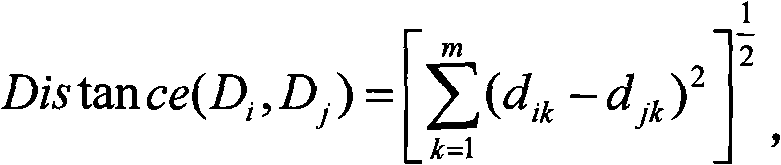Patents
Literature
100 results about "Requirement document" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
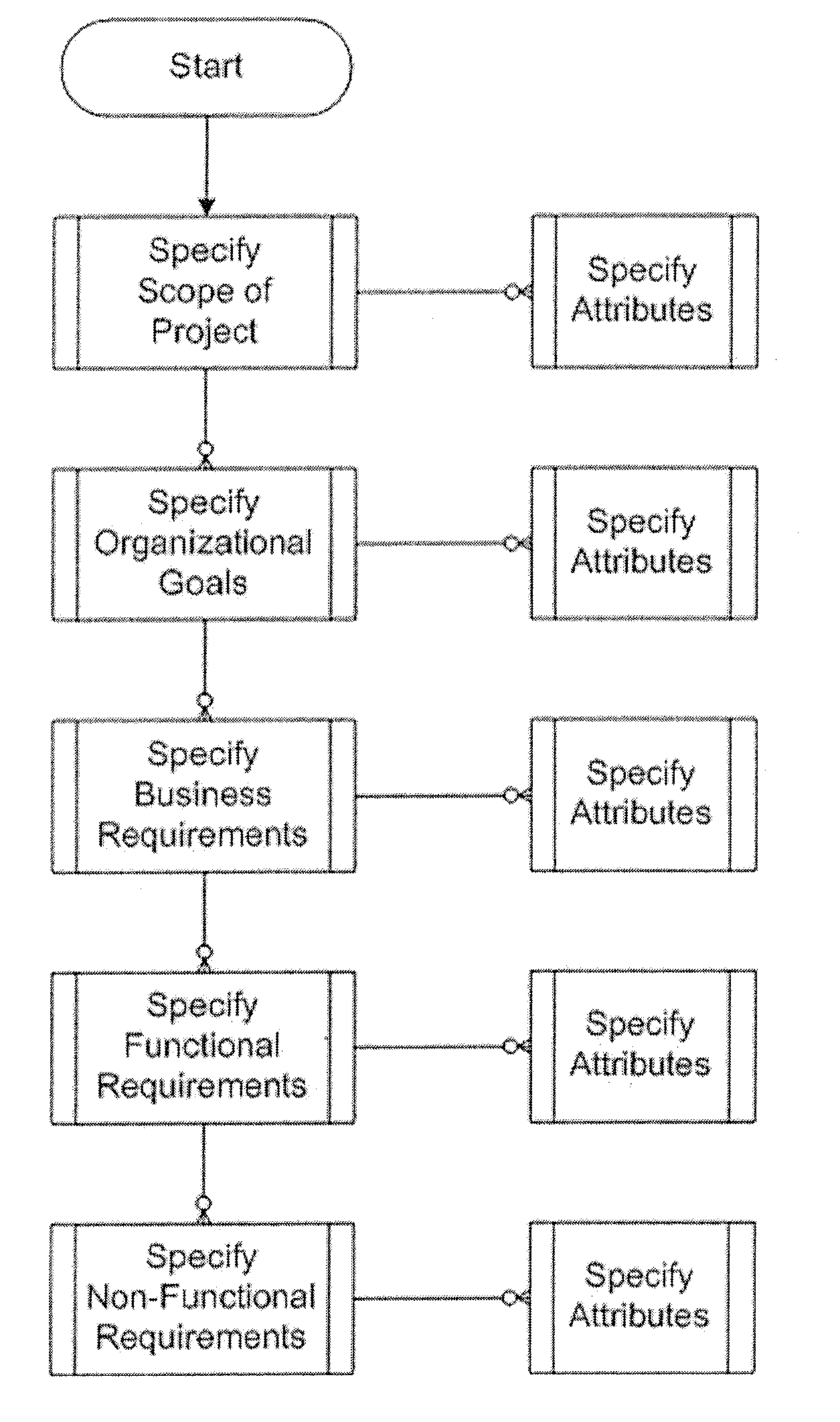
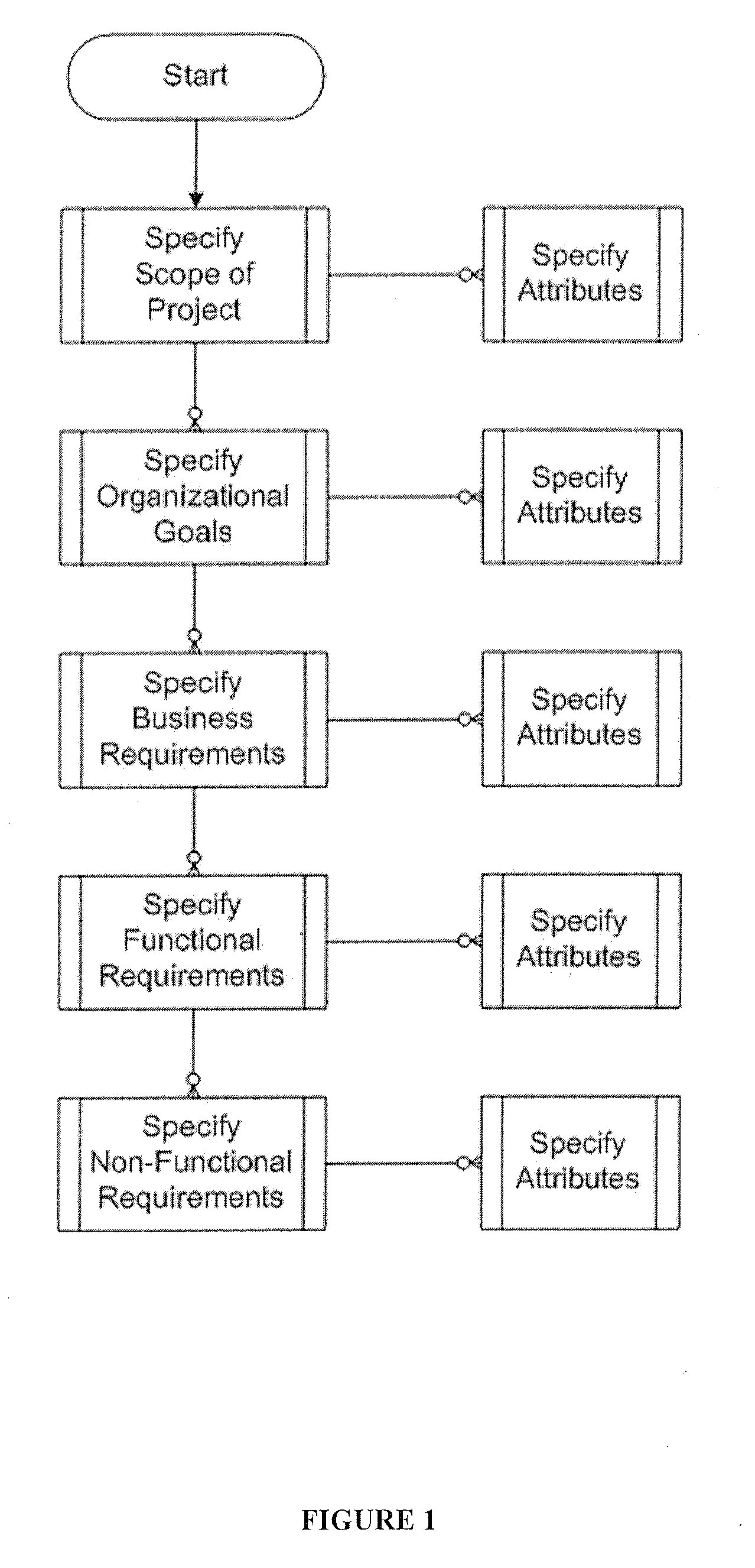
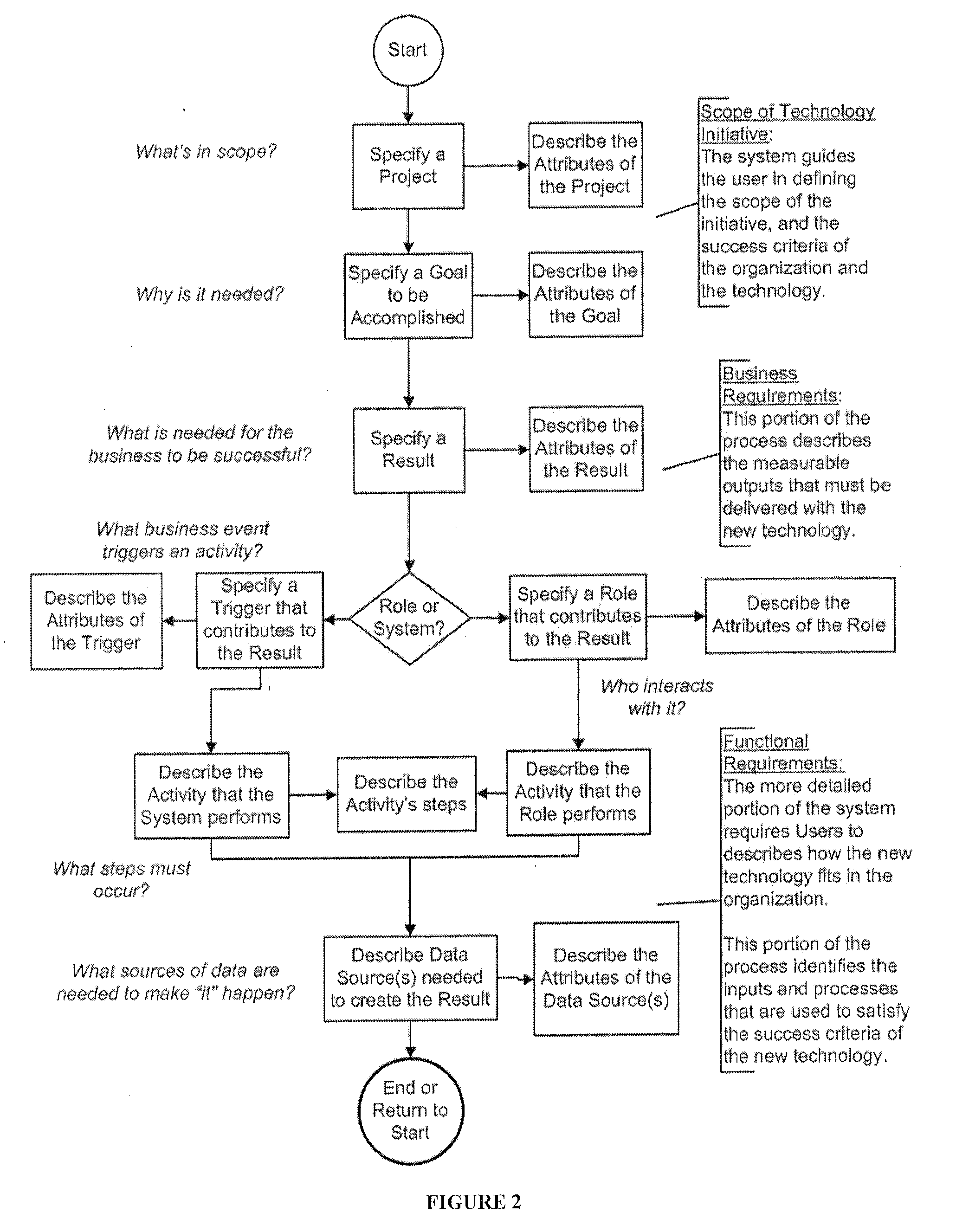
Requirements documents usually include user, system, and interface requirements; other classes of requirements are included as needed. User requirements are written from the point of view of end users, and are generally expressed in narrative form: The user must be able to change the color scheme of the welcome screen.
