Blockchain secret key encryption and decryption methods and devices based on biological identification and terminal
A technology of biometric identification and encryption method, which is applied in biometric-based block chain secret key encryption and decryption methods, devices and terminals, and can solve user economic losses, user digital asset rights and interests attacks, and illegal stealing of block chain secret keys, etc. problems, to achieve the effects of not being easy to lose, increasing the difficulty of stealing, and ensuring the safety and reliability of storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
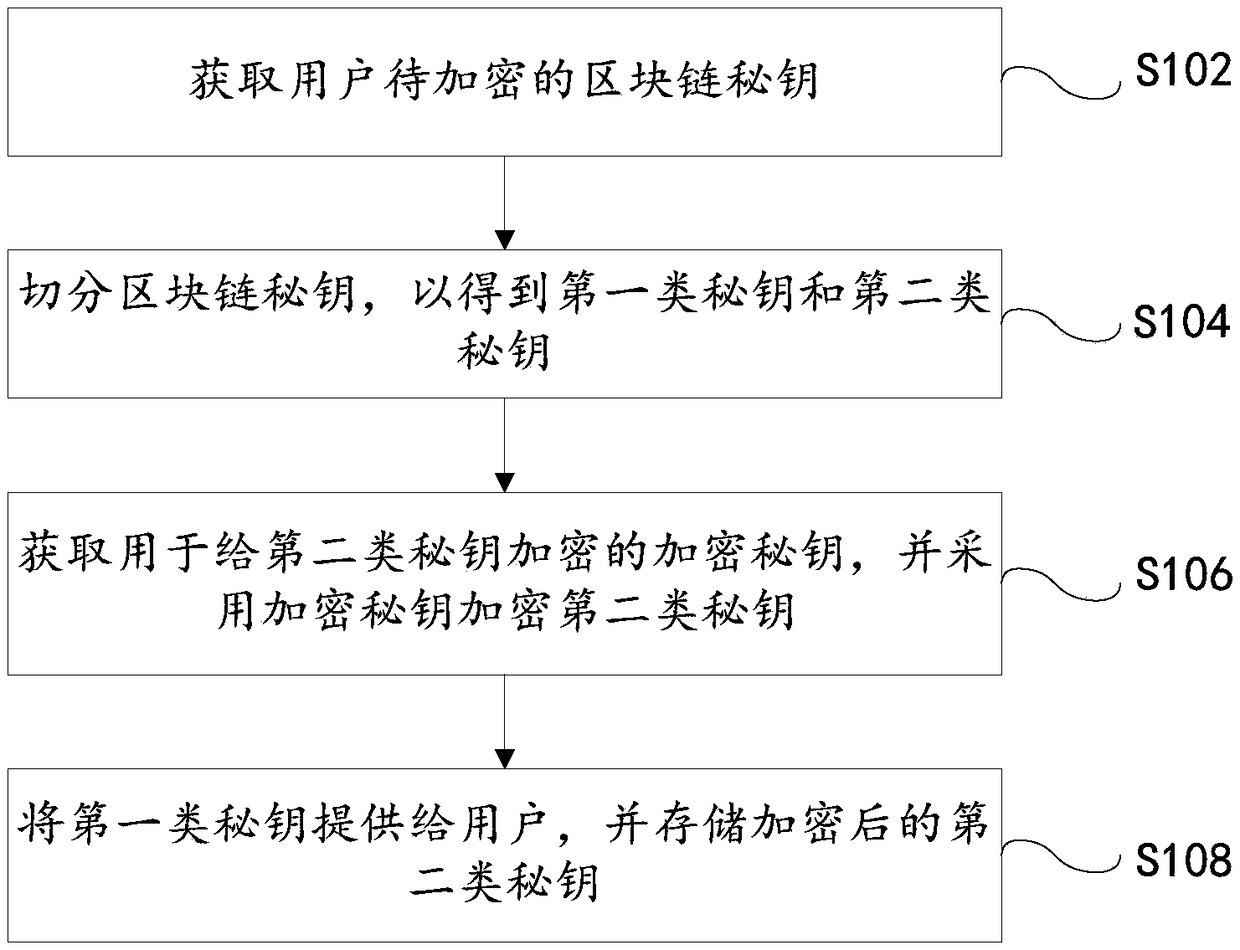
[0055] Obtain the blockchain secret key, and divide the blockchain secret key into sub-keys with a preset total number of shares. Assuming that the preset total number of shares is n, select a sub-key combination to form the first type of secret key , from which (n-a) molecular key combinations are selected to form the second type of key. For ease of understanding, in a simple implementation, it can be assumed that the blockchain key is divided into four parts ABCD, one of which is selected as the first type of key C, and three of them are selected as ABD. The second type of key.
