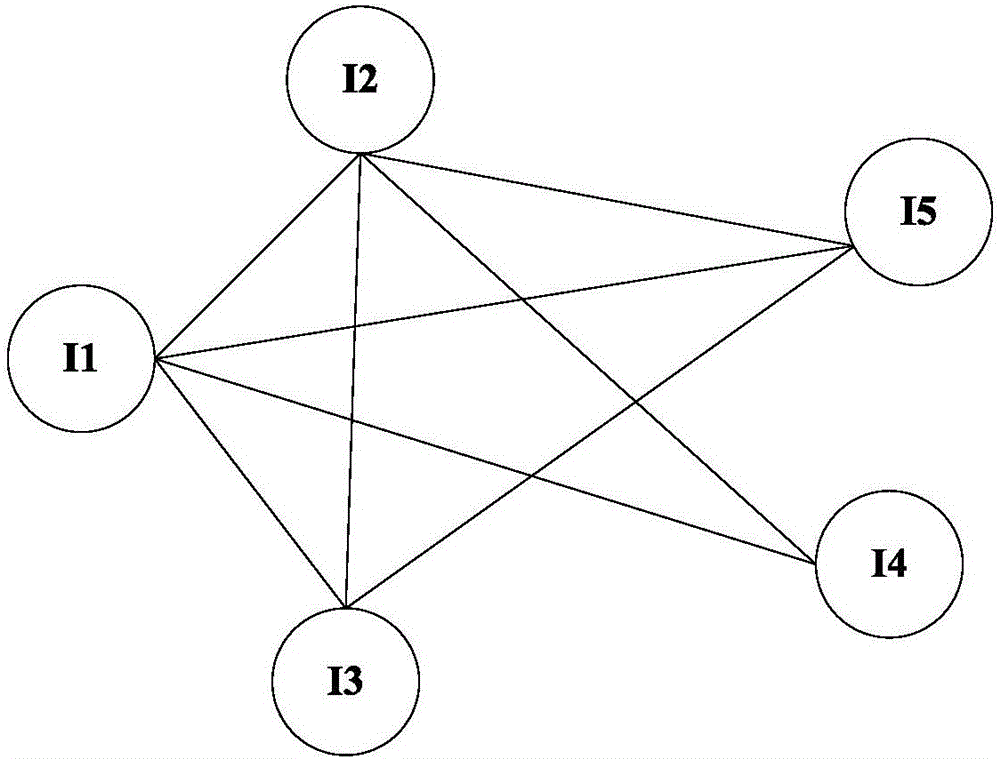
Method and device for log association analysis
ActiveCN105868328AReduce duplicate comparisonsImprove the efficiency of log correlation analysisPlatform integrity maintainanceSpecial data processing applicationsDepth-first searchRule mining
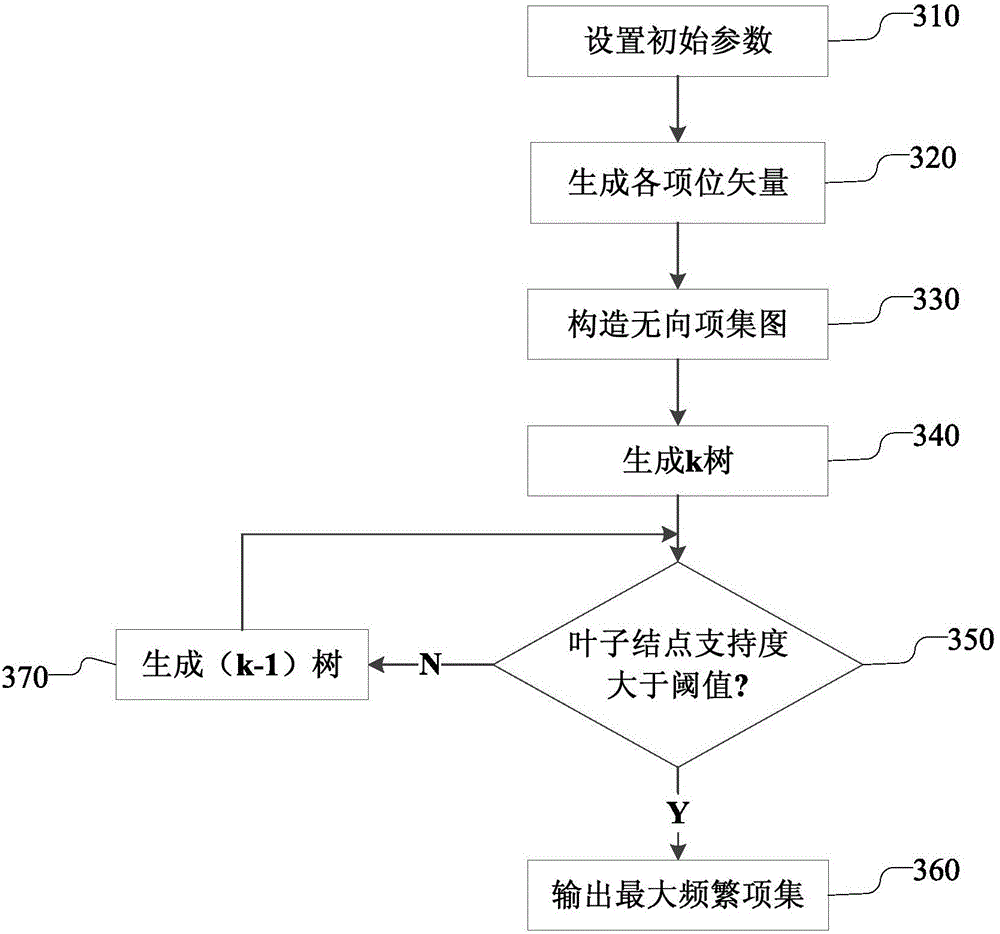
The invention discloses a method and device for log association analysis. In an embodiment, the generation sequence of a candidate item set is changed based on the association rule mining algorithm of a depth-first search tree, a maximum frequent item set is preferably looked for, and mining of the frequent item set is converted into discovery of the maximum frequent item set.
