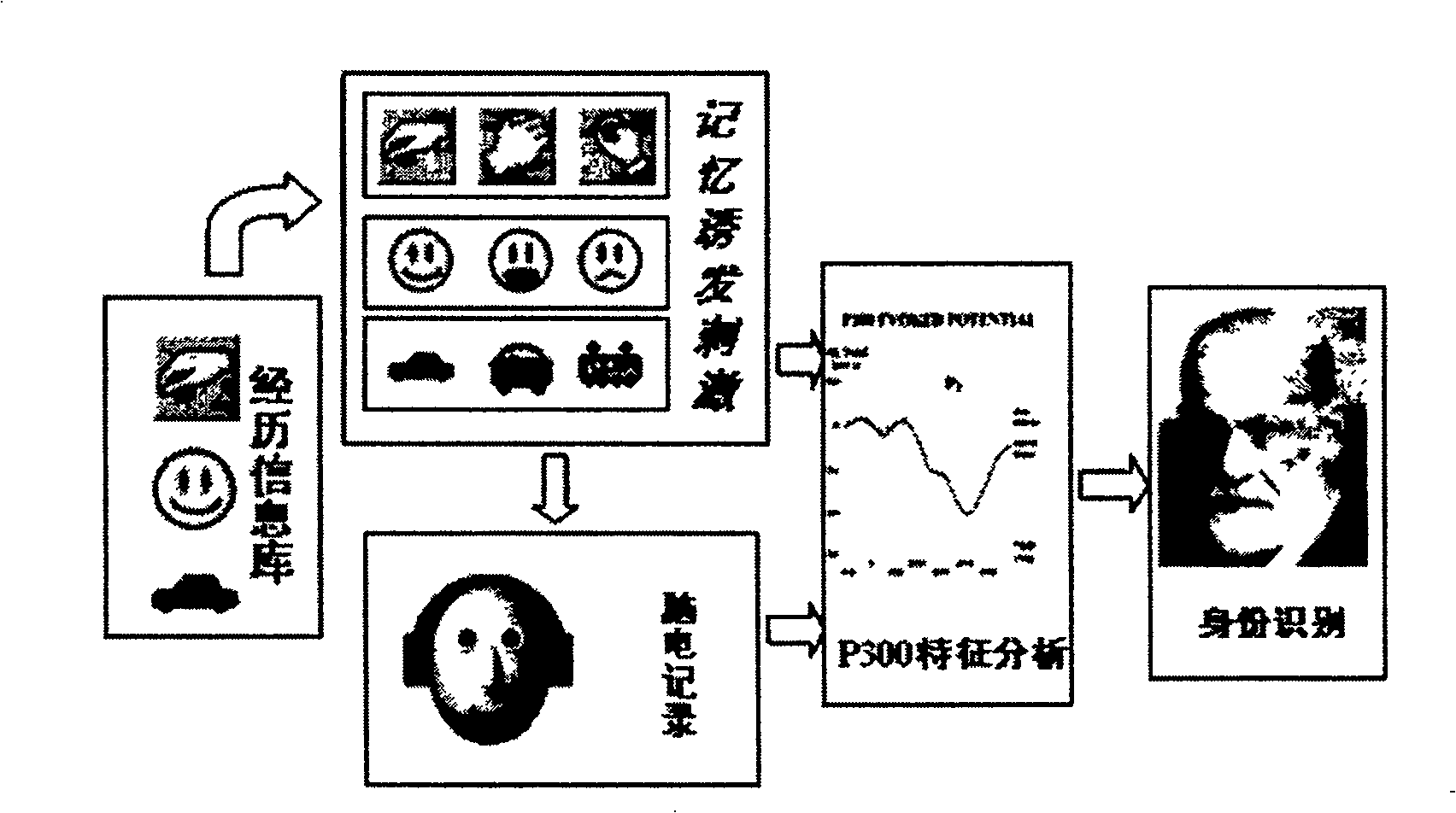
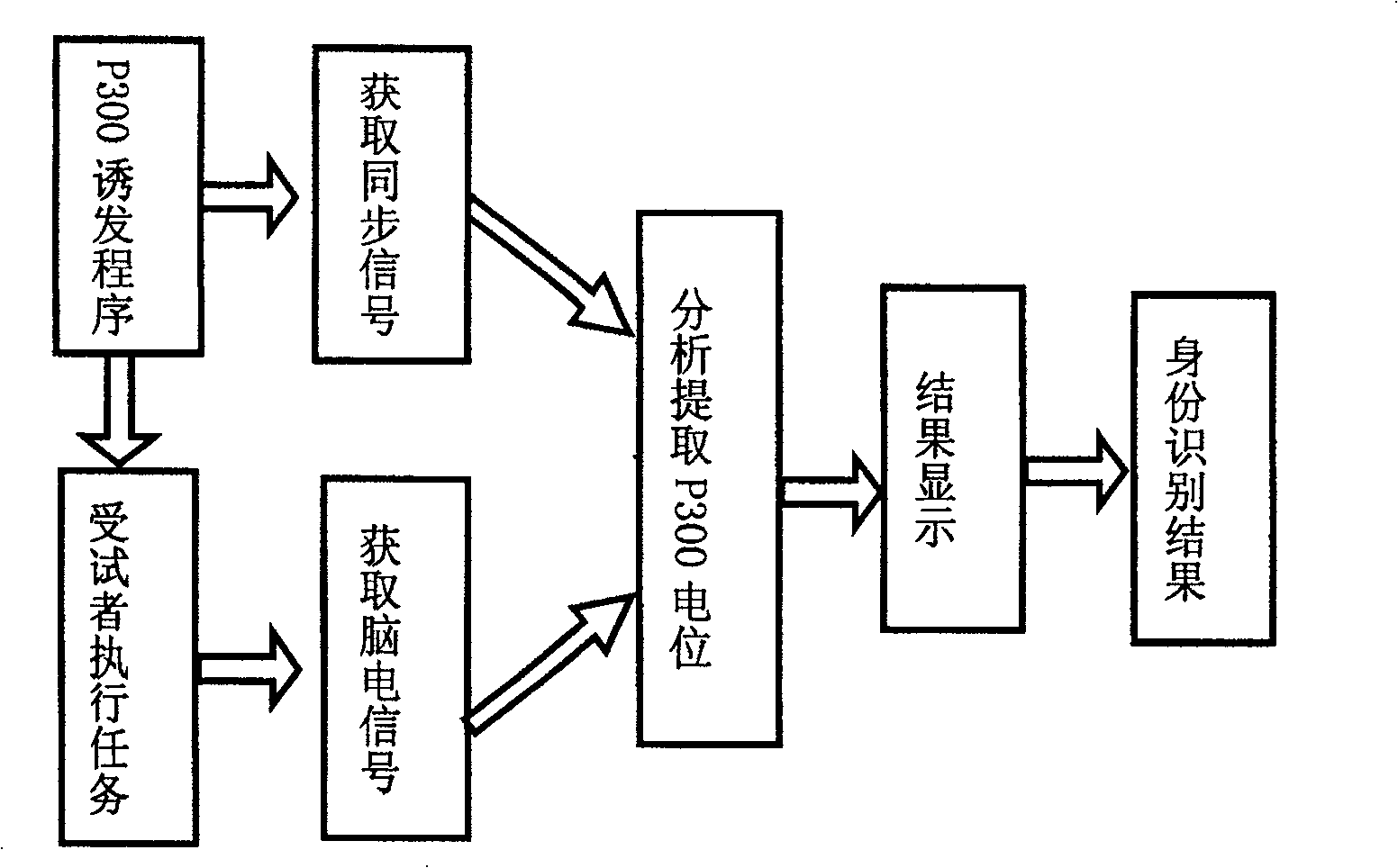
Objectively detected identity recognition method based on human brain memory character
An identity recognition and memory technology, applied in the field of personal identity recognition, can solve problems such as theft and forgery, and achieve the effect of high precision and good repeatability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
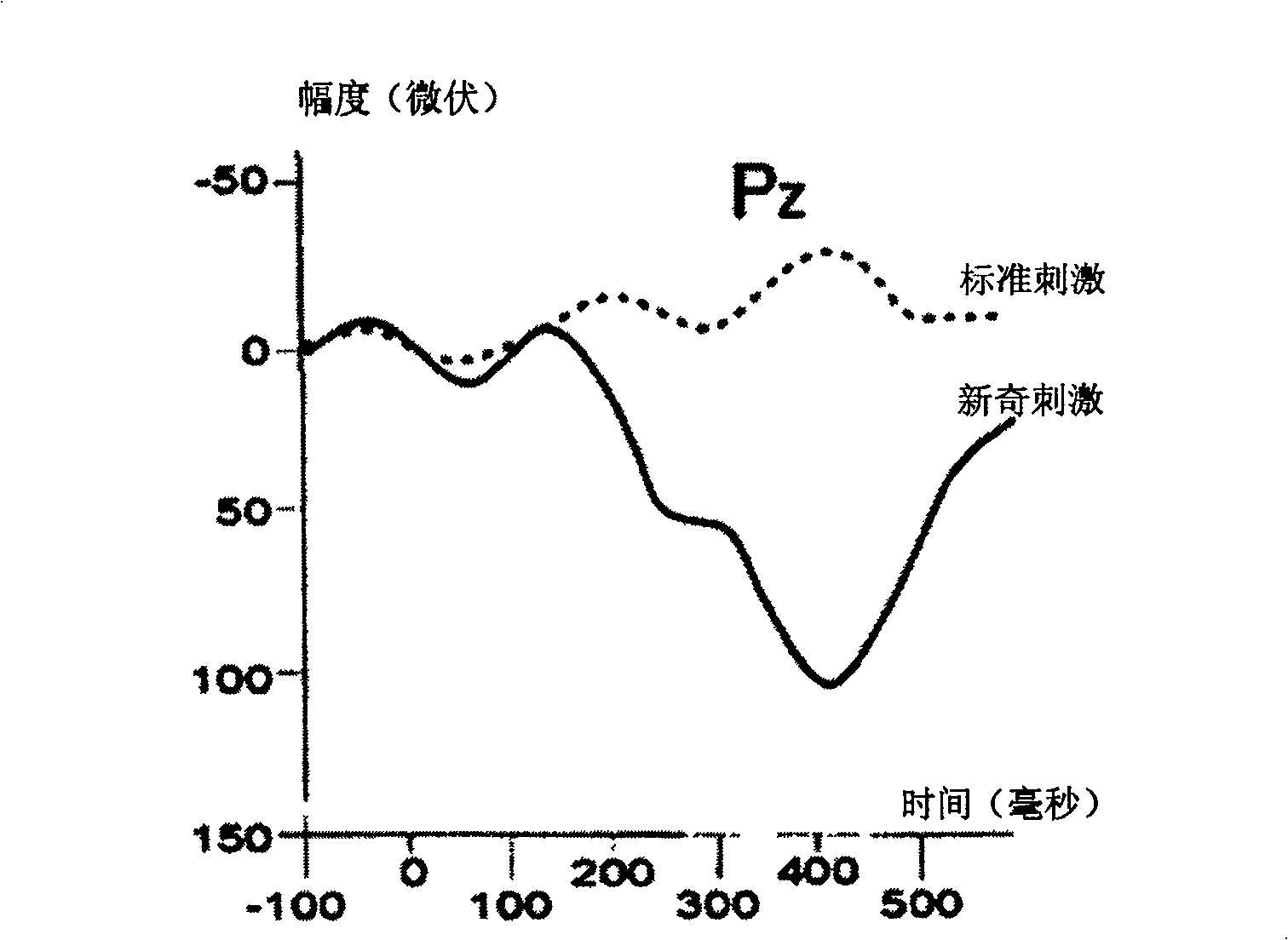
[0051] P300 was first discovered in 1965 by American psychologist Sutton et al. When the subject recognized the "target stimulus", the largest late positive wave recorded on the scalp with a latency of about 300 ms was the P300. P is the abbreviation of English "positive wave" (positivity), and 300 means that the latency is about 300ms.
[0052] figure 1 That is a typical P300 potential waveform. The classic stimulation mode to elicit P300 potential is the novel (Oddball) experimental mode. The main point of this experimental model is: a series of stimuli to the same sensory pathway consists of two stimuli, one stimulus has a high probability of appearing (such as 85%), which is called the standard stimulus; the other stimulus has a small probability of appearing ( Such as 15%), known as novel stimuli. The order in which the two stimuli appear is random. In this way, the deviated stimulus is accidental for the subject, so that the subject can press a button or remember its...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com