[0056] The encryption key is generated by asymmetric encryption technology, where the encryption key includes a public key g and a private key s, and the private key s is associated with the user's biometric information, that is, the private key s is associated with the biometric information bound. The public key g corresponds to the private key s. Both the public key g and the private key s are s...
Embodiment approach 2
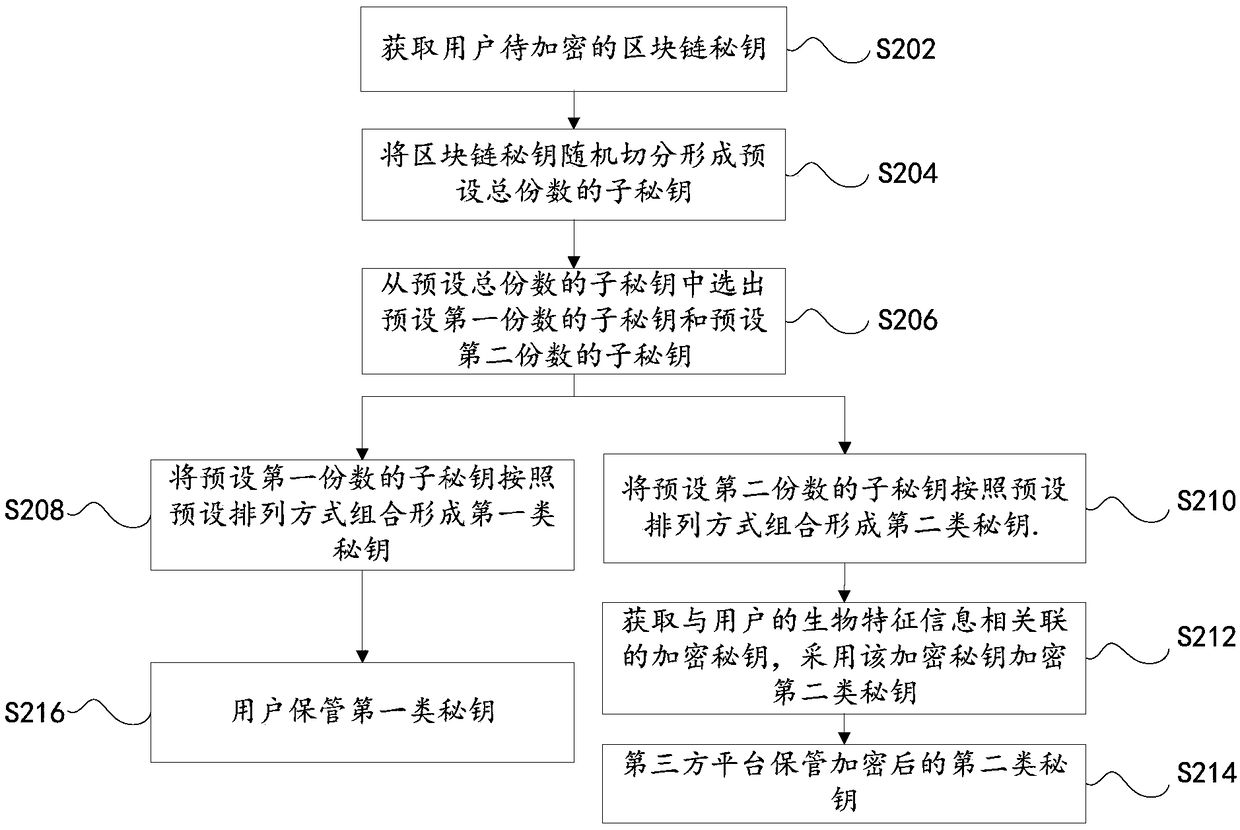
[0059] Obtain the blockchain secret key, divide the blockchain secret key into unequal sub-keys with a preset total number of shares, assuming that the preset total number of shares is n, select a sub-key combination to form the first type of secret key keys, from which (n-a) sub-keys are selected to combine to form the second type of keys. For ease of understanding, in a simple implementation, it can be assumed that the blockchain key is divided into four parts ABCD, one of which is selected as the first type of key C, and three of them are selected as ABD. The second type of key.