Owner:CHINA UNIONPAY
Intrusion detection method and device, storage medium and electronic equipment
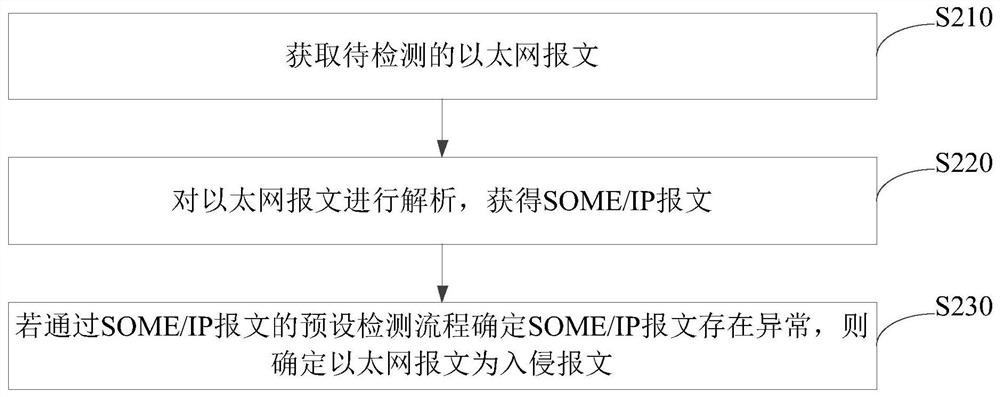
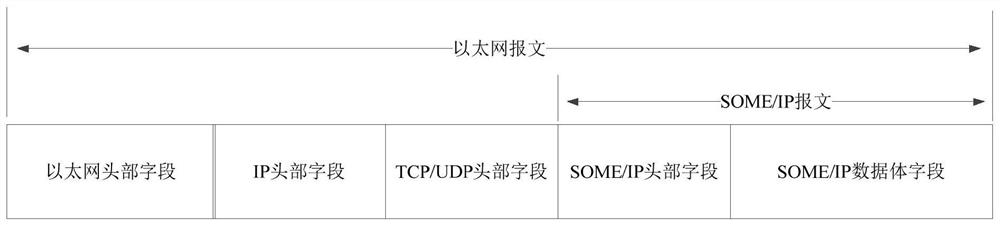
The embodiment of the invention provides an intrusion detection method and device, a storage medium and electronic equipment, and the method comprises the steps: obtaining a service-oriented data interaction middleware SOME / IP message, wherein the SOME / IP message is obtained through analysis of a to-be-detected Ethernet message; if it is determined that the SOME / IP message is abnormal through the preset detection process of the SOME / IP message, determining that the Ethernet message is an intrusion message, wherein the preset detection process comprises at least one of a detection process of a format of a head key field of the SOME / IP message, a detection process of a rule of the SOME / IP message and a detection process of a session state of the SOME / IP message. According to the embodiment of the invention, intrusion detection of the vehicle-mounted Ethernet can be realized, and the stability of a vehicle-mounted network and the safety of a user are guaranteed.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
High-speed railway safety zone intrusion alarm device and method based on infrared images
PendingCN111667655ARich textureRich color informationImage enhancementImage analysisData acquisitionEngineering
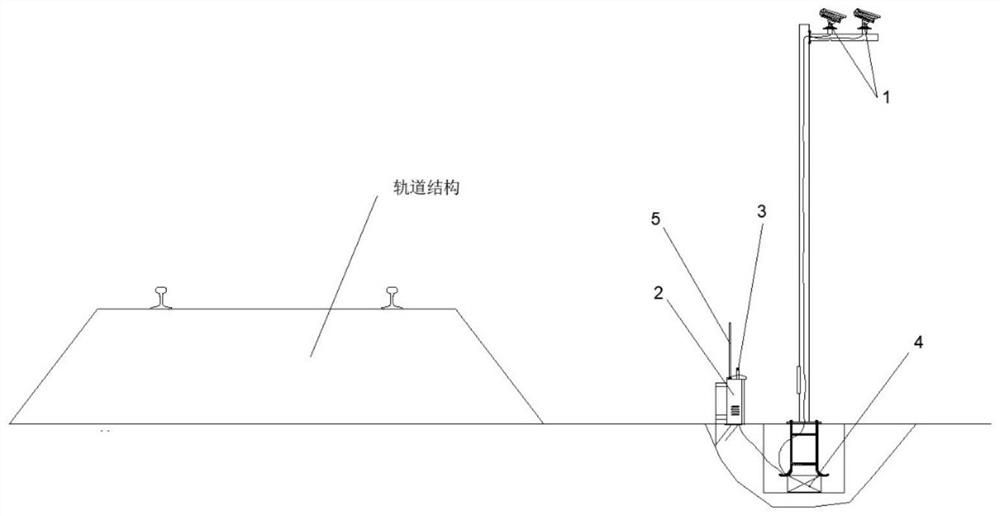
The invention relates to a high-speed railway safety zone intrusion alarm device and method based on infrared images. The alarm device comprises a data acquisition module, a ground analysis module, anearly warning module, a remote communication module, a power supply module and a terminal monitoring platform. The data acquisition module is used for acquiring a monitoring image of a