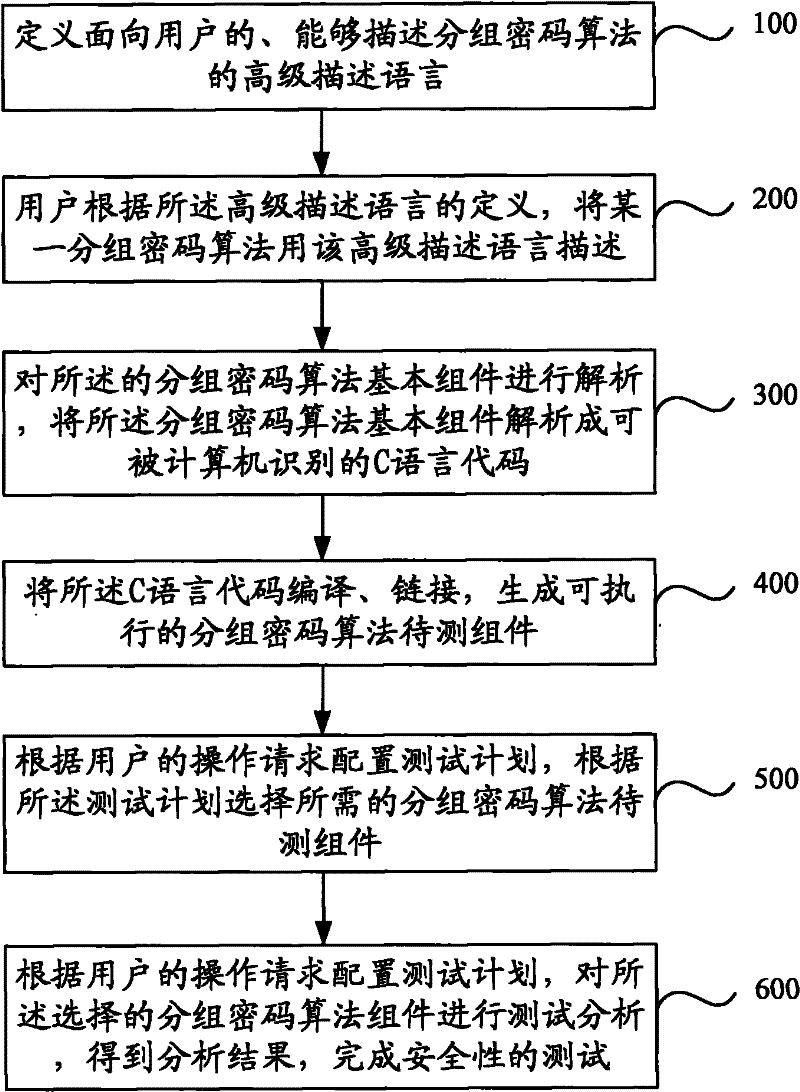
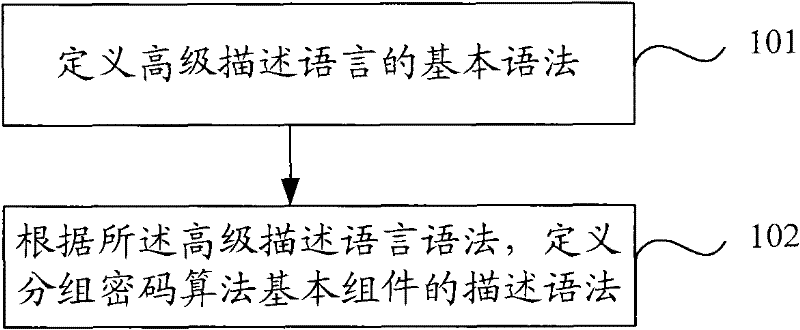
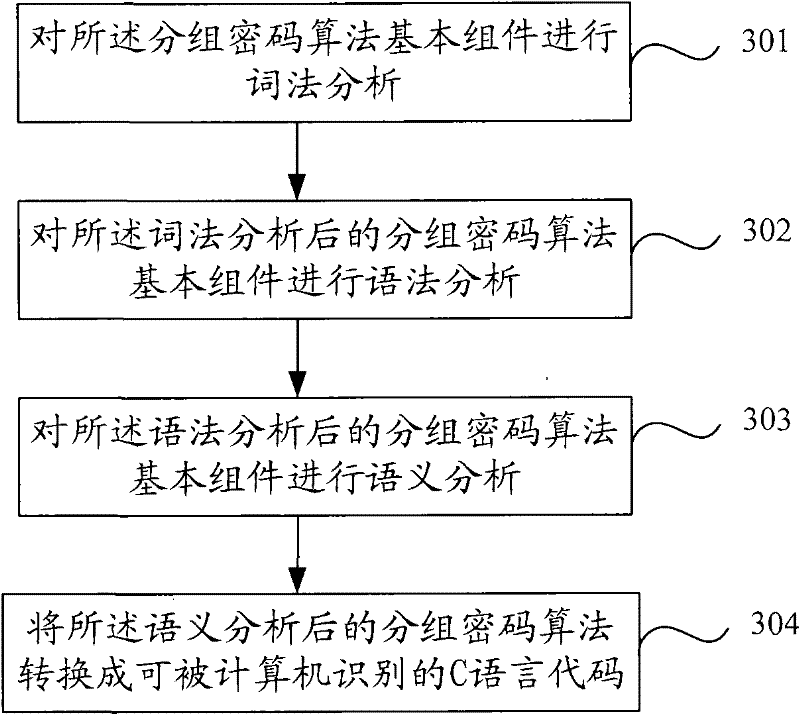
Patents
Literature
89 results about "C programming language" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Object-oriented knowledge base system
A useful object-oriented knowledge base system is provided, which comprises an 'object-oriented knowledge base', an inference mechanism, and an ideal dictionary, etc. Sentences used as a 'rule' and / or as a 'fact' in the 'object-oriented knowledge base' are described according to a simple English grammar. Hierarchical structure of nouns-system in an 'ideal thesaurus' is constructed, on the basis of special kind of 'object-oriented-lexical-definition of nouns' recorded in the ideal dictionary. Lexical meaning of a verb whose meaning is specific are derived from that of a verb whose meaning is general and universal, by using 'dichotomy' on the basis of C-language-like way of description of English sentences in the lexicon. The hierarchical structure of verbs-system in an 'ideal classification table' is constructed on the basis of them. The Inference mechanism processes not only mathematically well defined equations but, also simple English sentences, by making full use of the 'ideal thesaurus' and the 'ideal classification table', on the basis of specially contrived 'sentence based object-oriented categorical syllogism'.
Owner:OKUDE SHIN ICHIRO
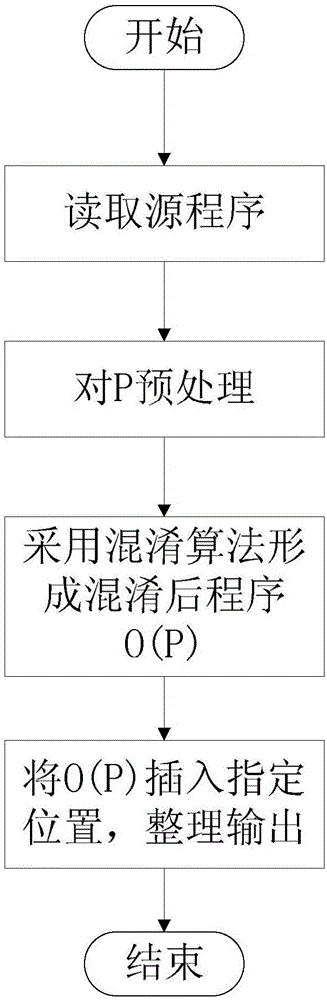
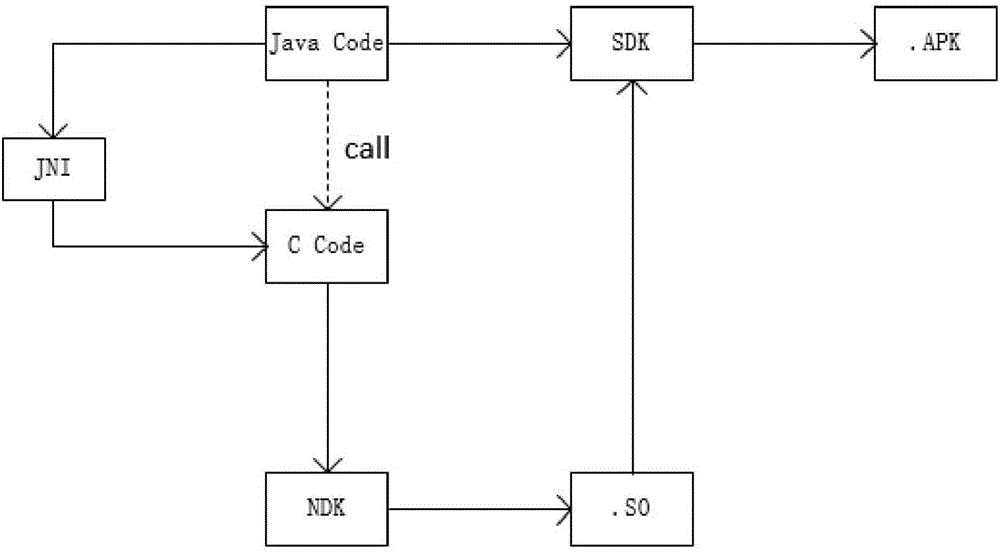
Android application reinforcing method baed on C source code mixing
InactiveCN106326694AImprove reusabilityImprove protectionProgram/content distribution protectionReusabilityC programming language
The invention discloses an Android application reinforcing method based on C source code mixing. The method comprises writing program key codes by using C programming languages and mixing C source codes. The reinforcement of Android application is achieved by mixing the C source codes in the Android application program, and the Android application program codes are protected. The Android application reinforcing method based on C source code mixing specifically includes the steps of writing the key part of the program by using C programming languages, writing programs into .so dynamic-link library file, invoking the dynamic-link library by using JNI technology in Java language, and then mixing the C source codes, so as to achieve the reinforcement of Android application. According to the Android application reinforcing method based on C source code mixing, important codes are saved in the C dynamic-link library by adopting NDK programming, and then the C source codes are mixed, the software protection is improved. At the same time, the important codes are written in a so library, the reusability of the codes are increased, ready-made so library can be directly introduced into other applications, so as to eliminate the troubles of secondary development.
Owner:北京鼎源科技有限公司
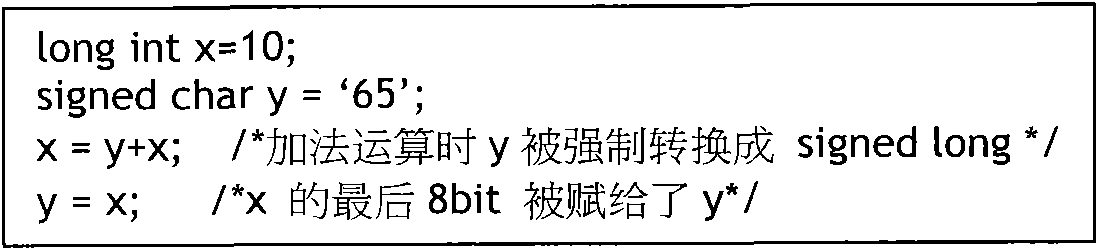
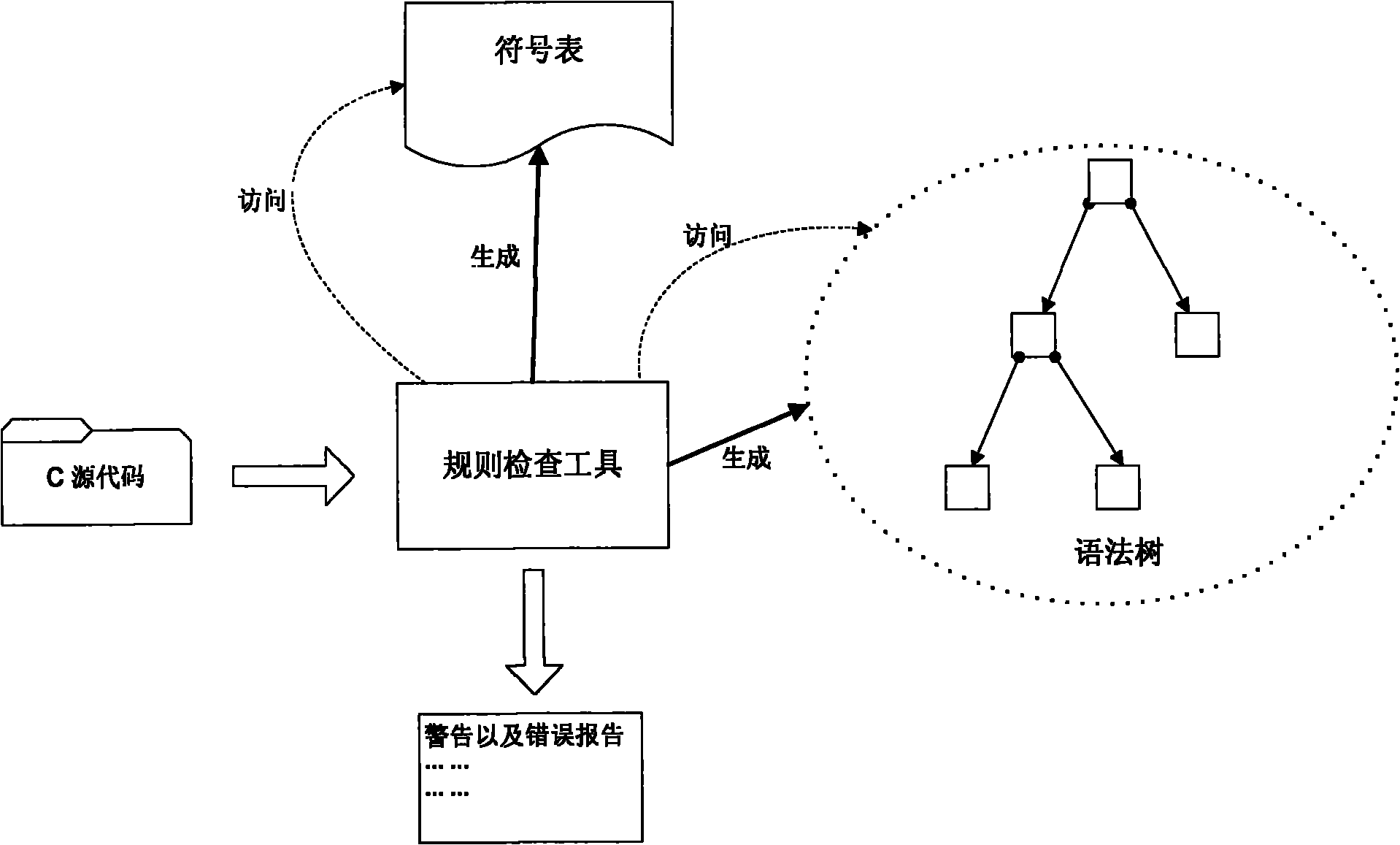
Static analysis-based checking method of safety rules of C language
InactiveCN102012991AMake up for the lack of securityPlatform integrity maintainanceStatic timing analysisType conversion
The invention relates to a static analysis-based checking method of safety rules of C language, which comprises the following steps: 1) checking the type of the C language to avoid the occurrence of compulsory type conversion and prohibiting the declaration of the type of a generic pointer; 2) stipulating that a global variable and a local variable can not be in homonymy, and the global variable and a formal parameter of a function can not be in tautonomy; 3) limiting a cyclic variable of a control flow statement; 4) strengthening the declaration and the definition of the C language; and 5) carrying out analysis of accidence, grammar and semanteme on source codes, and finding out places which do not meet the stipulation from the source codes. The method has the advantages of being capable of finding out possible loopholes on programming of the C language under the premise that the codes do not need to be executed and effectively making up for the deficiency of insufficient safety of the C language in soft engineering.
Owner:北京神舟航天软件技术股份有限公司
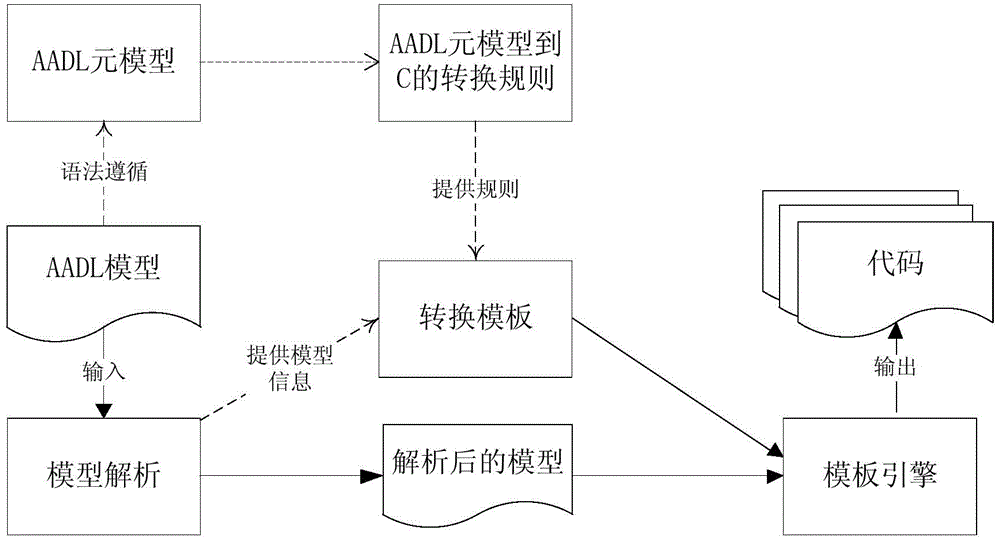
Automatic code generation method from AADL to C language
InactiveCN104932905ARealize automatic generationSolve Semantic MappingSpecific program execution arrangementsC programming languageCode transformation
The invention relates to an automatic code generation method from AADL to C language. The method comprises the following steps that 1, a transformational rule from an AADL meta model to the C language is defined according to the semantic meaning of the AADL meta model, the semantic meaning of an object run environment and the grammar semantic meaning of the C language; 2, an automatic code generation template is made according to the adopted meta model capable of being obtained by an AADL model, the semantic meaning of the meta model and the transformational rule from the AADL meta model to the C language; 3, a template transformation engine is compiled according to the automatic code generation template; 4, after the AADL model is input, the input AADL model is automatically analyzed, and information of the AADL meta model is extracted, and is generated into C language codes through the template transformation template according to the automatic code generation template. The method has the following advantages that the transformational rule from the AADL meta model to the C language is defined, and semantic mapping of the AADL and the C language is effectively achieved; the code transformation efficiency is improved through the template engine.
Owner:北京神舟航天软件技术股份有限公司
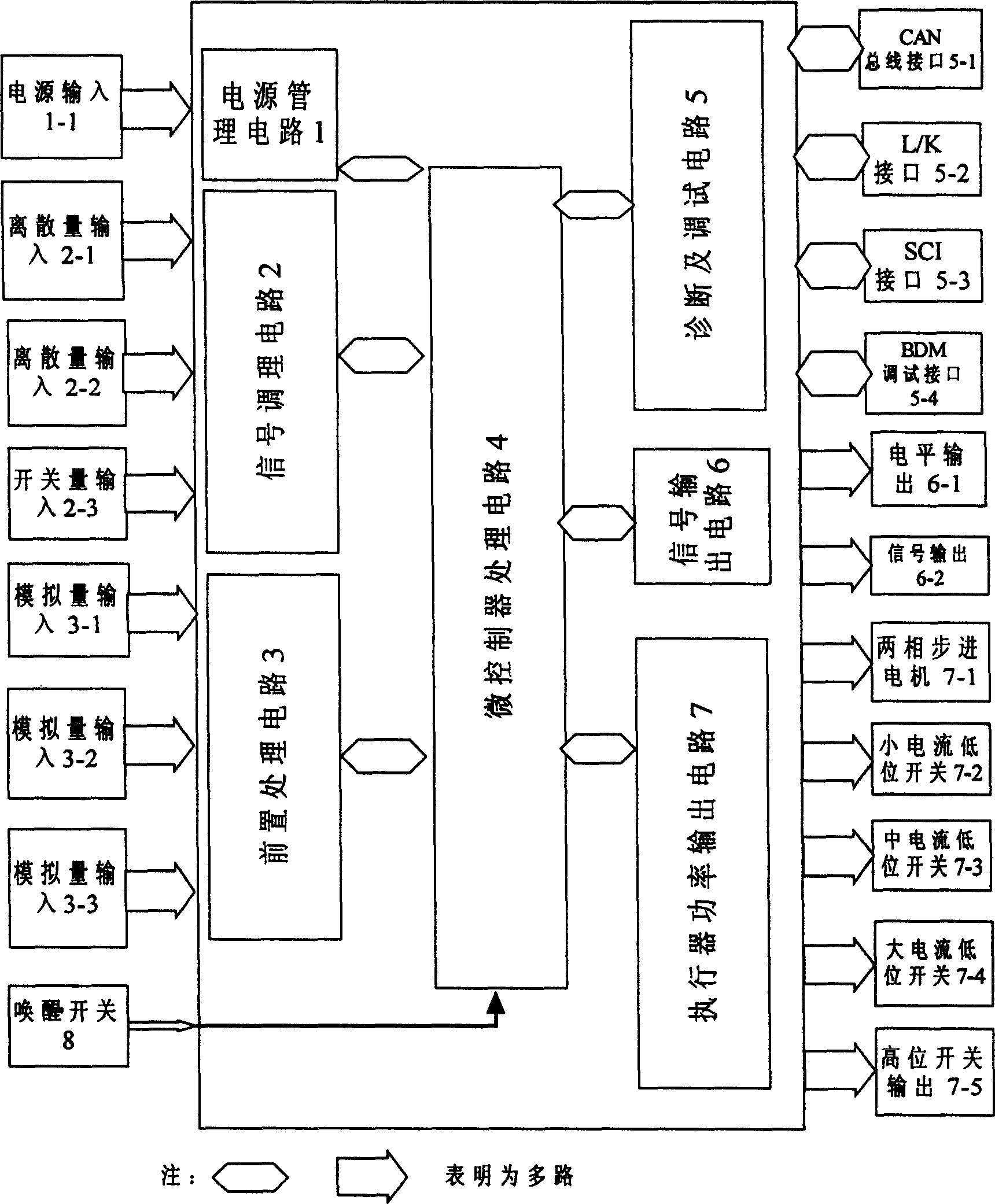
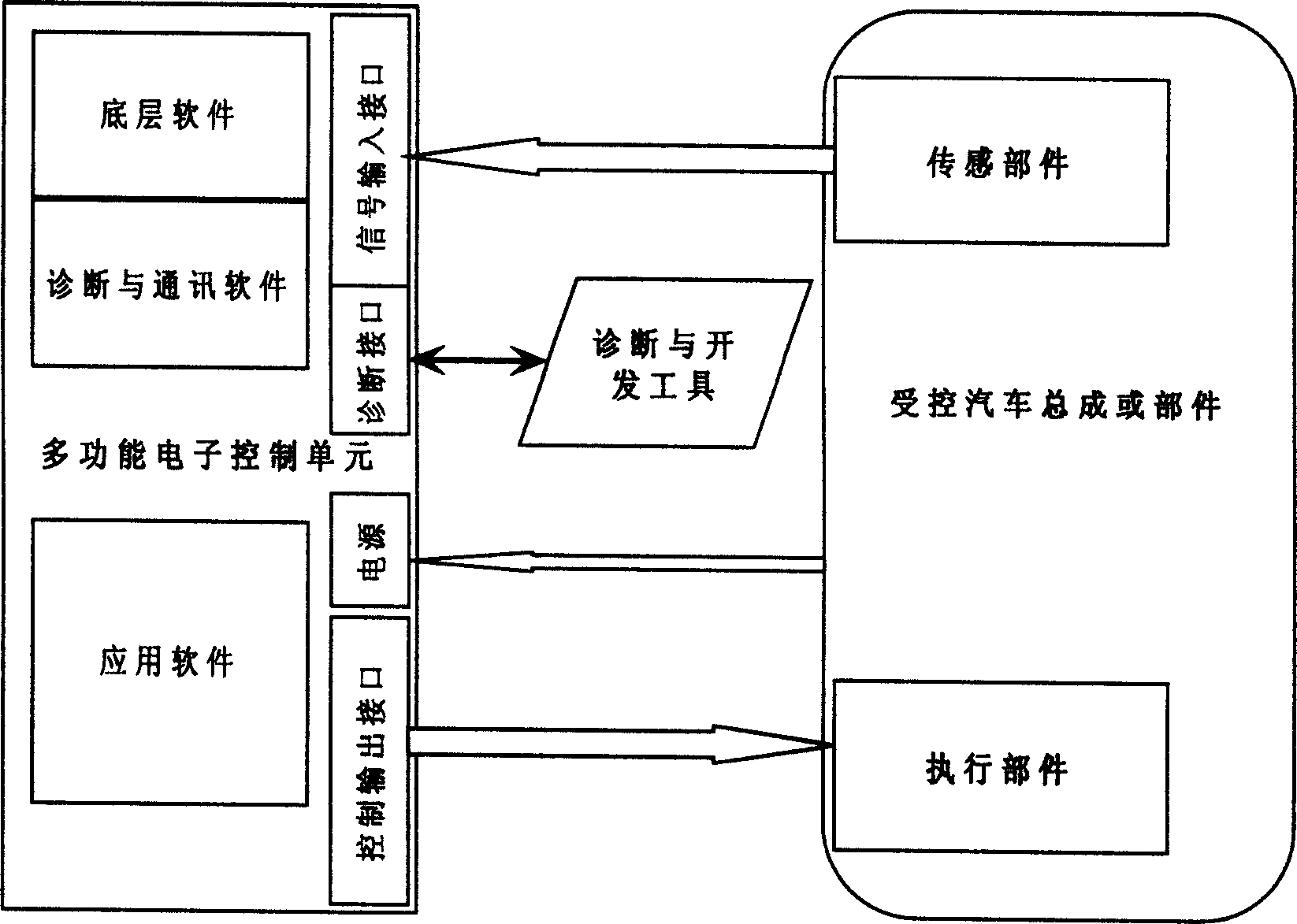
Developing platform and control method for multifunction automobile electronic control unit
InactiveCN1687849AQuick controlEasy to controlComputer controlC programming languageApplication software
The invention relates to the electronic field of autocar, and the whole circuit adopts regional design, altogether divided into power supply region, microprocessor region, input region, output region, communication debugging region and failure diagnosis region, and other functional regions. By loading the application software of the controlled object of the autocar, and inputting the needed input signals, it can control the target actuator based on the given control policy and makes on-line failure diagnosis on all the sensors and actuators, able to implement the development and design of autocar engine management system, auto gear box control system, ABS control system, autocar body control system, instrument and information system, and other electronic control systems. And the user only need possess the basis of C language so as to be able to make functional operation on all the interfaces and it can provide a friendly development environment of electronic control system for autocar and engine engineers of nonelectornic and computer specialties.