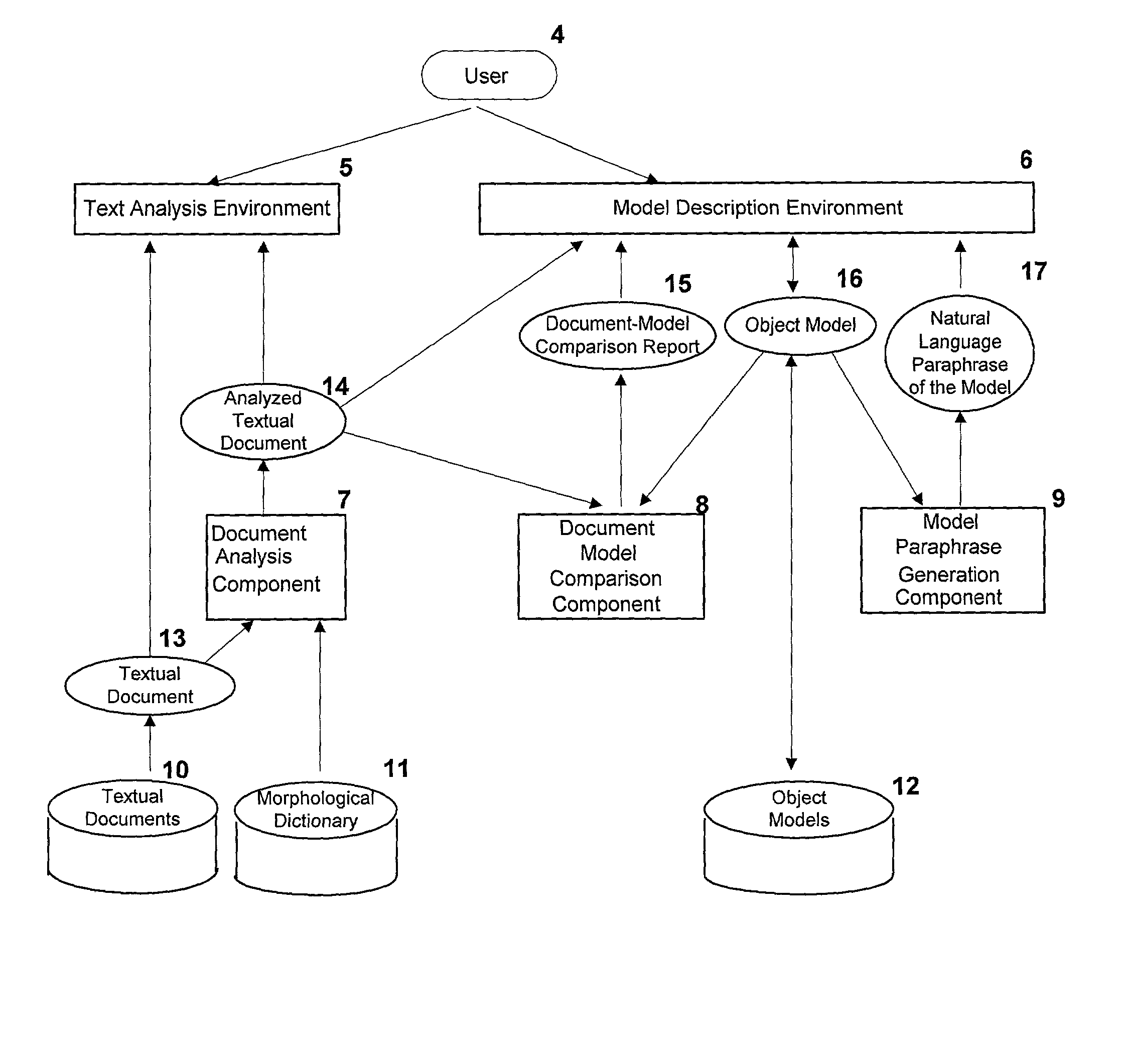
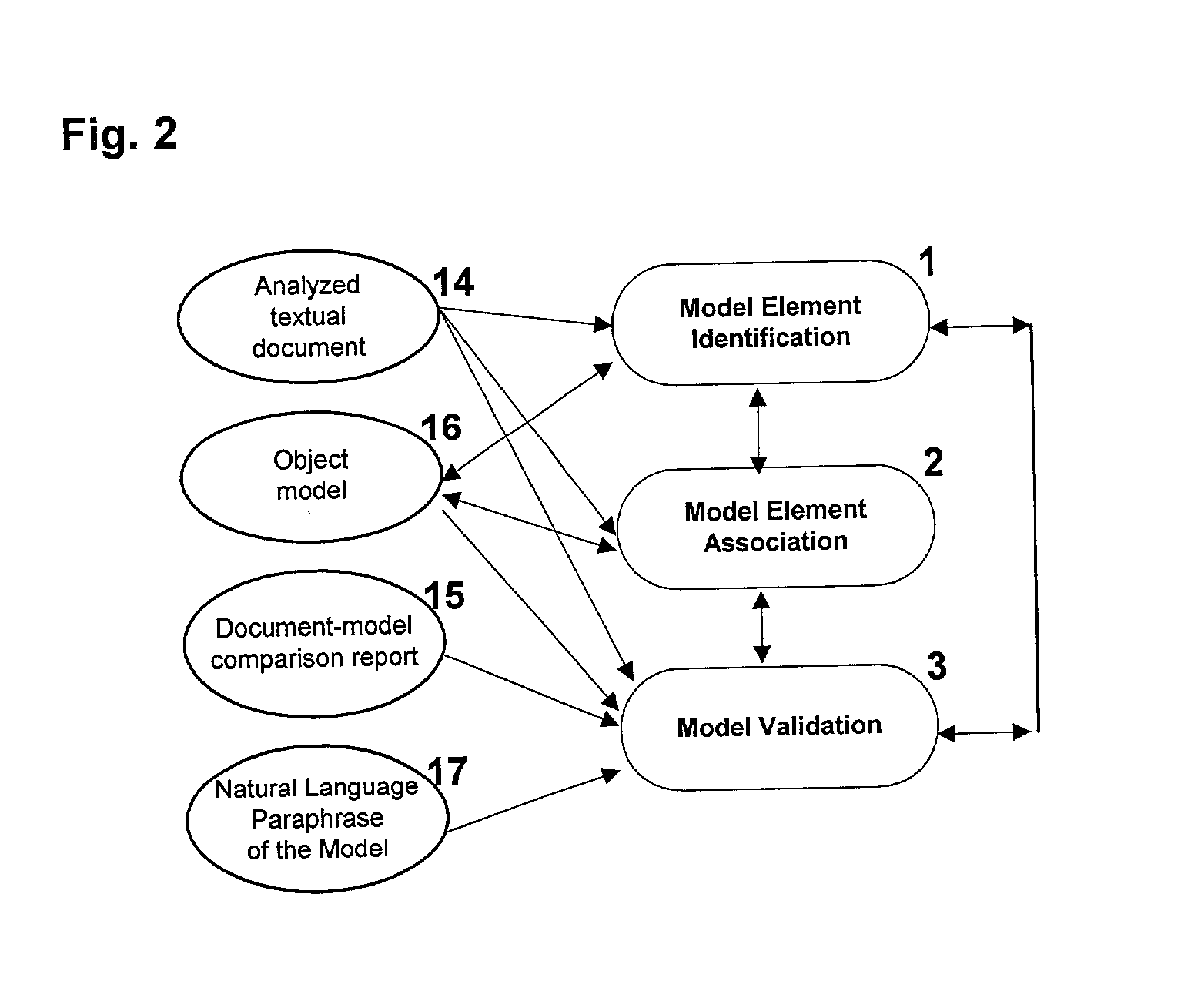
Linguistic assistant for domain analysis methodology
InactiveUS20030055625A1Semantic analysisSpecial data processing applicationsNatural language processingDomain analysis
A Linguistic Assistant For Domain Analysis Methodology to help a user define object models from documents such as requirements documents and validate object models against such documents. The approach is domain-independent and language-independent, mainly relying on widely available linguistic resources for the text analysis.
Owner:COGENTEX
