Method for implementing virtual engine technique for intrusion detection
A virtual engine and intrusion detection technology, applied in the field of computer networks, can solve the problems of high installation and maintenance costs, difficult deployment and monitoring, and inconvenient network expansion, achieving low cost investment, improving pertinence, and reducing false positives. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
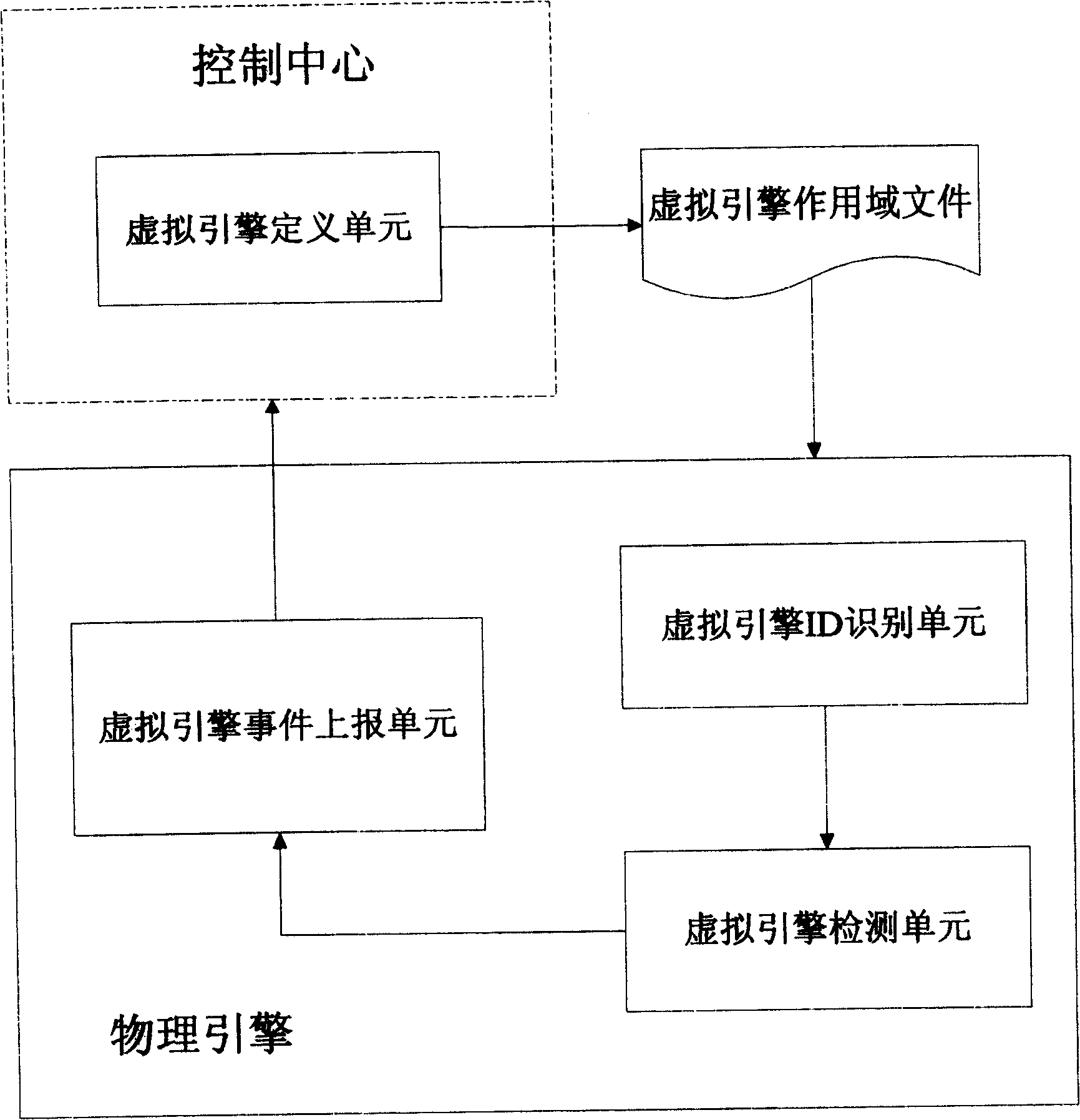
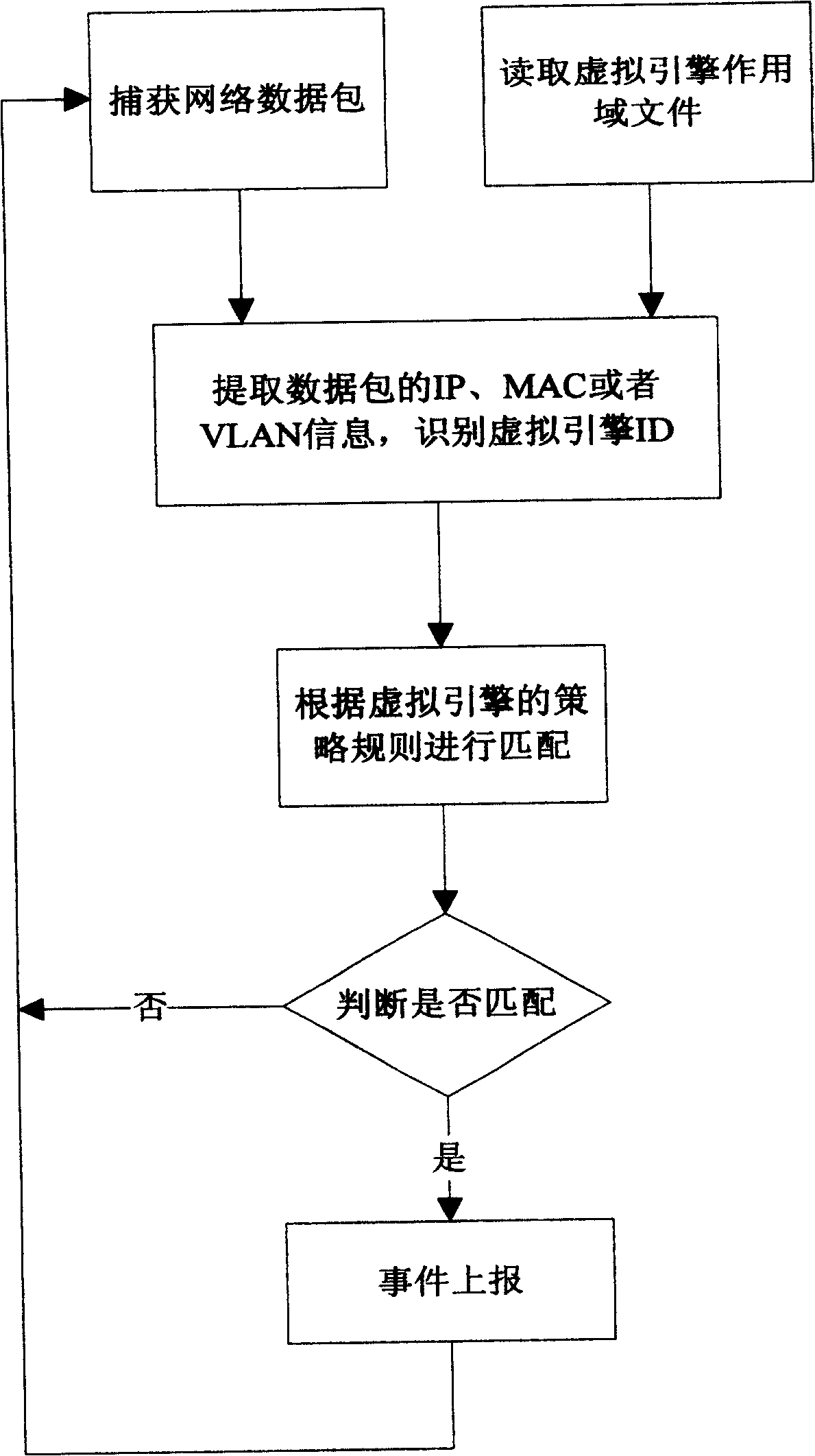
[0025] Embodiment 1: an intrusion detection virtual engine technology implementation method includes the following steps;
[0026] Define the virtual engine:
[0027] The Unreal Engine is customized through the Unreal Engine Customization Wizard.
[0028] The main content of defining the virtual engine includes: the name of the virtual engine, the division type and scope of the virtual engine.
[0029] Generally, virtual engines are divided and defined according to protected objects. The division types of the virtual engine include: division according to VLAN tag information, division according to IP address information, and division according to MAC address information.
[0030] VLAN tag division format, VLAN tag is the identification number (VLAN ID) of a certain VLAN, and the format includes VLAN ID enumeration and VLAN ID range. Among them, the enumeration of VLAN IDs is separated by ",", for example: 1, 2, 4; the range of VLAN IDs is separated by "-", for example: 6-12...
Embodiment 2
[0058] Embodiment 2: A scenario application example of an intrusion detection virtual engine technology implementation method;
[0059] For example, different departments in an enterprise, such as the president's office, financial department, sales department, and general office, have different security requirements. If the same intrusion detection strategy is adopted, various problems will inevitably arise. If the policy is set too strictly, it will inevitably cause departments with low security sensitivity requirements (such as general offices, logistics departments, etc.) to receive alarms constantly, challenging their nerves again and again, and will cause "wolf is coming" over time If the policy setting is too simple, although non-sensitive departments no longer have to endure frequent "false alarms", it will undoubtedly relax the control of important departments (such as the president's office, financial department, and sales department). etc.) data detection, these high...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com