Owner:镇江江奎科技有限公司
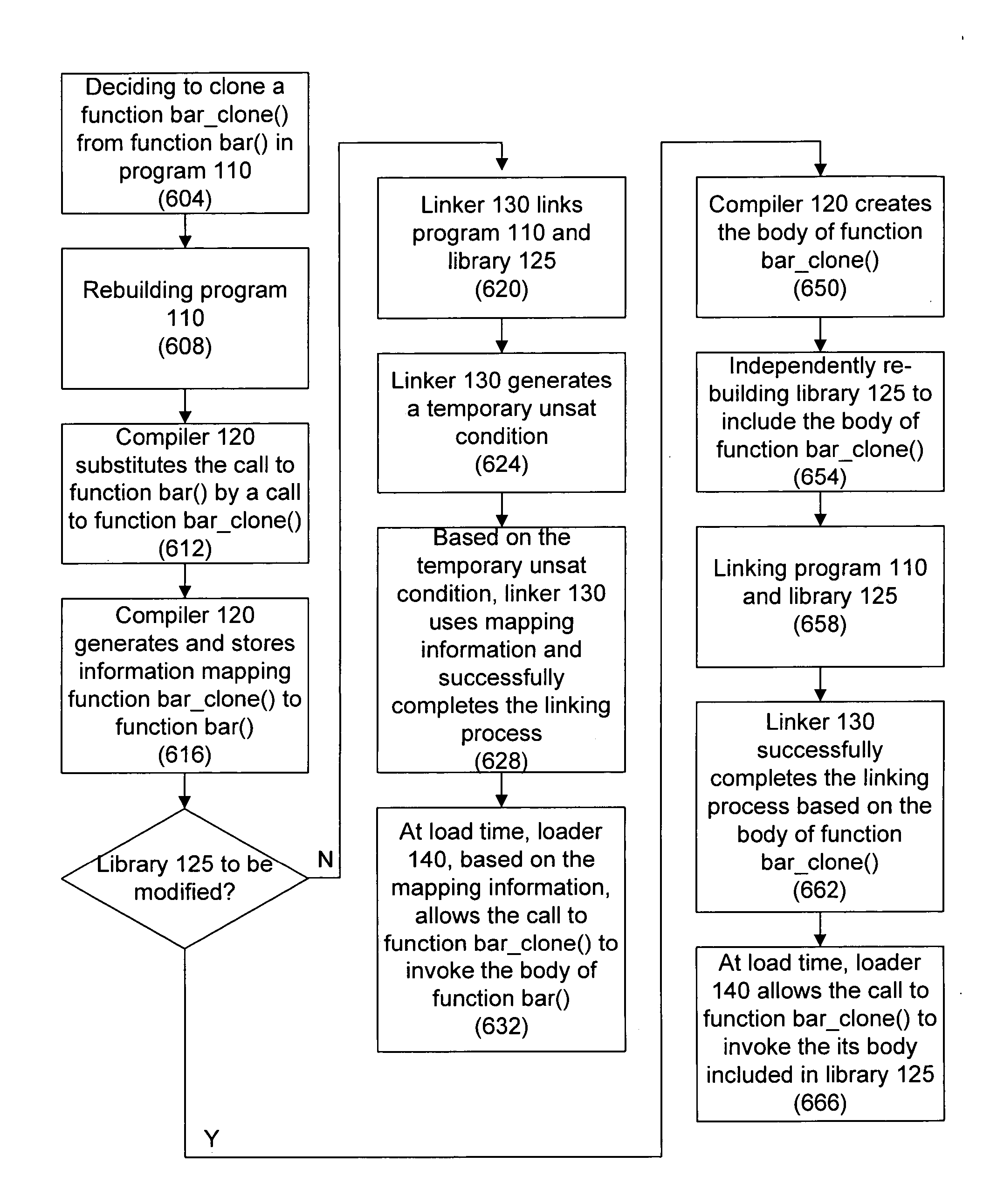
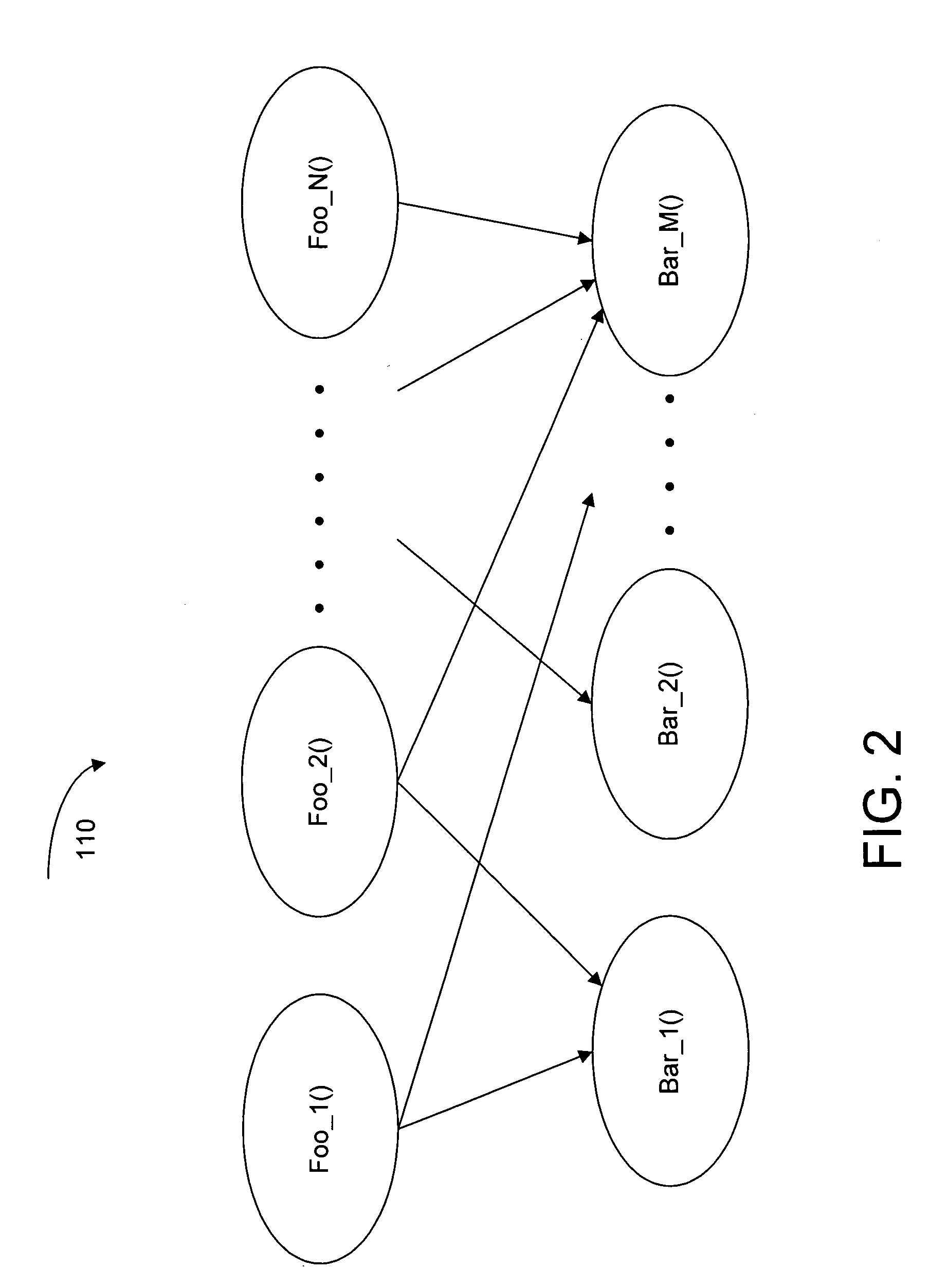
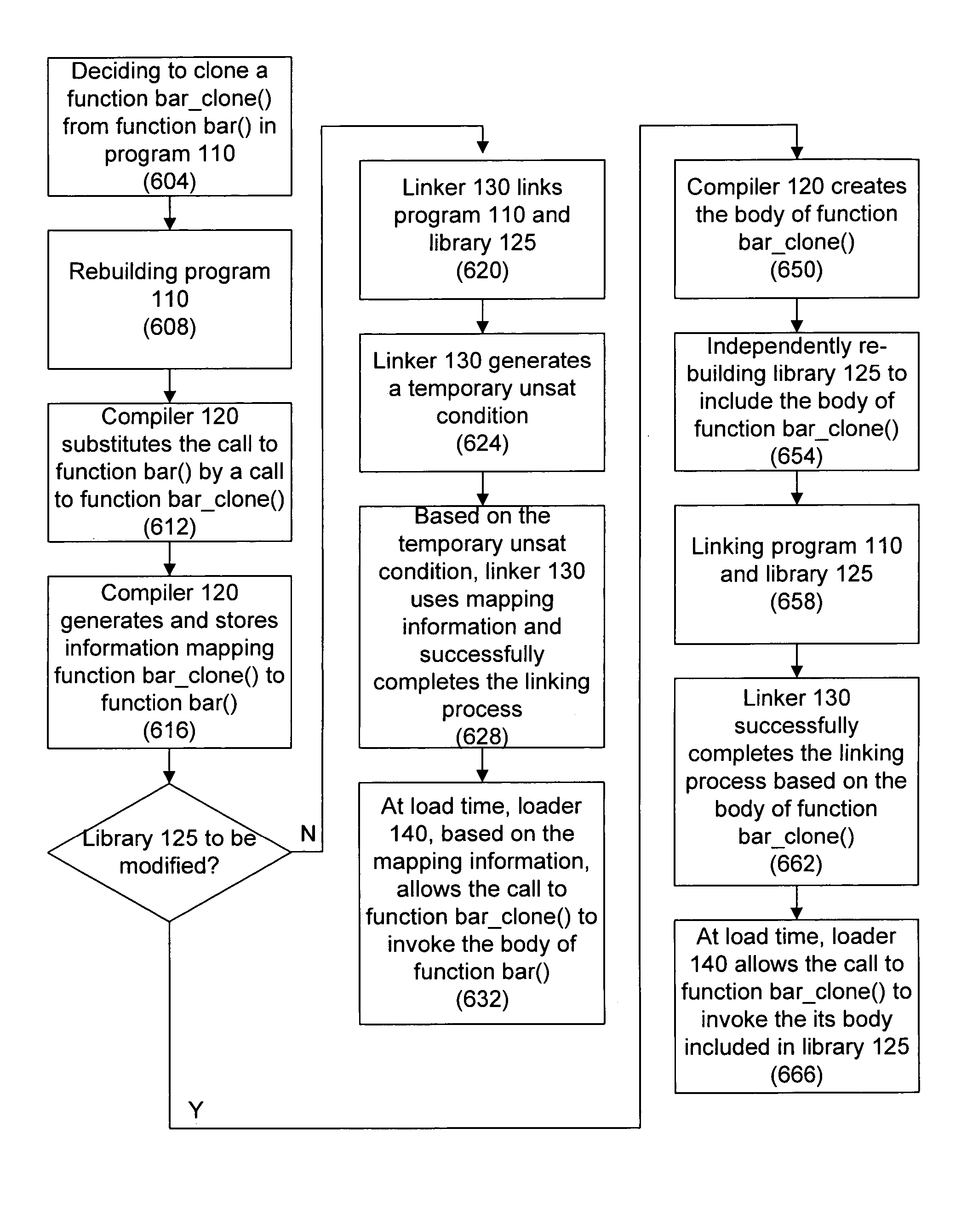
Cloning programming code
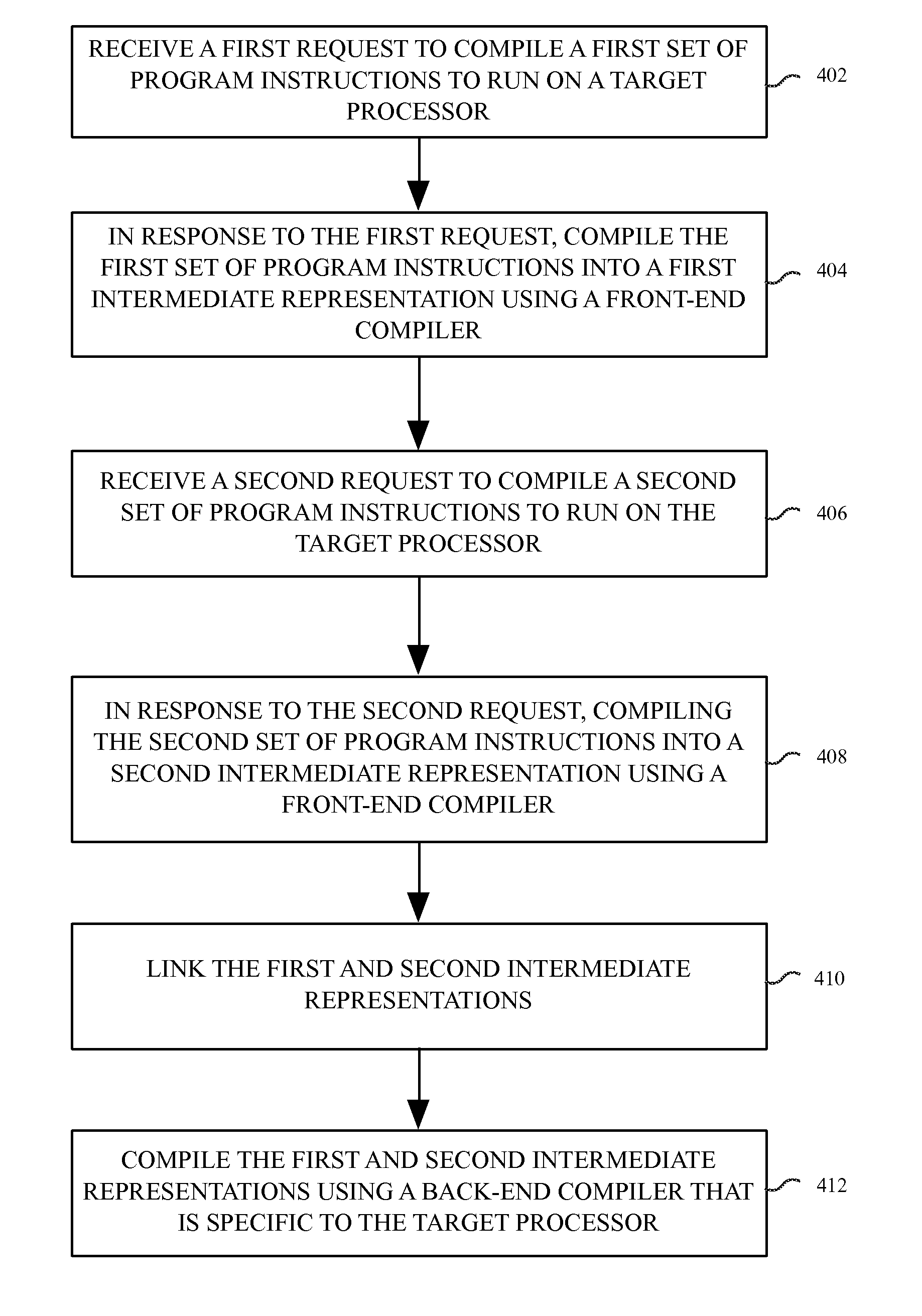
Techniques for cloning programming code are disclosed. In an embodiment, the cloned code is in the form of functions in the C language. Further, in a method embodiment, a clone of a function is invoked, and information mapping the clone to the function is generated. At link time, if no function body of the clone is accessible by a linker, then the linker uses information mapping the clone to the function to satisfy a linker's requirement. At load time, if no function body of the clone is accessible by a loader, then the loader, based on the mapping information, allows selection of a body of the function. However, if the body function of the clone is accessible by the loader, then the loader allows selection of the body of the clone.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
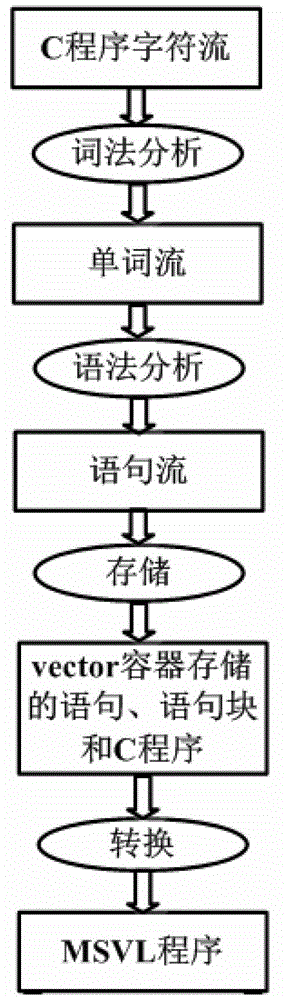
Computer language transformation system and transformation method from C language to MSVL (Modeling, Simulation and Verification Language)
ActiveCN103150200AImplement model checkingGuarantee safe and reliableProgram controlMemory systemsLexical analysisLexical rule
The invention relates to a computer language transformation system. The computer language transformation system is used for transforming C language program into MSVL (Modeling, Simulation and Verification Language) program, and comprises a lexical analysis module, a syntax analysis module and a transformation processing module, wherein the lexical analysis module is used for transforming character sequences into word sequences; the character sequences comprise definitions of key words, identification characters, constants, operators, header files and comment lines in C language; the syntax analysis module is used for identifying specific sentences in C language based on related lexical rules of C language specified in yacc (Yet Another Compiler Compiler); and the transformation processing module is used for transforming C language into MSVL language according to a language transformation rule between C language and MSVL language.
