An access request processing method and system
A technology for access requests and processing methods, applied in transmission systems, electrical components, etc., can solve problems such as attacking user websites, threatening the security of static resources of web servers, and affecting the results of dynamic resource access, so as to improve security and resist malicious The effect of the attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
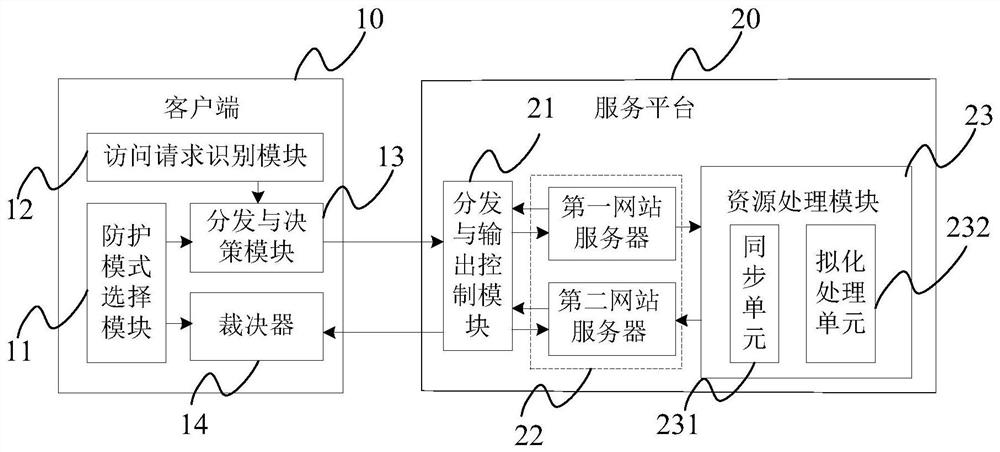
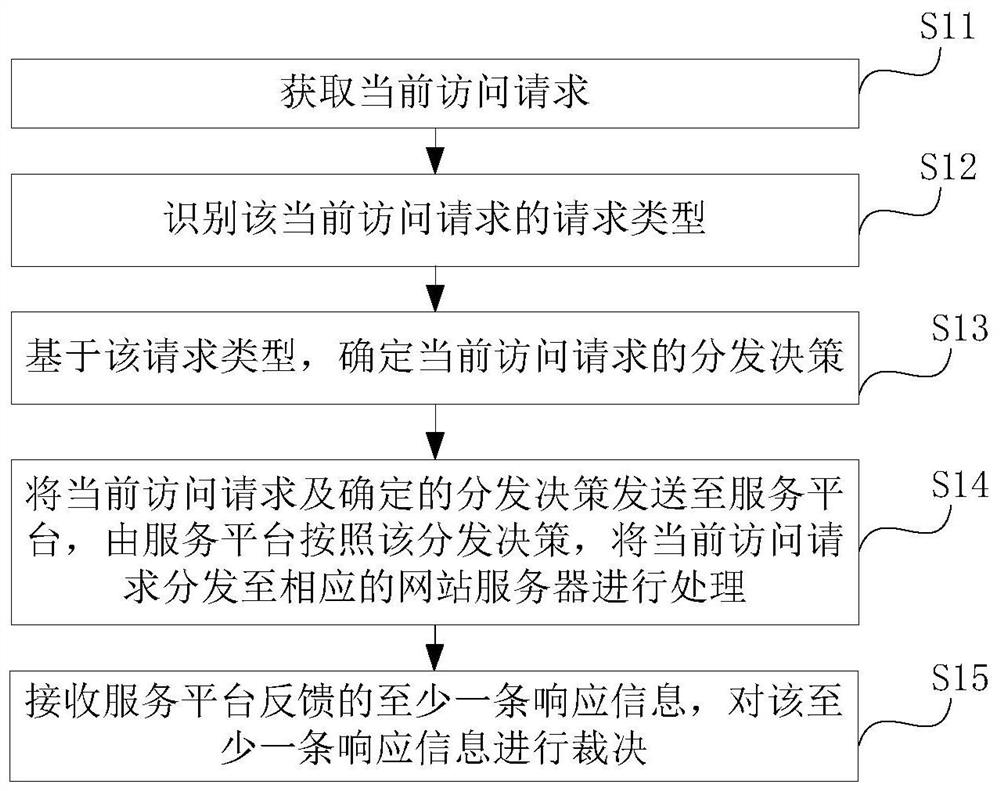
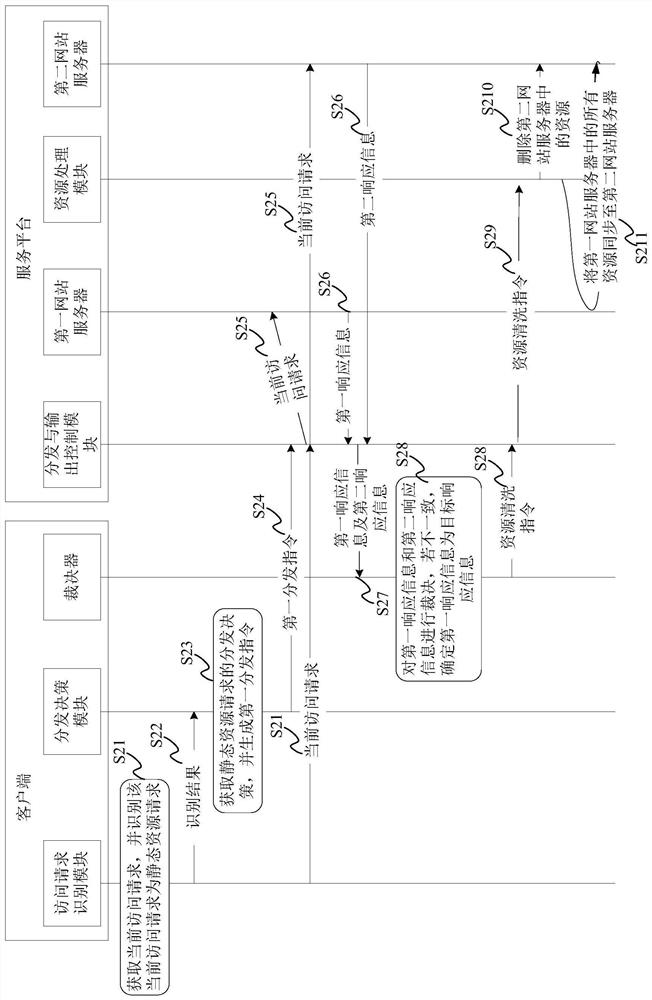
[0066] The inventors of the present invention found that in the prior art, the web server does not perform any differentiated processing on the access request initiated by the user, and directly feeds back the requested dynamic resource or static resource to the user client, which causes the web server and User clients are attacked by dark links hidden in dynamic resource access.
[0067] Based on this, the inventor proposes to classify access requests initiated by users, and to process and respond to access requests according to corresponding processing rules for different types of access requests. That is to say, the purpose of isolating the dynamic resource access that may cause security problems is to prevent it from affecting the user's access to the static resource, thereby greatly improving the security of the static resource of the Web server.
[0068] Moreover, the inventor also proposes mimetic processing of dynamic resources to ensure that access to dynamic resource...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com