high-speed railway safety zone in real time; the ground analysis module is used for analyzing and processing the acquired monitoring image; the early warning module is used for sending out a warning signal; the remote communication module is used for transmitting an identification result and the monitoring image; the power module is used for supplying power to the whole device; and the terminal monitoring platform is used for checking the identification result and a field image by a worker. The intrusion alarm device can autonomously perform image processing, human shape recognition and result feedback, adverse effects of factors such as illumination conditions, weather conditions and the like on the intrusion alarm device are avoided, and working efficiency and accuracy of the intrusion alarm device are improved.
Owner:SHANGHAI UNIV OF ENG SCI
Campus intrusion detection system and method
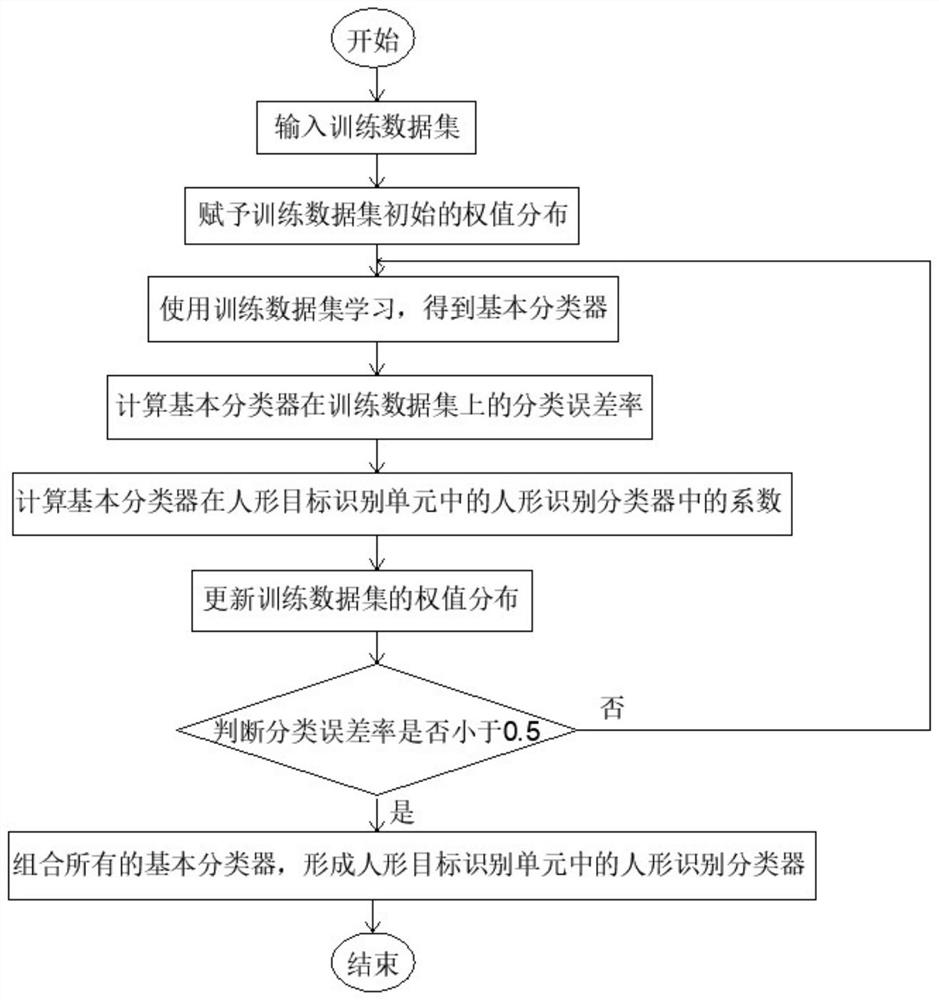
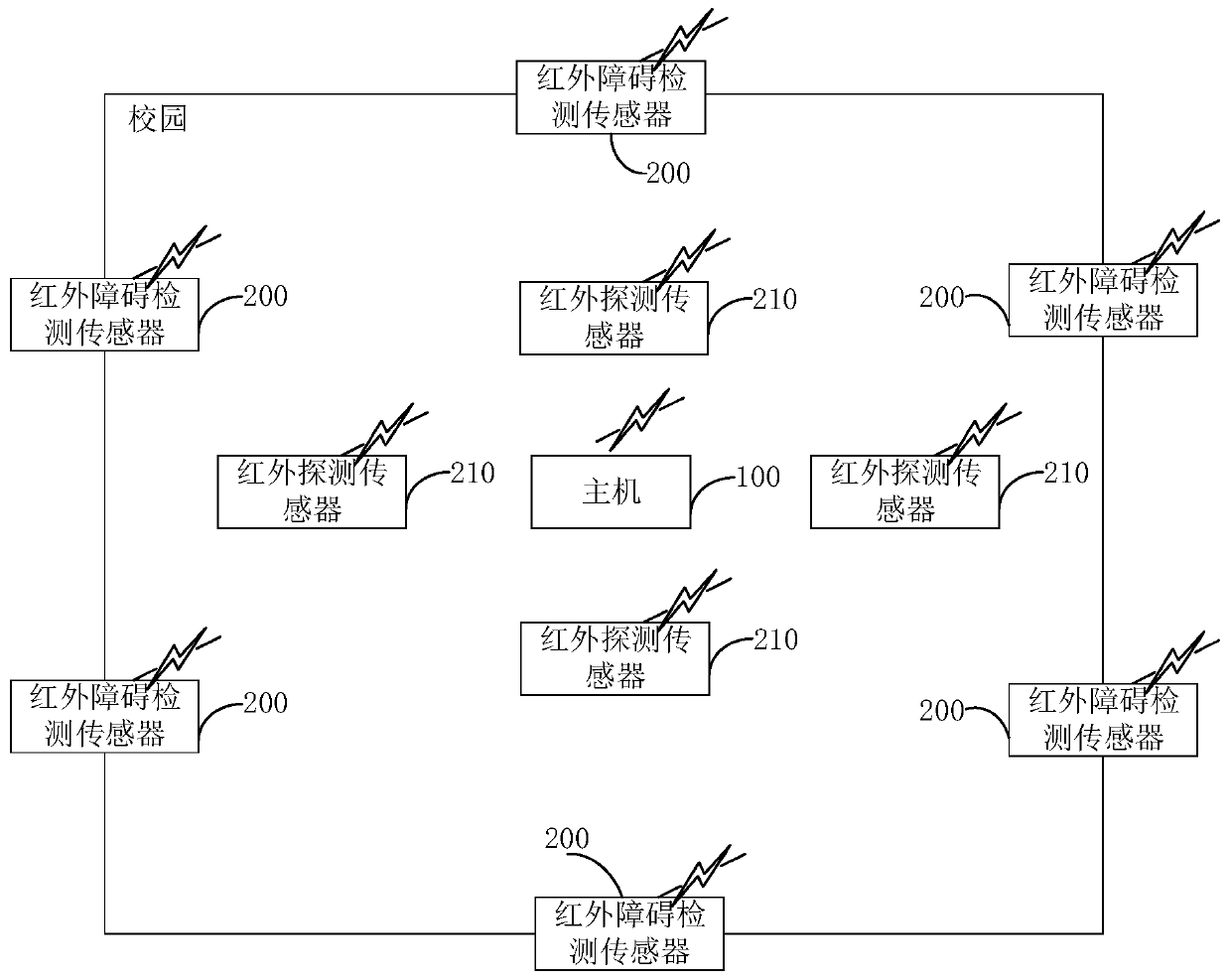
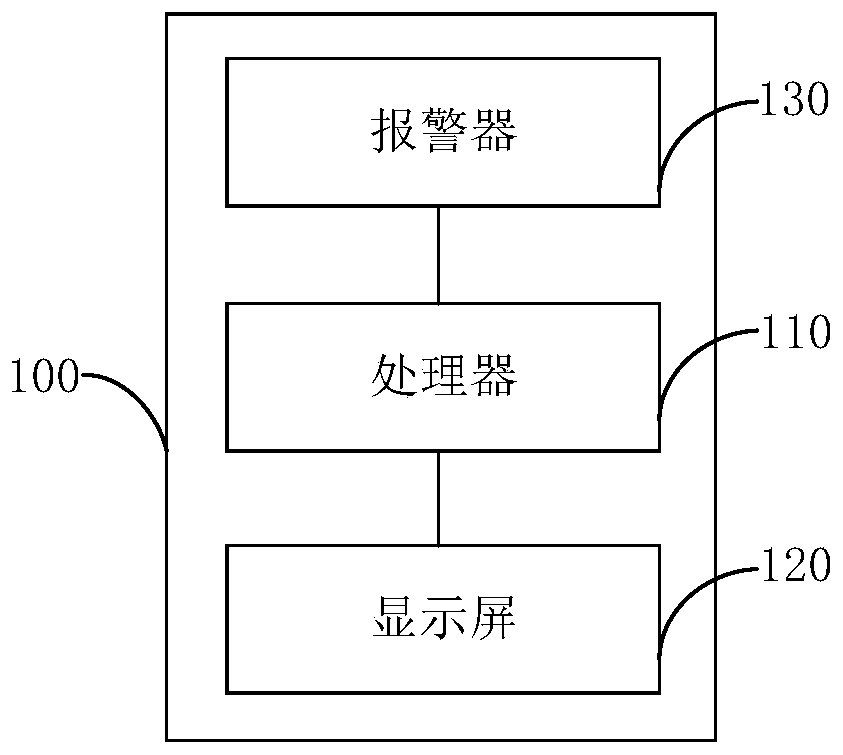
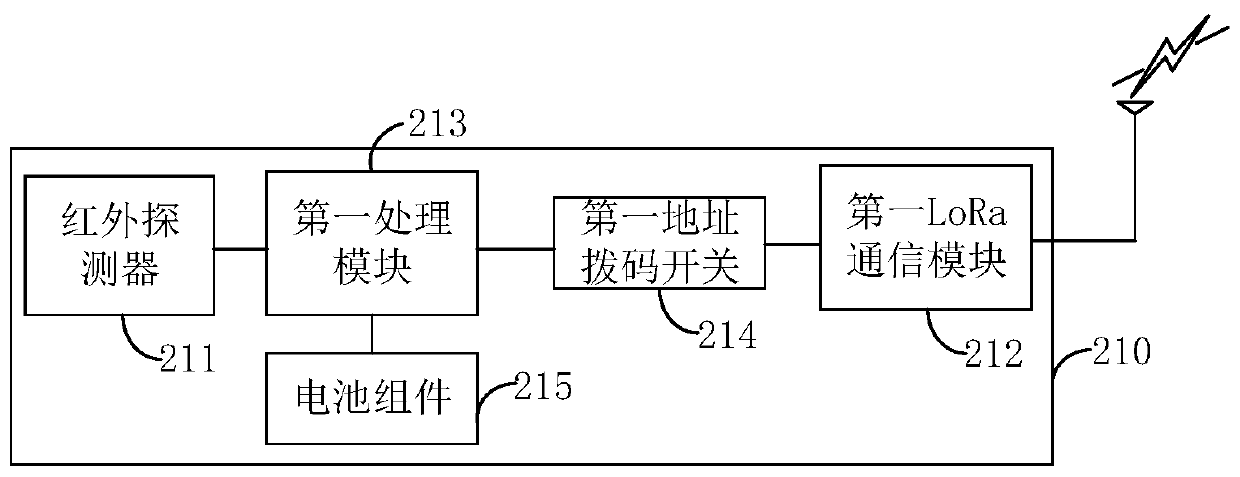
InactiveCN110827498AImprove securityImplement intrusion detectionBurglar alarm short radiation actuationIntrusion detection systemEngineering
The invention provides a campus intrusion detection system and method, and belongs to the technical field of wireless communication. The campus intrusion detection system comprises a host, a pluralityof infrared detection sensors and a plurality of infrared obstacle detection sensors, and the plurality of infrared detection sensors and the plurality of infrared obstacle detection sensors are respectively deployed at a plurality of designated detection points of the campus; and the host is in communication connection with the plurality of infrared detection sensors and the plurality of infrared obstacle detection sensors through a long-distance LoRa communication technology. According to the method and system of the invention, long-distance intrusion detection can be realized through the long-distance LoRa communication technology, and the safety coefficient of the campus is improved.