Owner:XIDIAN UNIV
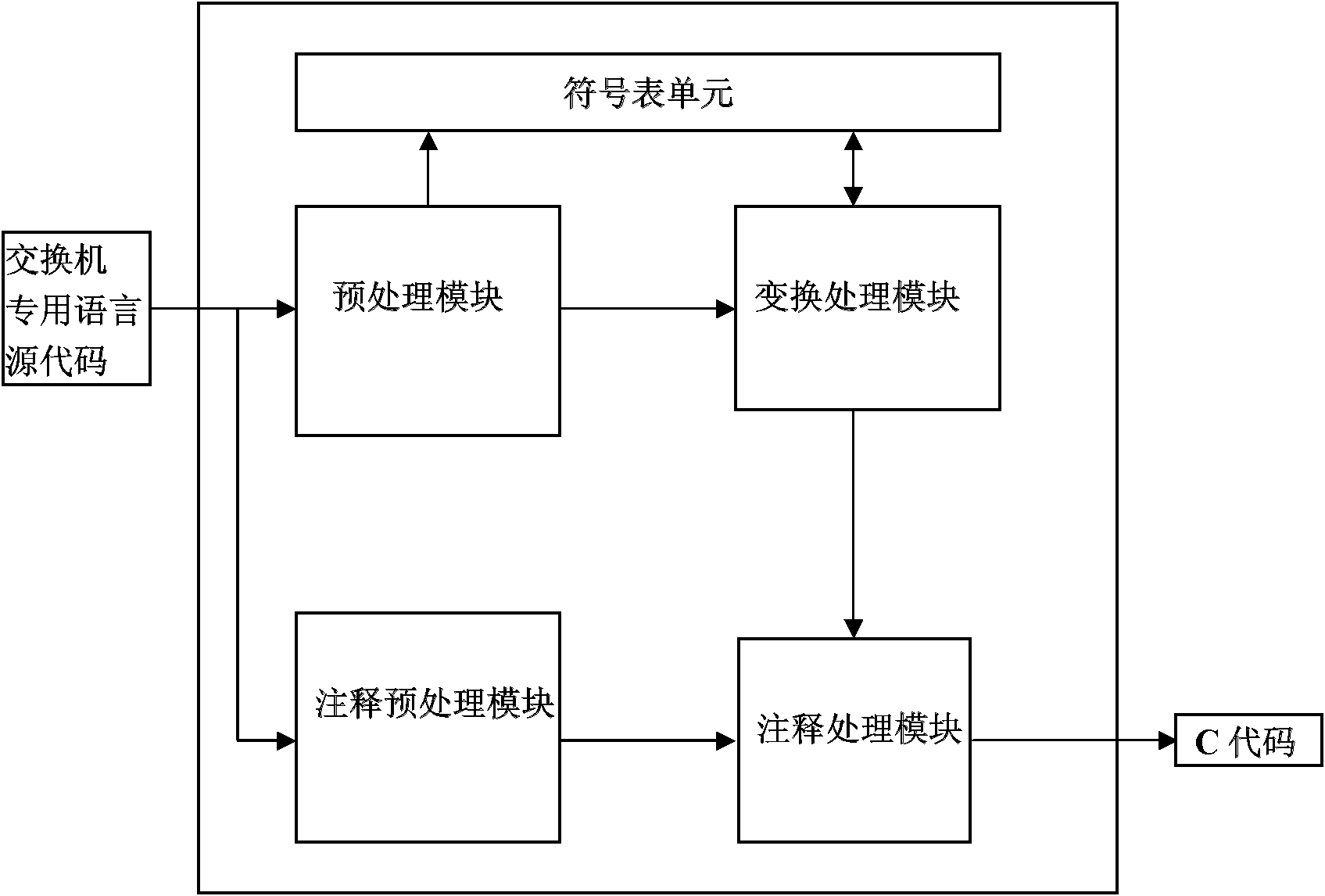
Method for transforming switch special language into C language
ActiveCN102222004AHigh transplantabilityImprove readabilitySpecific program execution arrangementsNatural language processingC programming language
The invention provides a method for transforming a switch special language into C language. In the method, a preprocessing module, a symbol list unit, a transformation processing module, an annotation preprocessing module and an annotation processing module are provided, wherein the preprocessing module comprises an LEX lexical analyzer and a Yet Another Compiler-Compiler (YACC) analysis program generator; the annotation preprocessing module comprises an LEX lexical analyzer and a YACC analysis program generator; the annotation preprocessing module comprises an LEX lexical analyzer, wherein source codes of the switch special language are imported into the preprocessing module and the annotation preprocessing module to be processed and then sentences and annotation contents which produce a global symbol table and a syntax tree format are obtained; and then final C language codes with the annotations are generated through the transformation processing module and the annotation preprocessing module. The method realizes the transformation of the switch special language into the C language, and the C language is provided with the annotations and is highly readable.
Owner:中电福富信息科技有限公司
Method and system for analyzing block cipher algorithm
InactiveCN102195773AEasy to understandEasy to useEncryption apparatus with shift registers/memoriesComputer hardwareC programming language
The invention discloses a method and system for analyzing a block cipher algorithm. The method comprises the following steps of: firstly, defining a high-level descriptive language; secondly, making a user describe the block cipher algorithm as the combination of a plurality of block cipher algorithm basic components according to the high-level descriptive language; thirdly, resolving the block cipher algorithm basic components into C language codes which can be identified by a computer, and compiling and linking the C language codes to generate executable block cipher algorithm components to be tested; and lastly, configuring a testing plan according to an operation request of the user, selecting a needed block cipher algorithm component to be tested, and testing and analyzing the selected block cipher algorithm component to be tested according to the testing plan to obtain an analysis result. Due to the adoption of the method and system for analyzing the block cipher algorithm, the security analysis of a block cipher is converted into the security analysis of the executable block cipher algorithm components to be tested, which can be identified by the computer, so that uniform analysis of the security of most conventional block cipher algorithms can be realized.
Owner:THE PLA INFORMATION ENG UNIV
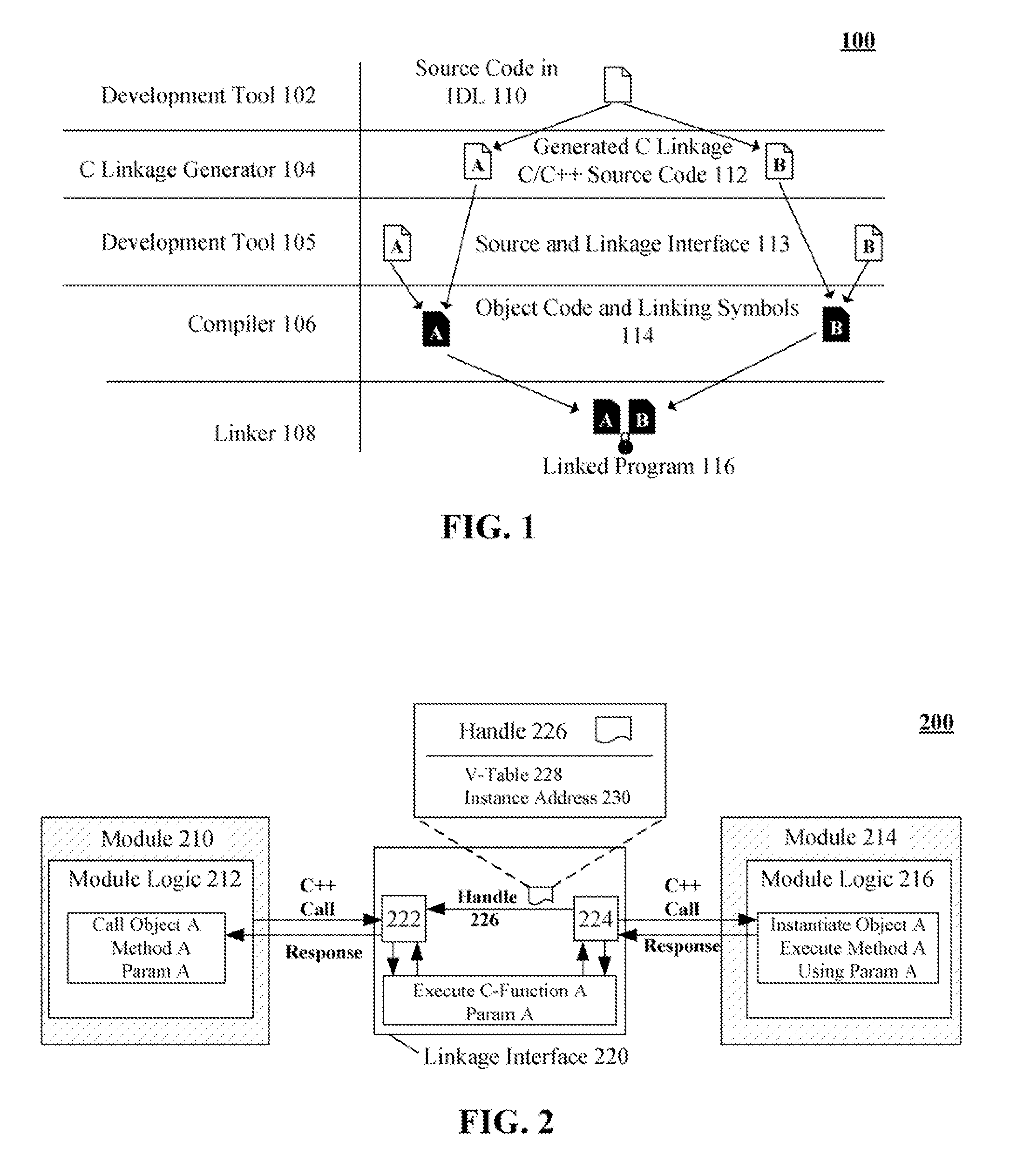
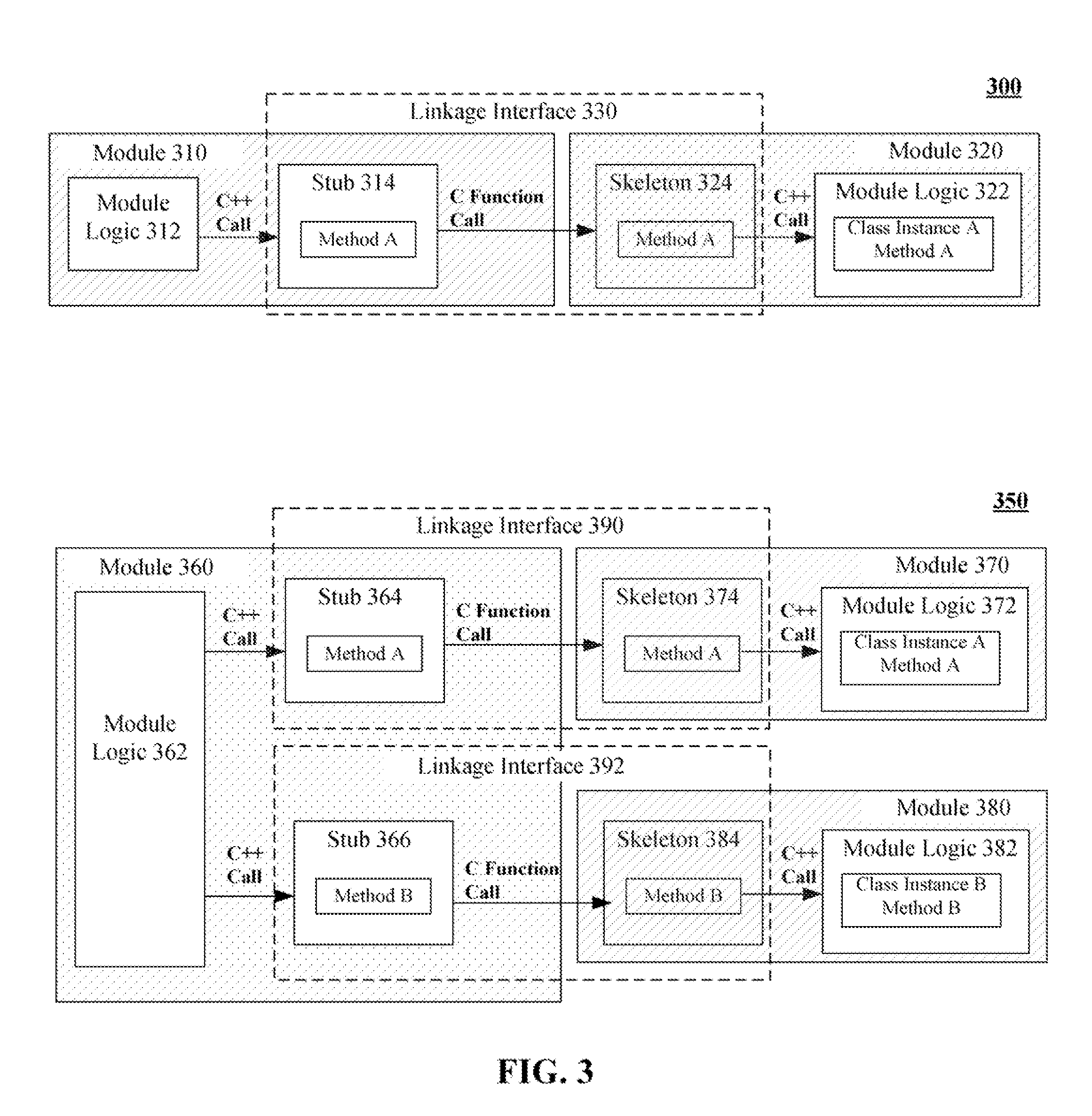
Compiler neutral linking solution for c++ code
InactiveUS20080098377A1Specific program execution arrangementsMemory systemsC programming languageSoftware modules
The present invention provides a solution where interactions between different C++ modules can be reduced to interactions written in the C programming language. This permits code linking the difference C++ software modules to be written in the C programming language. Because naming conventions for linking symbols are standardized for the C programming language across all compilers, the C++ software modules can be linked to each other in a compiler neutral fashion. This is true even when the linked software modules are complied using different C++ compilers having non-standardized naming conventions for linking symbols. In absence of the disclosed solution, the different C++ compilers would generate code that cannot be linked.
Owner:IBM CORP
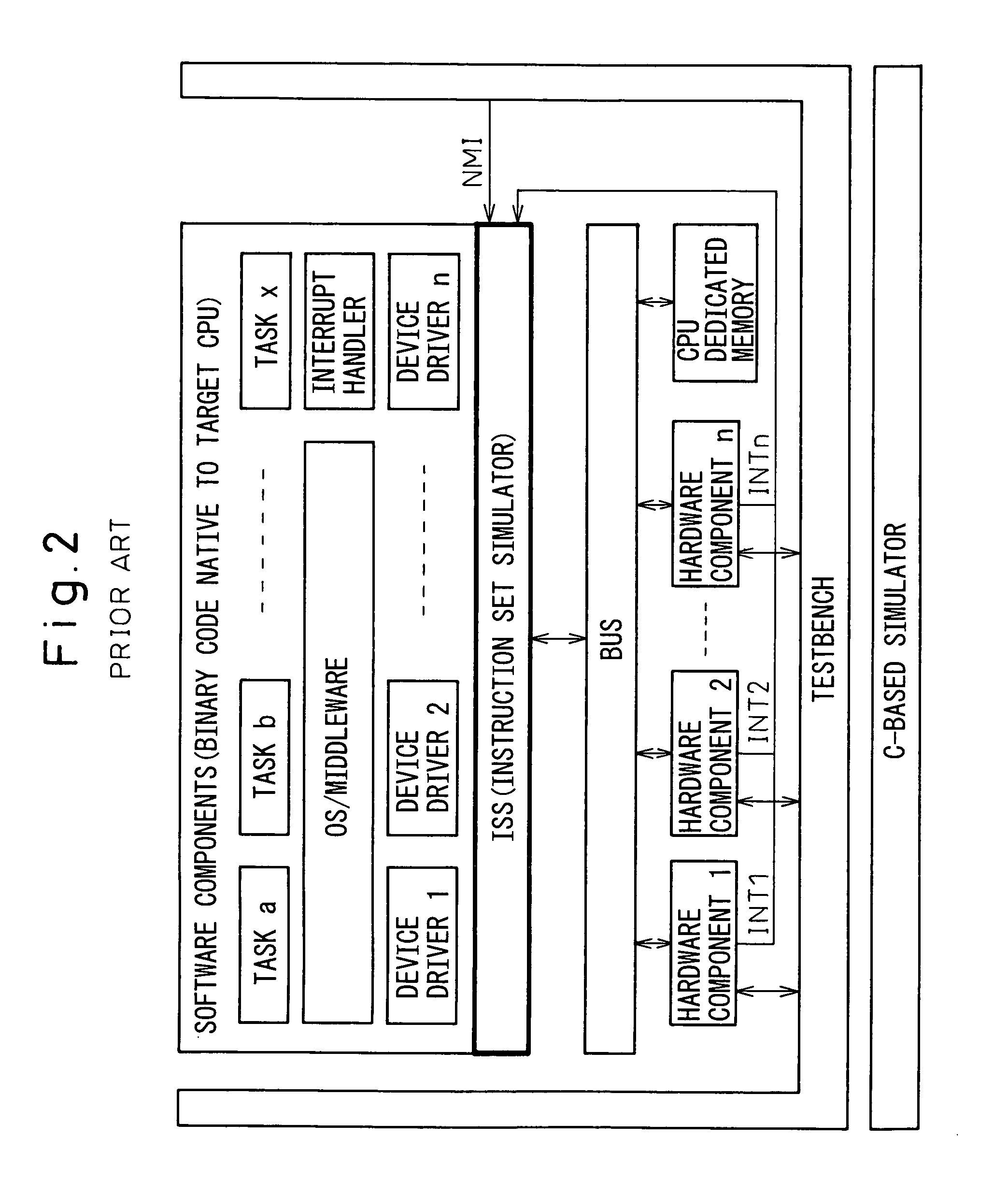
Method for co-verifying hardware and software for a semiconductor device
InactiveUS7155690B2Improve accuracyFast executionError detection/correctionElectrical testingComputer hardwareValidation methods
A hardware / software co-verification method that achieves fast simulation execution by implementing a C-based native code simulation without degrading the accuracy of timing verification. This method is a method for co-verifying hardware and software, by using a host CPU, for a semiconductor device on which at least one target CPU and one OS are mounted wherein, first, a timed software component described in a C-based language or constructed from binary code native to the host CPU and a hardware component described in the C-based language are input as verification models, necessary compiling is performed, and the compiled components are linked together. Next, a testbench is input and compiled. Then, the components and the testbench are linked together, after which simulation is performed and the result of the simulation is output.
Owner:SEIKO EPSON CORP
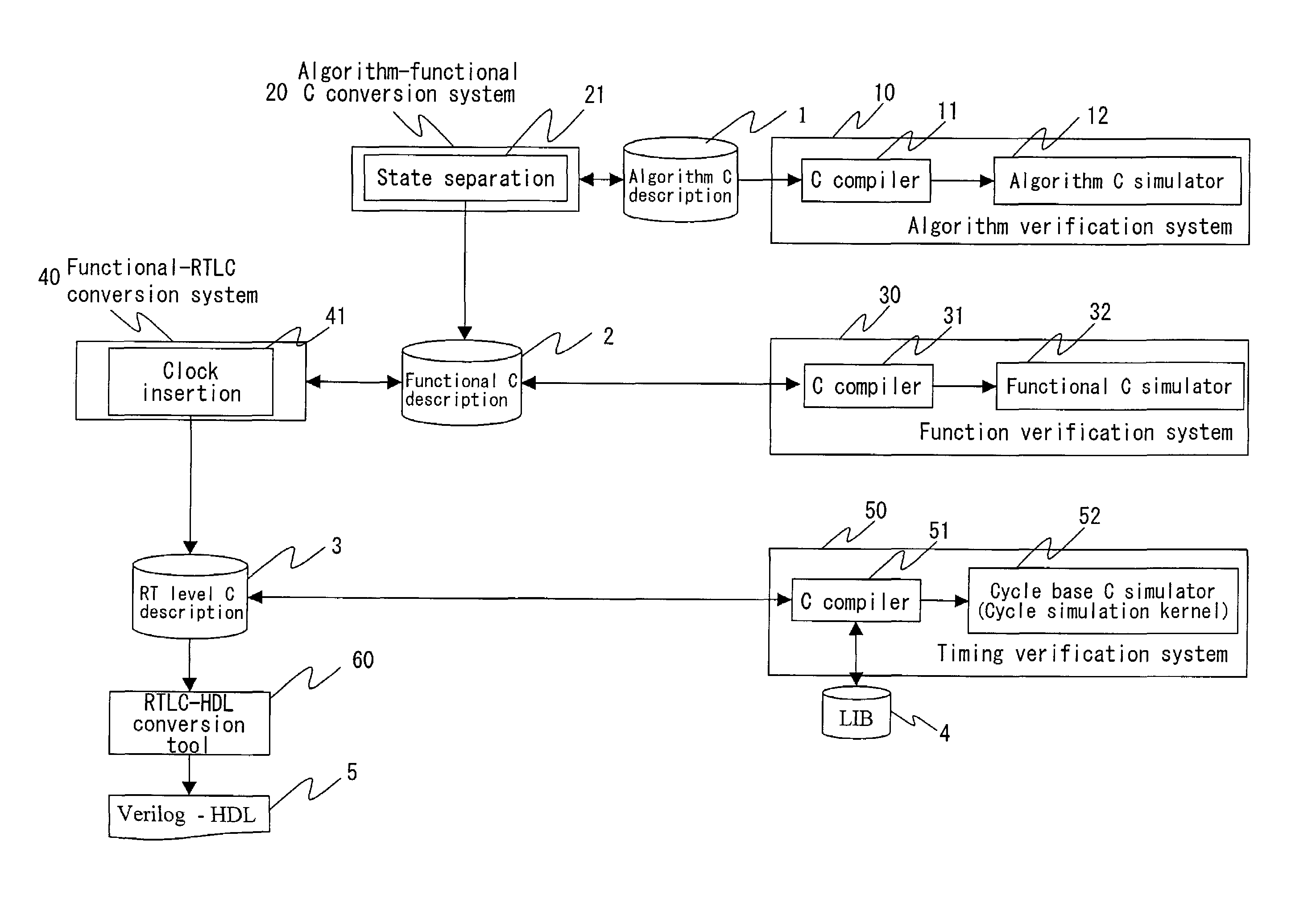
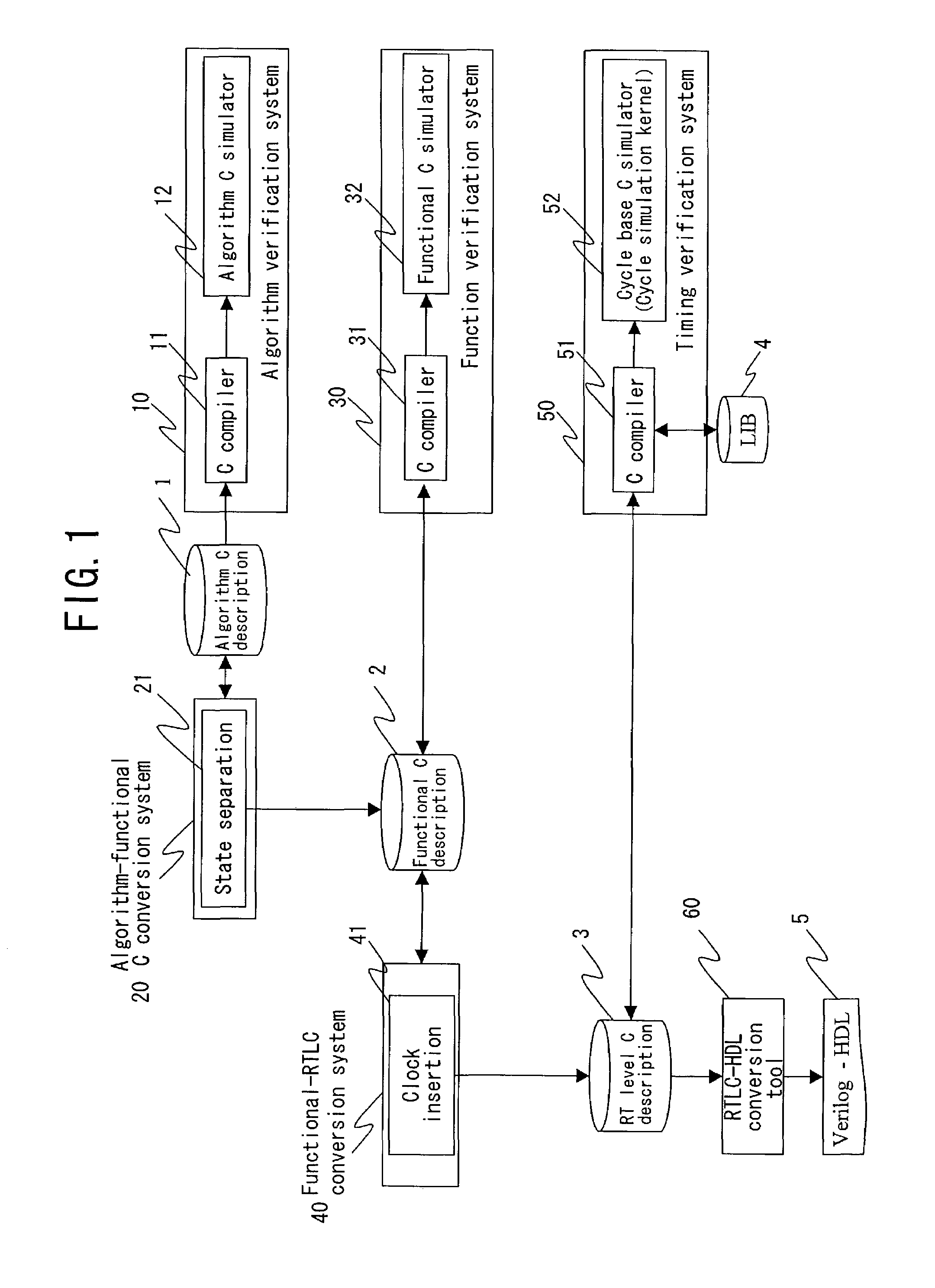
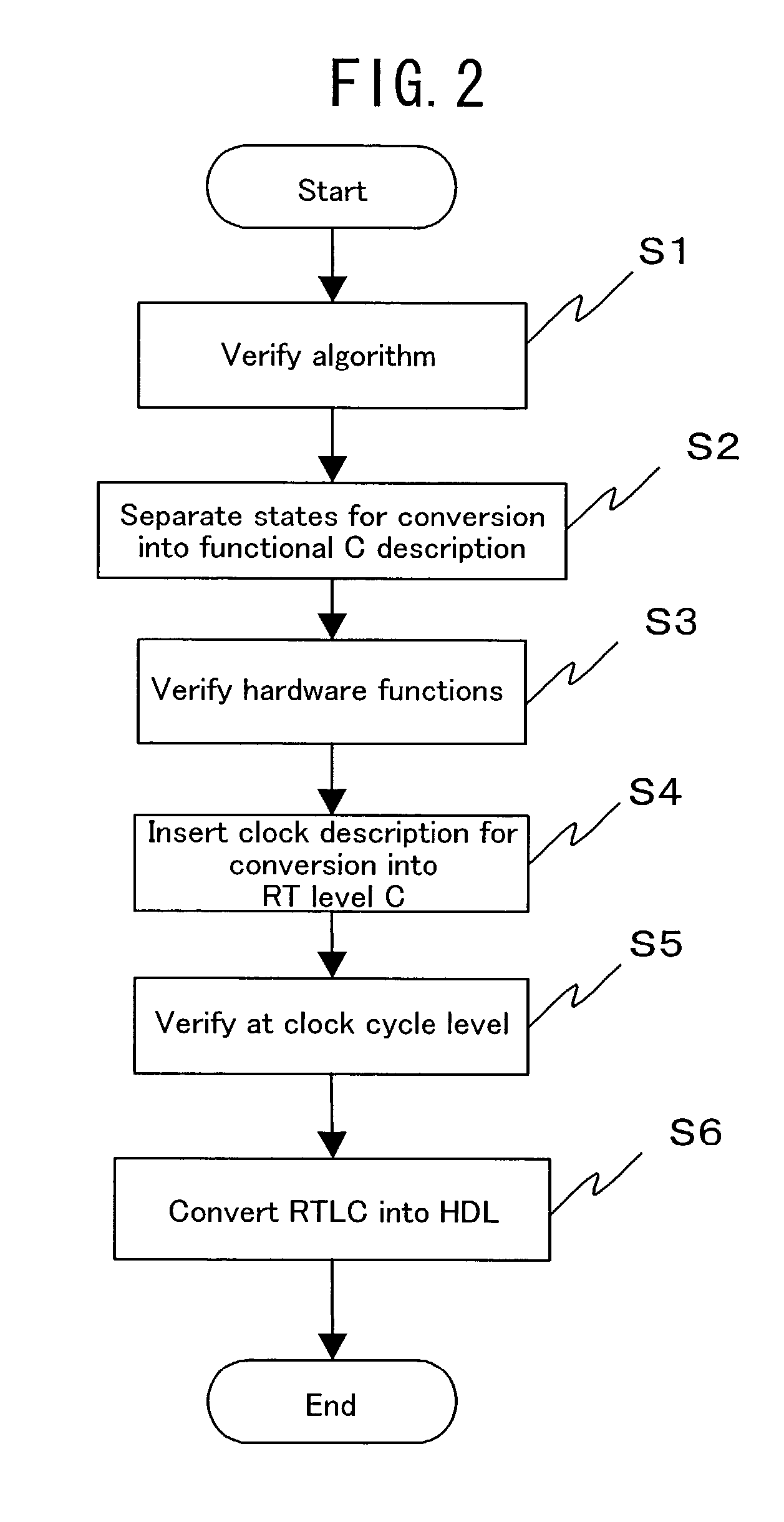
Method of designing a logic circuit utilizing an algorithm based in C language
InactiveUS7062728B2Quality improvementShort timeSemiconductor/solid-state device manufacturingCAD circuit designTheoretical computer scienceC programming language
An algorithm C description describing an algorithm of computation or control of a logic circuit in a C language is split into a plurality of states in units of processing, and the execution order of the split processing is described as state transition, to generate a functional C description with a control description embedded therein. A clock description as the conception of time is inserted in the functional C description, to be converted into a RT level C description. The RT level C description is converted into a RT level description in HDL with an existing conversion tool.
