Method for enhancing authenticity and expressiveness of hidden image decrypted in digital image
A digital image and authenticity technology, applied in image communication, image enhancement, image analysis, etc., can solve counterfeiting and other problems, achieve the effect of increasing real-time performance and reducing the possibility of being counterfeited
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
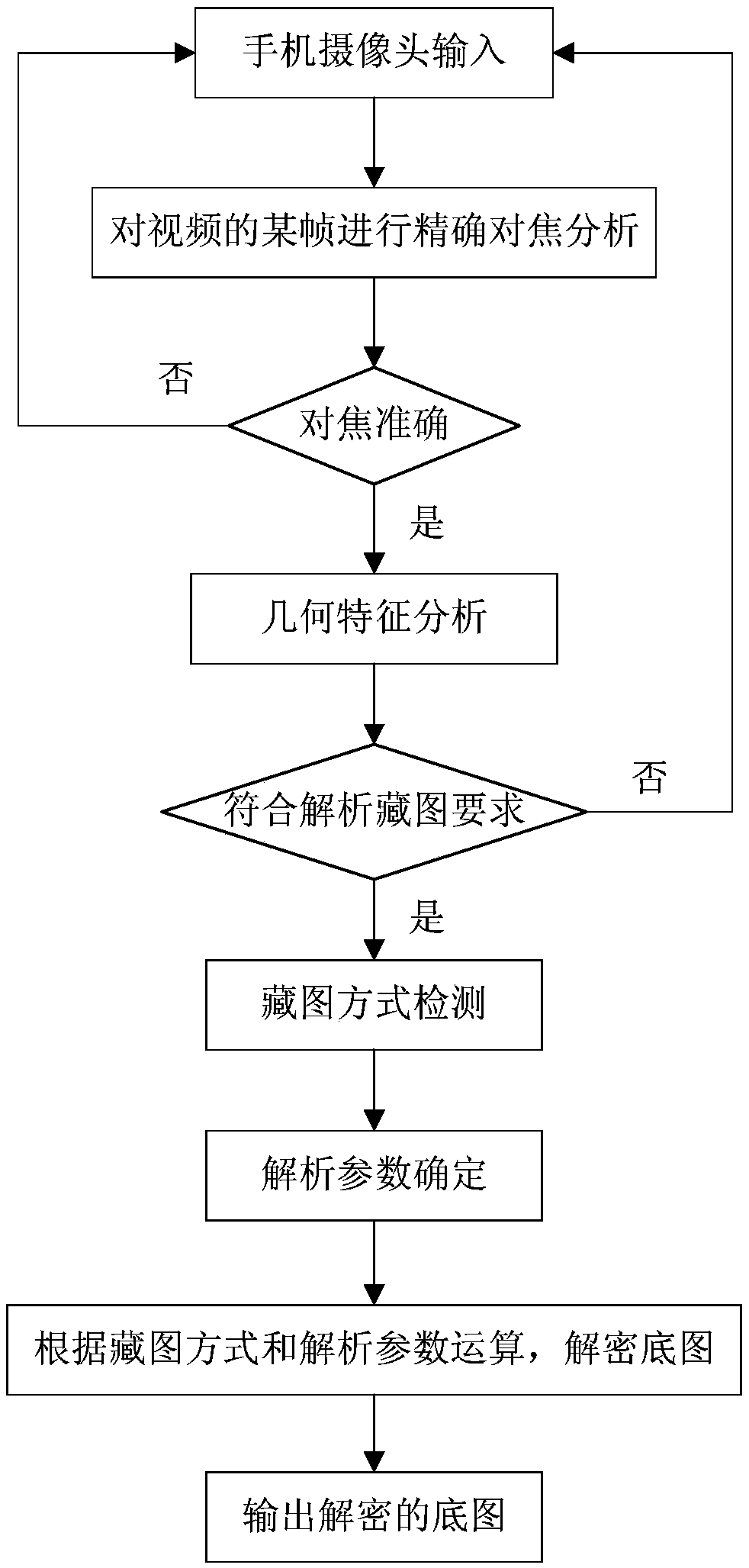
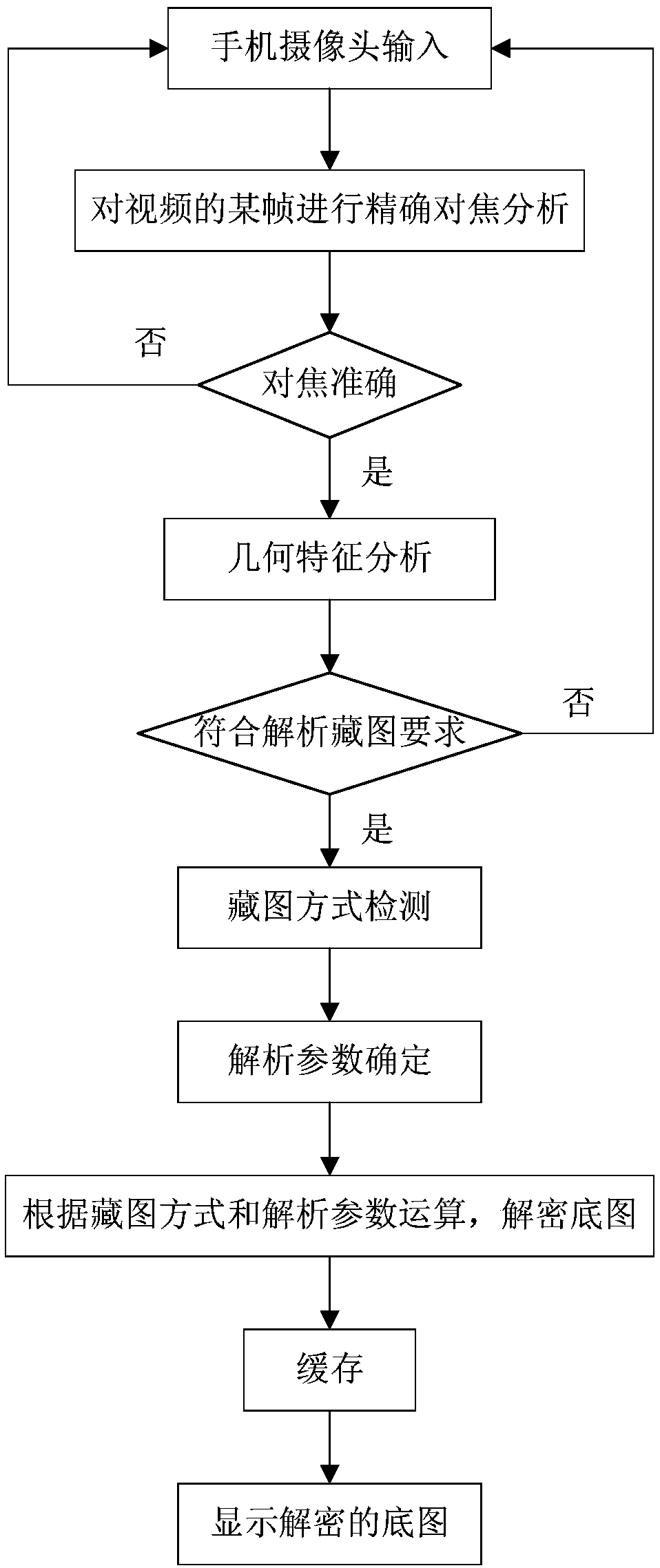
[0046] Through this embodiment, it is possible to understand the general process and difficulty of detecting a hidden image by a smart phone or a smart mobile device. Video is a series of discrete images with high acquisition frequency, so that visual persistence can be used to achieve visual continuity. Each discrete image is called a frame. Usually, the analytical interpretation of hidden images is done on a frame-by-frame basis.
[0047] The detection and decryption of the base map have specific requirements on the image quality of the captured or intercepted original image. Depending on the specific method of collecting pictures, the requirements are slightly different, but there are higher requirements for the focus and magnification of the shooting system.
[0048] Due to its high anti-counterfeiting and anti-copying functions, the technology of hiding images through the modulation of dot structure (for example: SI technology of Graphics Security System company, ICI tec...