[0060] The encryption key g is generated by symmetric encryption technology, and the encryption key g is associated with the biometric information of the user, that is, the secret key g is bound to the biometric information.
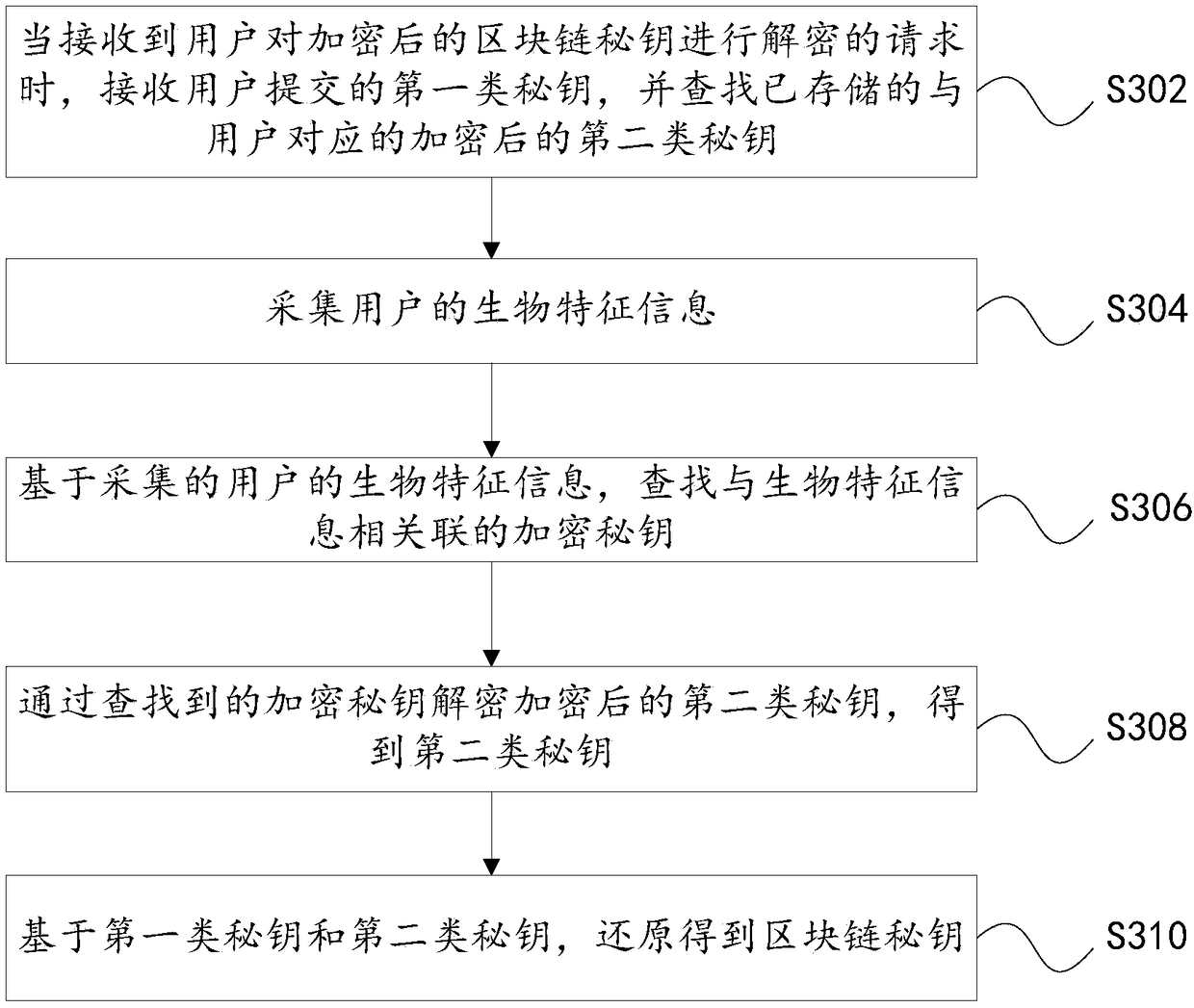
[0061] Encrypt part of the sub-keys of the second type of key with the above-mentioned encryption key g. The user retains the first type of secret key, and the third-party...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com