Owner:SOCIONEXT INC
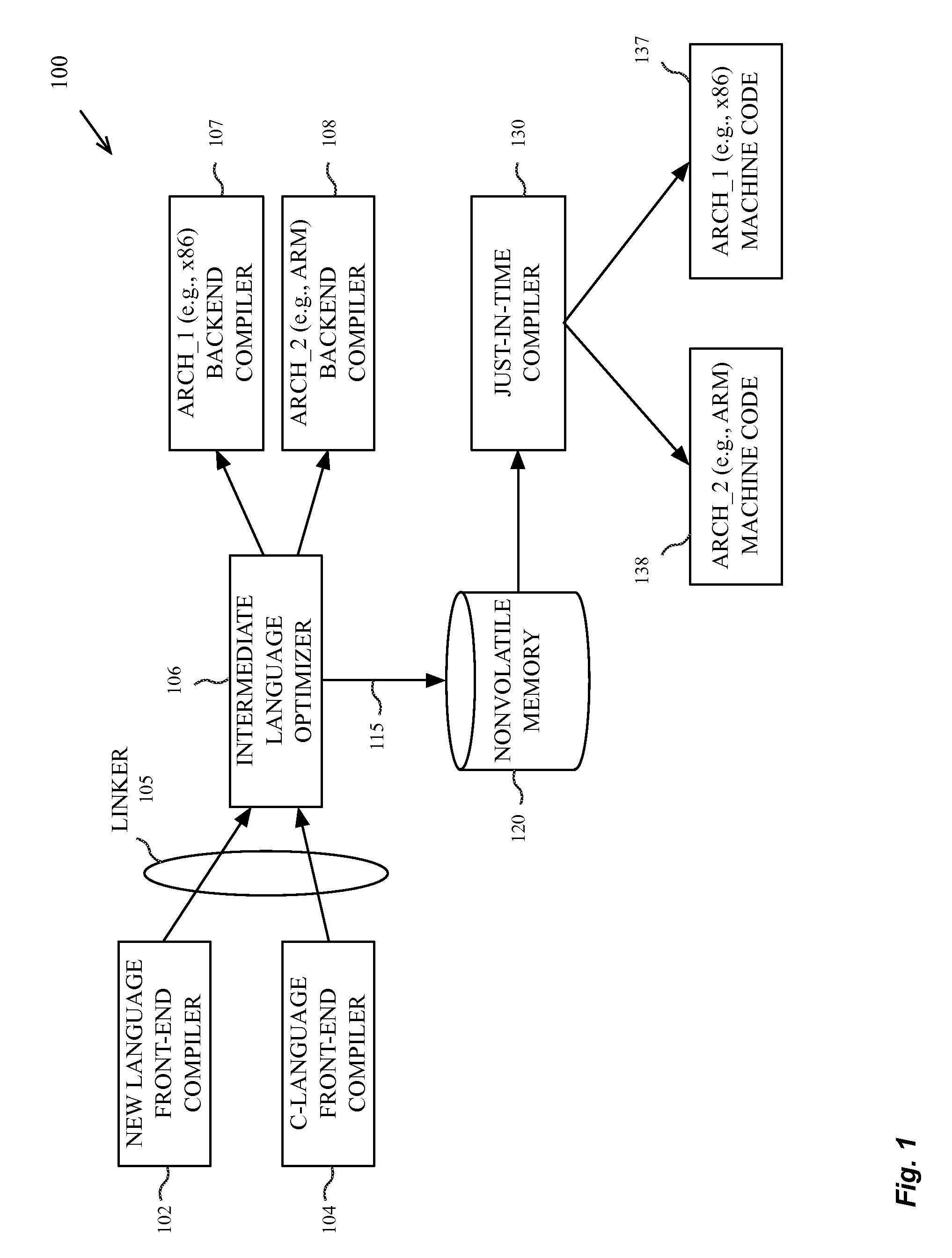
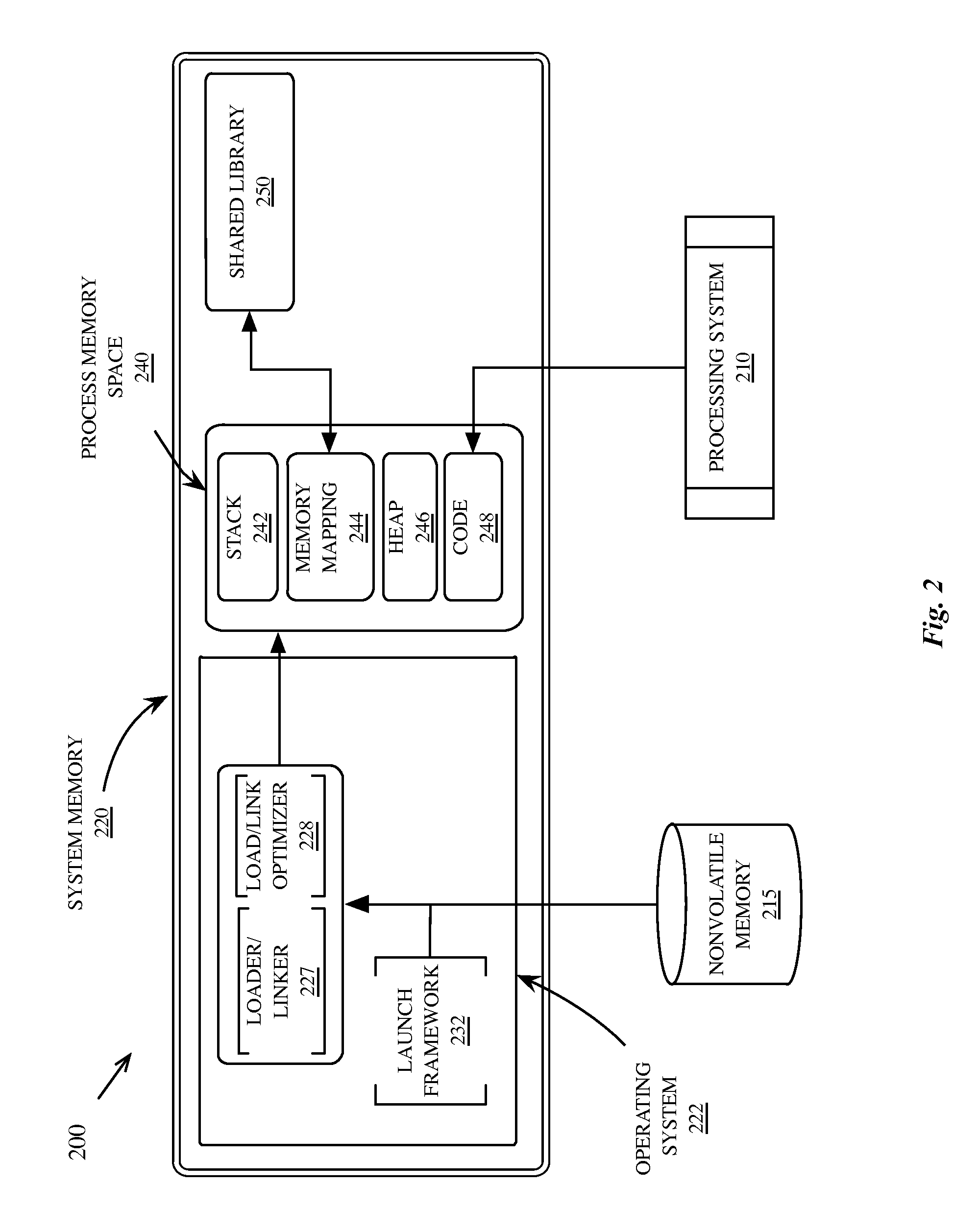
Programming system and language for application development
ActiveUS9329844B2Without harming functionalityLink editingPlatform integrity maintainanceInherent safetyComputer compatibility
In one embodiment, an improved programming system and language for application development is provided that combines elements of the C and Objective-C languages without the constraints imposed by a requirement to maintain compatibility with the C language. The language provides the functionality of the C language compatibility in certain areas to improve the inherent safety of software written in the language. The new language includes default safety considerations such as bounds and overflow checking.
Owner:APPLE INC
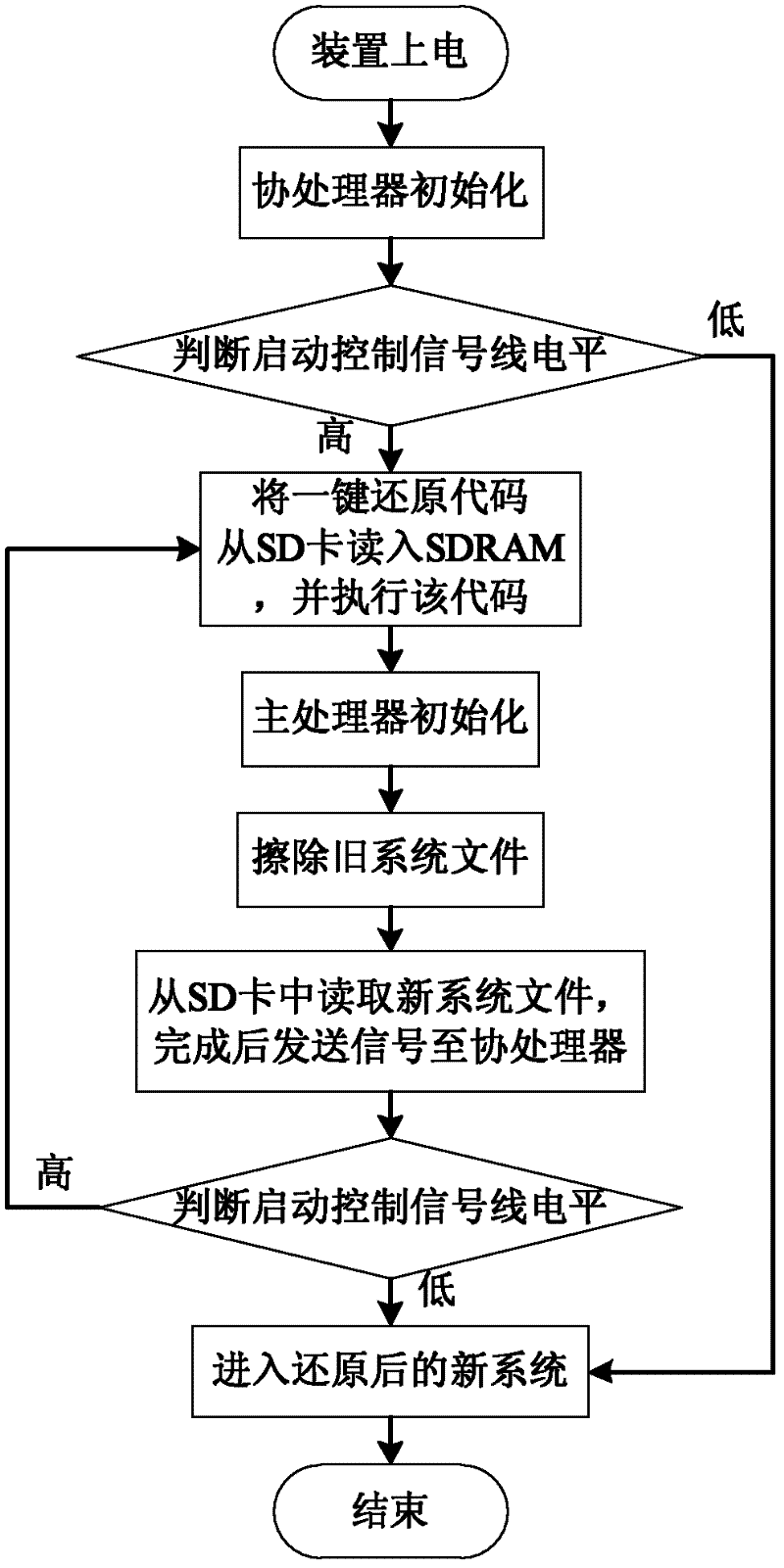
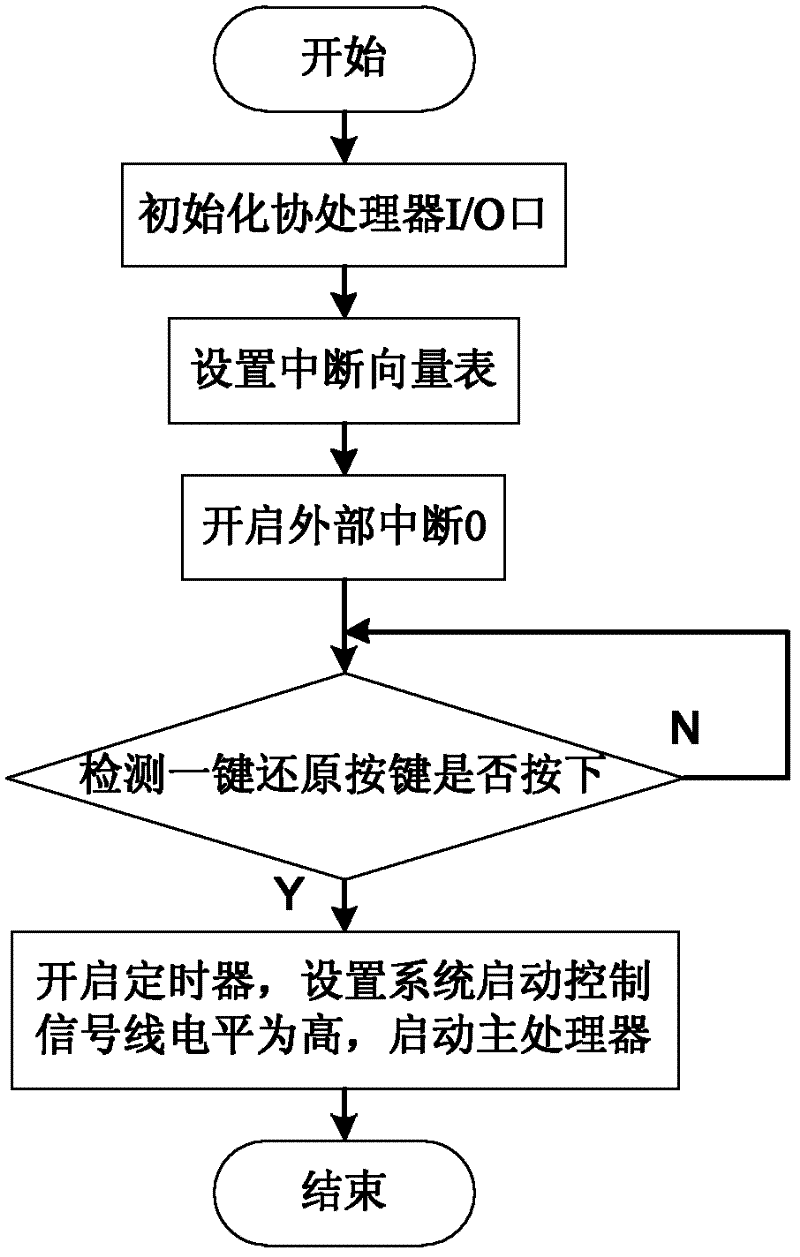
One-key reset method suitable for embedded Linux operating system
InactiveCN102520778ASolve the problem of needing to connect the upper computer to restore the systemHigh degree of intelligenceData resettingRedundant operation error correctionMicrocontrollerOperational system
A one-key reset method suitable for an embedded Linux operating system belongs to the technical field of an embedded system. The one-key reset method of the embedded operating system is constructed by C programming language and assembly language. A user starts the one-key reset of the system by a one-key reset button, and an operating system to be reset is stored in a common SD (Secure Digital) card. When the reset button is pressed, a main processor is triggered to start the level switching of a control module, and the starting mode of the main processor is changed to be in a one-key reset mode. When the reset is finished, a main processor module sends a signal to a reset module, the starting mode is changed to be a normal starting mode, the main processor module is reset, and the system is in login. The system adopts a modular design, a peripheral singlechip is additionally arranged and is taken as a coprocessor module to control the reset of the main processor and change the starting mode of the main processor. By the communication between a GPIO (General Purpose Input / Output) port and the main processor, the one-key reset method is suitable for the embedded main processors with different structures and solves the problem that a common embedded system needs to be connected with an upper computer to be reset.
