Intrusion detection method for self-learning protocol rule
A self-learning, rule-based technology, applied in the field of intrusion detection of self-learning protocol rules, can solve the problem of unable to automatically generate key field rules, unable to solve the problem of self-learning message communication format, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described below through specific embodiments and accompanying drawings.
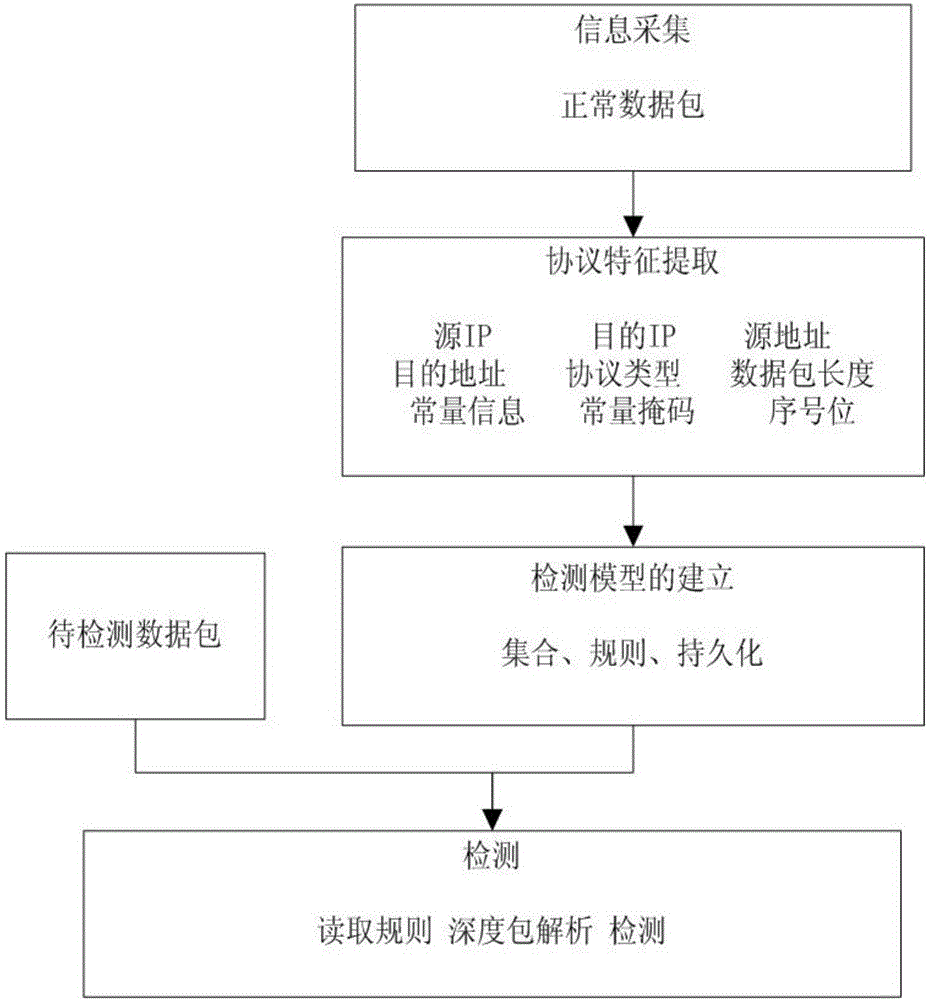
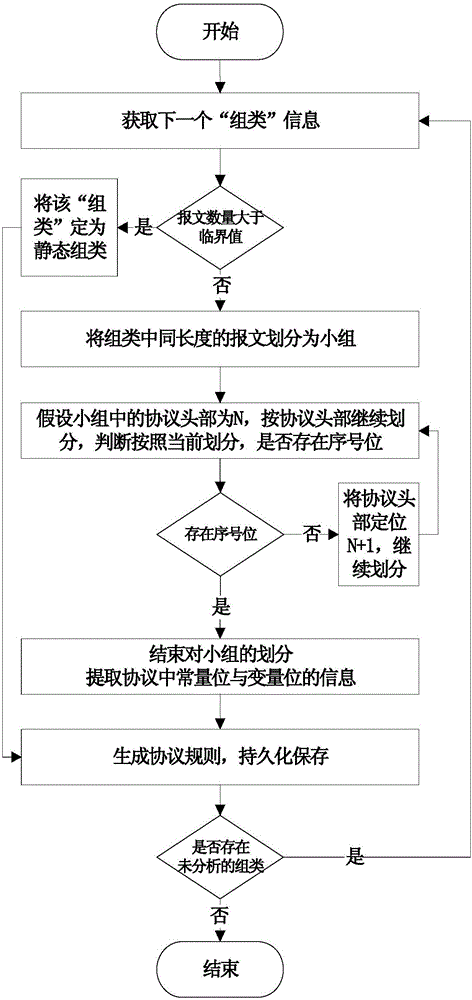
[0021] The intrusion detection method of the self-learning protocol rule of the present invention, its overall process is as follows figure 1 As shown, it specifically includes the following steps:
[0022] 1. Data packet collection
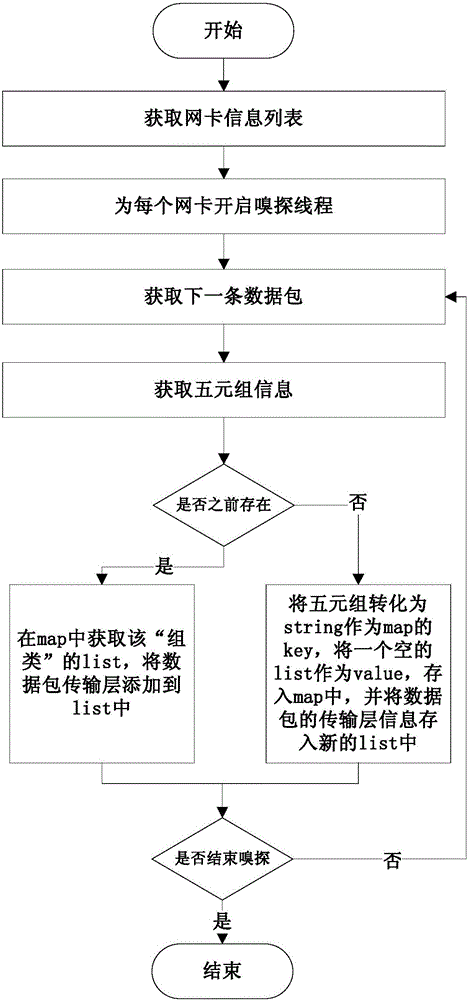
[0023] The interface based on the libpcap / winpcap dynamic library receives the message sent by the network device, turns on the promiscuous mode of the network card, and collects a set of normal workflow data. Divide the data packets into "groups" according to the source IP, destination IP, source port, destination port, and protocol type (TCP, UDP or ICMP), and sort the data packets in each group according to the order received . figure 2 It is a schematic diagram of the collection process flow, and the speci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com