Biometric authentication techniques
A lighting mode, camera technology, applied in biometric identification, digital data authentication, computing, etc., can solve the problem of incorrectly indicating the correct user, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
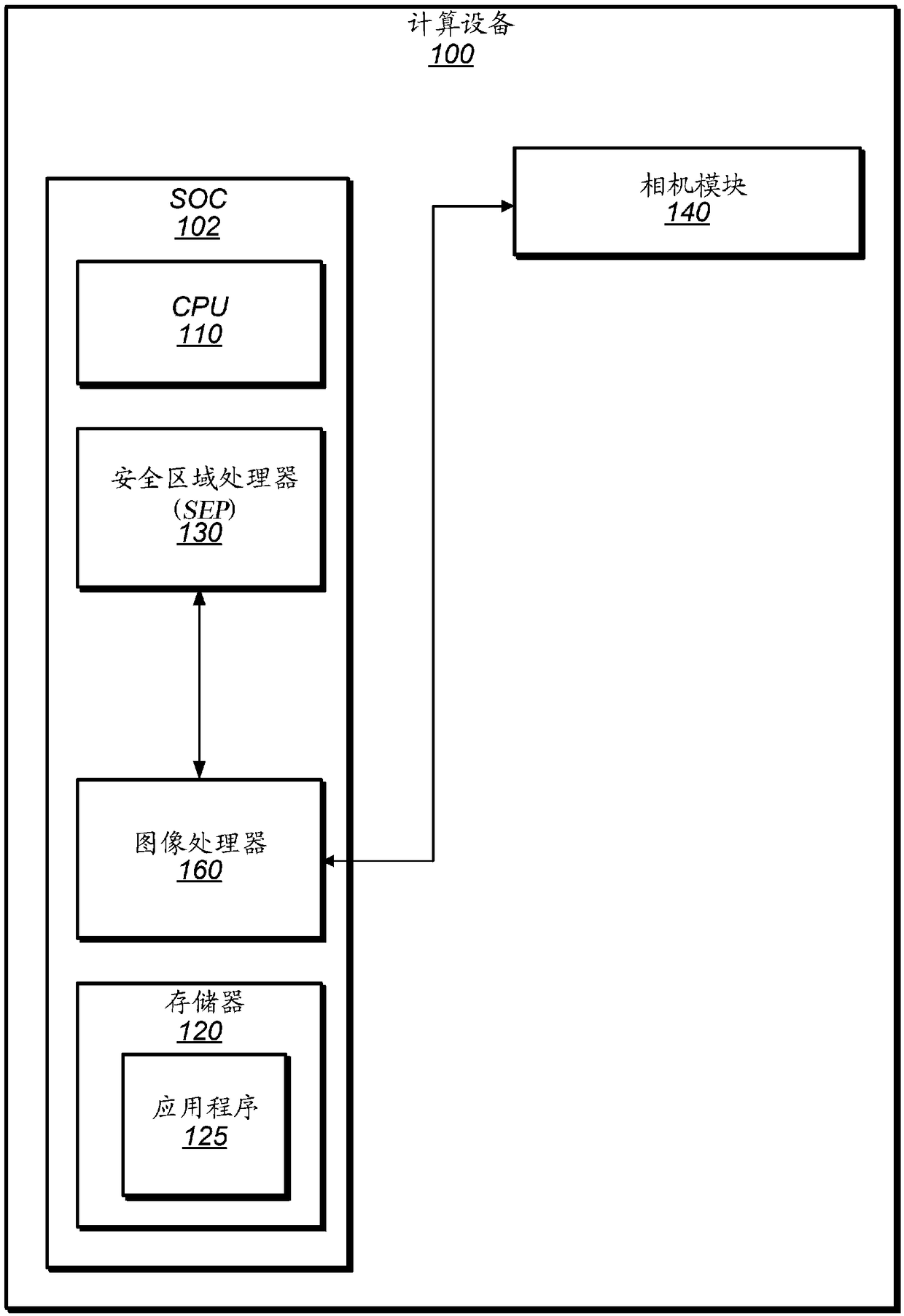
[0026] Overview of Exemplary Devices
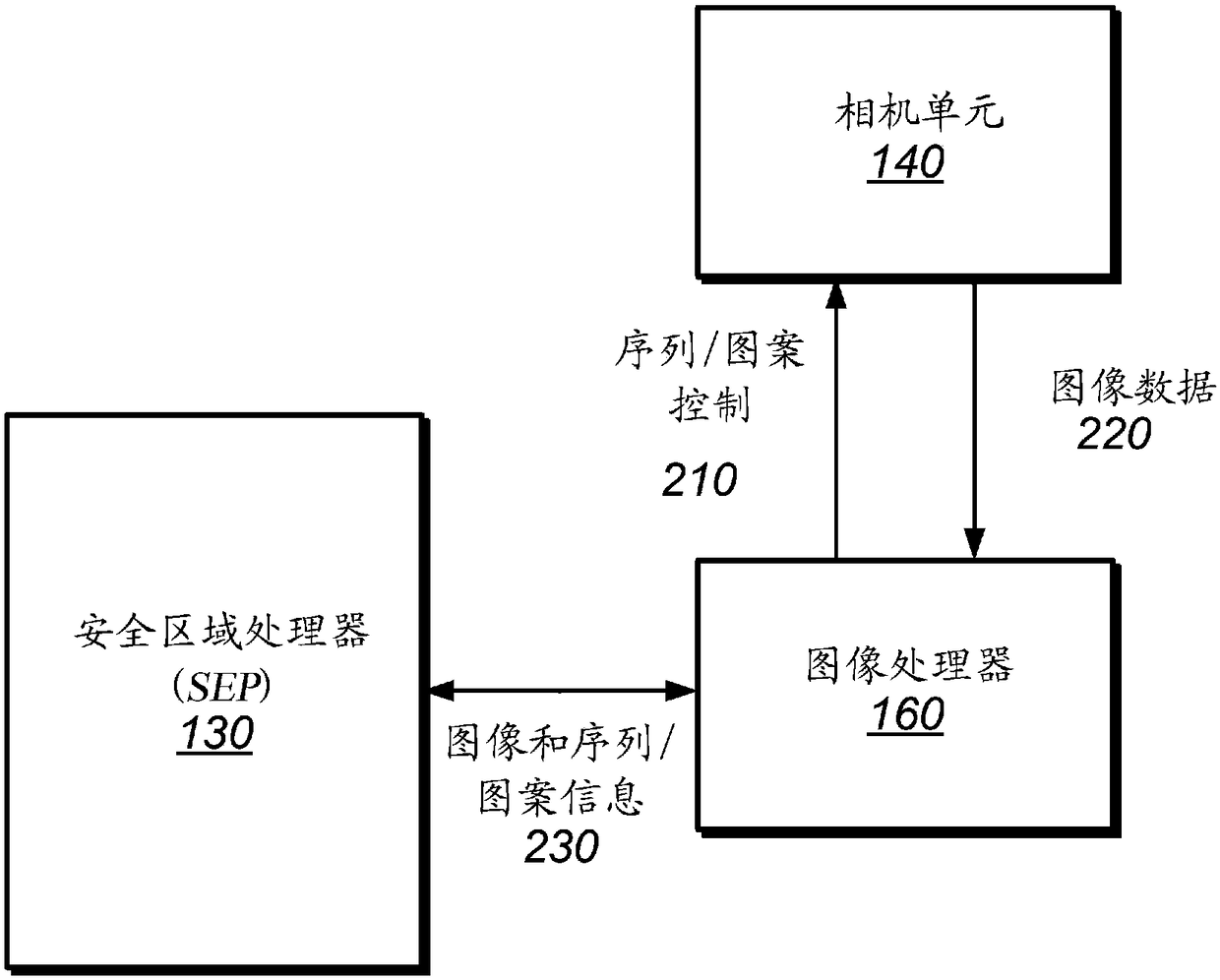
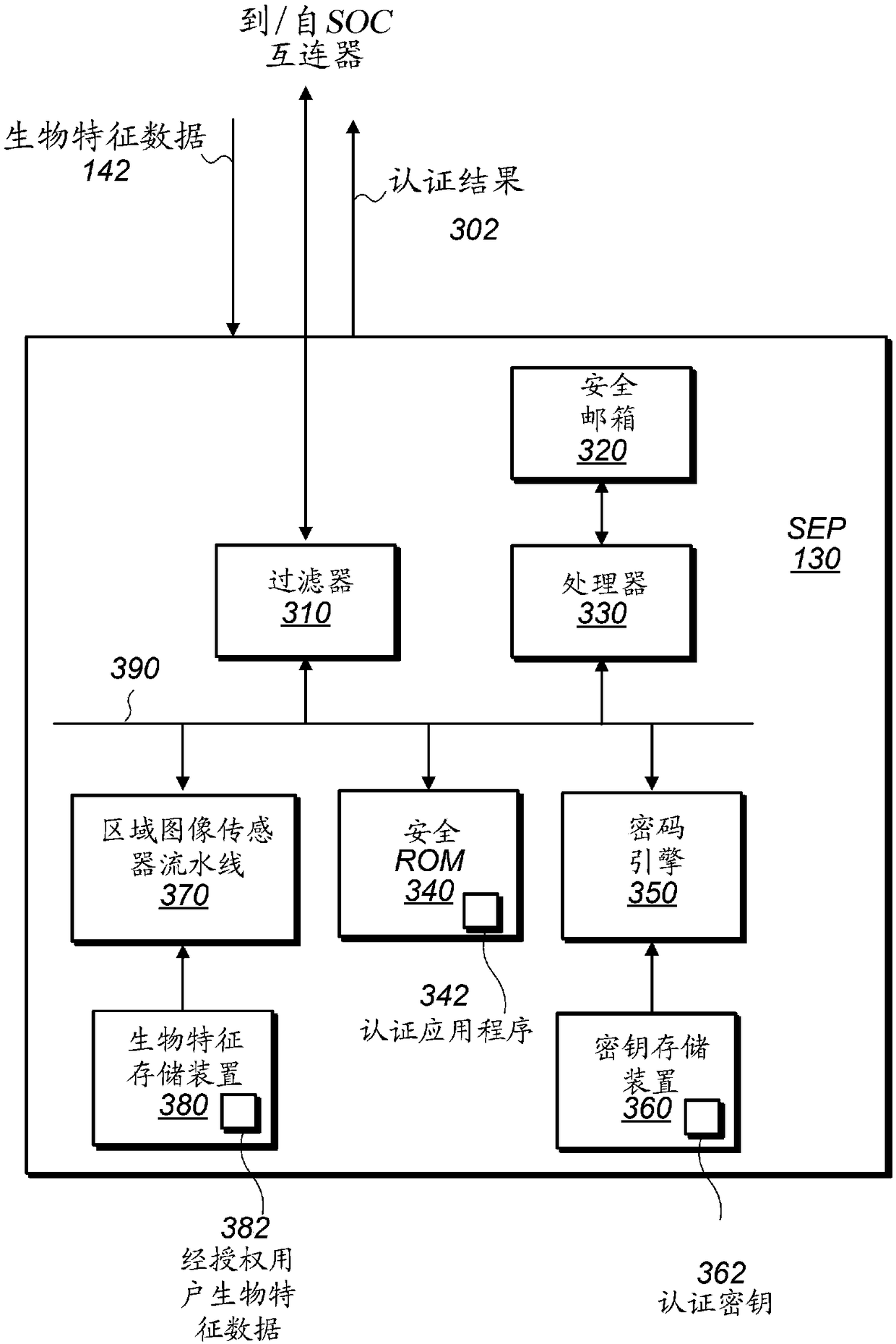
[0027] This disclosure generally relates to techniques for preventing spoofing or replay of biometric data, such as images used for facial recognition. A "replay" attack involves attempting to authenticate an individual using previously captured biometric information, typically valid, such as image data of the face of an authorized person who has previously passed biometric authentication. A malicious entity may attempt to show a previously captured image of a user to, for example, the device's camera in order to pass an authentication process as a registered user of the device. "Spoofing" attacks often use invalid data, such as data from another device or module purporting to be from the device's camera, or images of masks, statues, 3D projections, etc. that are not the actual current image of the known user. For example, a malicious entity could send a signal pretending to be from the device's camera unit to trick the device into think...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com