Owner:SHANDONG UNIV
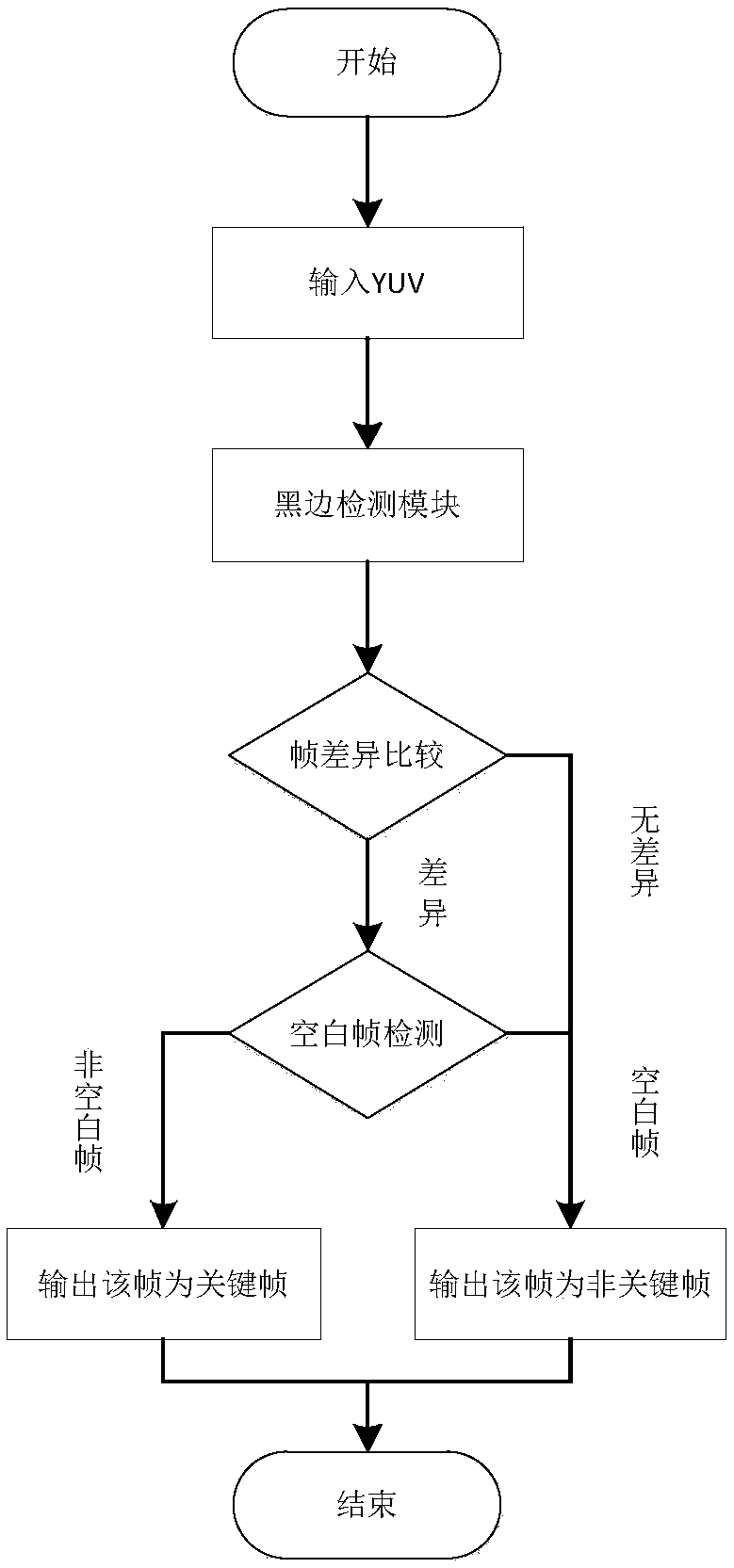
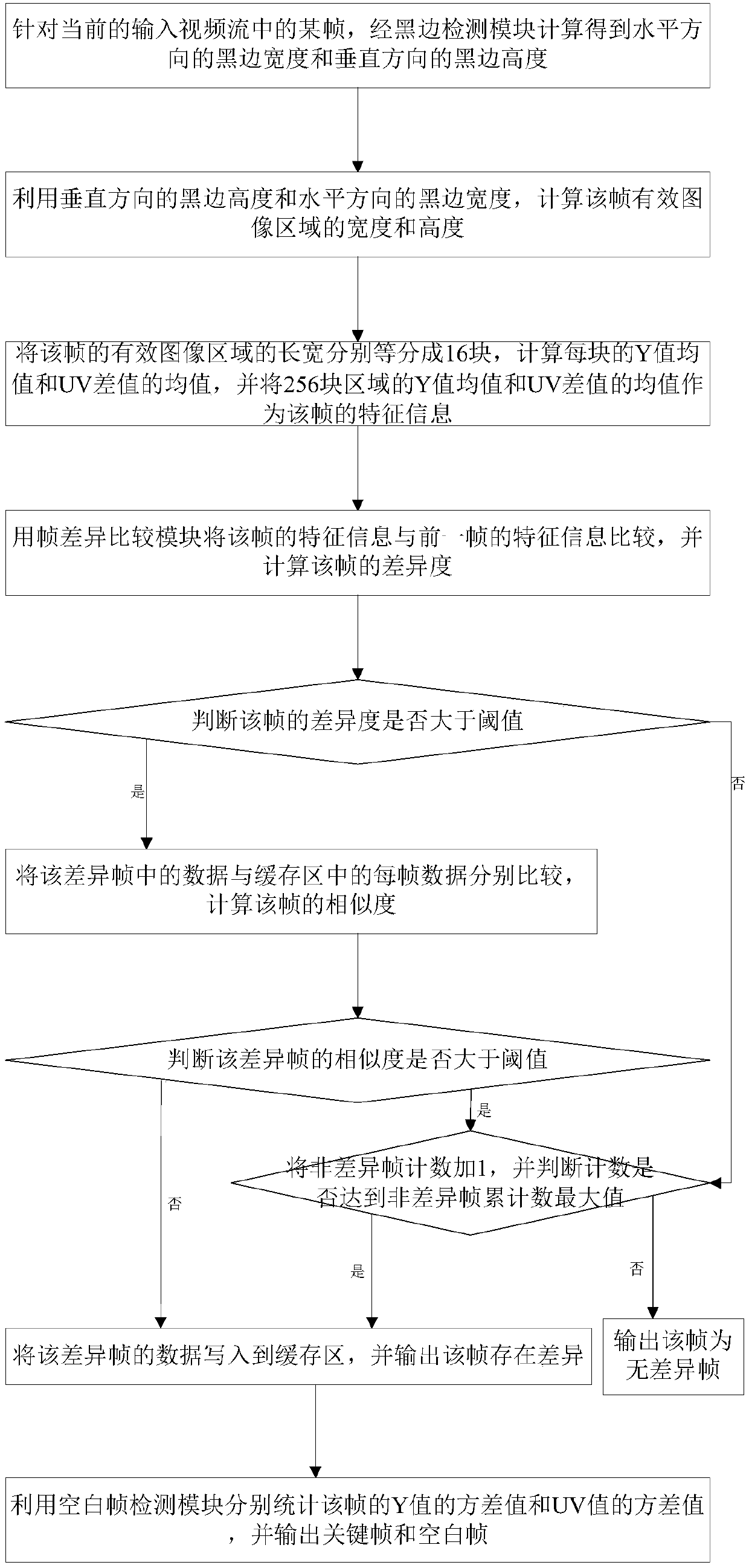
Video key frame extraction algorithm
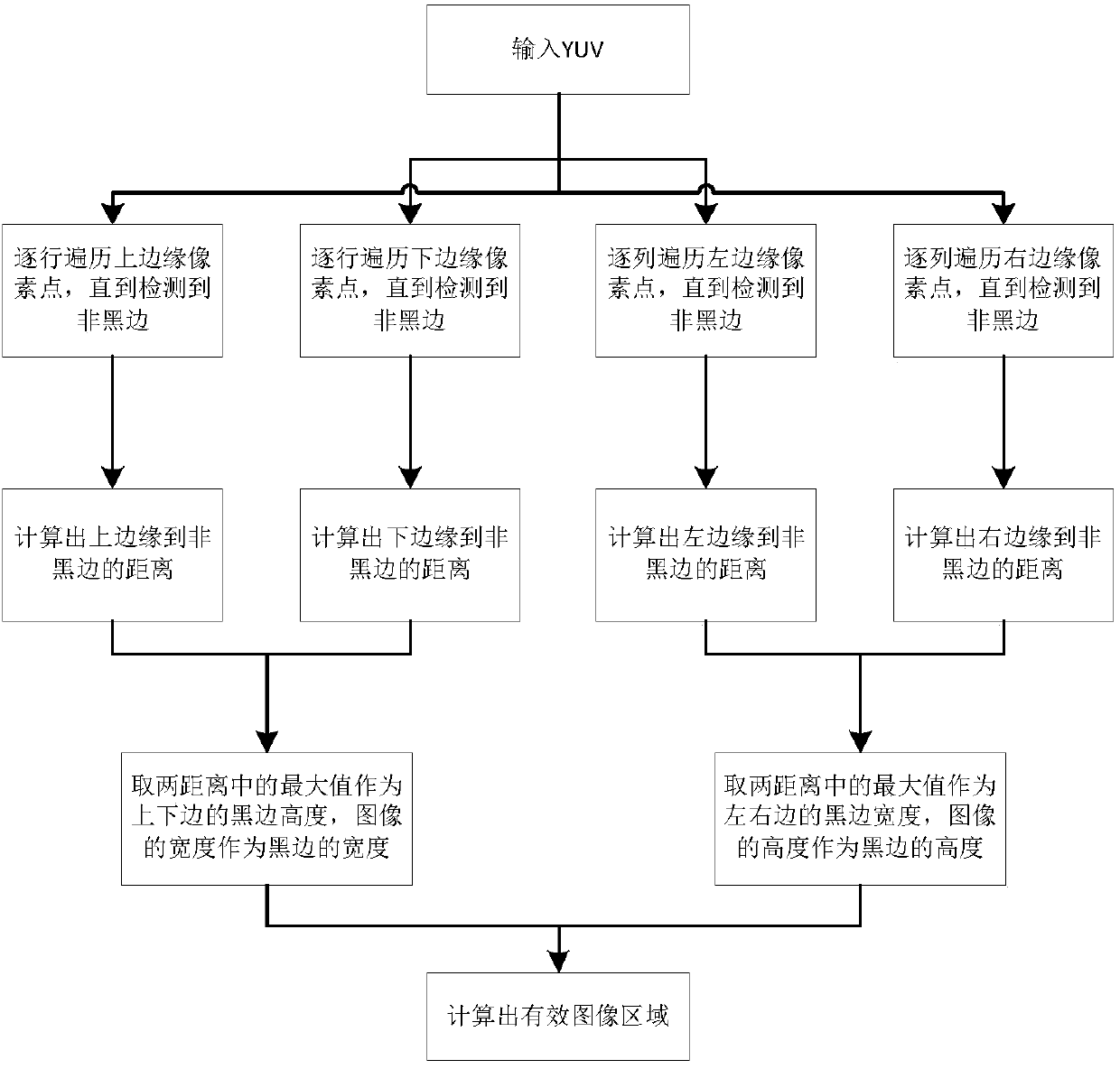
ActiveCN107832694AAdaptableCharacter and pattern recognitionSpecial data processing applicationsAlgorithmC programming language
The invention discloses a video key frame extraction algorithm, and belongs to the technical field of information security. According to the algorithm, firstly the black border width of the horizontaldirection and the black border height of the vertical direction of a certain frame in the current input video stream and the width and height of the effective image area of the frame are calculated;then the feature information of the effective image area of the frame is calculated and compared with that of the last frame so as to calculate the degree of difference; when the degree of differenceis greater than the threshold, the data in the difference frame are compared with each frame of data of a cache area so as to calculate the similarity of the frame; and when the similarity of the difference frame is greater than the threshold, the difference frame is regarded to be similar to the certain frame in the cache area, one non-difference frame is added, the maximum cumulative number of the non-difference frame is reached, the frame is outputted as the difference frame and written in the cache area, statistics of the variance value of the Y value and the variance value of the UY valueof the frame is performed and the key frame and the blank frame are outputted. The algorithm is realized by the C programming language and can be applied to multi-video and multi-thread calling so that the algorithm is high in adaptability and efficient and rapid.
Owner:BEIJING SCISTOR TECH +1
Software framework
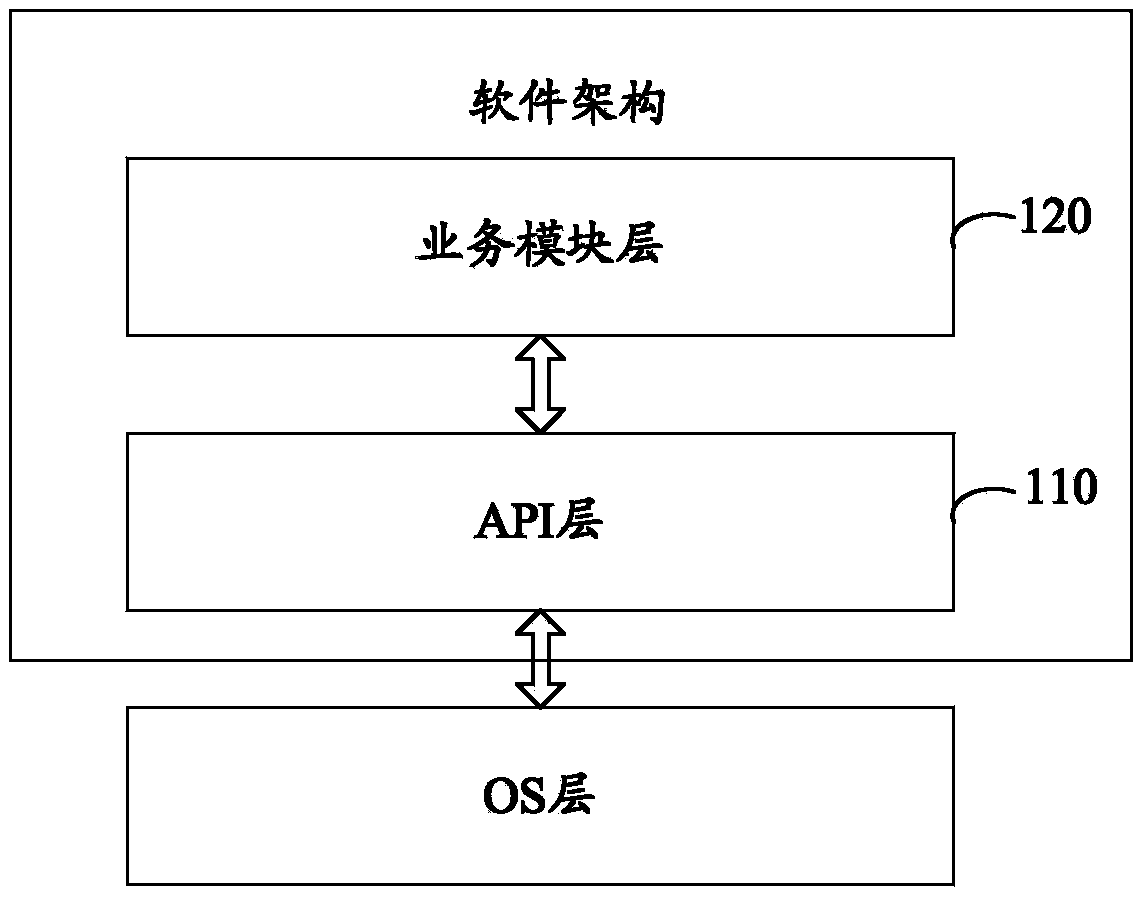
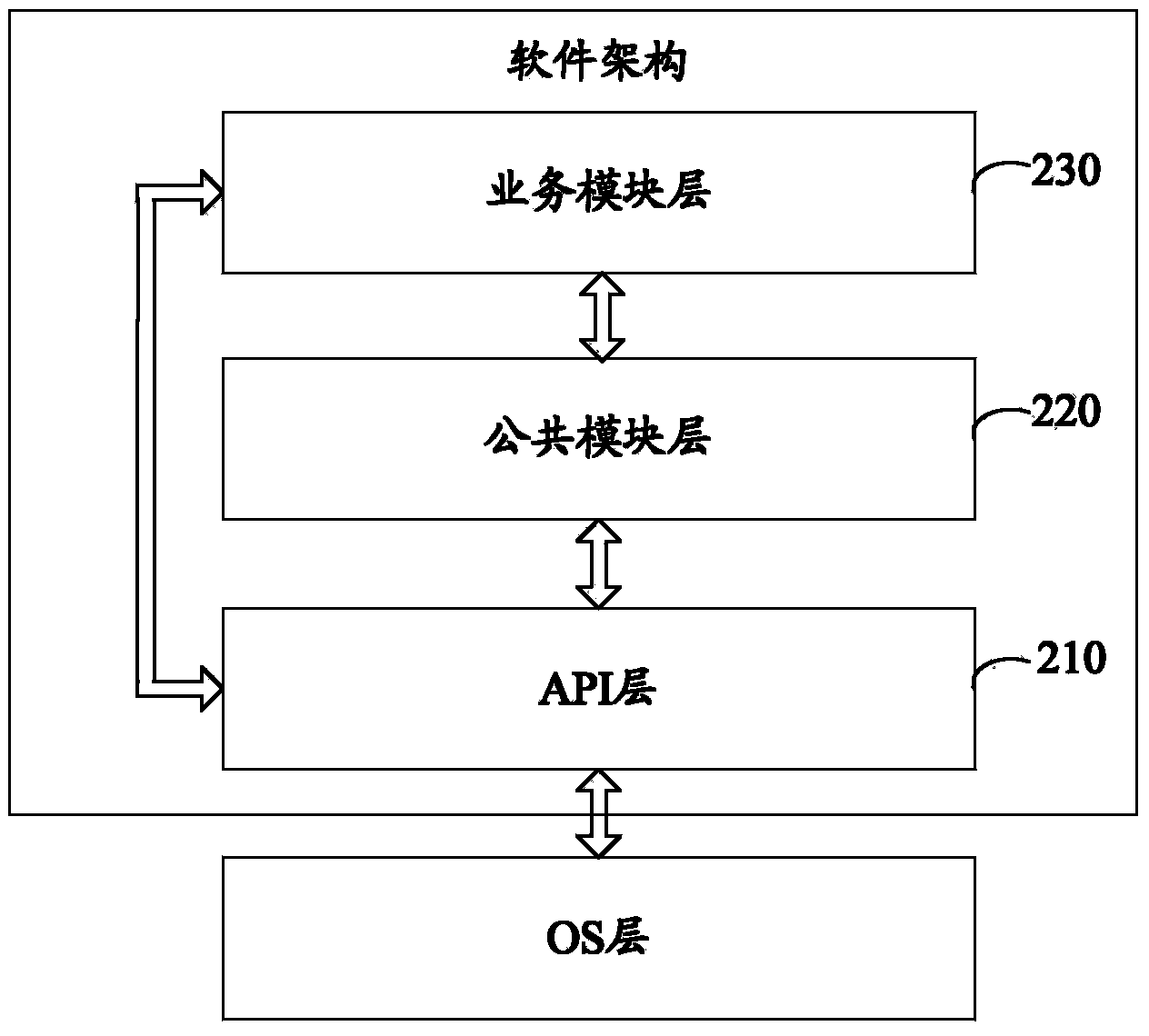
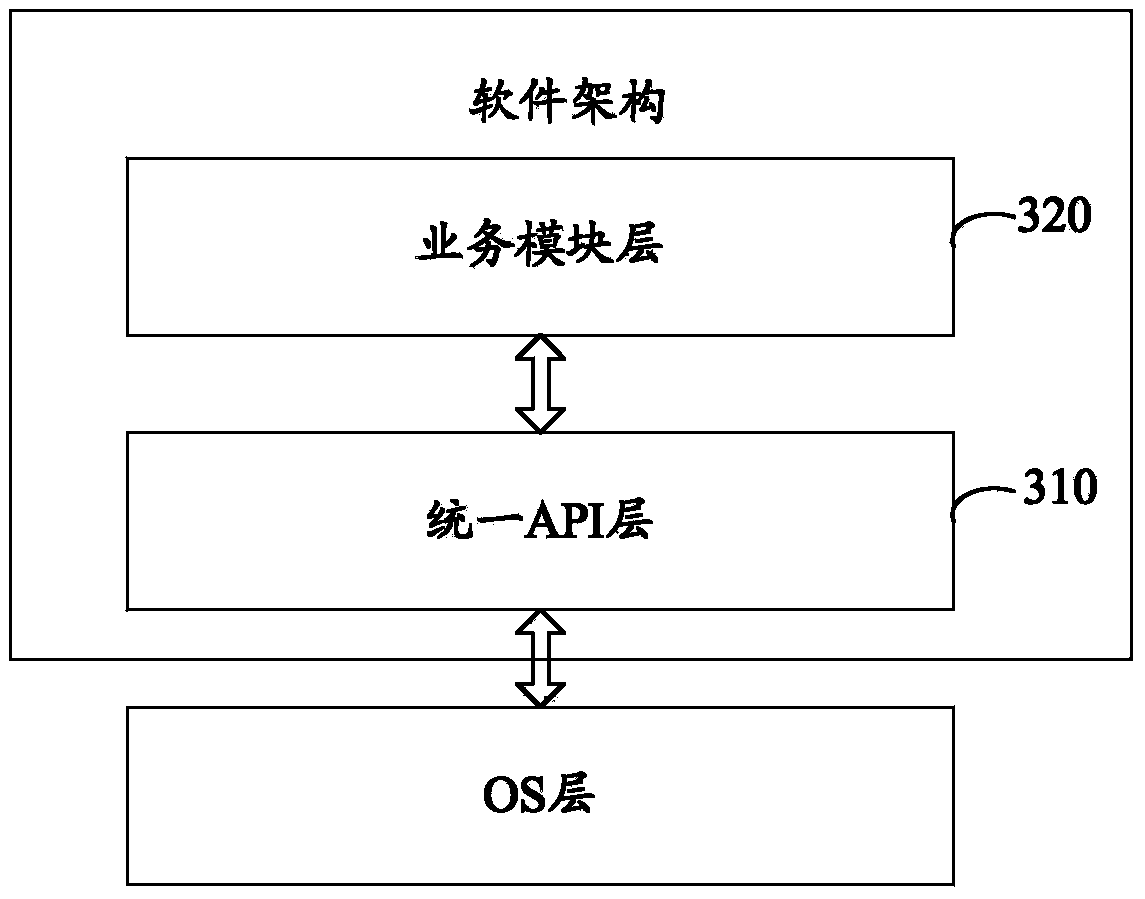
ActiveCN103399754AImprove management flexibilityHigh cohesion and low coupling characteristicsSpecific program execution arrangementsOperational systemSoftware architecture
The invention discloses a software framework which is suitable for application software running at a POS (point of sale) terminal. The software framework comprises an API (application programming interface) layer and a business module layer, wherein the API layer is based on a standard C programming language and private APIs corresponding to corresponding OSs (operation systems), and packaged with the APIs which correspond to the OSs suitable for the application software and are required by the businesses contained in the application software; the business module layer comprises business modules, each business module corresponds to one business uniquely, and software codes of each business module are achieved by calling the corresponding APIs in the API layer and the standard C programming language; and the APIs in the API layer and the business modules in the business module layer exist in a dynamic library manner, so that the dynamic loading is realized. Obviously, in the scheme, the business modules have high-cohesion and low-coupling characteristics, therefore, the business modules are mutually independent, and the management flexibility of the application software can be effectively improved.
Owner:CHINAUMS
Programming system and language for application development
ActiveUS20150347102A1Without harming functionalityLink editingPlatform integrity maintainanceInherent safetyComputer compatibility
In one embodiment, an improved programming system and language for application development is provided that combines elements of the C and Objective-C languages without the constraints imposed by a requirement to maintain compatibility with the C language. The language provides the functionality of the C language compatibility in certain areas to improve the inherent safety of software written in the language. The new language includes default safety considerations such as bounds and overflow checking.
