A method for SWF obfuscation encryption
An encryption method and file technology, which is applied in technical security-related fields, can solve problems such as core technology and business logic theft, and achieve the effect of protecting technical privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
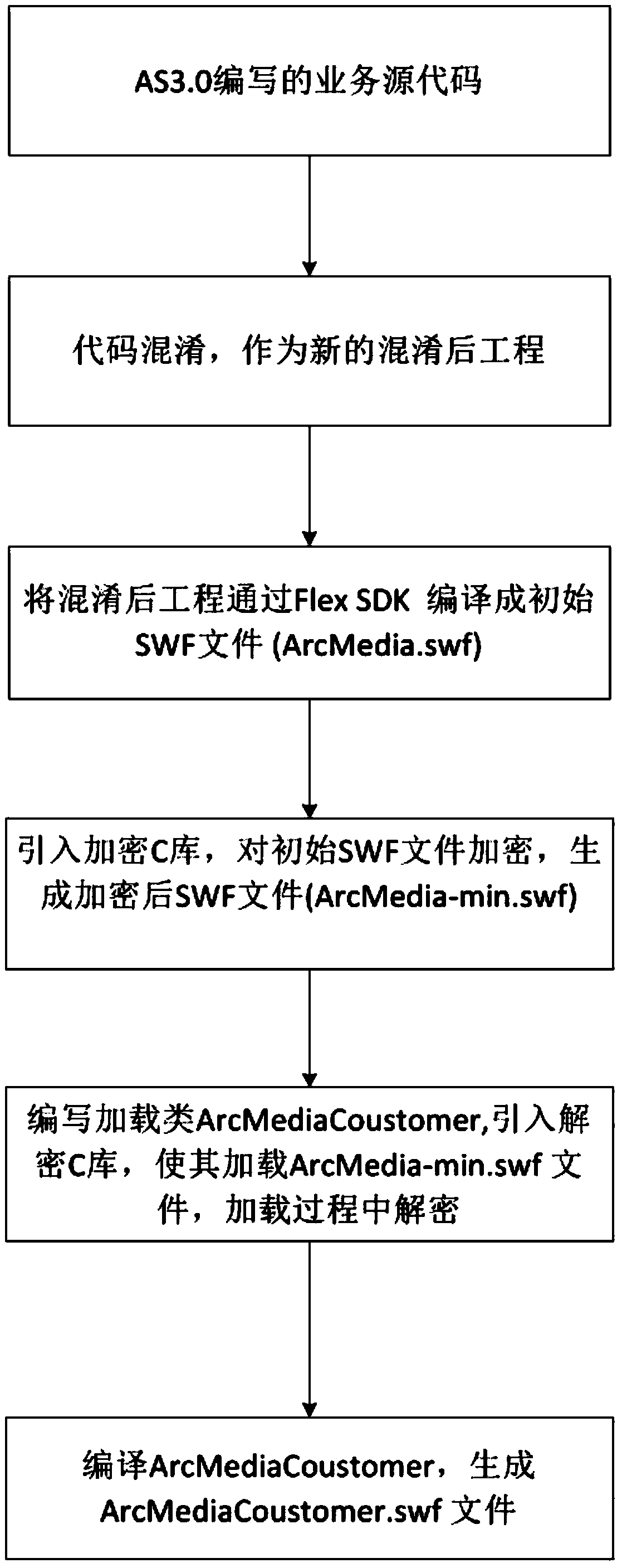
[0020] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0021] A method for confusing and encrypting SWF, specifically comprising the following steps:
[0022] (1) Determine the source code of the core AS3.0 project file to be protected; this project file is generally a business logic code written by technicians.
[0023] (2) Write a general obfuscation class to confuse the contents of the files in the source package; the obfuscation rules are as follows: first scan the package where the source code to be obfuscated is located, the package name, package path, variable name, method name, and callback function method in the source code Replace it with other meaningless symbols to make the code less readable and increase the difficulty of technology theft; keywords, native classes, and external dependent packages in the source code cannot be replaced. If the native class is replaced, compilation will f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com