A cloud environment data integrity verification method based on fully homomorphic encryption
A data integrity, fully homomorphic encryption technology, applied in the field of information security, can solve the problems of inappropriate cloud storage massive data service mode, does not support public verification, high computational overhead, etc., to reduce communication overhead, achieve significant effects, logically tight effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
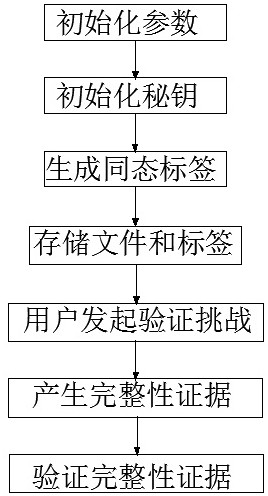
[0039] Specific examples are given below to further describe the technical solution of the present invention in a clear, complete and detailed manner. This embodiment is the best embodiment on the premise of the technical solution of the present invention, but the protection scope of the present invention is not limited to the following embodiments.
[0040] During the actual implementation of the present invention, the cloud storage server sends the calculated integrity proof to the user without including files or subsets of the files. Carry out verification calculations, and judge whether the target data block of this verification maintains integrity in the cloud according to the results of local calculations. Diffie-Hellman scheme, RSA scheme and bilinear pairing are common algorithms with homomorphic properties in this type of protocol.
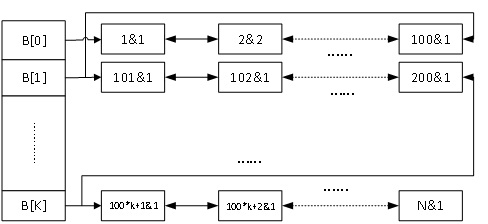
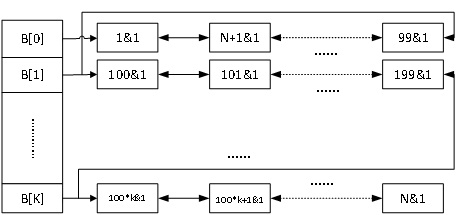
[0041] Such as figure 1 As shown, a method for verifying data integrity in a cloud environment based on fully homomorphic encryption i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com