Owner:APPLE INC
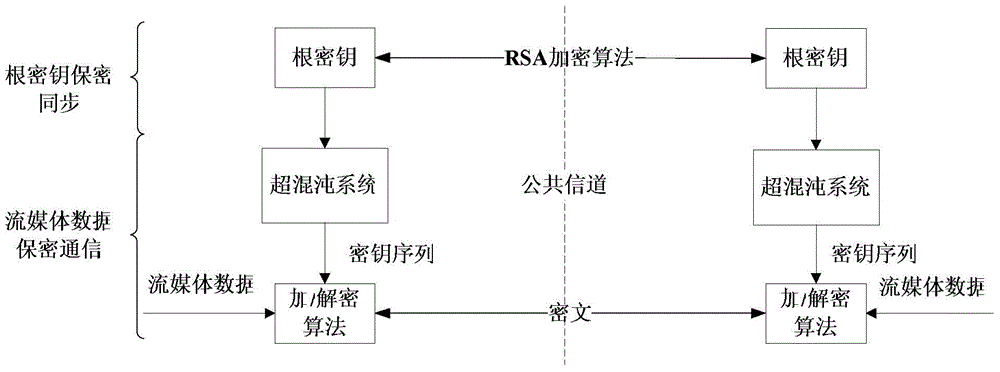
Dual-chaotic system dynamic key and RSA jointed streaming media secret communication method
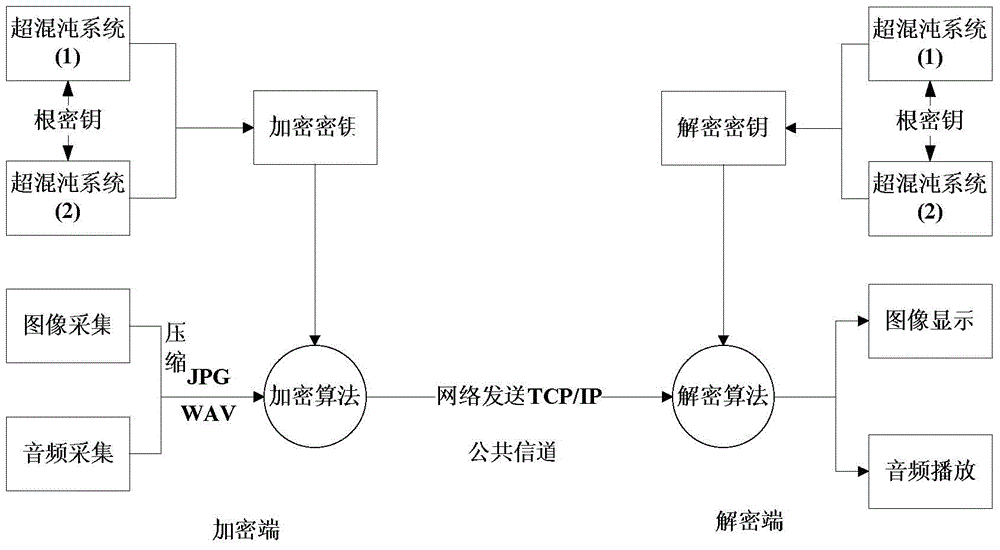
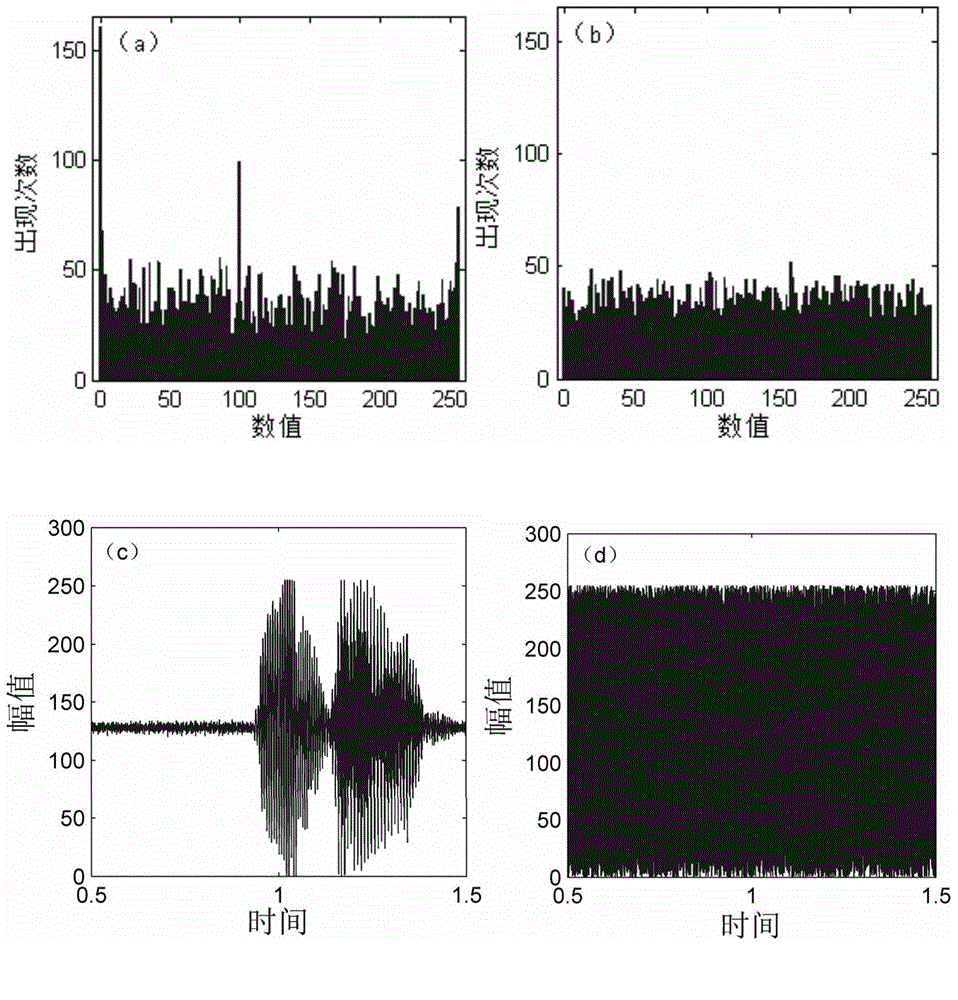
ActiveCN104618091ASatisfy securityIncrease randomnessEncryption apparatus with shift registers/memoriesChaotic systemsC programming language
A dual-chaotic system dynamic key and RSA jointed streaming media secret communication method relates to the technical field of communication encryption and solve the problem of certain potential safety hazards and poor secrecy of streaming media communication due to the fact that the root key is not effectively protected in the network transmission process of streaming media communication. Chaotic system parameters, iterative step length generated in a chaotic sequence and the preset iteration times serve as dynamic parameters, values meeting the conditions are generated randomly before each communication and form the root key, and the root key is subject to secrecy synchronization through the RSA algorithm. Difference of root keys makes the chaotic key sequences used for each encryption and deception are different. Meanwhile, the chaotic key sequences are formed by interweaving combination of two hyper-chaotic sequences so the chaotic key sequences are more complicated. The dual-chaotic system dynamic key and RSA jointed streaming media secret communication method reduces the generating time of the chaotic key sequences and improves the encryption speed. Testing of software written through C programming language in the local area network proves that the dual-chaotic system dynamic key and RSA jointed streaming media secret communication method can meet requirements of streaming media communication for safety and timeliness.
Owner:HARBIN UNIV OF SCI & TECH
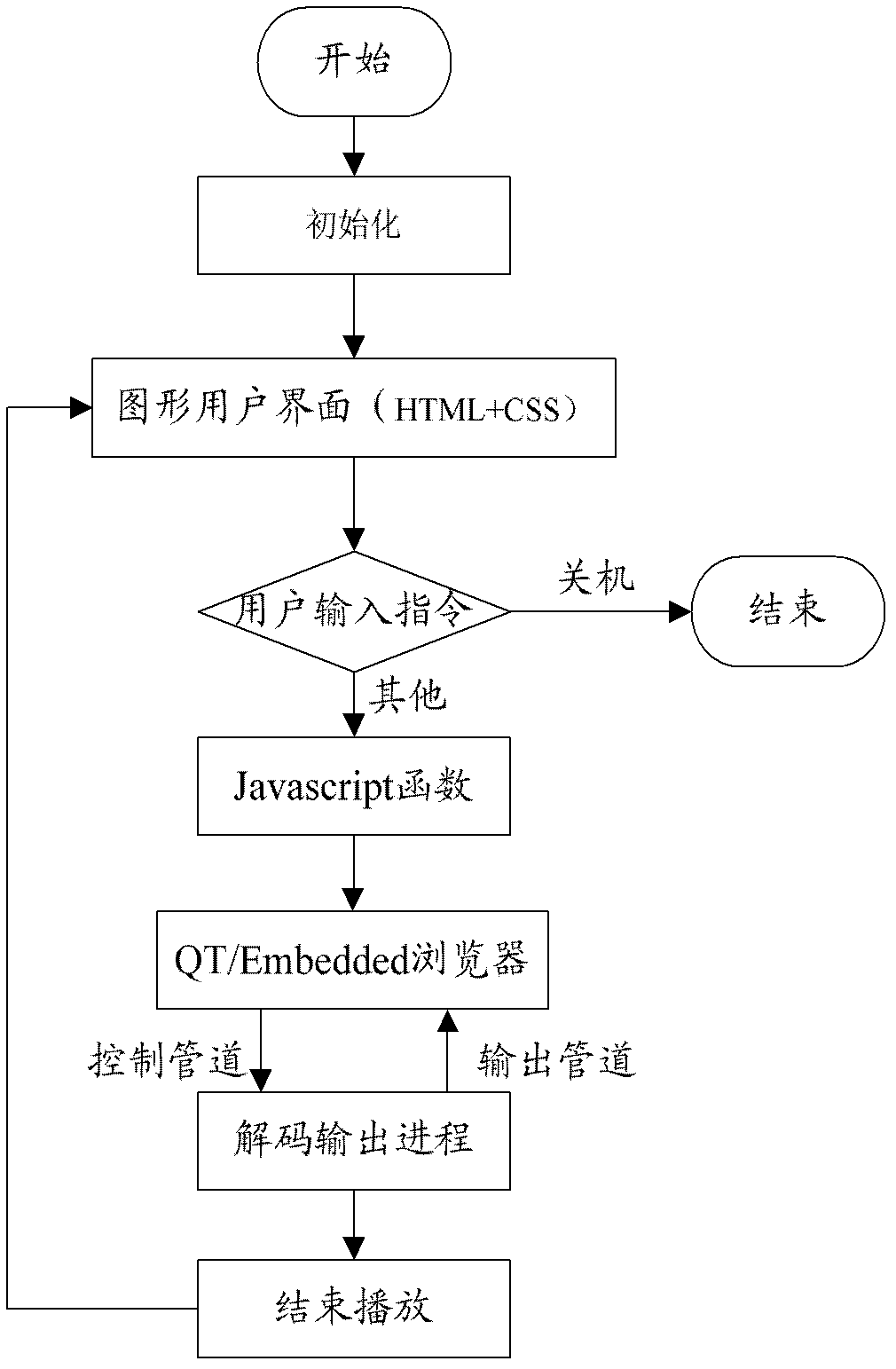
Embedded multimedia playing system and method
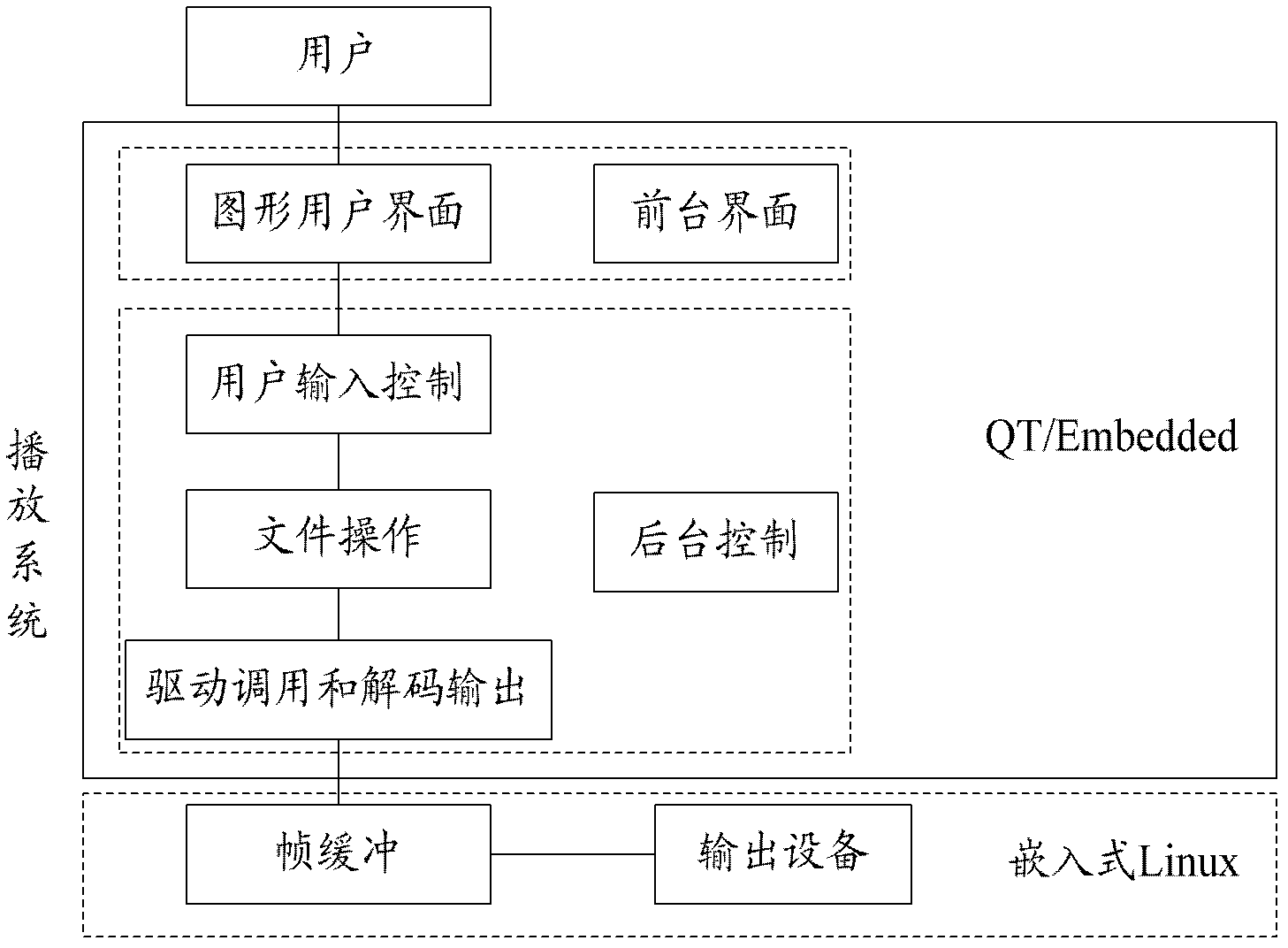
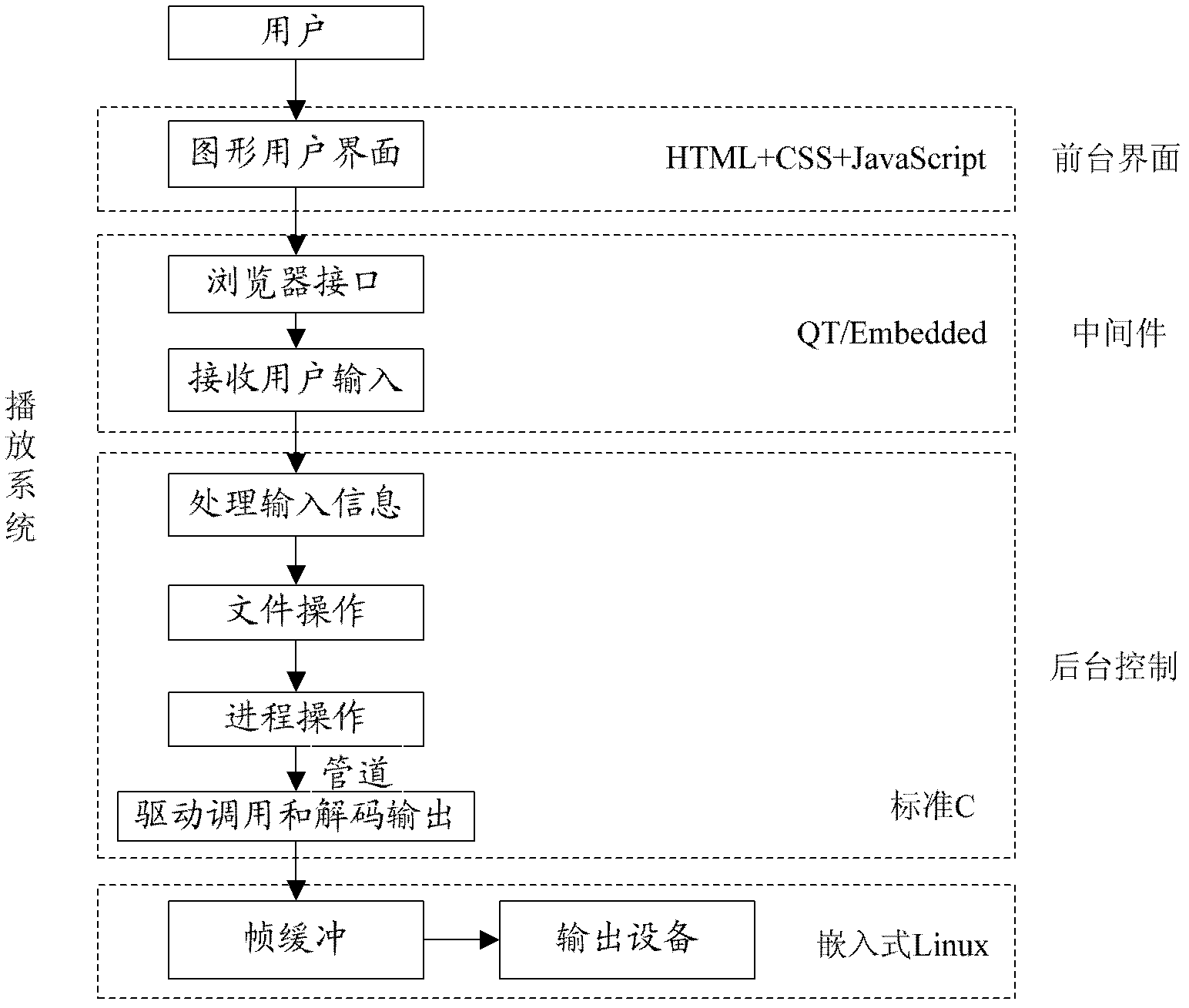
InactiveCN102681846AImprove developmentReduce couplingSpecific program execution arrangementsFault toleranceC programming language
The embodiment of the invention discloses an embedded multimedia playing system. The embedded multimedia playing system comprises a foreground interface, a middleware and a background control module, wherein the foreground interface is a graphical user interface based on hypertext markup language (HTML), cascading style sheet (CSS) and JavaScript language; the middleware is based on Qt / Embedded, is used for providing an interface and supporting display output, and is connected with the background control module; the background control module adopts standard C language; and a user inputs information from the graphical user interface, the middleware receives the information input by the user through the interface, and the background control module processes the input information, does corresponding operation and invokes a drive to perform decoding play. The Qt / Embedded serves as the middleware, the graphical user interface and the background control module are separated from the Qt / Embedded frame, the interface for accessing mutually is provided, and background control is realized by using the C language, so the coupling degree of the foreground module and the background module is reduced, the fault tolerance and the stability of the system are improved, and the using efficiency of resources is improved. The invention also discloses an embedded multimedia playing method with high fault tolerance and stability.
Owner:SUN YAT SEN UNIV
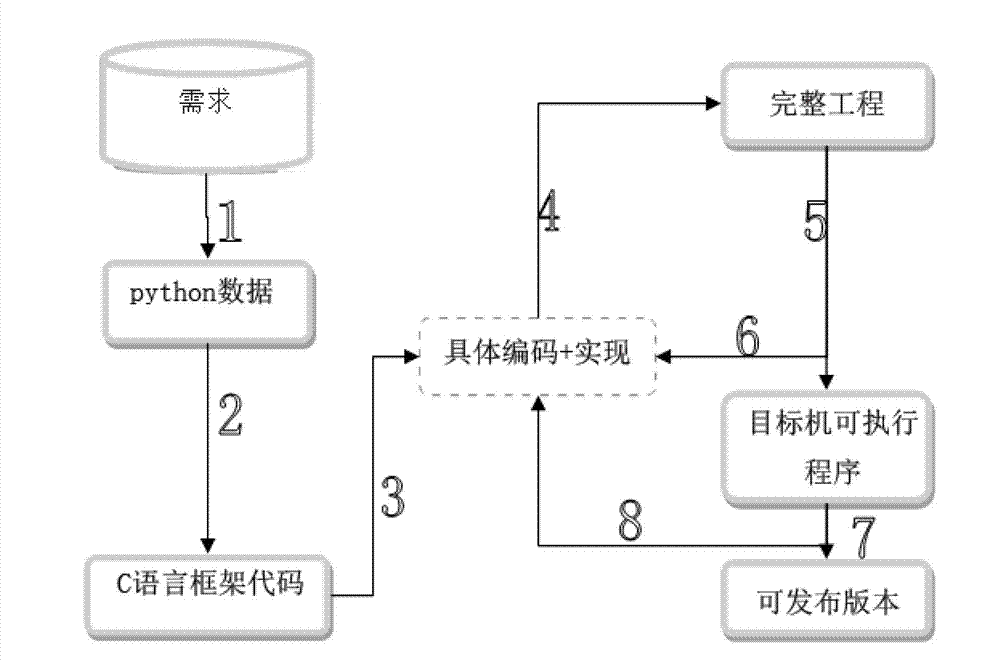
Embedded automation development method
InactiveCN102902540AFree laborImprove stabilitySpecific program execution arrangementsVisual BasicDocumentation procedure
The invention discloses an embedded automation development method which comprises the following steps of: parsing a requirement document into a data format which can be understood by python through VB (Visual Basic); translating the generated Python data to generate a related frame code of a C programming language or C++ programming language again by the python according to the actual customization needs, and supplying the frame code to a coder to use; carrying out writing by the coder on the basis of the frame code so as to realize the needed features and functions; uploading the code after writing to a code server to finish a complete code project; formulating a compiling specification and a compiling time of an item through an automatic compiling tool bamboo; if compiling succeeds, generating an executable program, introducing the executable program into a target machine through a script, carrying out automation test based on robot framework, and finally issuing a version through the test; and if the compiling fails, carrying out mail notification on the coder with a revise history on the code server, and in addition, recording an error reason and an error causing person.
