Digital signature method for cooperative SM2
A technology of digital signature and signed data, applied in the field of cryptography, it can solve the problem of high communication and computational complexity of participants, and achieve the effect of avoiding data exchange and operation and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
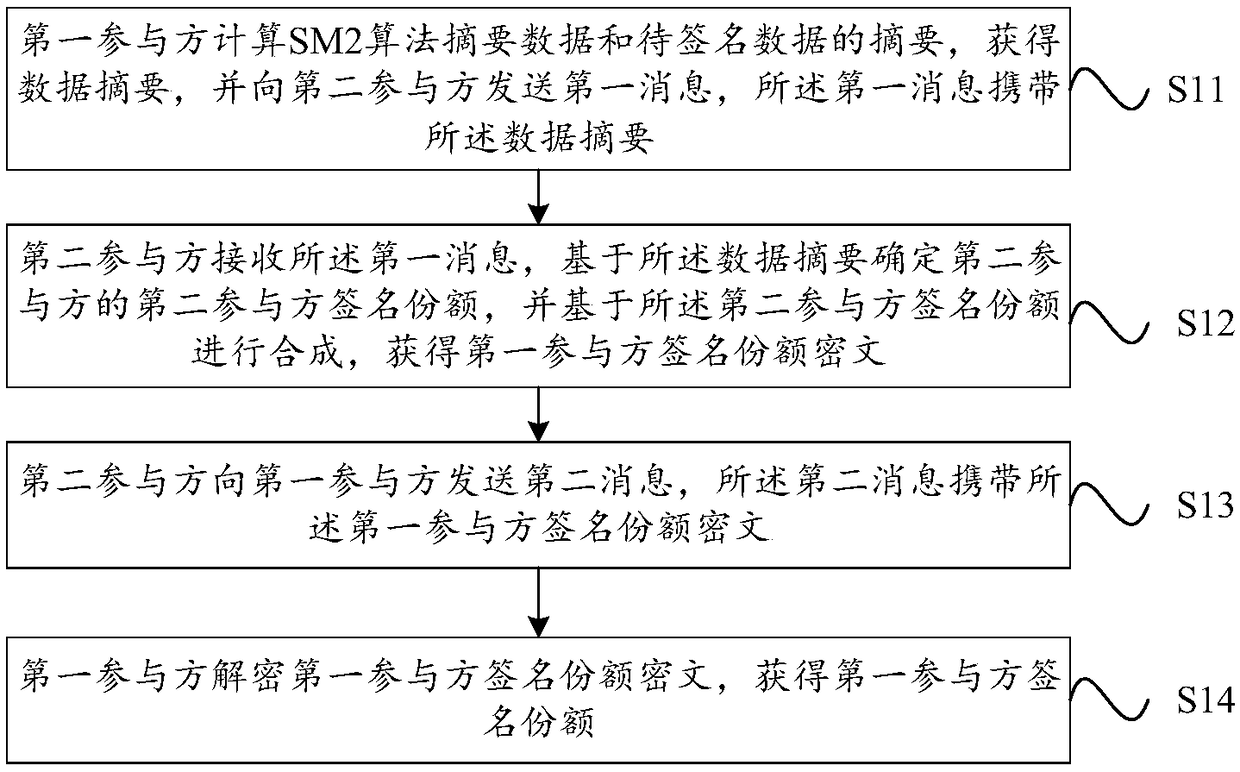
[0089] Embodiment 1: The private key is shared in the form of addition.
[0090] In one embodiment, the method of constructing the private key based on additive sharing may also be called additive sharing. When the private key is constructed by additive sharing, the form in one embodiment can be written as d=d 1 +d 2 -1.
