A method, device and system for secure pairing
A security device and security technology, applied in the direction of computer security devices, instruments, digital data authentication, etc., can solve the problems of no secure pairing of the security device and the host device, and the host device is in an untrusted environment, so as to achieve safe pairing, reduce The effect of safety costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
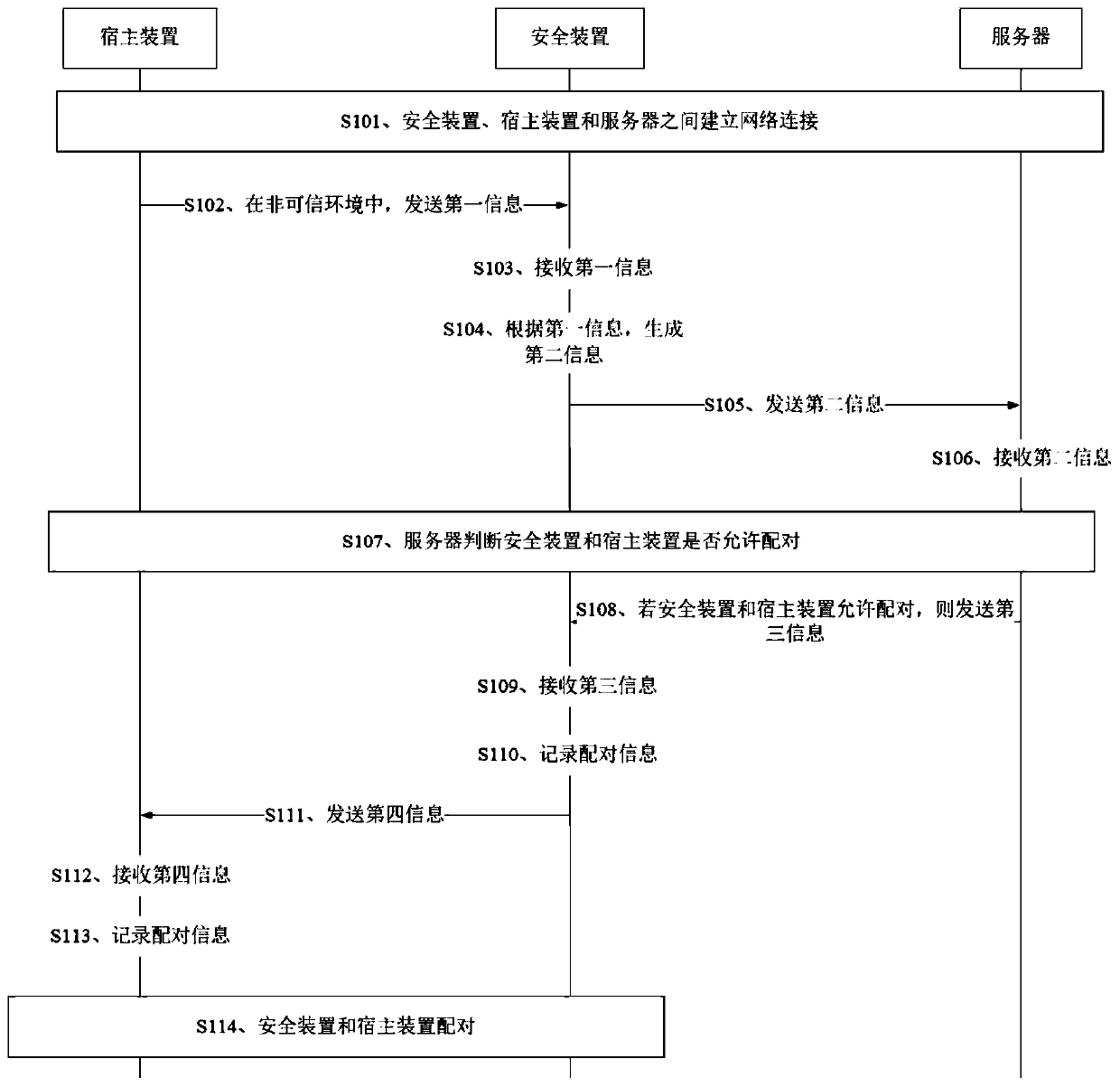
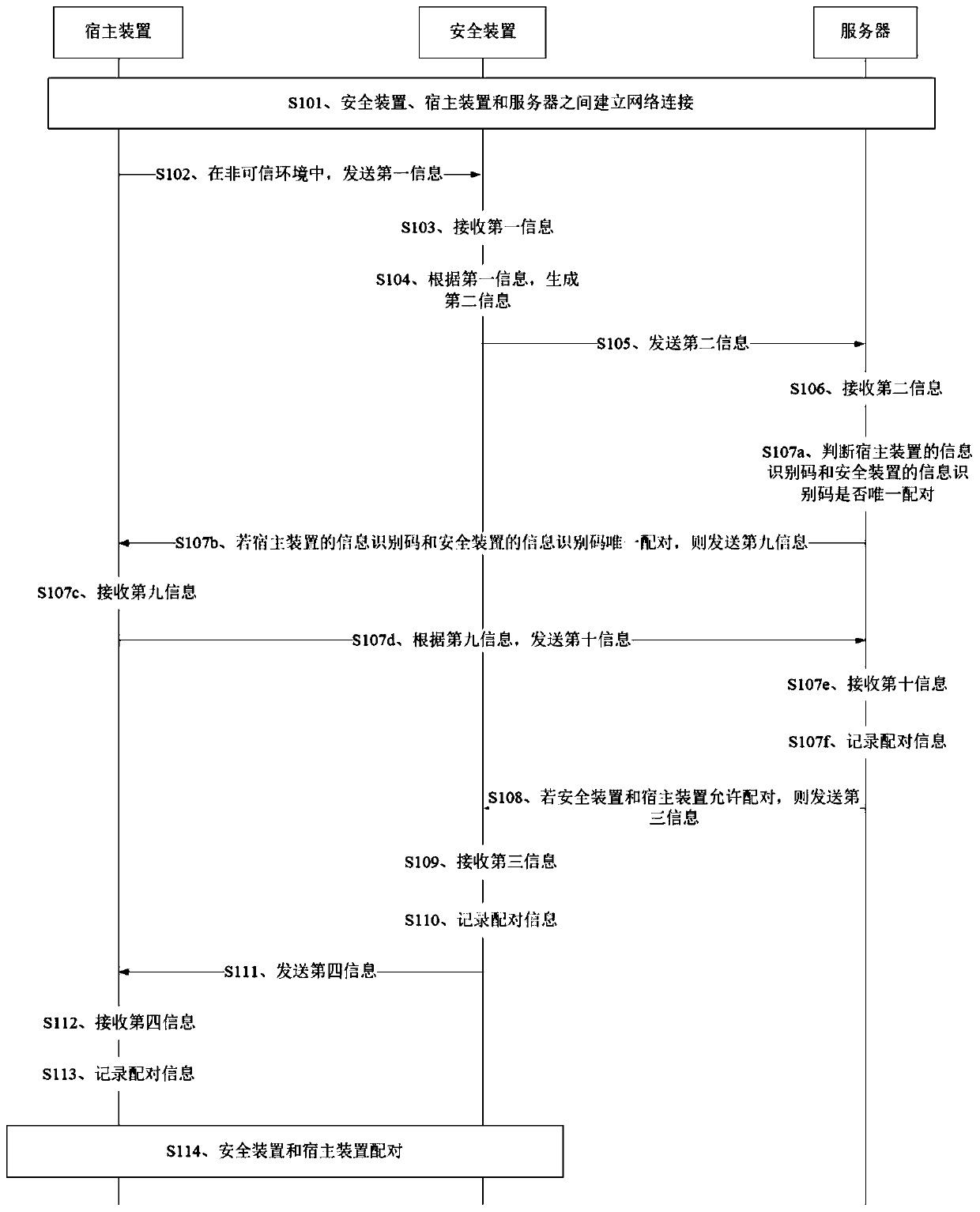
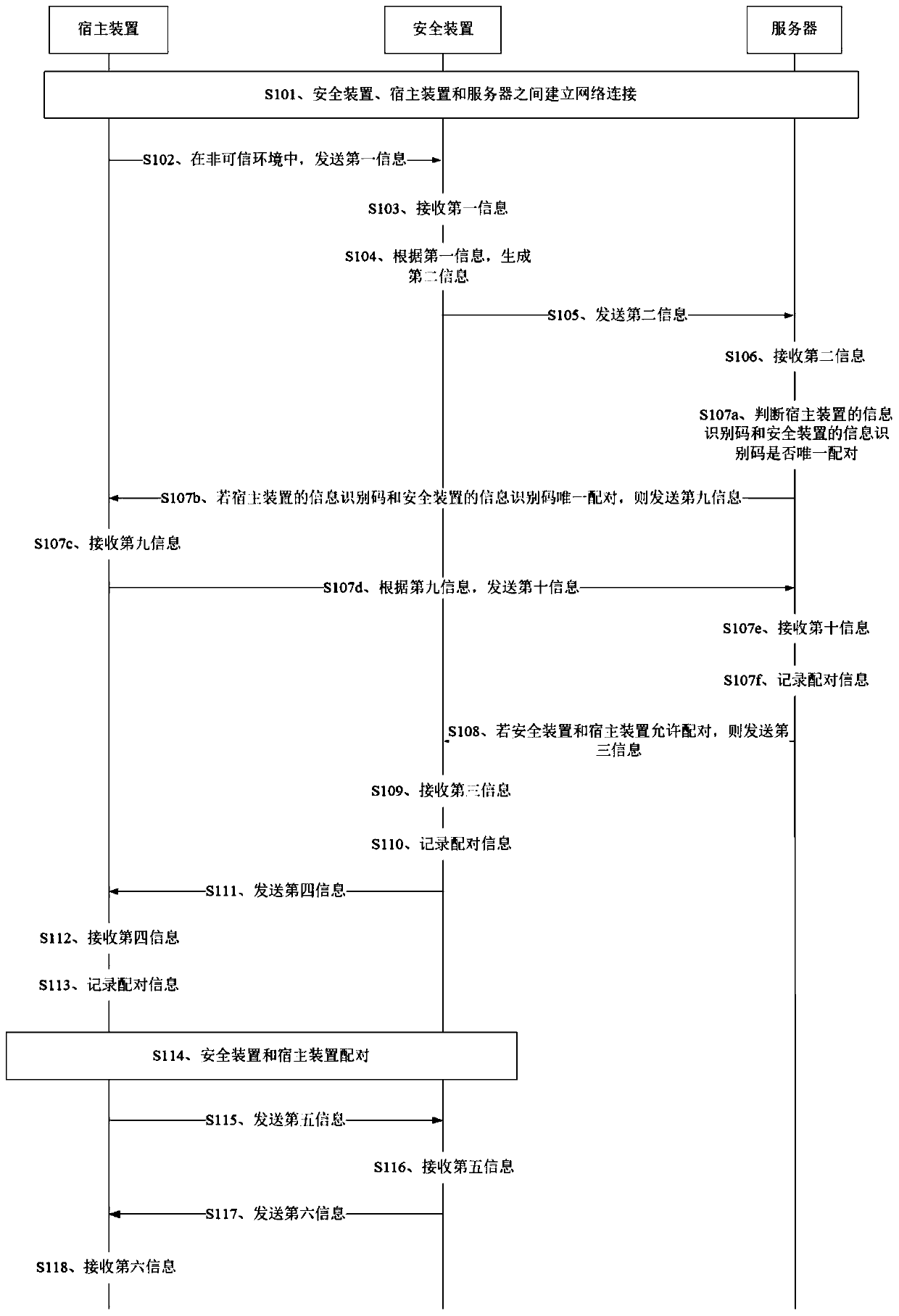
[0077] figure 1 It is a schematic flowchart of a secure pairing method provided by Embodiment 1 of the present invention. This embodiment can be applied to scenarios where the security device is paired with the host device and there is no information about pairing with the security device in the host device. The method specifically Including the following steps:
[0078] S101. Establish a network connection between the security device, the host device and the server.
[0079] The network connection established between the security device, the host device and the server may be a trusted network connection (that is, a trusted environment) or an untrusted network connection (that is, an untrusted environment), which is not specifically limited in this embodiment of the present invention.