Owner:ZHEJIANG CHUANGJIA DIGITAL TECH
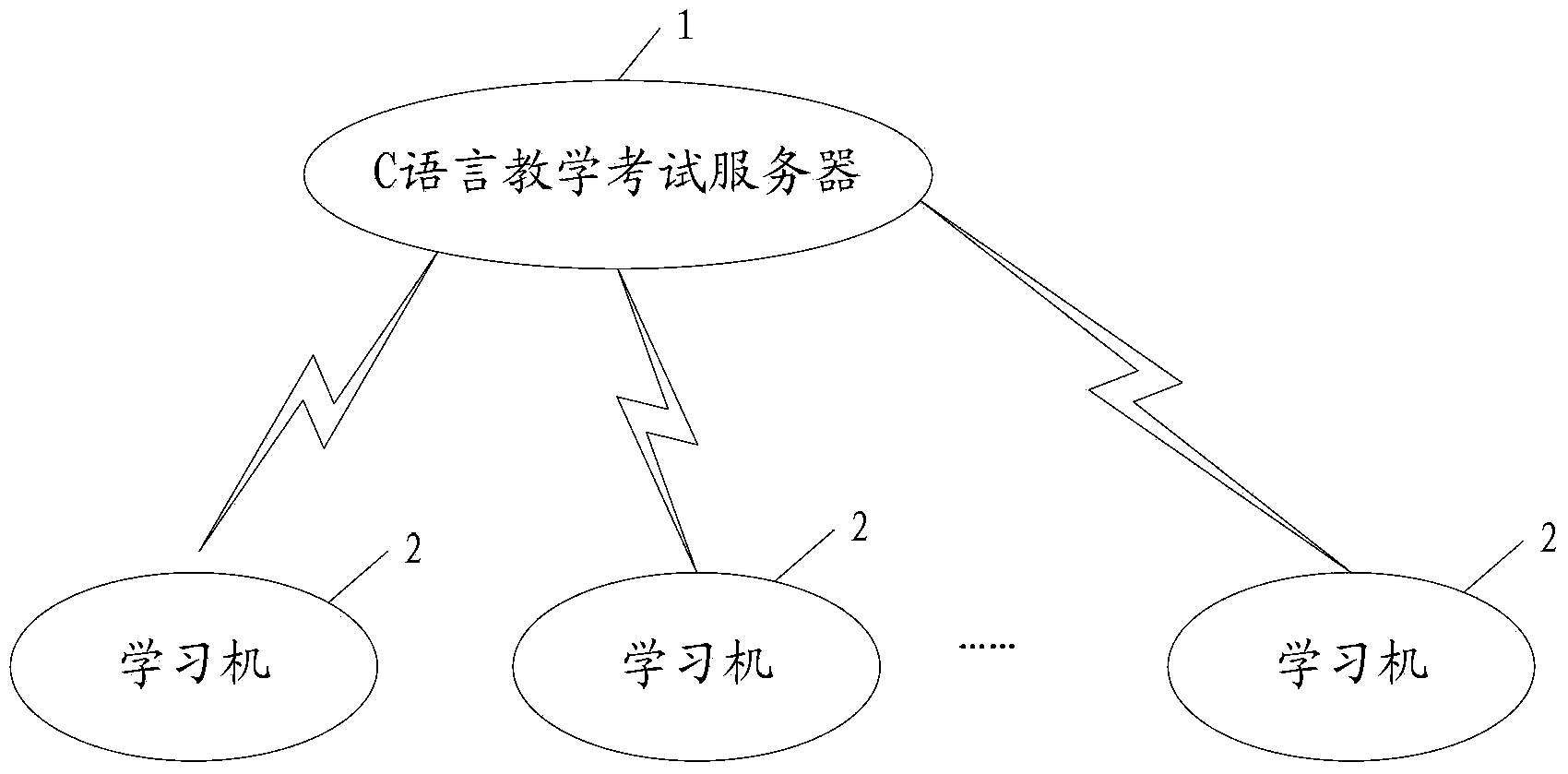
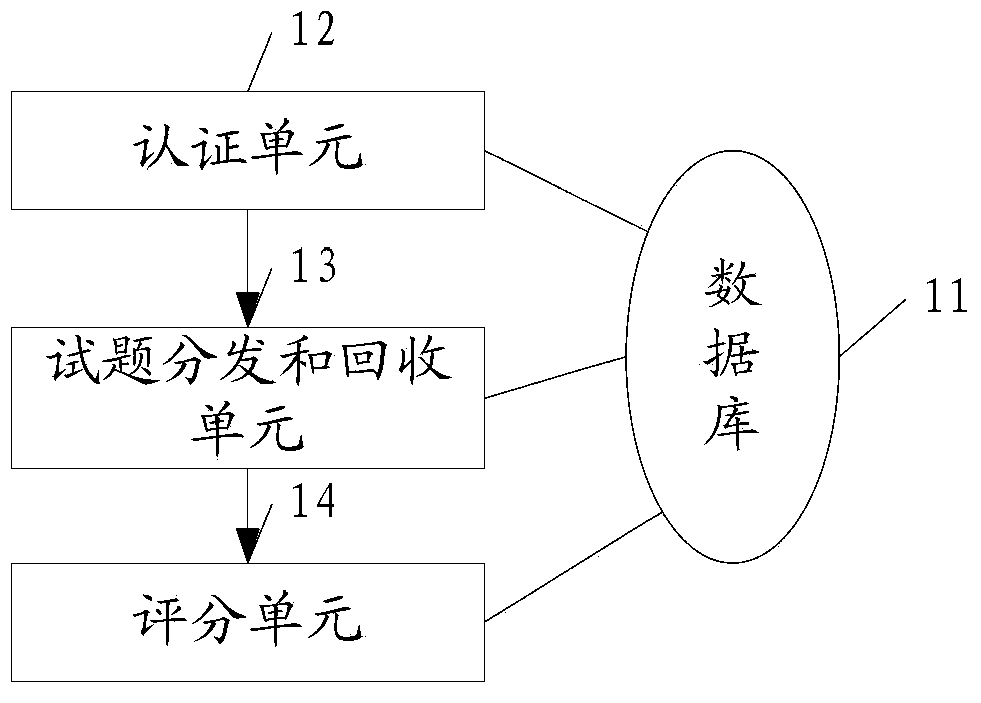
C language programming teaching and test comprehensive system and method
InactiveCN103413470AEasy to manageImprove practical programming skillsElectrical appliancesLearning machineC programming language
The invention provides a C language programming teaching and test comprehensive system and method. The C language programming teaching and test comprehensive system comprises a C language teaching and test server and a plurality of learning machines, the C language teaching and test server is connected with the learning machines through the network to form a C language programming teaching and test integrated platform, exercise and test of C language programming can be achieved for students by means of the C language programming teaching and test integrated platform, examination of the practical programming ability of the students is achieved, the programming environment where the students learn can be standardized and unified, management can be conveniently conducted on every student, and therefore the practical programming ability of the students can be effectively improved.
Owner:SOUTHWEST UNIVERSITY
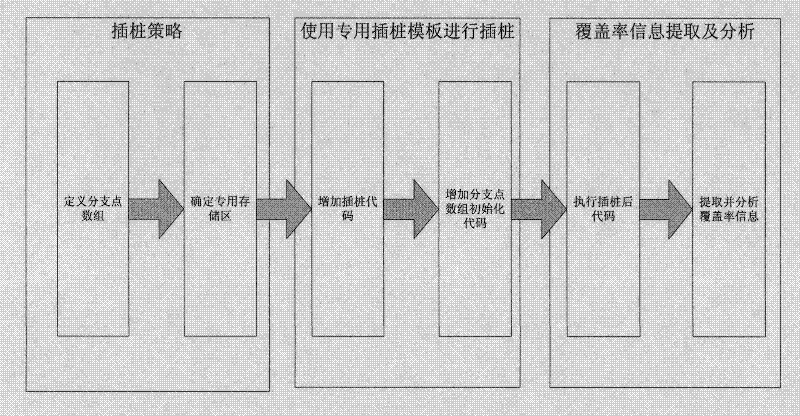
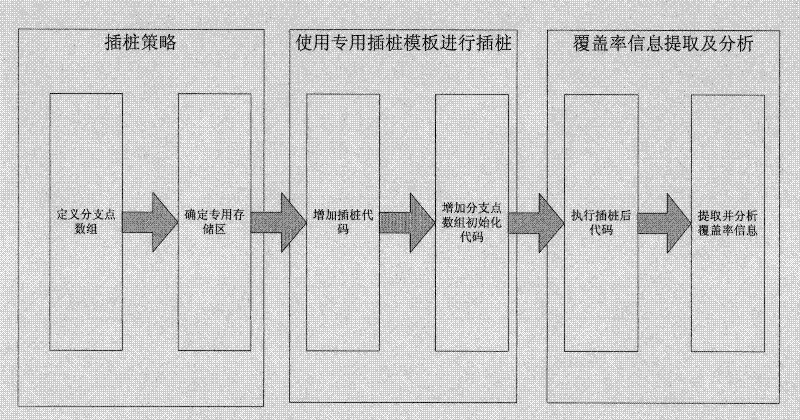
Instrumentation and dynamic test coverage information extraction method of C-language embedded software
InactiveCN102419731AReduce expansionSave storage spaceSoftware testing/debuggingAction CodeArray data structure
The invention discloses an instrumentation and dynamic test coverage information extraction method of C-language embedded software. The method comprises the following steps of: regarding a C-language program as an array which is formed by all branch points, wherein each branch point corresponds to an element in the array; defining each element to be in two states, wherein 1 represents that the branch points are executed, and 0 represents that the branch points are unexecuted; defining the array in a special storage area; at each branch point of the C-language program, adding an operation code into a branch point information array which is defined in the special storage area, wherein the operation code is used for outputting information which indicates whether the branch points are executed; executing the C-language program into which the operation code is added, and then extracting the branch point information array from the special storage area; and according to the state of each element in the branch point information array, determining the execution situation of each branch point in the C-language program, and thus obtaining the dynamic test coverage of the C-language program. The instrumentation and dynamic test coverage information extraction method of the C-language embedded software has the characteristics of low code expansion rate, small storage space of branch point information, and convenience for extraction of coverage information.
Owner:BEIJING INST OF CONTROL ENG
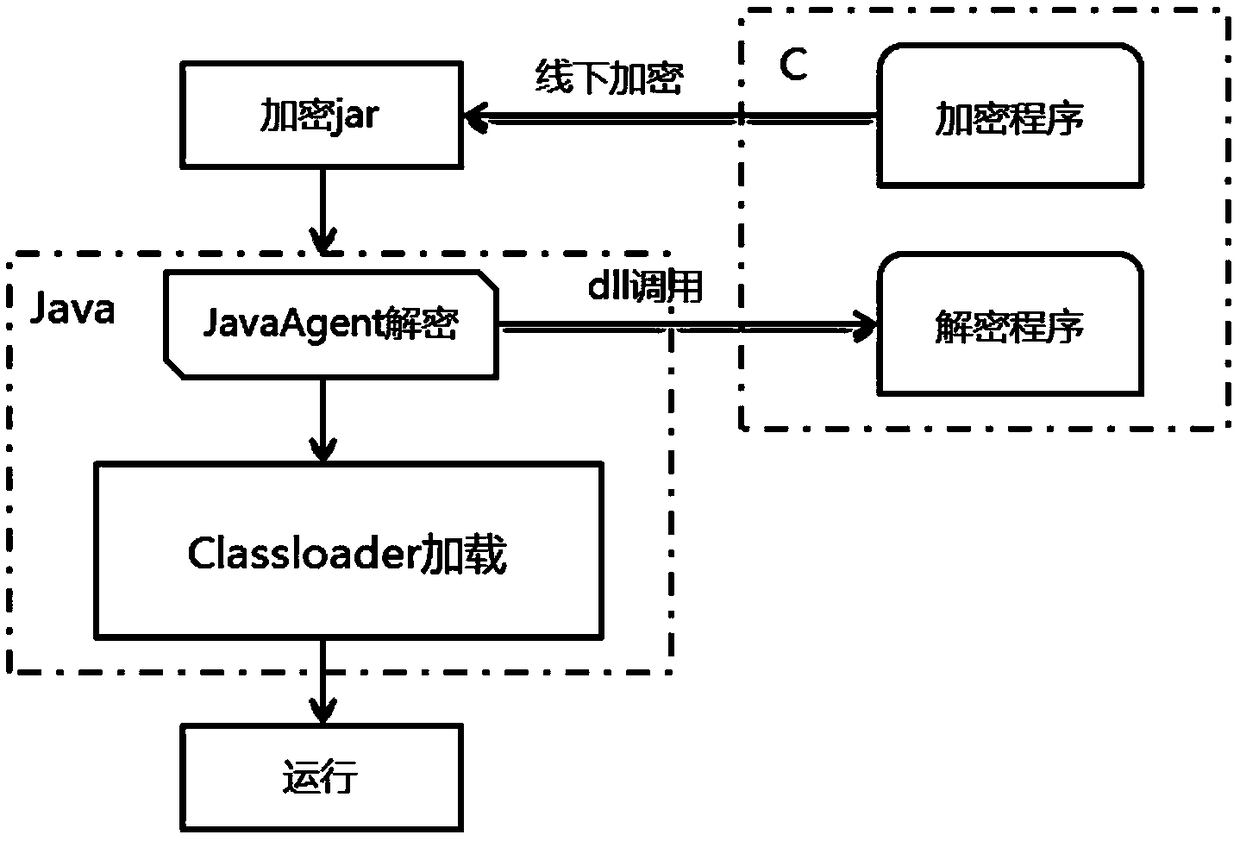
Security method for enhancing Java distribution software based on JavaAgent and dll
InactiveCN108898007ANon-invasiveDoes not affect the processProgram/content distribution protectionC programming languageByte
Provided is a security method for enhancing Java distribution software based on JavaAgent and dll. The security method comprises the following steps that step 1, an encryption program programmed withC language and jar package offline c language encryption program only needing to be released perform encryption operation; and a to-be-encrypted package jar path is transmitted to the encryption program; step 2, the encrypted jar package adds the JavaAgent into a startup script of an application, and after decryption, the JavaAgent is loaded by a Classloader and then operates. Related commands ofthe JavaAgent are used for carrying out decryption work before a jvm is loaded; the JavaAgent is a program performing intercept and modification on byte codes before Java loads a class file, and is connected to an executable file of a jar package address for decryption in a shared function library through a dll dynamic link library.
Owner:FOCUS TECH
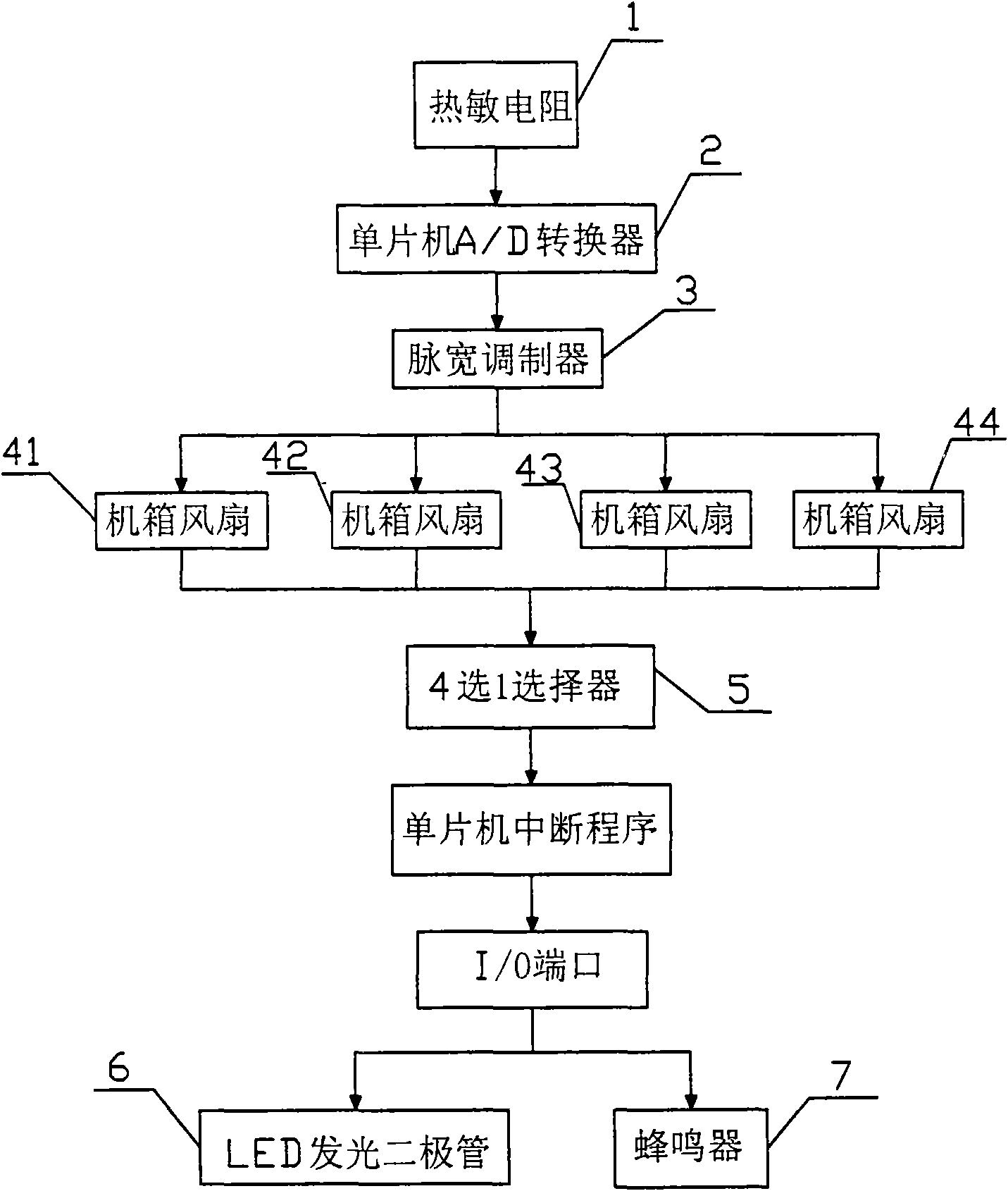
Alarmed fan module of temperature-control industrial personal computer
InactiveCN101672292ASimple designLow costDigital data processing detailsPump controlMicrocontrollerC programming language
The invention discloses an alarmed fan module of a temperature-control industrial personal computer (IPC). A single-chip A / D (analog-to-digital) converter, and a pulse width modulator (PWM) and a single-chip selector based on C programming language are arranged in a single-chip; the control module of the single-chip comprises a test circuit composed of thermistors and the single-chip A / D converter, a control circuit composed of the PWM and a chassis fan, and an alarm circuit composed of the single-chip selector, an LED (light-emitting diode) and a buzzer; a 74HC151 chip-selection integrated chip is arranged in the single-chip selector; and the single-chip is a 8-bit single-chip. Since the functional circuits are integrated by the single-chip, and most functions are achieved by the C programming language in the single-chip, the invention has the advantages of simple circuit design, low cost and good performance; and the invention provides an alarm device, thereby better solving the problem that faults occurring to the cooling fan cannot be found in a timely manner and providing reliable guarantee for the safe operation of the IPC.
Owner:上海爱瑞科技发展有限公司
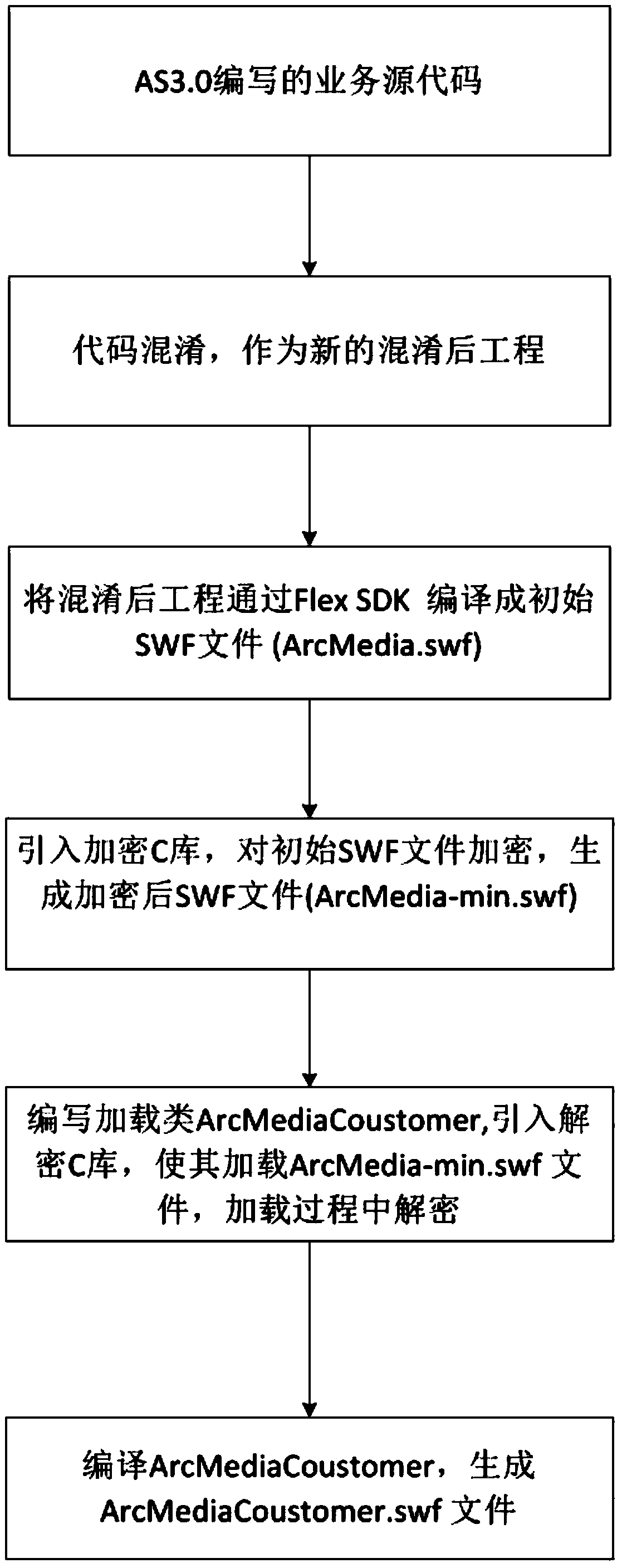
A method for SWF obfuscation encryption
InactiveCN109740314ANot readable in plain textProtect technical privacyProgram/content distribution protectionObfuscationPrivacy protection
The invention discloses a method for SWF confusion encryption. The method specifically comprises the following steps: (1) determining a to-be-protected core AS3.0 engineering file source code; (2) compiling a universal confusion class, and confusing the contents of the files in the source packet; (3) compiling the mixed source code into a source SWF file through a Felx SDK; (4) comiling an encryption tool, enabling the encryption tool adopt an encryption method compiled by a C language, and after an SWF file is read according to byte streams, conducting AES encryption on the SWF file; (5) compiling an application for loading the SWF for loading the SWF file generated in the last step; and (6) compiling and publishing the application in the step (5) into a formal SWF file, and externally providing the formal SWF file for a client to use. The method has the beneficial effects that the personal technology is protected from being stolen by a hacker for reuse, byte stream encryption is carried out on the SWF file generated by compiling, and the effects of double encryption and technical privacy protection are achieved.