Owner:杜运
Electronic fence intrusion alarm system and use method thereof
PendingCN112530112AWork reliablyStable jobBurglar alarm by disturbance/breaking stretched cords/wiresLaser rangingMonitoring system
The invention provides an electronic fence intrusion alarm system and a use method thereof. The electronic fence intrusion alarm system comprises a monitoring system; the monitoring system comprises acontrol module and a laser distance measurement module connected with the control module; the detection direction of the laser distance measurement module faces a monitored site of the monitoring system; the control module performs distance measurement on a monitored site through the laser distance measurement module according to a preset frequency; when the distance measurement result exceeds the threshold value, the control module judges that the monitored site is invaded; and laser distance measurement can be used for determining whether the target area is invaded by the outside.
Owner:XIAMEN UNIV TAN KAH KEE COLLEGE
Internet-based e-commerce platform intrusion detection method and computer equipment
ActiveCN111324883BEnsure the effect of intrusion detectionImplement intrusion detectionDigital data protectionDigital data authenticationComputer networkThe Internet
The invention provides an internet-based e-commerce platform intrusion detection method and computer equipment, which can judge whether a first user terminal is an intrusion terminal or not based on afirst order feature vector of an output order and a second order feature vector of a target order when an electronic order in an electronic order information set is the output order. When an electronic order in an electronic order information set is an input order, whether a first user terminal is an intrusion terminal or not can be judged based on a user behavior track of a third user terminal interacting with the first user terminal. Thus, the intrusion terminal of the first user terminal can be judged based on the electronic order information, intrusion detection on the online e-commerce platform provided by the computer equipment is further realized, the intrusion detection effect on the online e-commerce platform is ensured, and the security of the privacy information of the user terminal interacting with the online e-commerce platform is ensured.
Owner:成都我行我数科技有限公司
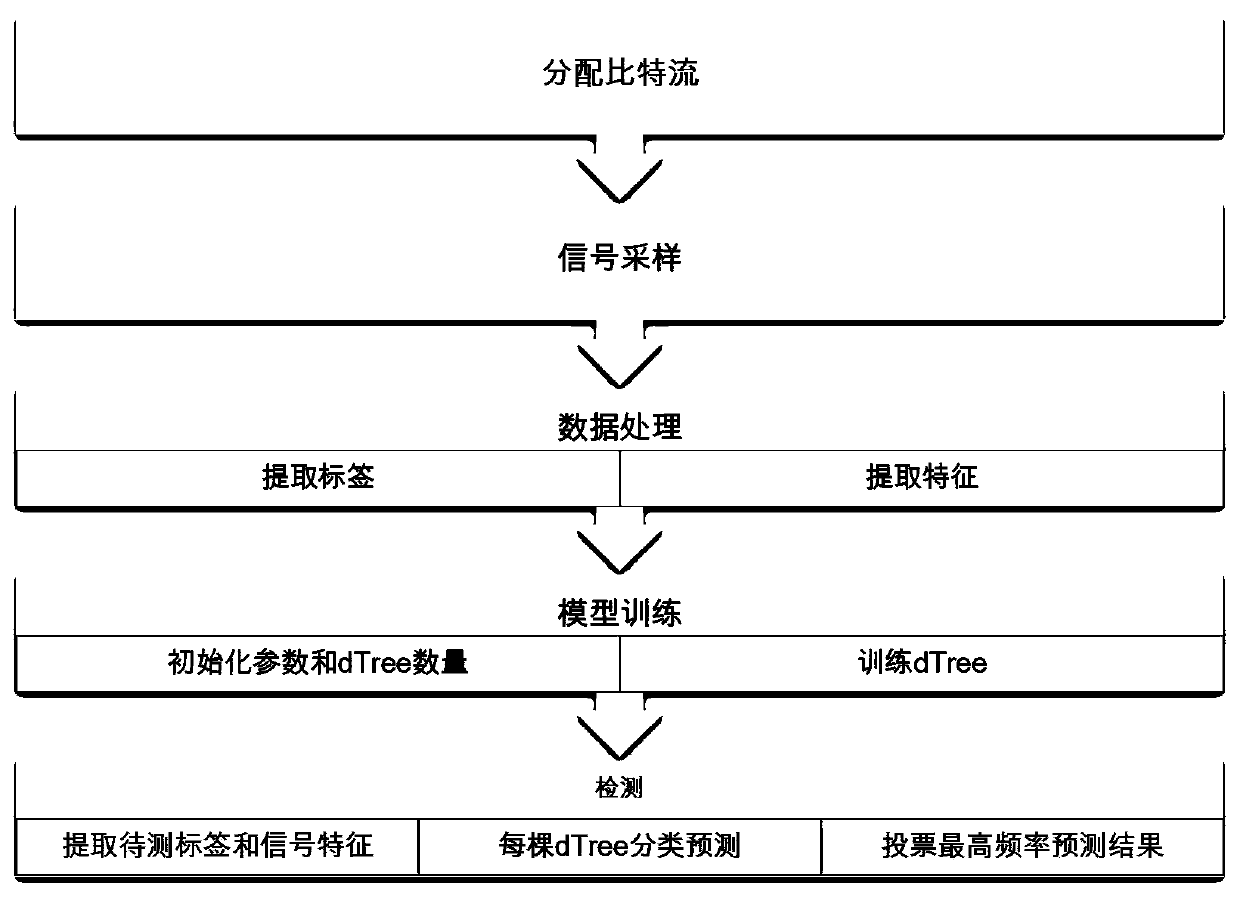
Intrusion detection method, device and apparatus for satellite network
ActiveCN110647942AImplement intrusion detectionSolve inefficiencyCharacter and pattern recognitionPlatform integrity maintainanceData setEngineering
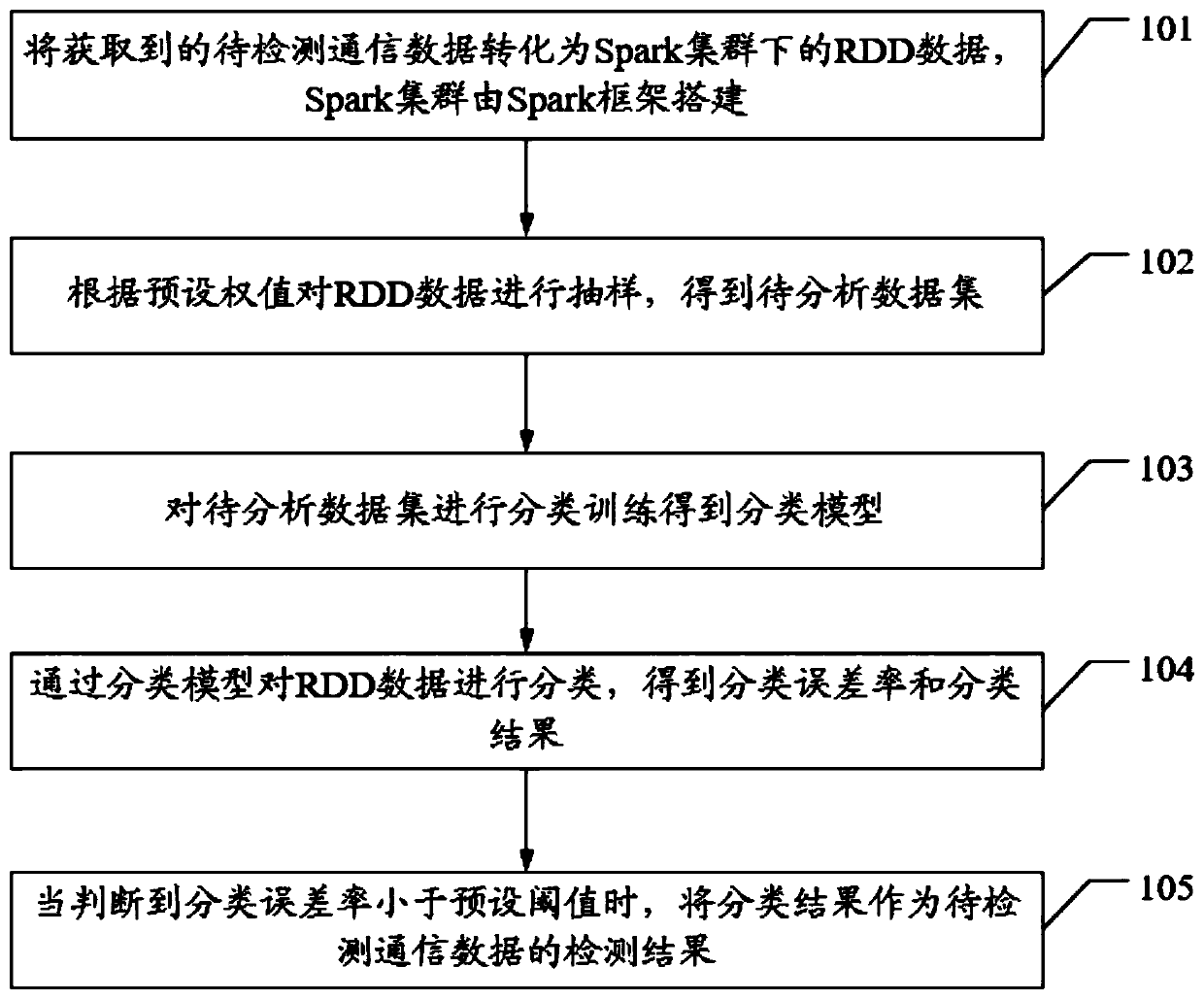
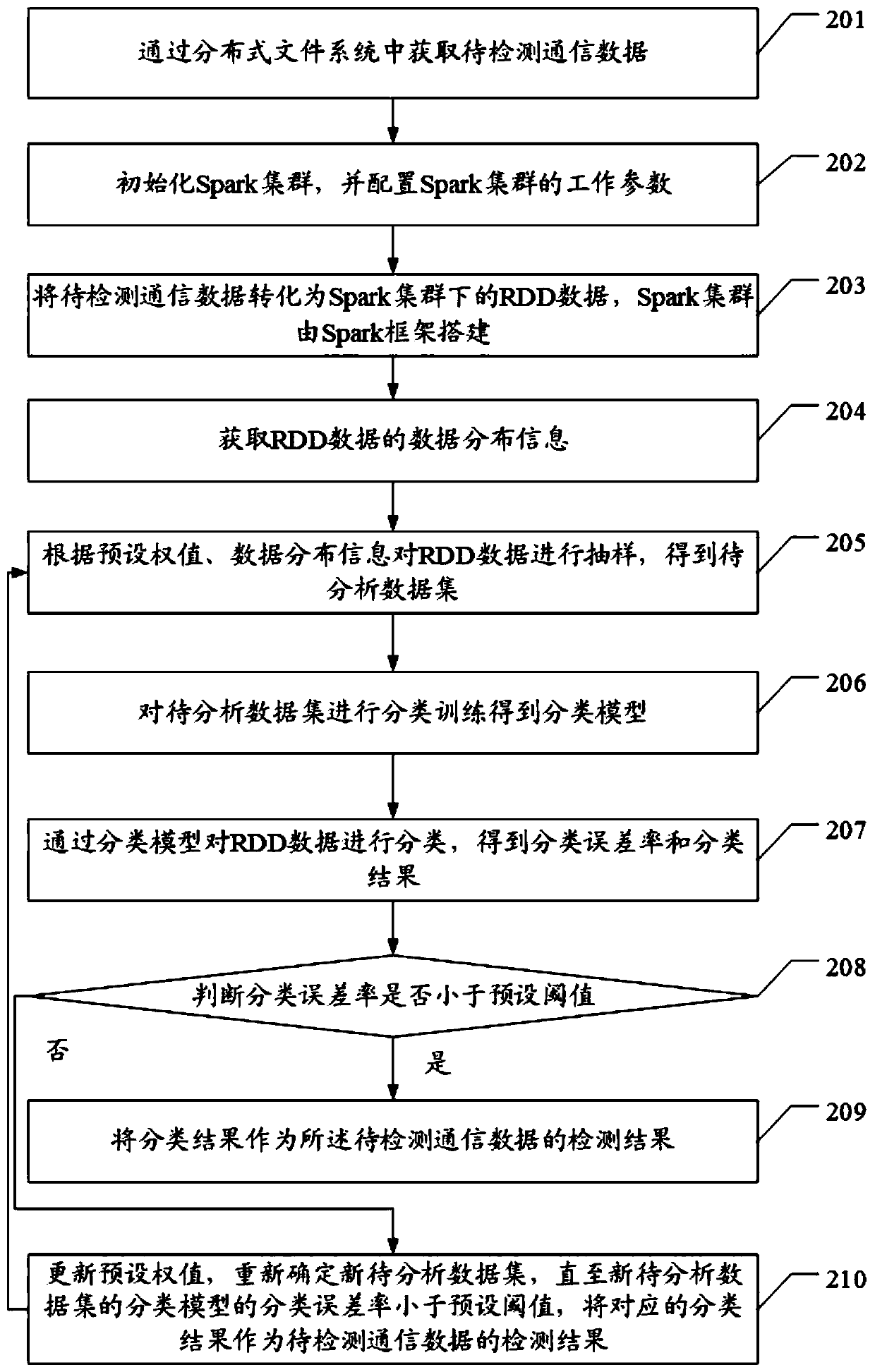
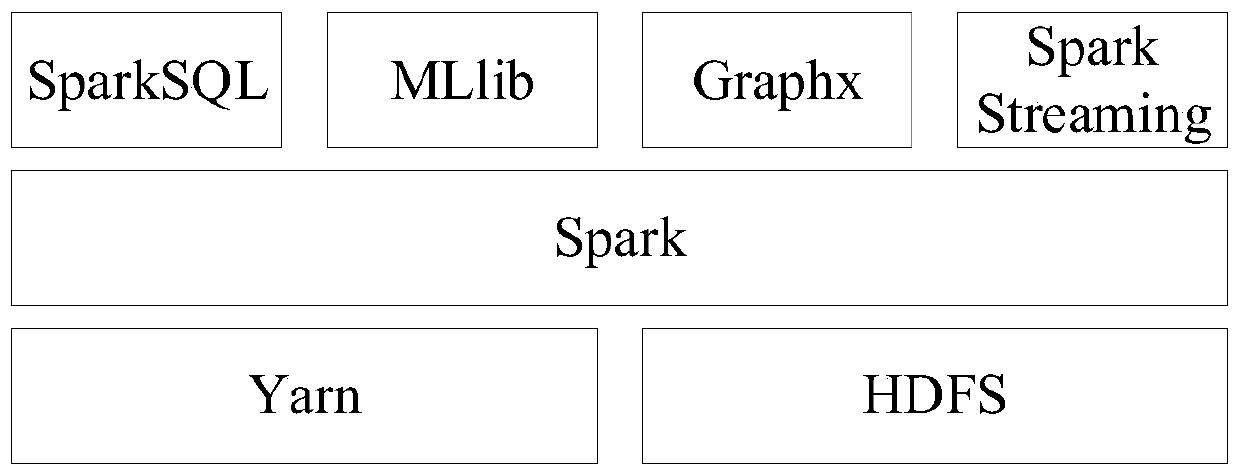
The invention discloses an intrusion detection method, device and apparatus for a satellite network, and the method comprises the steps: converting obtained to-be-detected communication data into RDDdata under a Spark cluster, and enabling the Spark cluster to be built through a Spark framework; sampling the RDD data according to a preset weight to obtain a to-be-analyzed data set; performing classification training on the to-be-analyzed data set to obtain a classification model; classifying the RDD data through the classification model to obtain a classification error rate and a classification result; when judging that the classification error rate is smaller than a preset threshold value, enabling the classification result to serve as a detection result of the to-be-detected communication data, and the technical problems that an existing intrusion detection method is low in efficiency, tedious and limited in application are solved.
