Hidden model training and use method, device and computer readable storage medium
A model training and model technology, applied in the field of communication, can solve problems such as poor hiding effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0036] The development trend of contemporary steganography is mainly reflected in several branches: digital media information hiding, language steganography, file system steganography, and network steganography. The history of digital media steganography can be traced back to the 1970s, and its development methods include patchwork, significant bit modification, texture block encoding, etc. These techniques are used in lossy or lossless compressed images. Linguistic steganography is mainly accomplished by changing the paragraphs, word order or synonyms of the carrier text language. In today's development of steganography, a large amount of text information, even including spam, may become the carrier of text steganography. File system steganography refers to embedding steganographic information into an isolated computer environment, so that it can automatically search the encrypted files of the disk to achieve the purpose of obtaining information. Network steganography is th...
no. 2 example
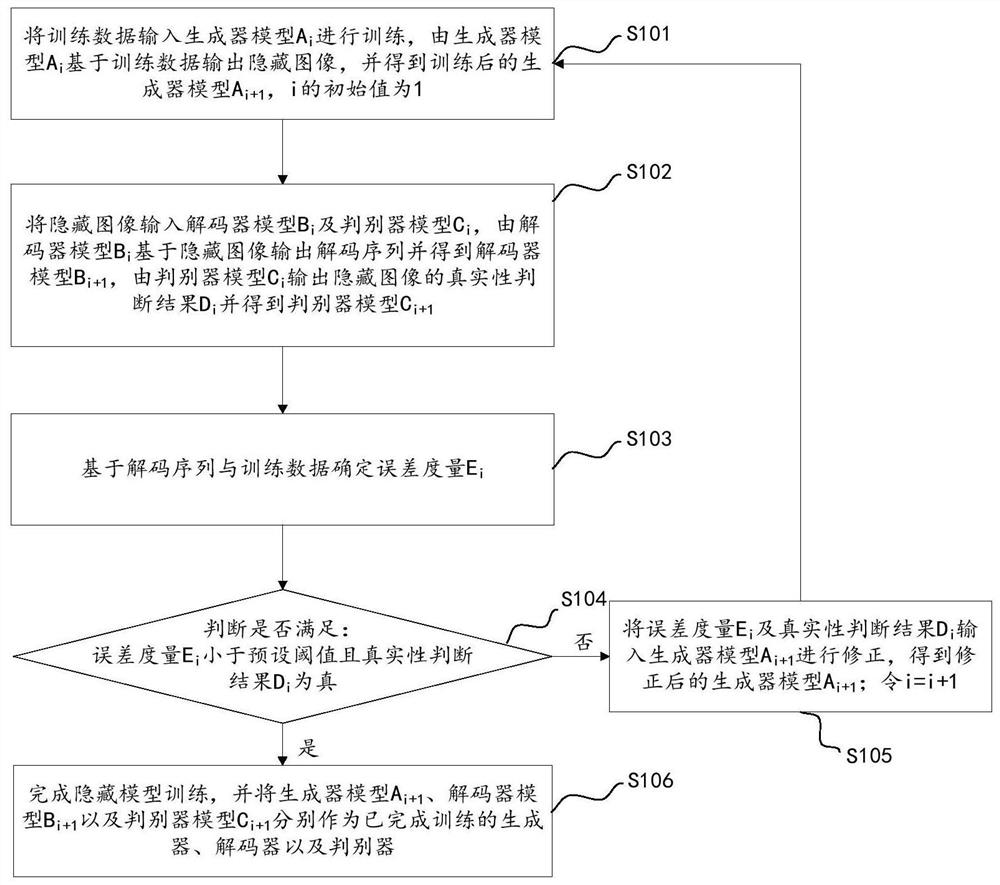
[0053] This embodiment also provides a method for using a hidden model, where the hidden model is obtained by training the hidden model training method provided in the first embodiment, the hidden model at least includes a generator, and the method for using the hidden model includes:
[0054] The information to be hidden is input into the generator, and the generator outputs a hidden image based on the information to be hidden.
[0055] In some other examples of this embodiment, the information to be hidden here is a uniformly distributed hidden information sequence.
[0056] It should be understood that the information to be hidden can be converted into a hidden image to be hidden by the generator in the hidden model, so as to avoid the detection of the detector. The hidden model also includes a decoder and a discriminator, both of which are also trained by the hidden model training method provided in the first embodiment. It should be understood that the decoder correspond...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com