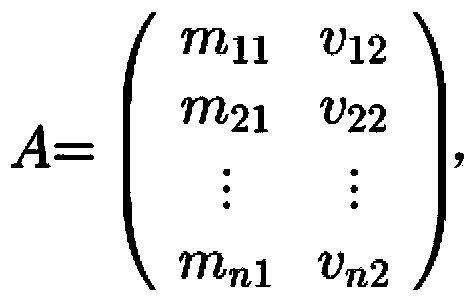Method for intrusion detection based on wireless signal characters
An intrusion detection and wireless signal technology, applied in wireless communication, electrical components, security devices, etc., can solve the problems of intrusion detection system light conditions that cannot achieve wall penetration, cumbersome system layout, and inapplicability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
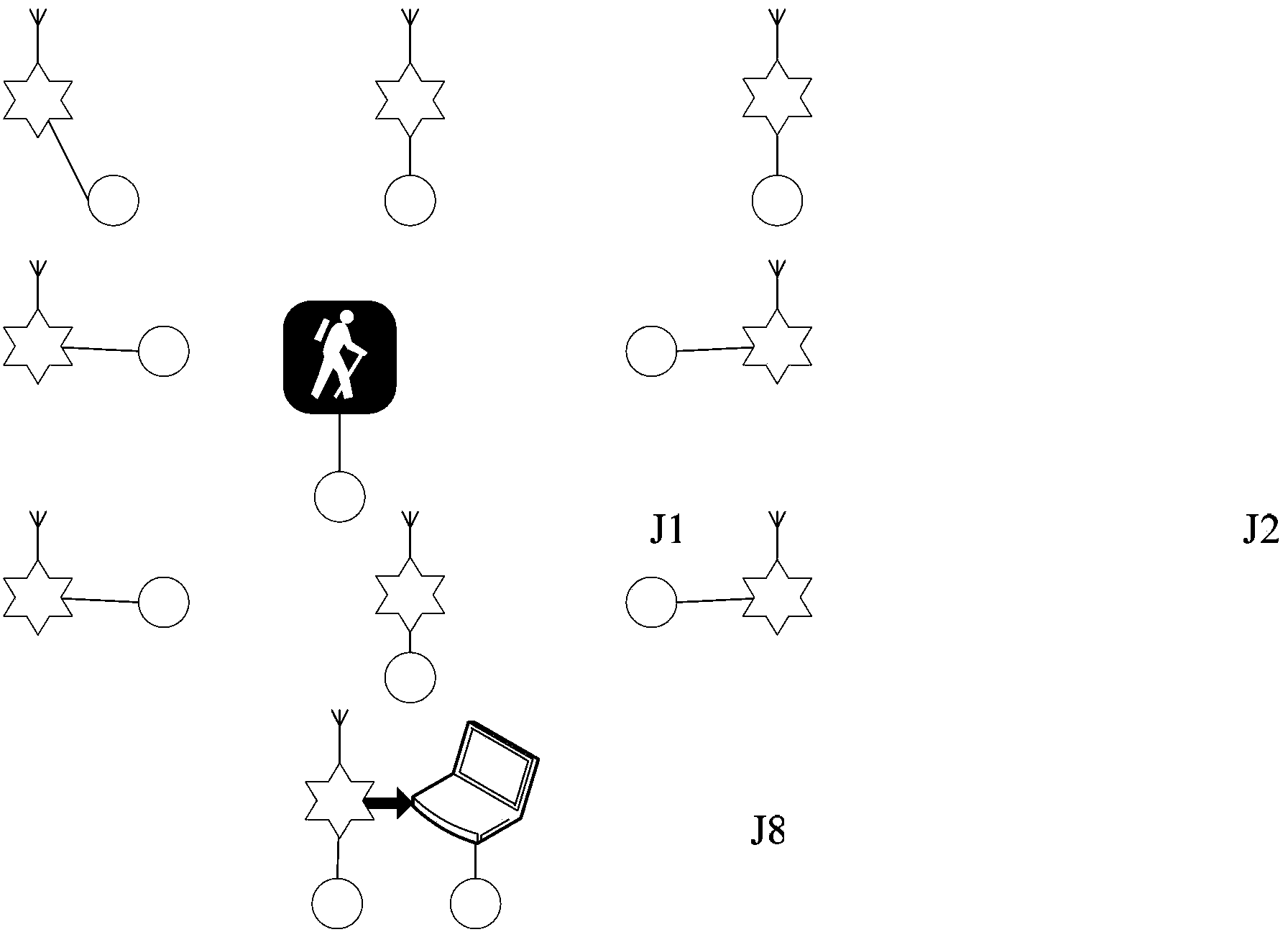
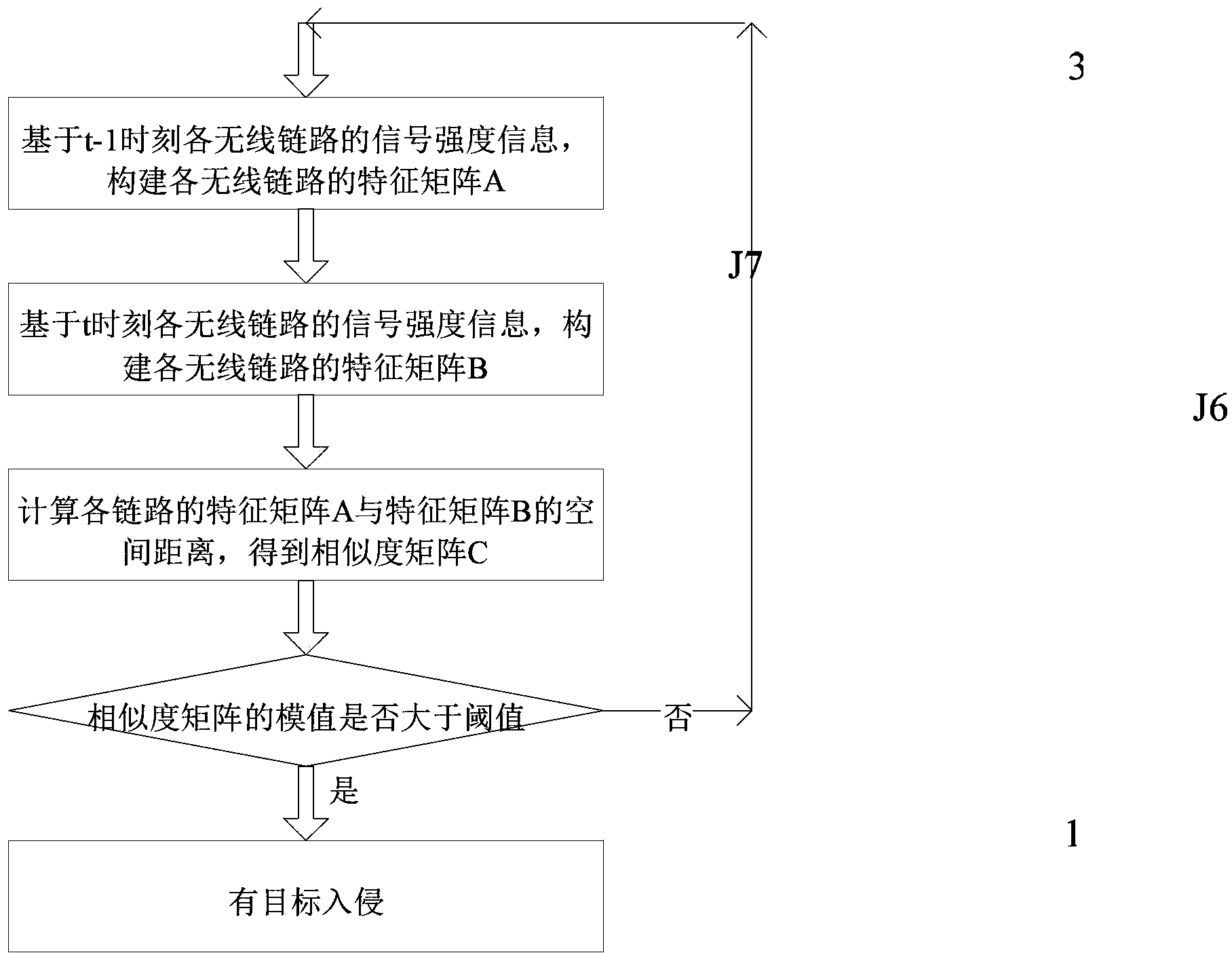
[0018] The present invention will be described in detail below in conjunction with specific technical solutions and accompanying drawings, but the present invention is not limited to specific embodiments. Example: as attached figure 1 As shown, the system adopted by the intrusion detection method is composed of wireless scanning nodes, wireless convergence nodes, general-purpose PCs, and intrusion detection algorithms. The system is set up with 8 wireless scanning nodes J1, J2, ... J8 and wireless sink node 1, all of which are designed based on the wireless module working at 433MHz, with a transmission power of 20dBm and an antenna gain of 1dB. The wireless scanning nodes J1, J2, ... J8 are placed on the four sides of a 10m×10m rectangular area, and a wireless scanning node is placed at an interval of 5m on each side, and the placement height is 1m. The wireless aggregation node 1 and the PC 2 are placed on one side of the monitoring area or inside the monitoring area, within...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com