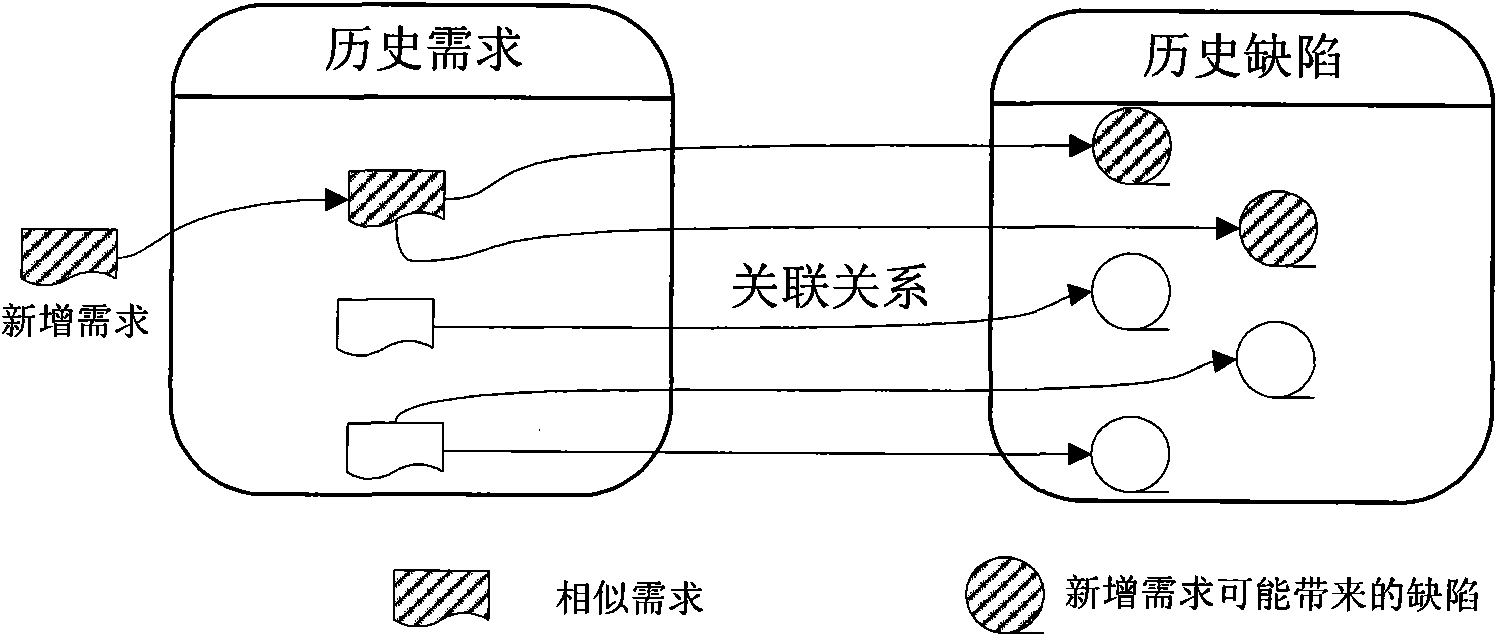
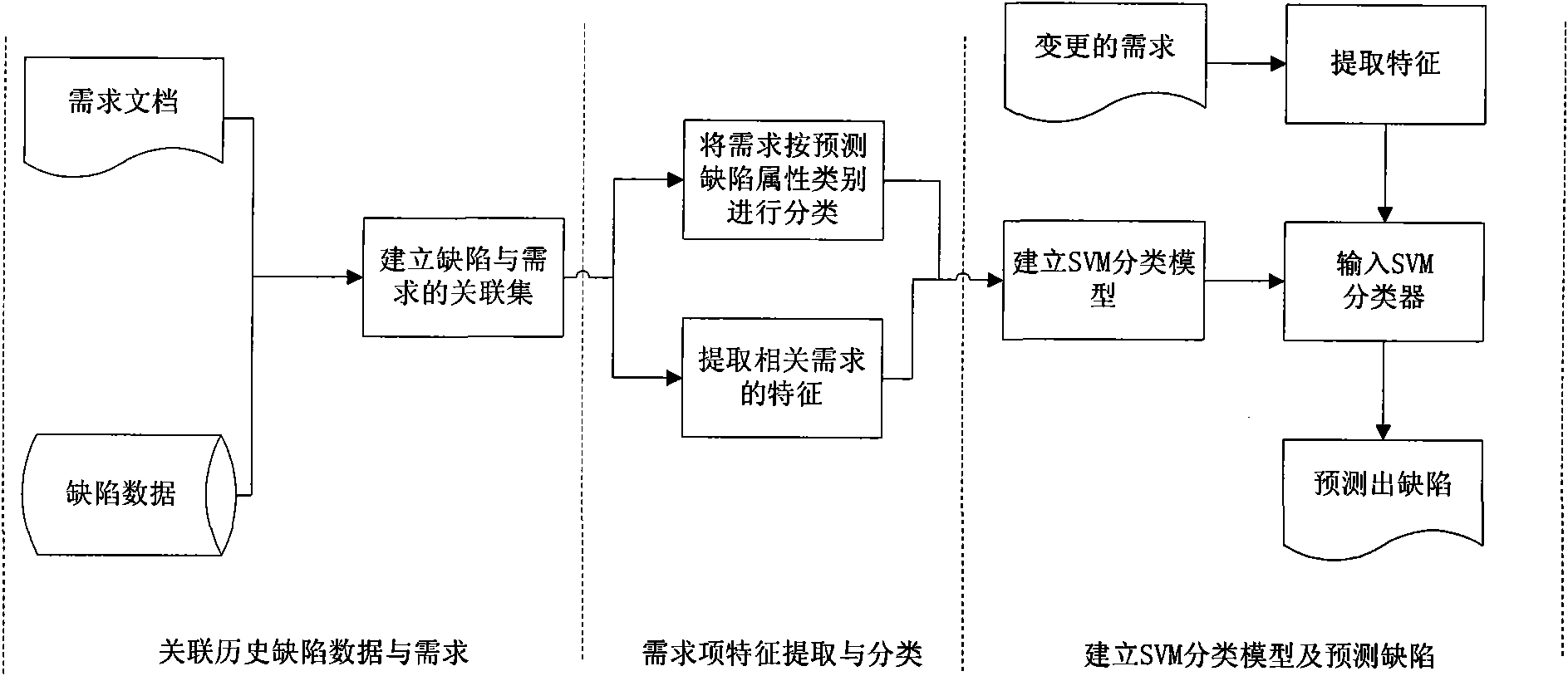
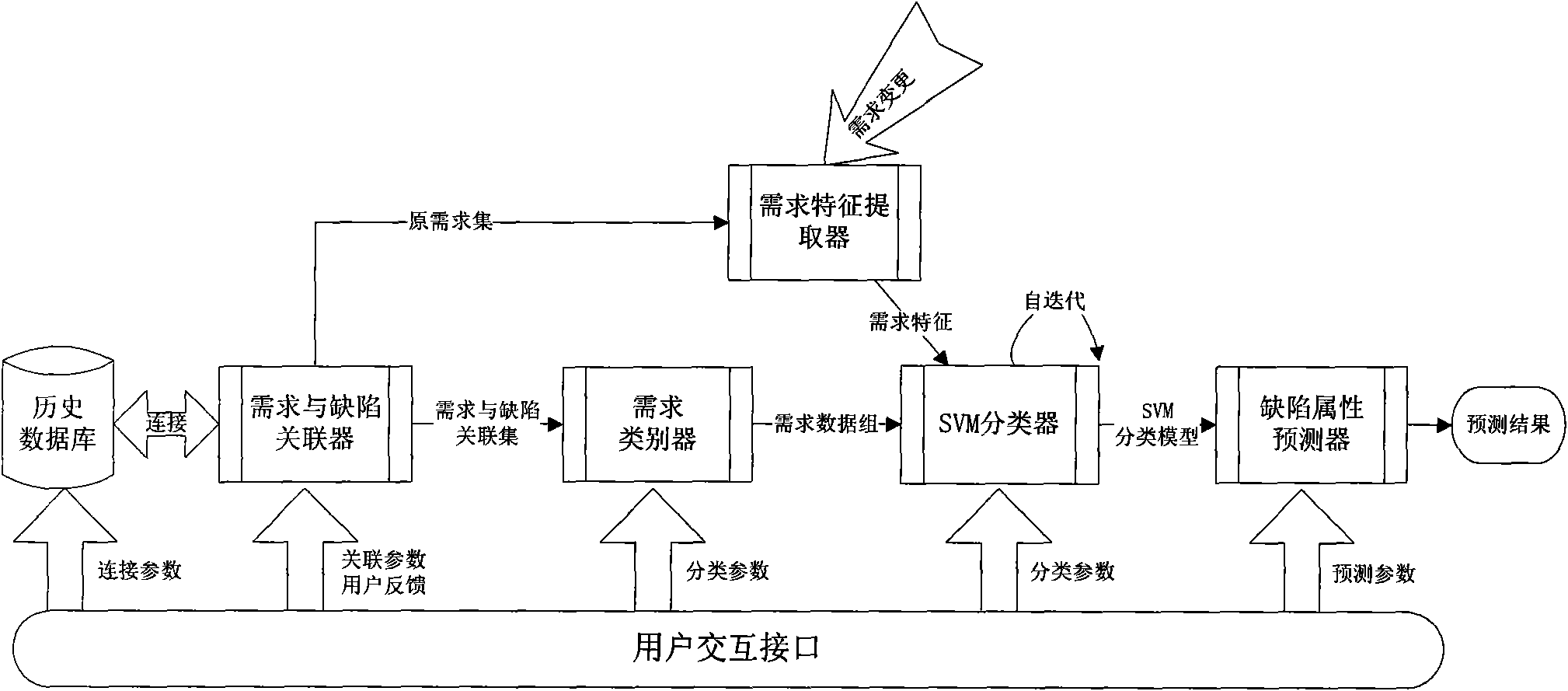
Defect prediction method and system based on requirement change
InactiveCN101556553AControlling the riskCost controlSoftware testing/debuggingSvm classifierDocumentation
The invention belongs to the computer security field and specifically relates to a defect prediction method and a system based on requirement change. The invention uses software project history defect data and a requirement document to construct a correlation set of requirements and defects, a