Owner:GUANGDONG POWER GRID CO LTD +1
Host Intrusion Detection Method Based on Relational Network
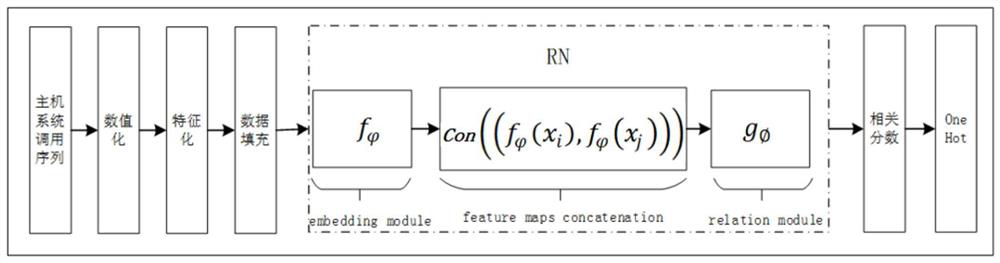
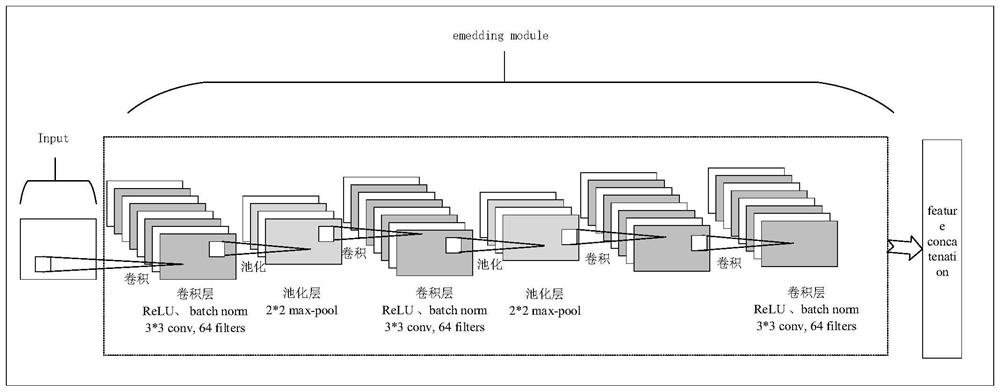
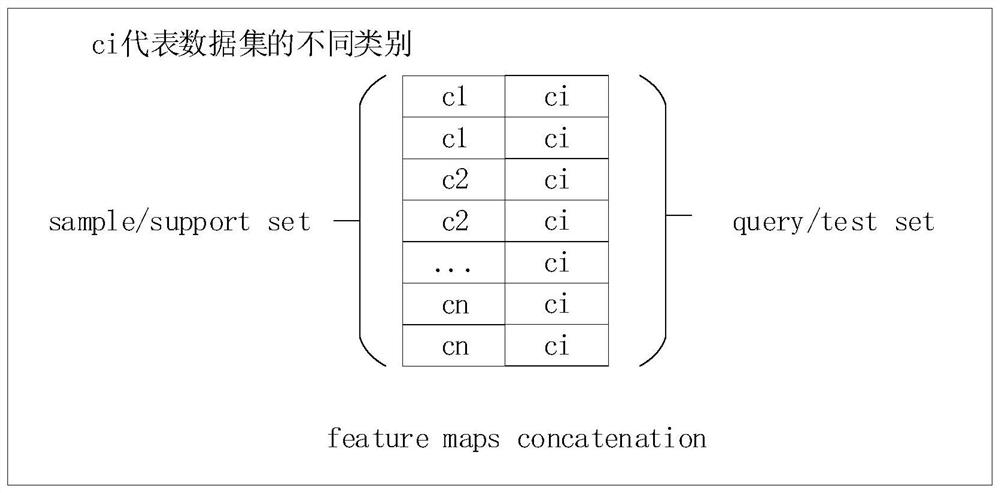
ActiveCN111431863BImplement intrusion detectionChange the objective functionPlatform integrity maintainanceNeural architecturesData setEngineering
The invention discloses a host intrusion detection method based on a relational network, comprising: step 1, characterizing the host system call sequence sample set; step 2, dividing the data set processed in step 1 into training sets, supporting Set and test set; Divide the training set into sample set and query set again; Step 3, construct relational network model; Described relational network model includes embedding module, connection module and relational module; Step 4, define the target of relational network model Function; step 5, train the constructed relational network model to obtain the host intrusion detection model; step 6, input the trained host intrusion detection model into the host intrusion detection model after step 1 to detect the host system call sequence to be detected. The invention proposes a host intrusion detection method based on a relational network, which can realize host intrusion detection of existing intrusion modes and host intrusion detection of unknown intrusion modes under the condition of small samples.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Optical fiber intrusion detection method based on space-time two-dimensional sparse representation k-s test of vibration signal
