Network access device
A network access device and server-side technology, which is applied in the field of network access devices, can solve problems such as hidden dangers in network security and lack of network security protection measures, and achieve the effects of improving security performance, solving authentication and security problems, and being easy to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
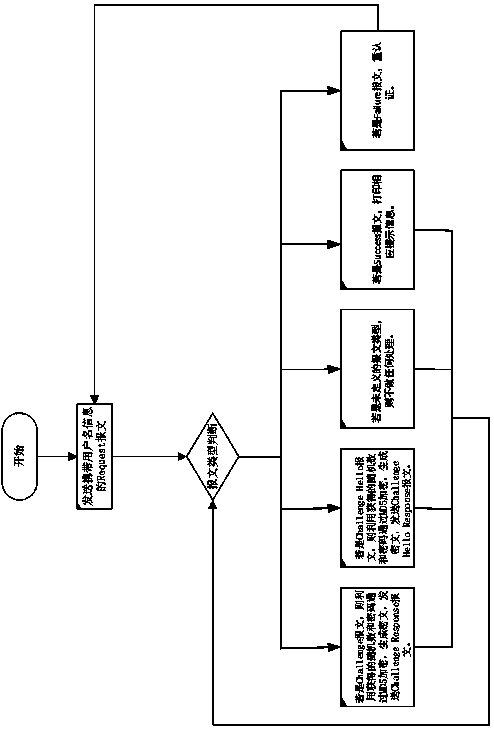
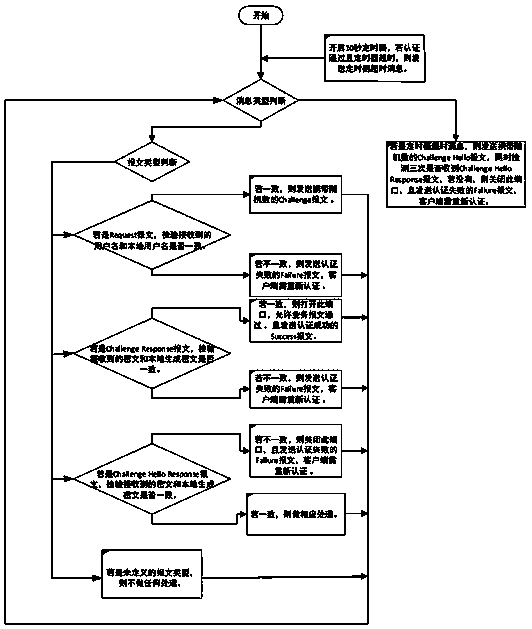
[0027] This embodiment provides a network access device. The network access device includes a client device and a server device. The process authentication is performed between the client device and the server device by adding random values. If the process authentication passes, the The service message is passed, and at the same time, re-authentication is performed between the client device and the server device, and if the re-authentication fails, the client re-authenticates.
[0028] Specifically, the server-side device adds an entry of MAC, port number, user name and password of the client; the password in the entry of the password is stored using the RC4 encryption method; the client device adds the MAC of the server, port No., user name and password, and the password is saved using the RC4 encryption method. After the authentication is completed, the client can access the server.
[0029] Specifically, the re-authentication includes defining a threshold value, the server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com