Right setting method and device
A permission configuration and permission technology, applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of heavy workload and slow response, achieve the effect of achieving flexibility and improving the efficiency of permission setting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
[0035] Rights management is an important means to ensure information security. Rights management refers to the security rules or security policies set by the system, so that users can access and only access resources authorized by themselves based on their own account information. Generally speaking, enterprises will set up a small number of system administrators, and configure everyone's permissions through the system administrators. However, this permission setting method will cause the problems of heavy workload and slow response.
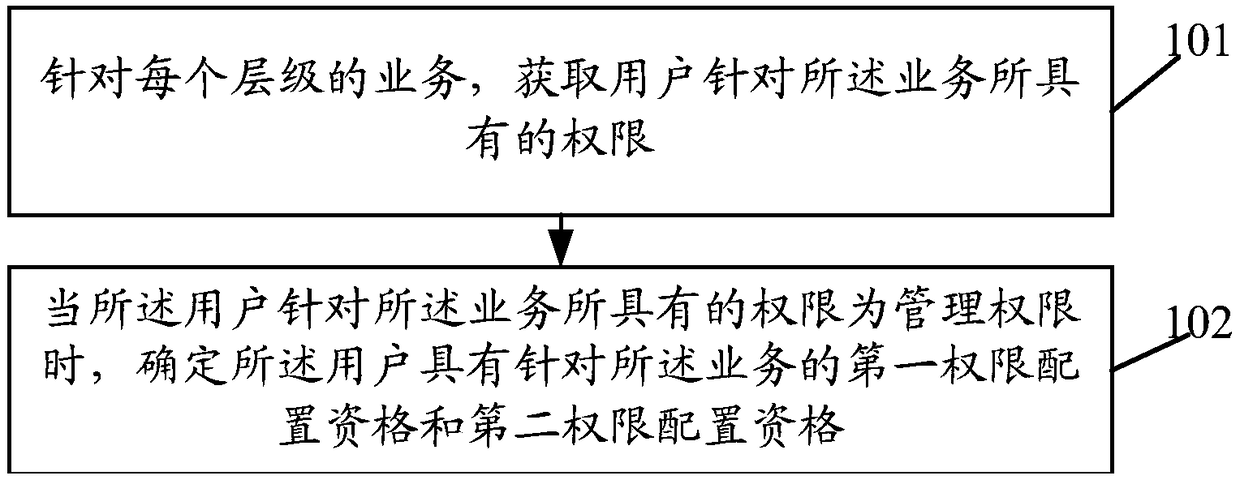
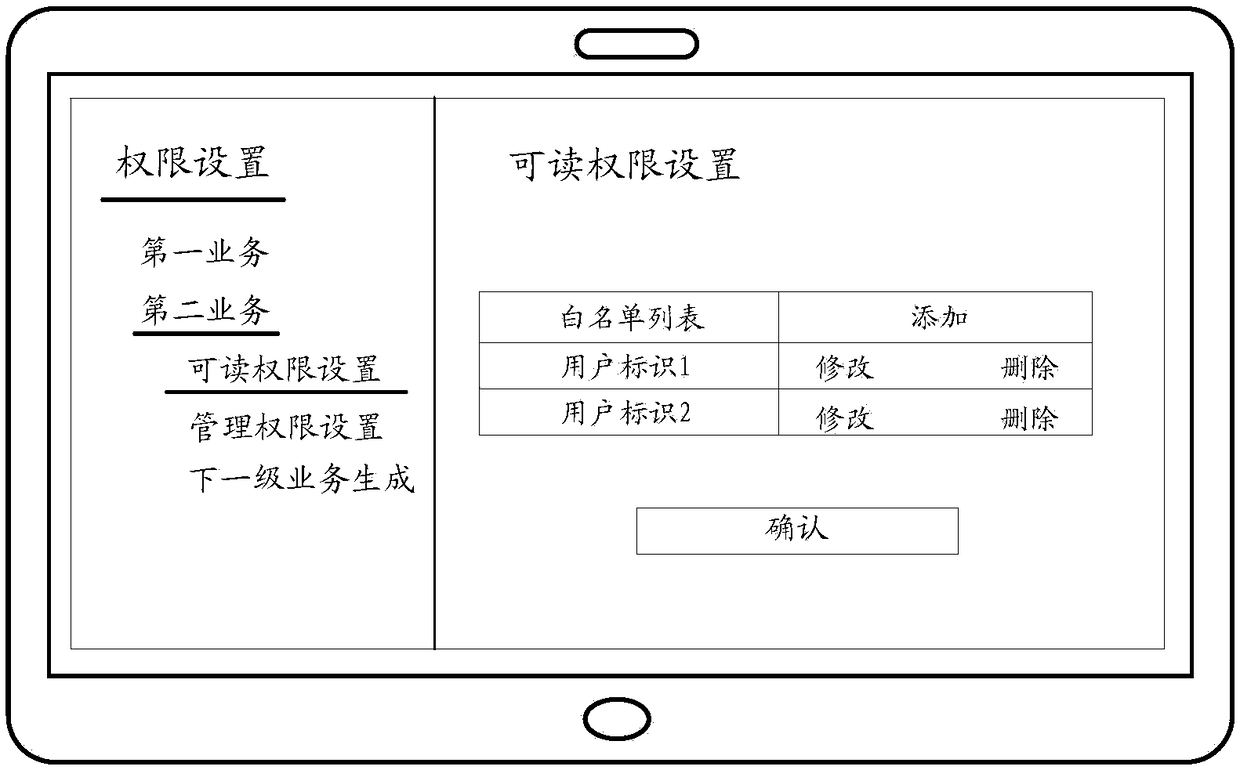
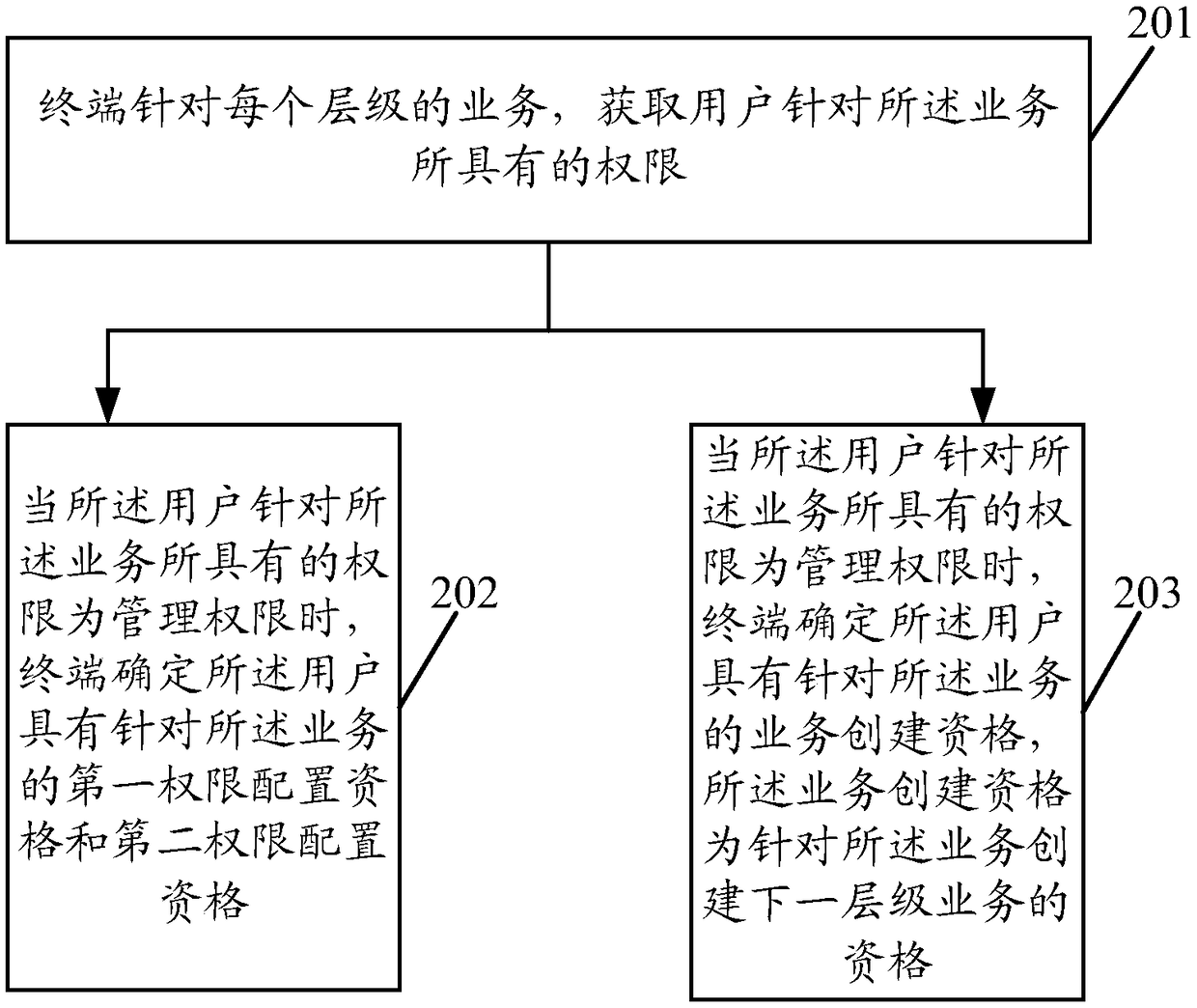
[0036] In order to solve this problem, an embodiment of the present application provides a permission setting method, which can be applied to a business that includes at least two levels, and each level of business is set with management permissions and readable permi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com