A data encryption authenticity verification method and system based on exchange server
A technology for data encryption and verification methods, applied in the field of data encryption authenticity verification based on Exchangeserver, can solve the problem that the test method does not have universality and generalizability, does not consider the diversity and compatibility of existing network application scenarios, and cannot. Ensure that the functions are actually available and other issues, to achieve the effect of highlighting the substantive features, verifying the conclusion is true and reliable, and easy to operate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Specific embodiments of the present invention will be described below in conjunction with the accompanying drawings.
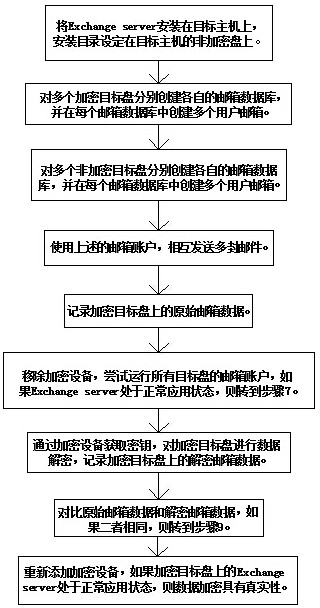
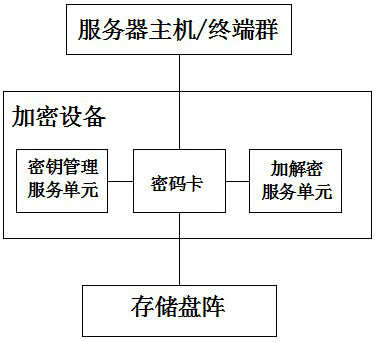
[0029] Such as figure 1 Shown a kind of data encryption authenticity verification method based on Exchange server, comprises the following steps:
[0030] Step 1: Install the Exchange server on the target host, and set the installation directory on the non-encrypted disk of the target host;
[0031] Step 2: Create separate mailbox databases for multiple encrypted target disks, and create multiple user mailboxes in each mailbox database;
[0032] Step 3: Create separate mailbox databases for multiple non-encrypted target disks, and create multiple user mailboxes in each mailbox database;
[0033] Step 4: Use the above email accounts to send multiple emails to each other;
[0034] Step 5: Record the original mailbox data on the encrypted target disk. The original mailbox data includes mailbox database information, mailbox account information and mail d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com