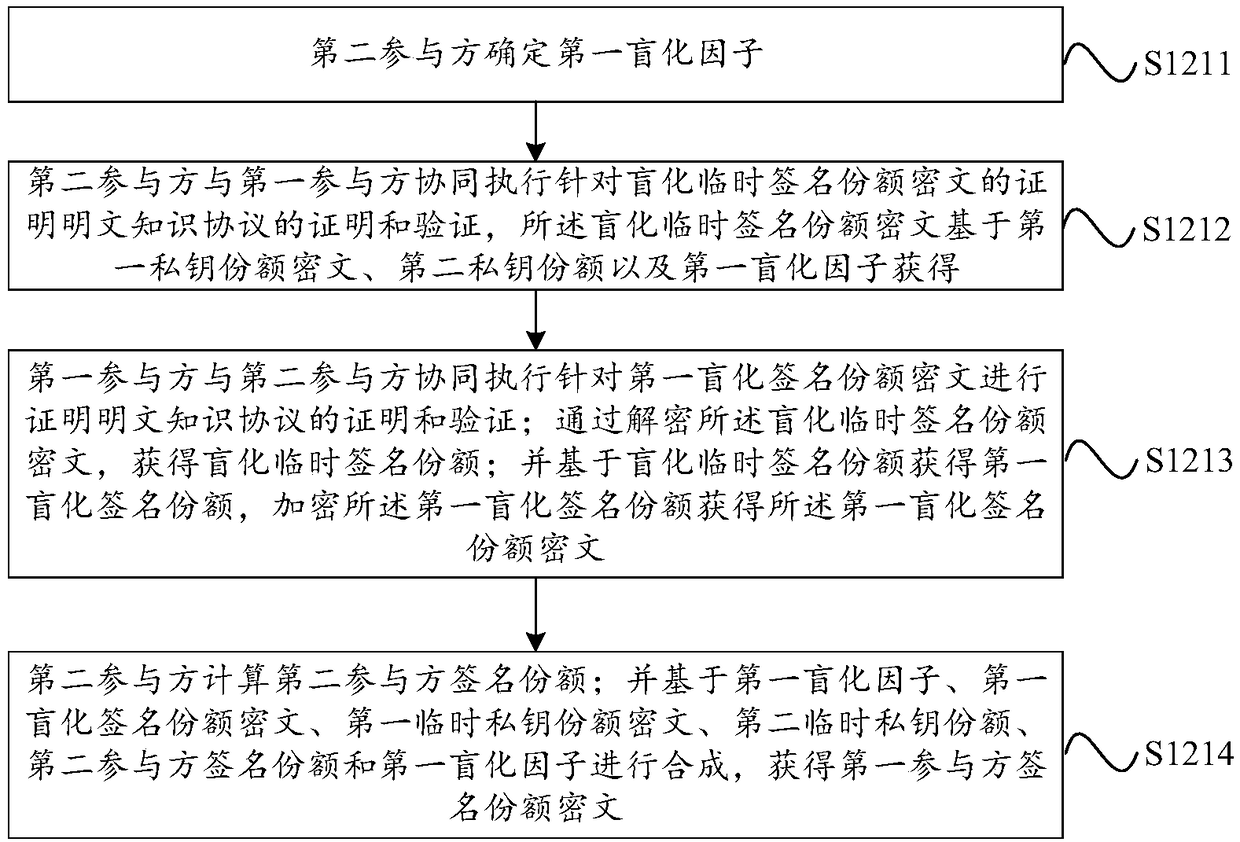
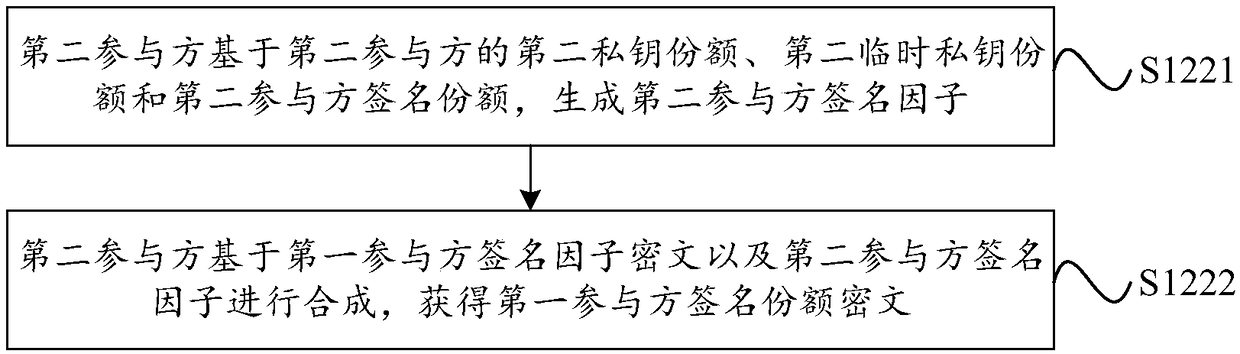
[0091] On the premise that the private key d is constructed by additive sharing, a temporary private key can be constructed by additive sharing, and its form can be recorded as k=k 1 +k 2 ; It is also possible to construct a temporary private key through multiplication and sharing, and its form can be recorded as k=k 1 k 2 . Where d is the shared private key, which is a complete private key, d 1 is the private key share held by participant 1 (referred to as the first private key share in the embodiment of this application), d 2 is the private key share held by participant 2 (denoted as the second private key share in this embodiment of the applicatio...
Embodiment 2
[0145] Embodiment 2: The private key is shared in the form of multiplication.
[0146] In one embodiment, the method of constructing a private key based on multiplication sharing may also be referred to as multiplication sharing. In an embodiment, when the private key is constructed by multiplication and sharing, its form can be recorded as d=d 1 d 2 -1.
[0147] On the premise that the private key is constructed by multiplication and sharing, a temporary private key can be constructed by multiplication and sharing, and its form can be recorded as k=k 1 k 2 ; It is also possible to construct a temporary private key through addition and sharing, and its form can be recorded as k=k 1 +k 2 . Where d is the shared private key, which is a complete private key, d 1 is the private key share held by participant 1 (referred to as the first private key share in the embodiment of this application), d 2 is the private key share held by participant 2 (denoted as the second private ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com