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY +1
Method for implementing virtual engine technique for intrusion detection
InactiveCN100429894CLittle impact on performanceImplement intrusion detectionUser identity/authority verificationHardware monitoringPhysics engineIp address
The invention features the physical engine of an Intrusion Detection System that virtualizes multi engines, by which the classified protection can be made according to the network condition of client, VLAN TAG information, IP address information or MAC address information. On each virtual engine, different detection strategy and security strategy standard can be executed and set in order to implement the object-oriented intrusion detection.
Owner:BEIJING VENUS INFORMATION TECH +1
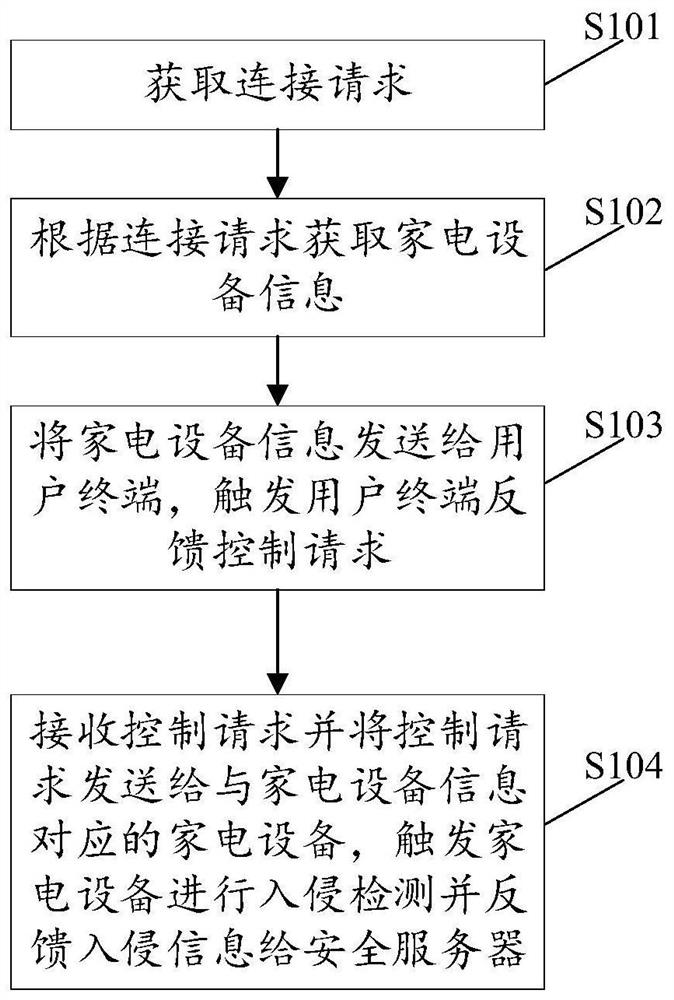
Method and device for intrusion detection and server
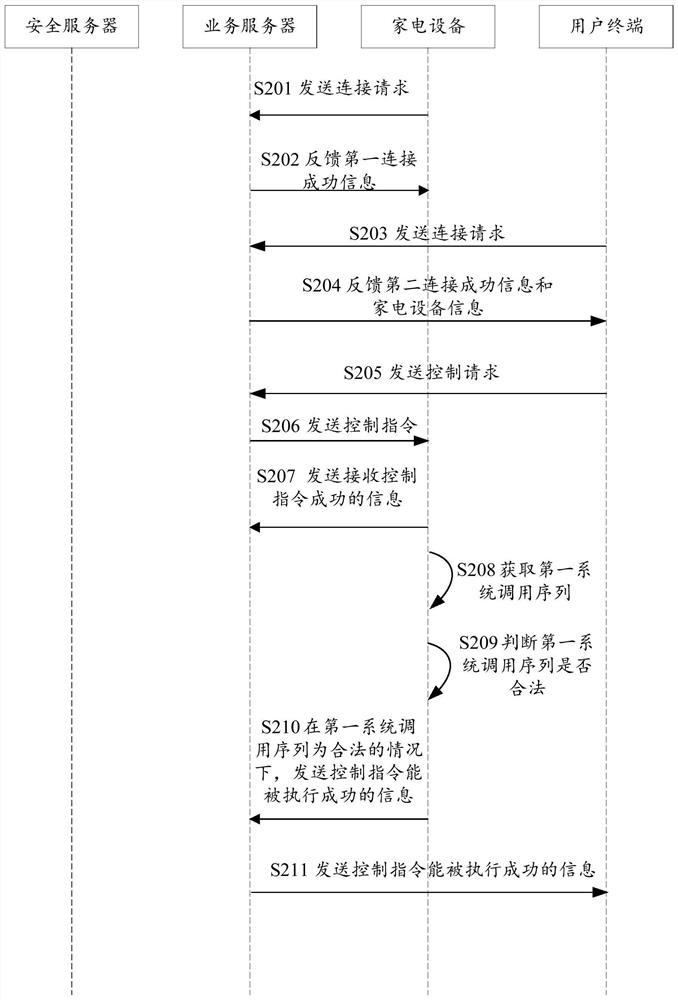
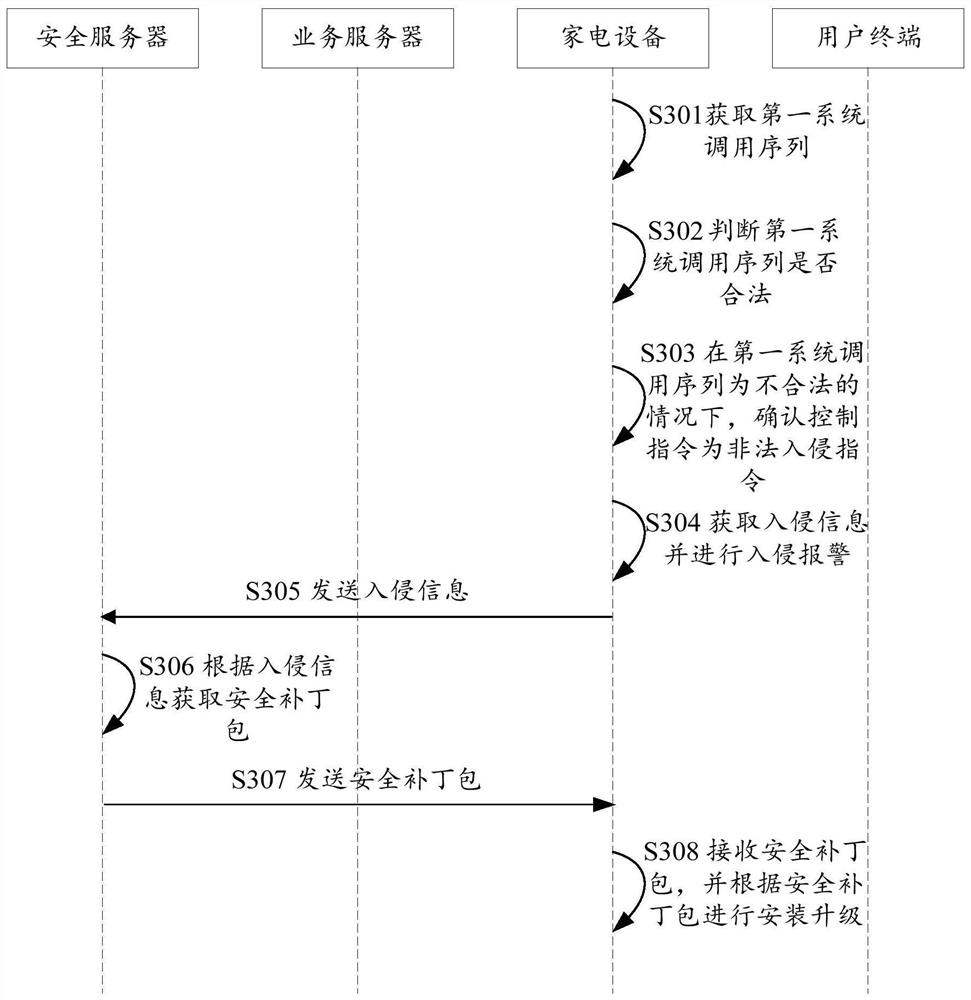
PendingCN112182574AImprove securityImplement intrusion detectionSoftware engineeringPlatform integrity maintainanceComputer securityServer-side
The invention relates to the technical field of communication, and discloses a method for intrusion detection, which is applied to a service server side. The method comprises obtaining a connection request; acquiring household appliance information according to the connection request; sending the household appliance information to a user terminal, and triggering the user terminal to feed back a control request; and receiving the control request, sending the control request to a household appliance corresponding to the household appliance information, triggering the household appliance to carryout intrusion detection, and feeding intrusion information back to a security server. The control request is acquired, the control instruction is acquired