Owner:HANGZHOU ARCVIDEO TECHNOLOGY CO LTD
Cloning programming code
Techniques for cloning programming code are disclosed. In an embodiment, the cloned code is in the form of functions in the C language. Further, in a method embodiment, a clone of a function is invoked, and information mapping the clone to the function is generated. At link time, if no function body of the clone is accessible by a linker, then the linker uses information mapping the clone to the function to satisfy a linker's requirement. At load time, if no function body of the clone is accessible by a loader, then the loader, based on the mapping information, allows selection of a body of the function. However, if the body function of the clone is accessible by the loader, then the loader allows selection of the body of the clone.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Analysis method and monitoring method for C language simulation model
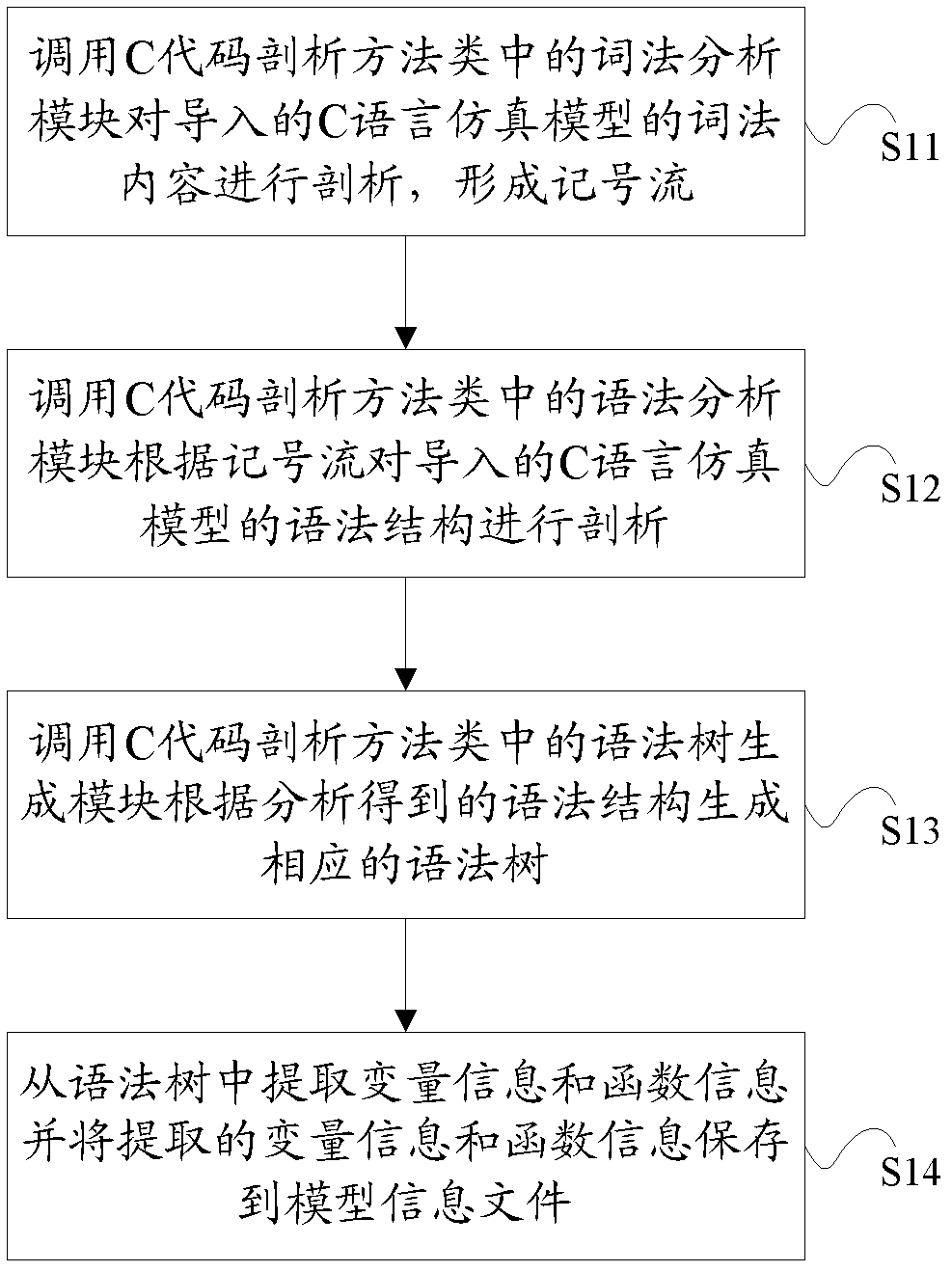
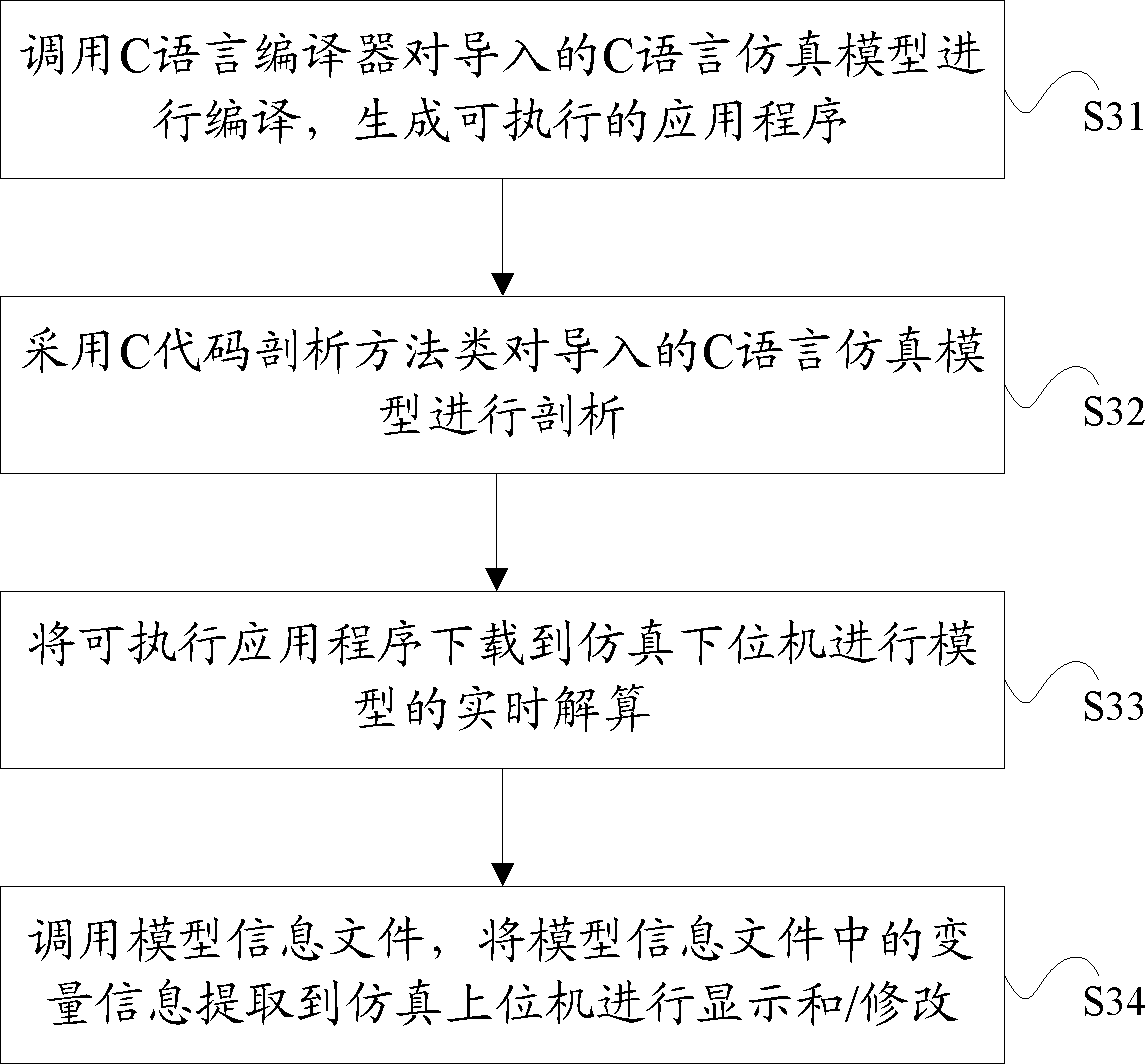
ActiveCN102629213AApplicable analysisApplicable monitoring requirementsProgram controlMemory systemsLexical analysisC programming language
The invention provides an analysis method for a C language simulation model. A C code analysis method category is generated by grammar files in advance, wherein the C code analysis method category comprises a syntax analysis module, a lexical analysis module and a syntax tree generation module. The method includes the steps that the lexical analysis module in the C code analysis method category is called to analyze lexical content of the imported C language simulation model, so as to form a token flow; the syntax analysis module is called to analyze the syntax content of the imported C language simulation model according to the token flow; the syntax tree generation module is called to generate a corresponding syntax tree according to the syntax content obtained through analysis; and information is extracted from the syntax tree and stored in a model information file. The invention further provides a monitoring method of the C language simulation model. The monitoring method comprises the analysis method. The analysis method and the monitoring method provided by the invention fill in the present blanks in the C language simulation model analysis and monitoring technology in china, and the implementation processes of the analysis method and the monitoring method are simple.
Owner:BEIJING RUNKE GENERAL TECH
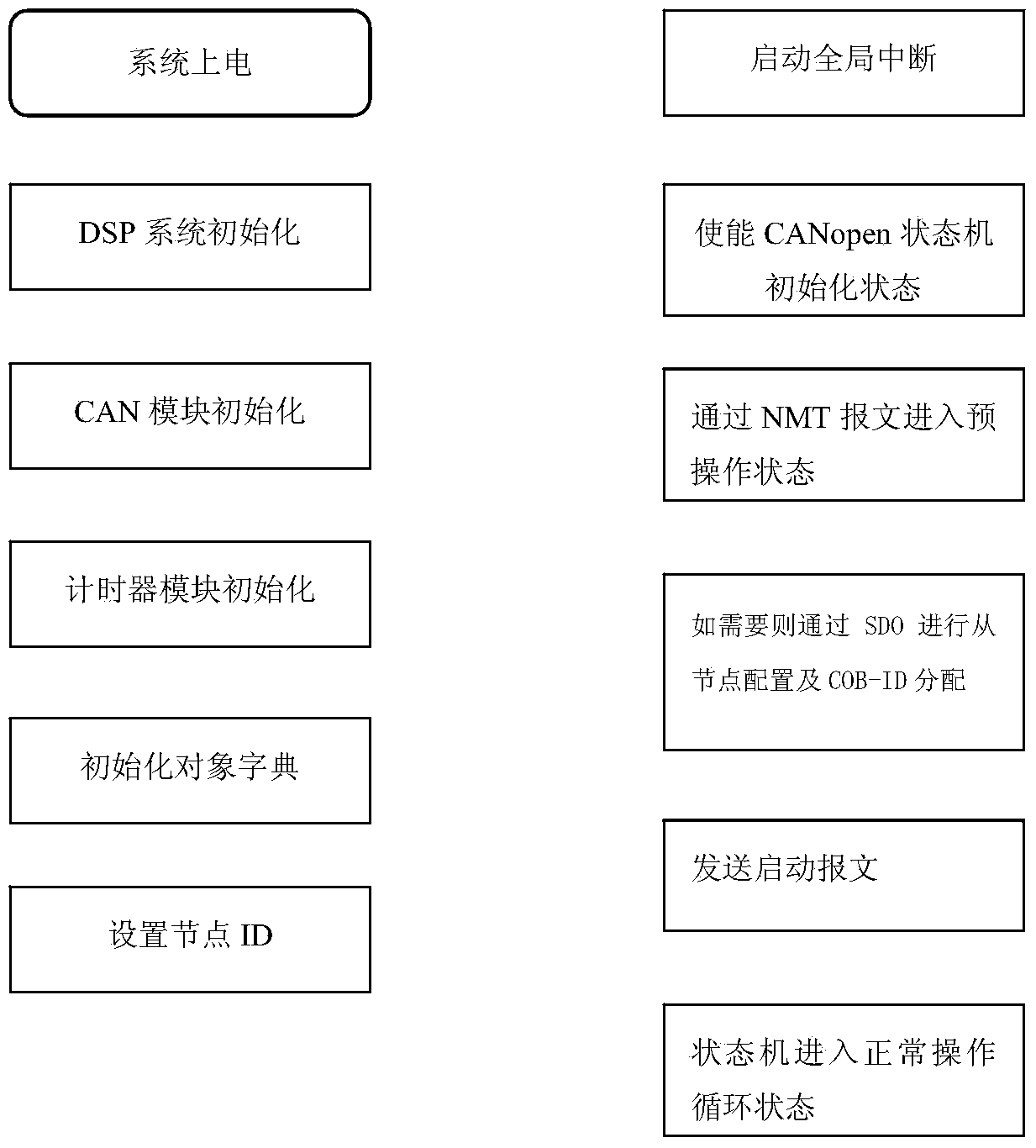
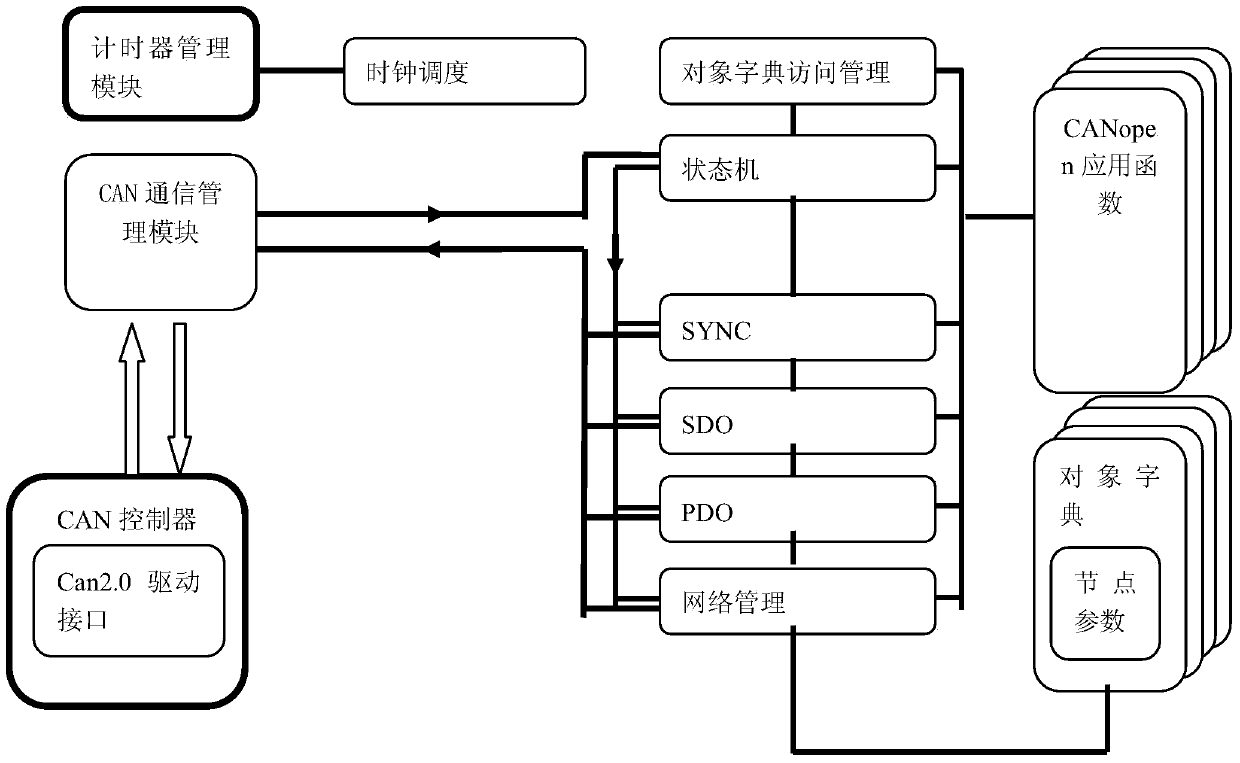
Implementation method of CANopen master station based on DSP 28335
The invention discloses an implementation method of a CANopen master station based on DSP 28335. The CANopen master station comprises a CanOpen protocol slave stack system, a state machine module, a CAN communication management module, an object dictionary management module, a network management module, a timer management module and a communication object management module. The implementation method of the CANopen master station based on the DSP 28335 has the advantages that the method that a DSP 28335 platform is configured to be the perfectly functional CANopen master station through simple configuration is adopted, and the targeted optimization CANopen slave node function is achieved on the DSP 28335 platform and can be ported to a CPU of the same series through simple modification; writing of the standard C programming language has good porting performance; codes can be reduced, the occupied system resource is small, and instantaneity is high. Standard C programming language writing highly fits other user programs so that seamless link and imbedding among the programs can be achieved, applicability is high, development cost is low, maintenance and function extension are convenient, and miniaturization of products is facilitated.
Owner:RENERGY ELECTRIC TIANJIN
Database server performance evaluation implementation method based on Informix
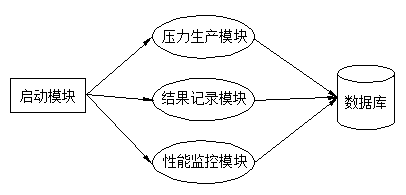
InactiveCN103970876AAchieve standardizationEasy to transplantError detection/correctionSpecial data processing applicationsDatabase serverSoftware engineering
The invention discloses a database server performance evaluation implementation method based on Informix. The C programming language and the SQL are used for development, the method is compatible with host systems of different structures, and a performance evaluation standard model is provided for an Informix data system; the performance evaluation standard model mainly comprises a starting module, a pressure generating module, a result recording module and a performance monitoring module; the performance evaluation method achieves standardization and routinization of an Informix pressure testing model, meanwhile avoids harmful effects on later performance evaluation of complex SQL statements and programmer levels, is convenient to transplant, and is compatible with the host systems of different structures.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
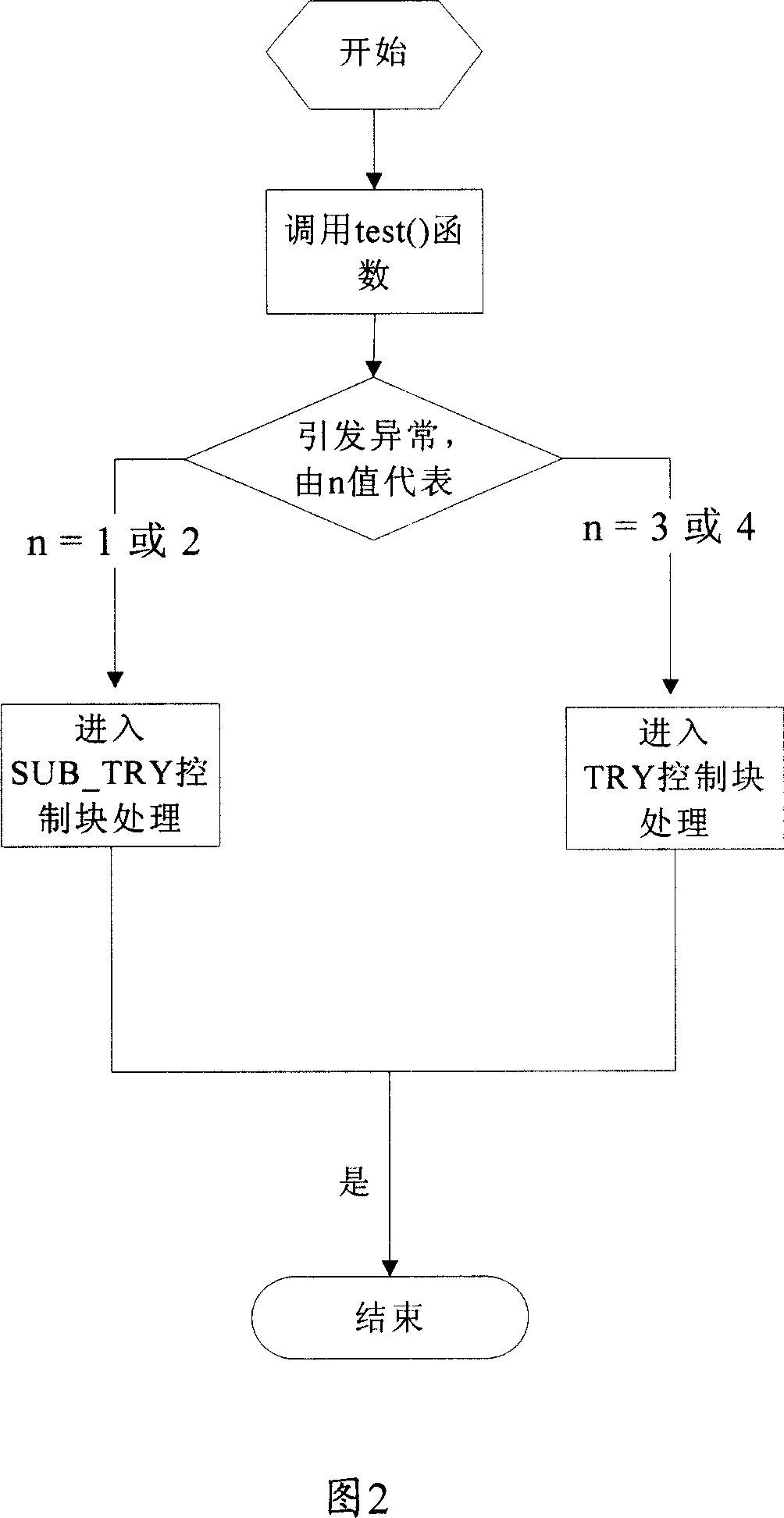
A method making nonlocal skip tool imitated into exception mechanism by C programming language
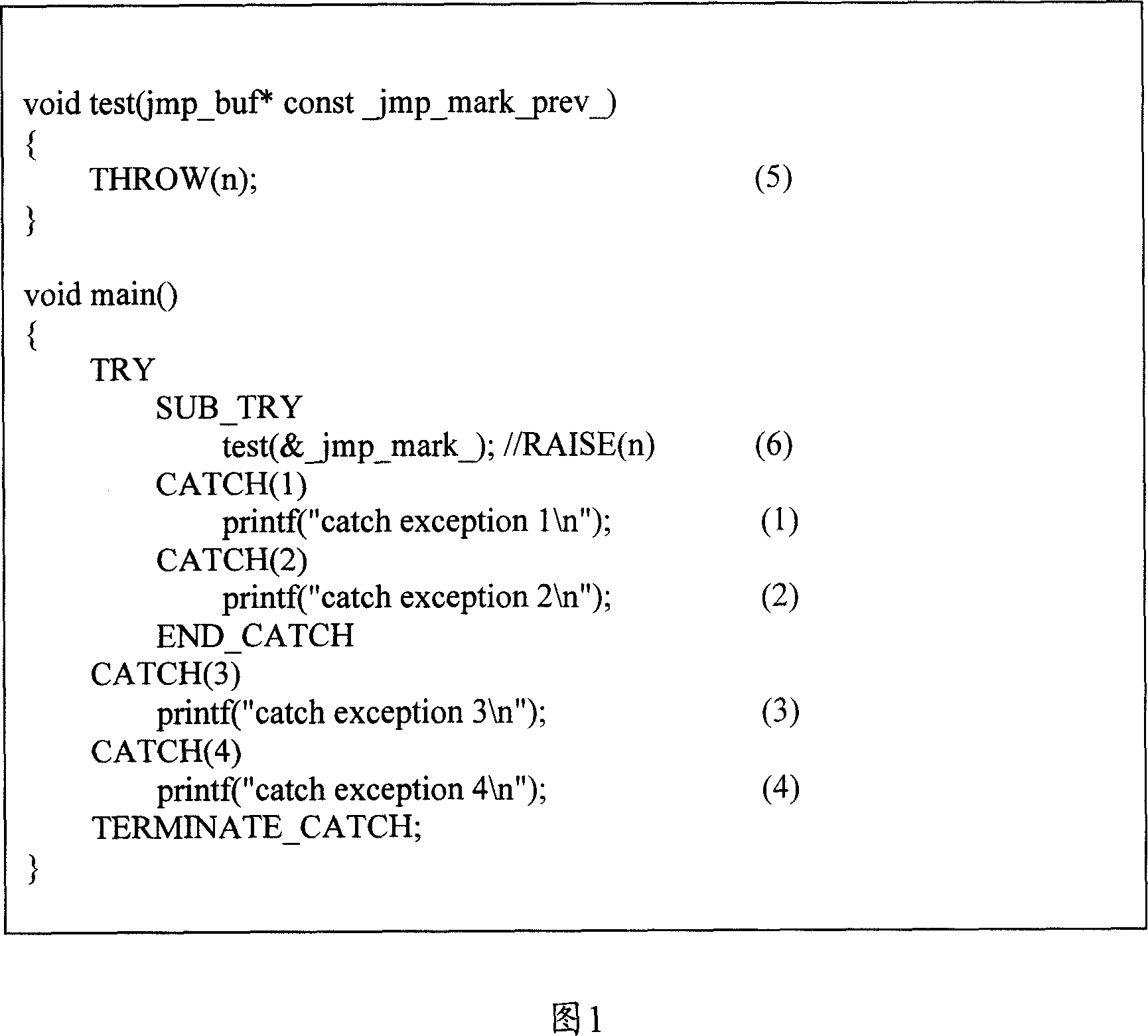
InactiveCN1952880AFlexible process controlEffective process controlProgram initiation/switchingSpecific program execution arrangementsSoftware engineeringNon local
This invention discloses a method to use C language non local jump tool analogue abnormal mechanism, which comprises the following steps: in each needed jump flow control point using setjmp to record transfer environment; when the transfer function enters next layer flow to keep front layer transfer environment variable; when executing flow jump, transferring non local jump tool to front record transfer environment.
Owner:KONKA GROUP
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com