A verification and optimization method and system for a single point of failure in power communication services
An optimization method and power communication technology, applied in the field of network communication, can solve the problems of hidden danger of single node failure, long time-consuming inspection and maintenance, low degree of automation, etc., and achieve the effect of eliminating hidden danger of single point failure, saving manpower and material resources, and high degree of automation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
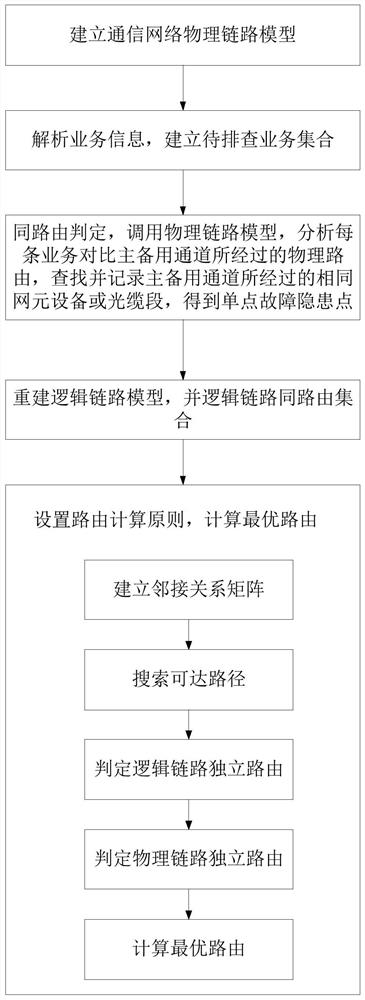
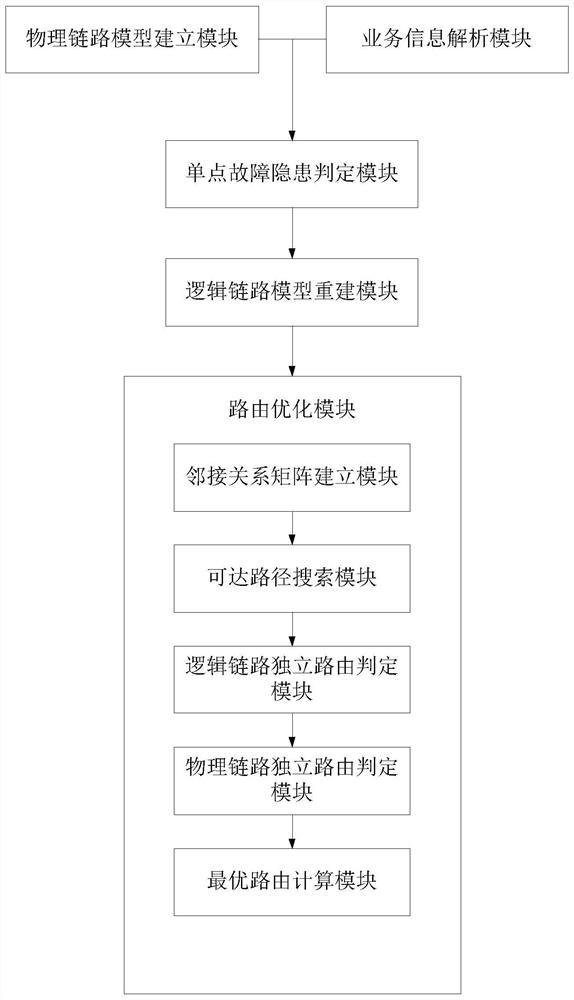
[0045] Such as figure 1 , figure 2 As shown, the method for checking and optimizing the single point failure of the power communication service of the present invention includes the following steps:
[0046] (1) Establish a physical link model of the communication network, including all network element equipment of the entire communication network, and the name of the optical cable section interconnected between each network element, the length information of the optical cable, and the occupied optical core resources;
[0047] (2) Analyze the full amount of business information of the communication network management server, obtain business type information and business logic channel routing information according to the keywords in the business configuration information, and establish a set of services to be checked, wherein the set of services to be checked can be divided into the following according to the type of business Business subsets: protection, security control, au...
Embodiment 2
[0100] On the basis of embodiment 1, the difference is that: the principle of routing optimization is set to select the minimum transit principle, k1=1, k2=k3=0 are set; the total weight of each route is calculated in the physically independent routing set, namely The sum of the weights of each segment passed by the entire route defines the total weight W=∑Pi,j; according to the minimum transit principle selected by the user, the optimal route for the user's needs is calculated.
Embodiment 3
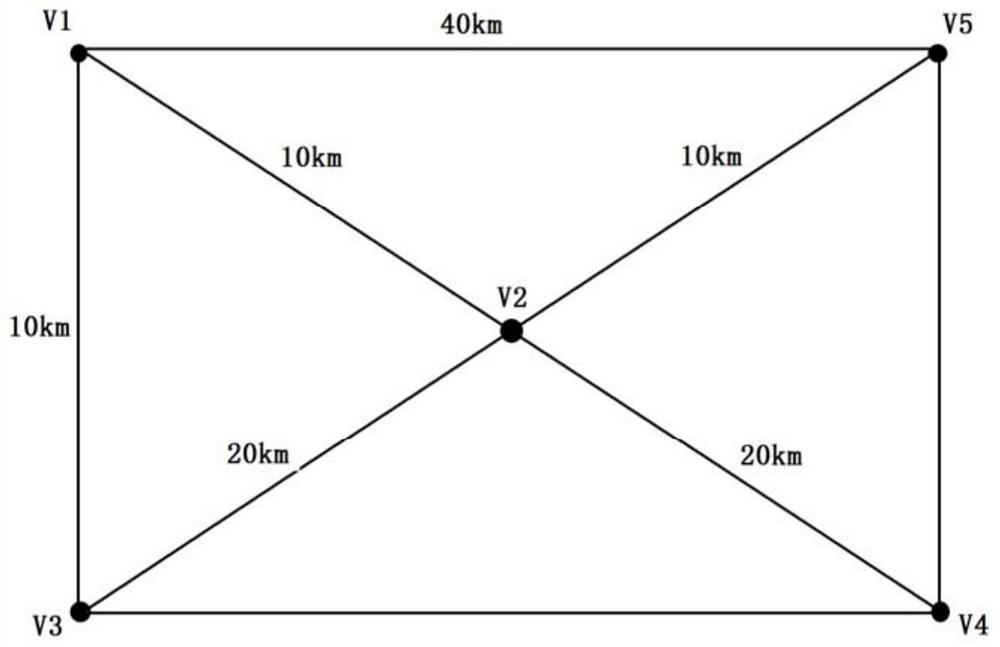
[0102] On the basis of Embodiment 1, the difference is that the reachable route search uses the depth-first algorithm to traverse the adjacency matrix, stop when it encounters an end node or a branch forms a loop from the starting point, and records when it reaches the target node. Thereby, the paths of reachable routes are obtained, and a set of reachable routes is established.
[0103] Using the depth-first algorithm, not all nodes are reserved, and the expanded nodes are popped out and deleted from the database. Generally, the number of nodes stored in the database is the depth value, which occupies less space. When there are many nodes in the search tree, other methods are used. It is easy to cause memory overflow, and it is more convenient to use the depth-first algorithm to solve it.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com