A method and device for cross-device individual identification based on privacy protection
A recognition method and cross-device technology, applied in digital data protection, character and pattern recognition, computer security devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
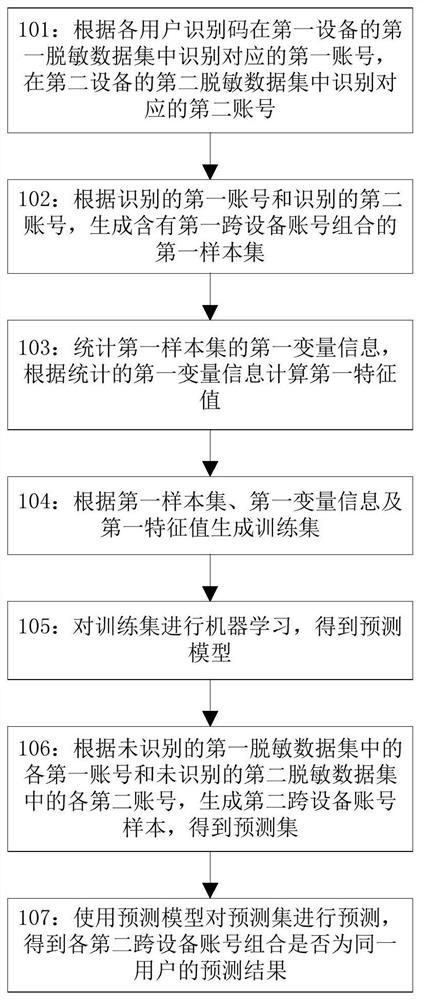
[0094] According to the implementation mode of the present application, a method of cross-device individual identification based on privacy protection is proposed, such as figure 1 shown, including:
[0095] Step 101: Identify the corresponding first account in the first desensitized data set of the first device according to each user identification code, and identify the corresponding second account in the second desensitized data set of the second device;
[0096] Wherein, the user identification code is the unique identifier of the user; the first device and the second device are different devices, and may also be different devices in different network environments; the first desensitization data set includes desensitization data sets of each user on the first device The first desensitized account and the first recorded data corresponding to the first account; the second desensitized data set includes the second account of each user on the second device and the second recor...
Embodiment 2
[0220] According to the implementation of the present application, a device for cross-device individual identification based on privacy protection is also proposed, such as Figure 11 shown, including:
[0221] The identification module 201 is configured to identify a corresponding first account in the first desensitized data set of the first device according to each user identification code, and identify a corresponding second account in the second desensitized data set of the second device;
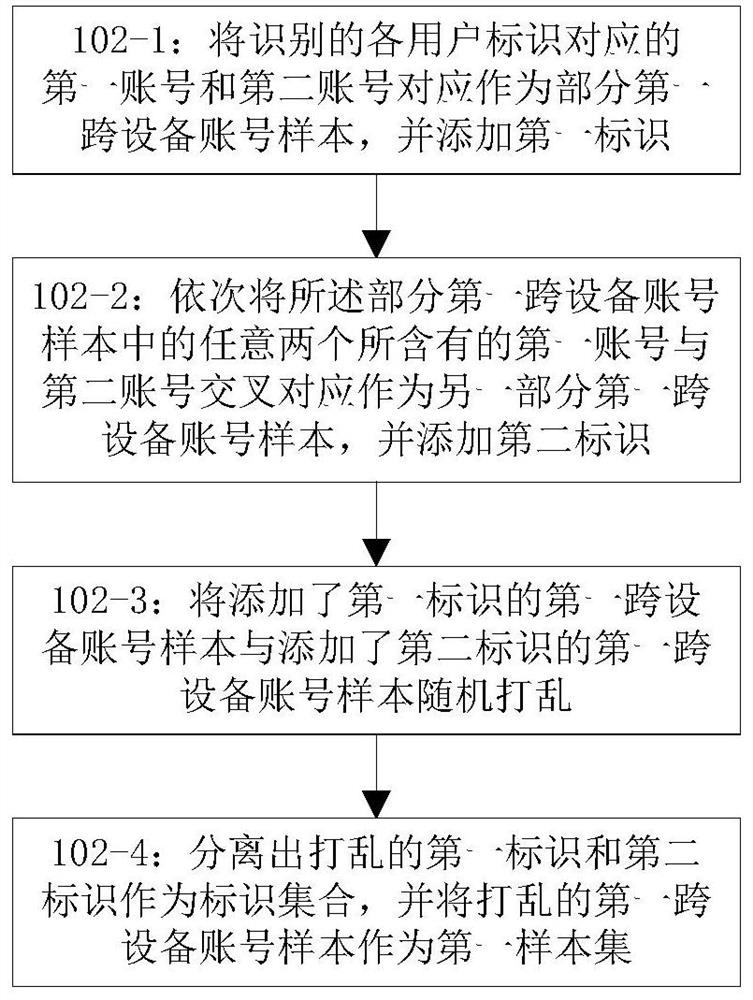
[0222] The first generation module 202 is configured to generate a first cross-device account sample according to the first account and the second account identified by the identification module 201, to obtain a first sample set;
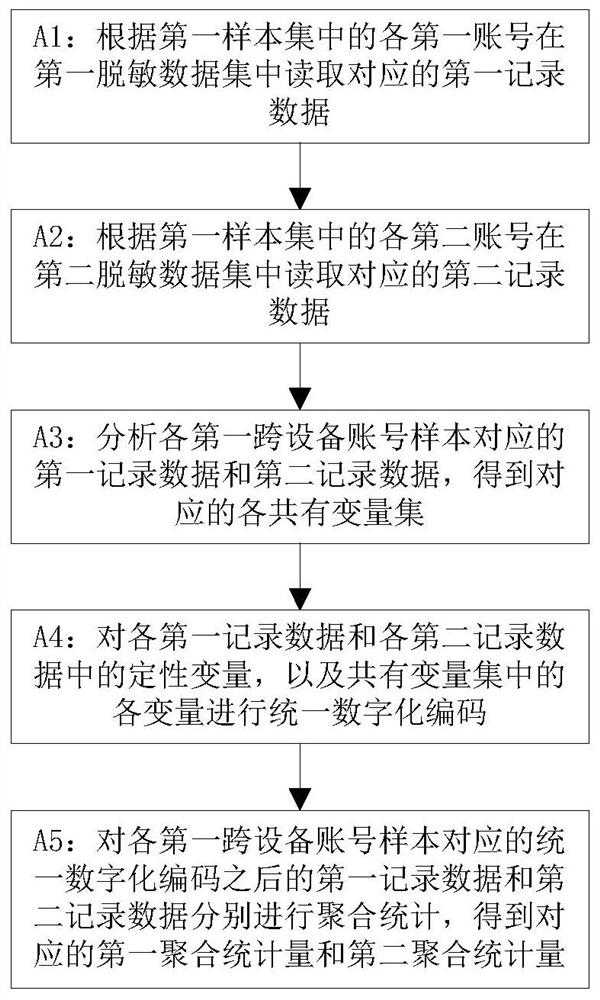
[0223] A first statistical module 203, configured to count first variable information of the first sample set;
[0224] A first calculation module 204, configured to calculate a first feature value according to the first variable information;
[0225] The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com