according to the control request, and the control request is sent to the household appliance, so that the household appliance is triggered to carry out intrusion detection, and the safety of the household appliance is improved. The invention further discloses a device for intrusion detection and a server.
Owner:QINGDAO HAIER TECH
A smart contract intrusion detection method, device, terminal device and storage medium
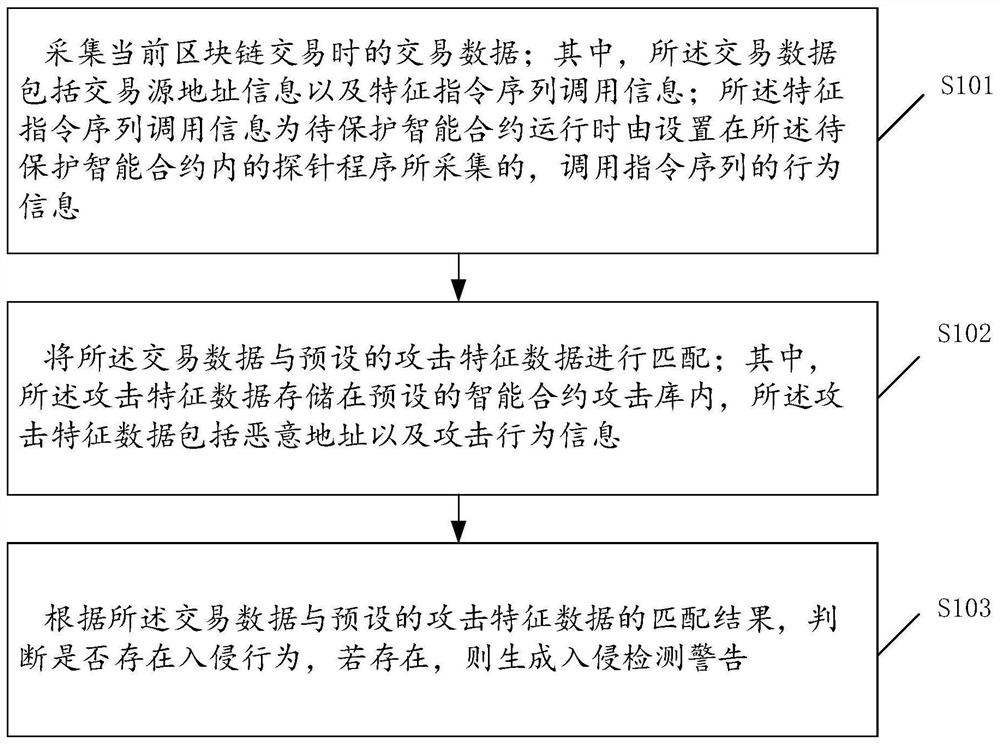
ActiveCN111683084BImplement intrusion detectionImprove securityPlatform integrity maintainanceSecuring communicationAttackTransaction data
The invention discloses a smart contract intrusion detection method, device, terminal equipment and storage medium. The method includes: collecting transaction data during the current block chain transaction; wherein, the transaction data includes transaction source address information and characteristic instructions Sequence call information; the characteristic instruction sequence call information is collected by the probe program set in the smart contract to be protected when the smart contract to be protected is running, and the behavior information of the call instruction sequence; the transaction data and the preset The attack feature data is matched; wherein, the attack feature data is stored in the preset smart contract attack database, and the attack feature data includes malicious addresses and attack behavior information; according to the transaction data and the preset attack feature data According to the matching result of the data, it is judged whether there is an intrusion behavior, and if there is, an intrusion detection warning is generated. The security of smart contracts can be improved by implementing the embodiments of the present invention.
Owner:GUANGZHOU UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com