Security method for enhancing Java distribution software based on JavaAgent and dll
A security and software technology, used in computer security devices, program/content distribution protection, instruments, etc., can solve problems such as weak customizability, inability to decrypt files that can be divided into different ways, etc. effect of difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] In order to make the technical scheme, technical purpose and technical effect of the present invention clearer, the present invention will be further described in detail below in conjunction with specific embodiments.
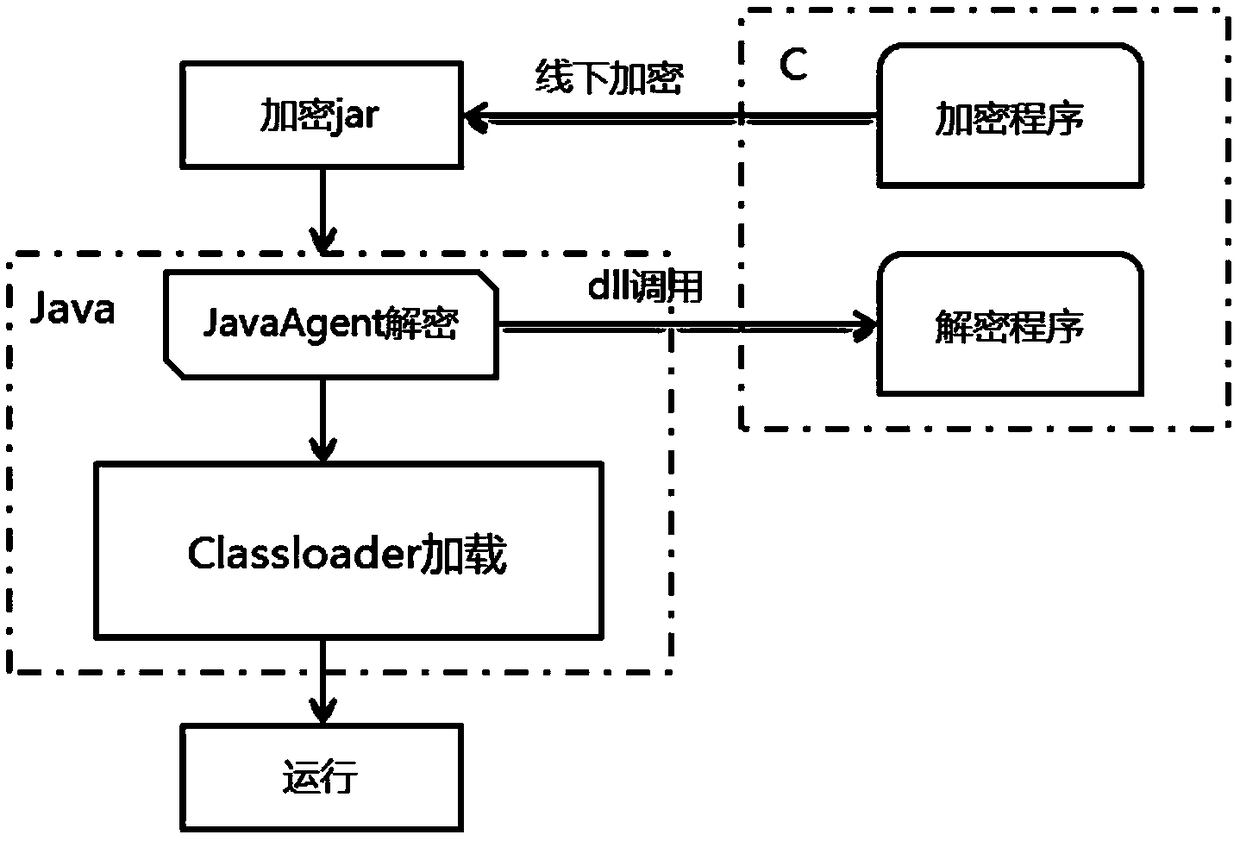
[0017] 1. Complete the development of the application according to the normal process, and package it into a jar package or war package to be released.
[0018] Execute the C language encryption program, and pass the packaged jar package or war package path. The encryption program will encrypt the corresponding jar package / war package. Generate encrypted jar package / war package. The encrypted jar package / war package cannot be run directly through java commands or containers, and cannot be decompiled. An encryption program written in C language, which encrypts the jar package to be released;
[0019] 2. Add JavaAgent-related commands in the startup script of the application to decrypt before loading the jvm.
[0020] Modify the application startup scr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com