requirement classifier classifies history requirements according to the correlated history defect attributive classification, calculates the requirement characteristic value of a requirement item and establishes an SVM classifier; when new requirement change occurs, a requirement characteristic extractor extracts the requirement characteristic of the requirement, and a defect attribute predictor finds the requirement classification to which the predictor is belonged in the SVM classifier according to the information of the requirement characteristic, consequently obtains the related defect attribute of the classification and completes the defect prediction. The invention can automatically add or delete the requirement characteristic classification to be extracted and modify the weights of these characteristics in a classification model so as to lead the obtained prediction model to be more accurate and improve the prediction accuracy. The system can automatically complete prediction with directviewing prediction result.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
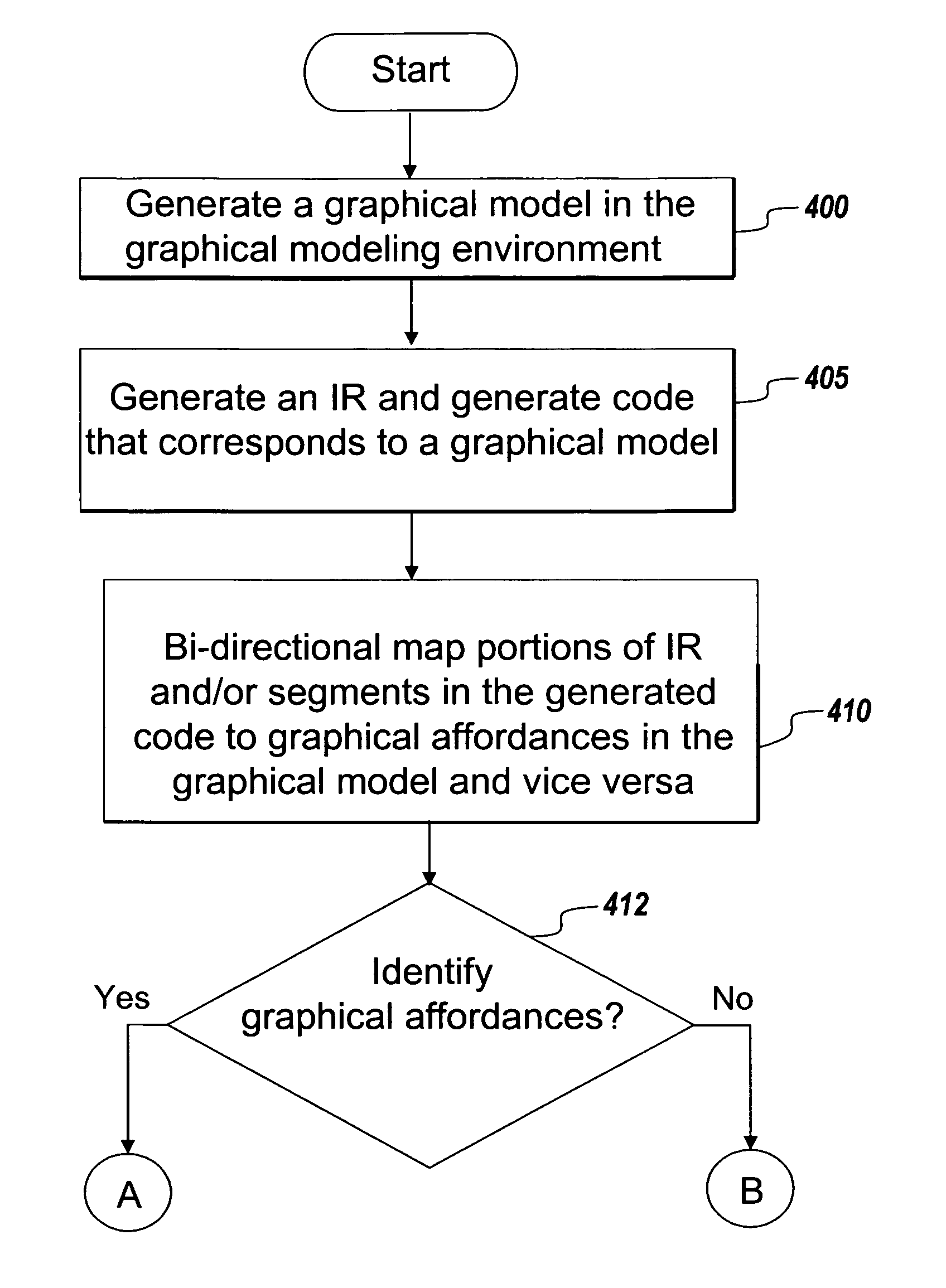
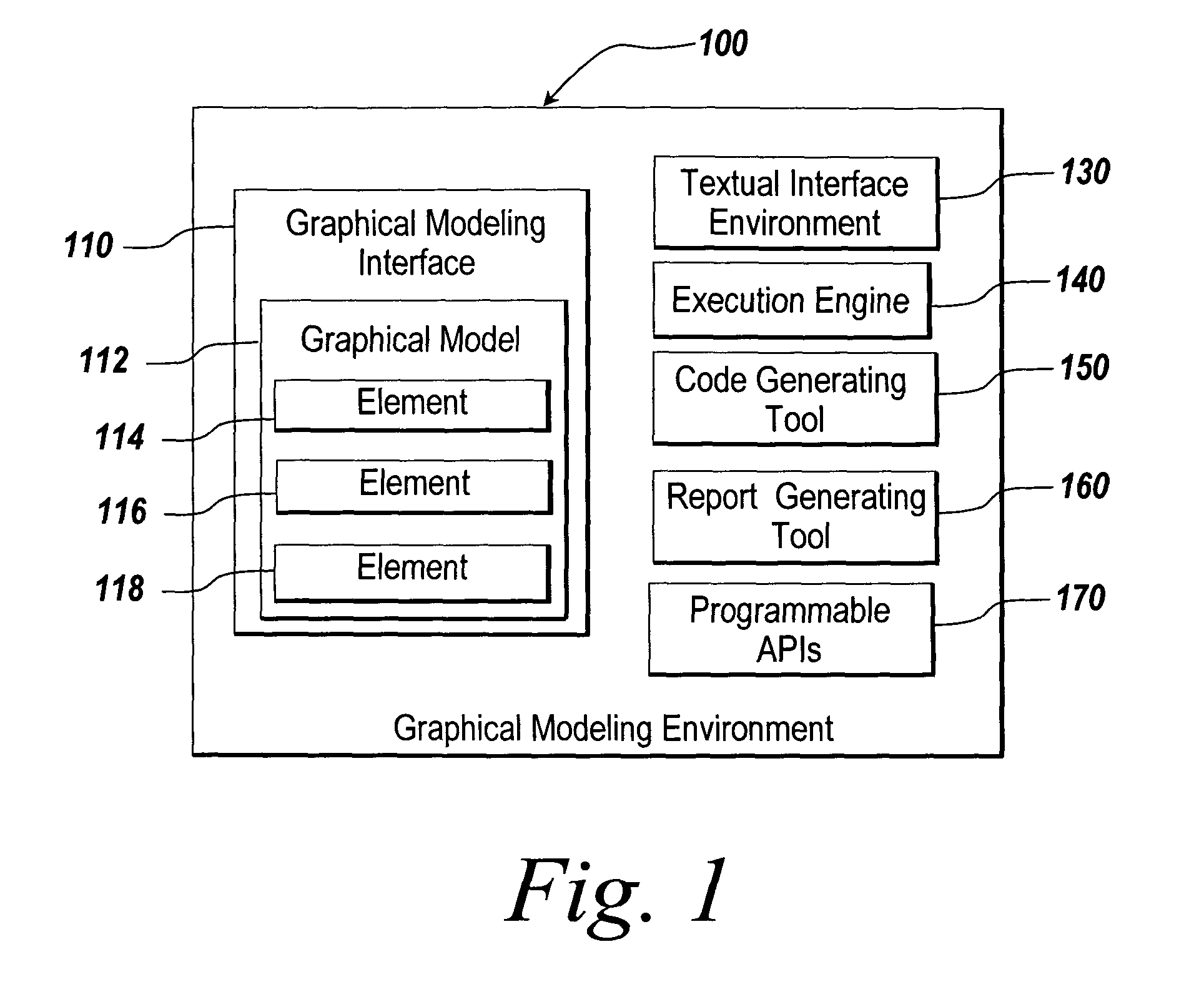
Traceability in a modeling environment
ActiveUS8104017B2Facilitate graphical identificationError detection/correctionProgram documentationGraphicsDocumentation procedure
Exemplary embodiments employ a mapping among entities that are related to each other. The entities may include a graphical model, generated code, a generated report, a requirements document and / or an intermediate representation. The mapping may facilitate graphical identifications between parts of one entity that maps to part of another entity. The graphical identification may occur based on a selection of a part in one of the entities.