Embodiment 2
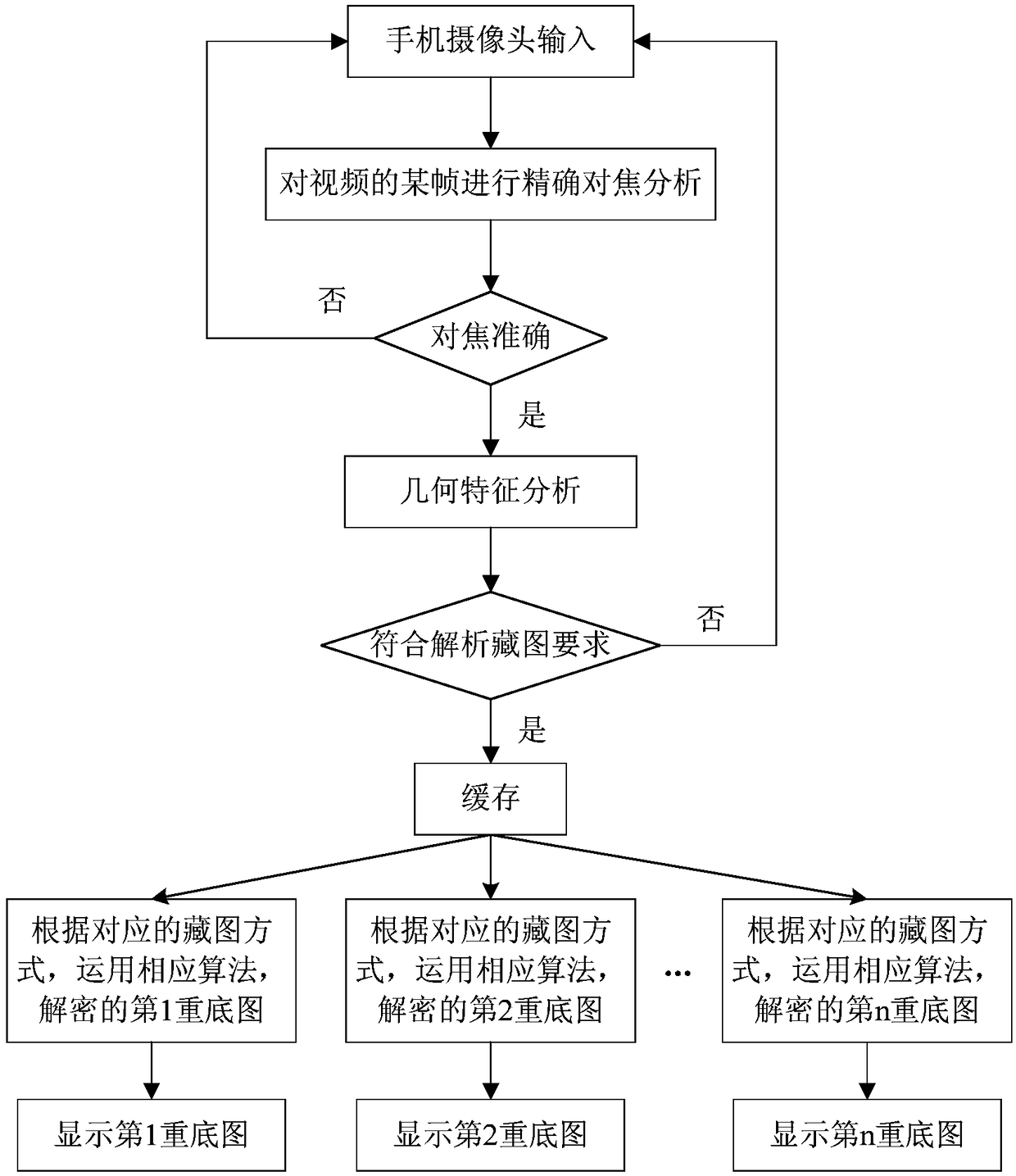
[0087] The decryption of the base map in the Tibetan printed matter is completed by a decryption method corresponding to the Tibetan map method combined with a set of parameters, and the change of the parameters can affect the detection effect of the base map. For example: the most common image hiding method is to modulate the phase of periodic dots, and the base image of the printed matter after the image is hidden by this method can be detected by a frequency-matched grating film. The change in the angle of the grating sheet can cause changes in the density and direction of the interference fringes (moire) when the base image is displayed. The movement of the grating sheet can cause a phase change, thereby causing the movement effect of interference fringes (Moiré). A similar effect can also be obtained from the digital basemap image decrypted by the smart phone or smart mobile device APP of such printed matter, such as Figure 6 As shown, the method is to make correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com