[0080] It should be noted that the host device may be a user equipment or an APP loaded in the user equipment, wherein the user equipment includes but is not limited to smart phones, tablet co...
Embodiment 2
[0135] Figure 5 A schematic structural diagram of a security device provided by Embodiment 2 of the present invention includes a receiving module 10 , a processing module 11 and a sending module 12 .
[0136] The receiving module 10 is configured to receive first information sent by the host device in an untrusted environment, wherein the first information includes the information identification code of the host device and the certificate of the host device;
[0137] The processing module 11 is configured to generate second information according to the first information received by the receiving module 10, wherein the second information includes the information identification code of the host device, the certificate of the host device, and the information identification code of the security device;
[0138] The sending module 12 is configured to send the second information generated by the processing module 11 to the server, so that the server judges whether the security devi...
Embodiment 3
[0150] Figure 7 A schematic structural diagram of a host device provided by Embodiment 3 of the present invention includes a sending module 20 and a receiving module 21 .
[0151] The sending module 20 is configured to send first information to the security device in an untrusted environment, where the first information includes the information identification code of the host device and the certificate of the host device;
[0152] The receiving module 21 is configured to receive fourth information sent by the security device to pair the security device with the host device, wherein the fourth information includes a certificate of the security device.
[0153] further, Figure 8 It is a schematic structural diagram of another host device provided in Embodiment 3 of the present invention, and the host device further includes a storage module 22 .
[0154] The storage module 22 is configured to record pairing information, wherein the pairing information includes the correspond...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com