Owner:THE MATHWORKS INC
Method, device and system for testing ECU (Electronic Control Unit)
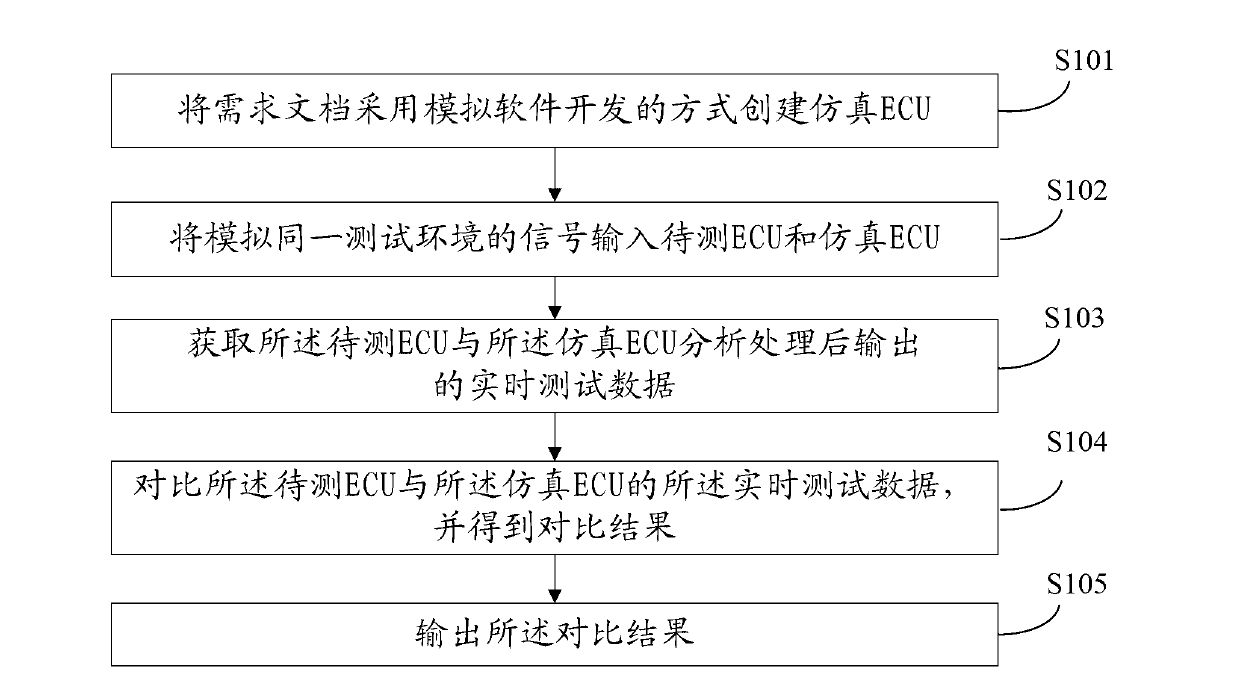
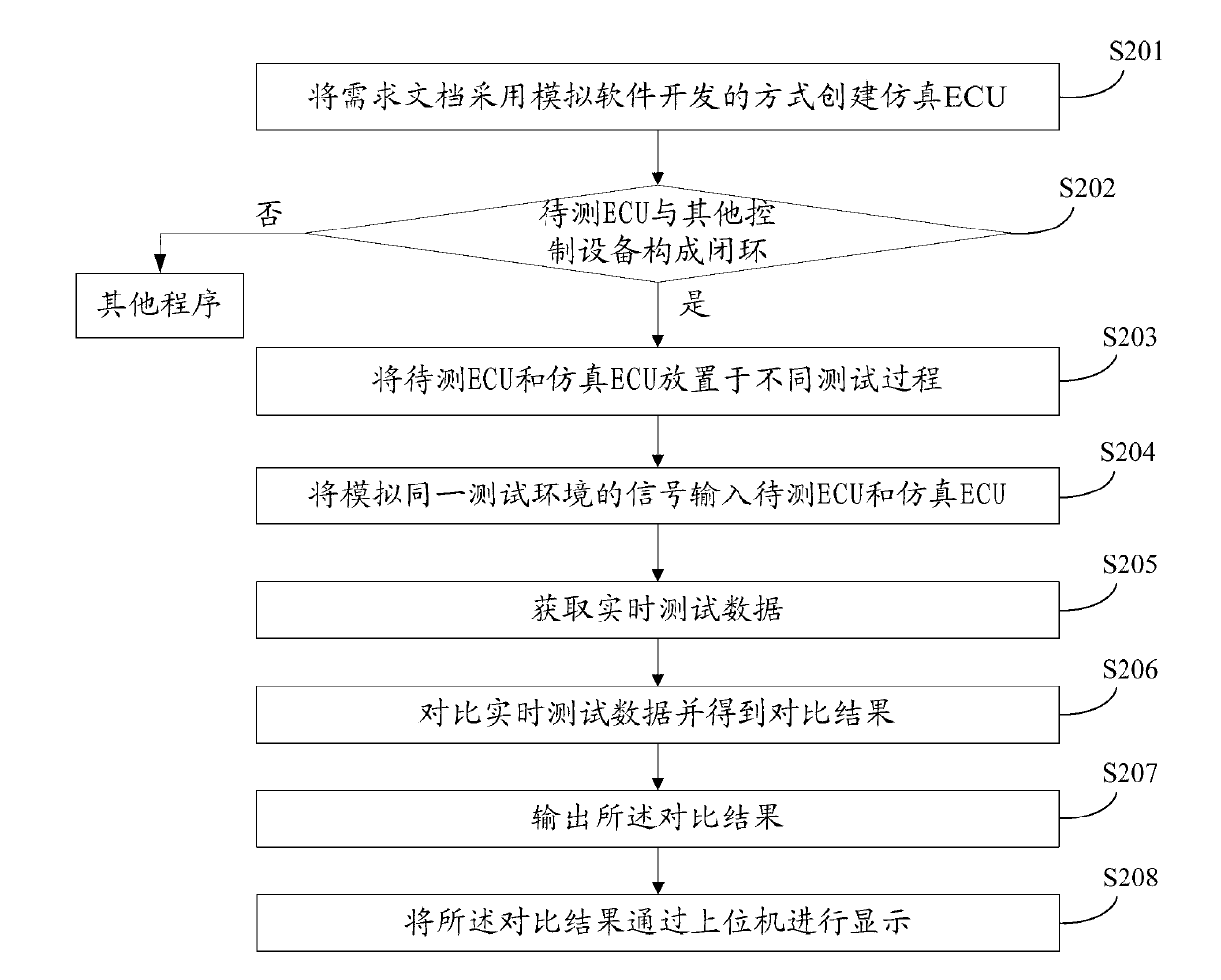
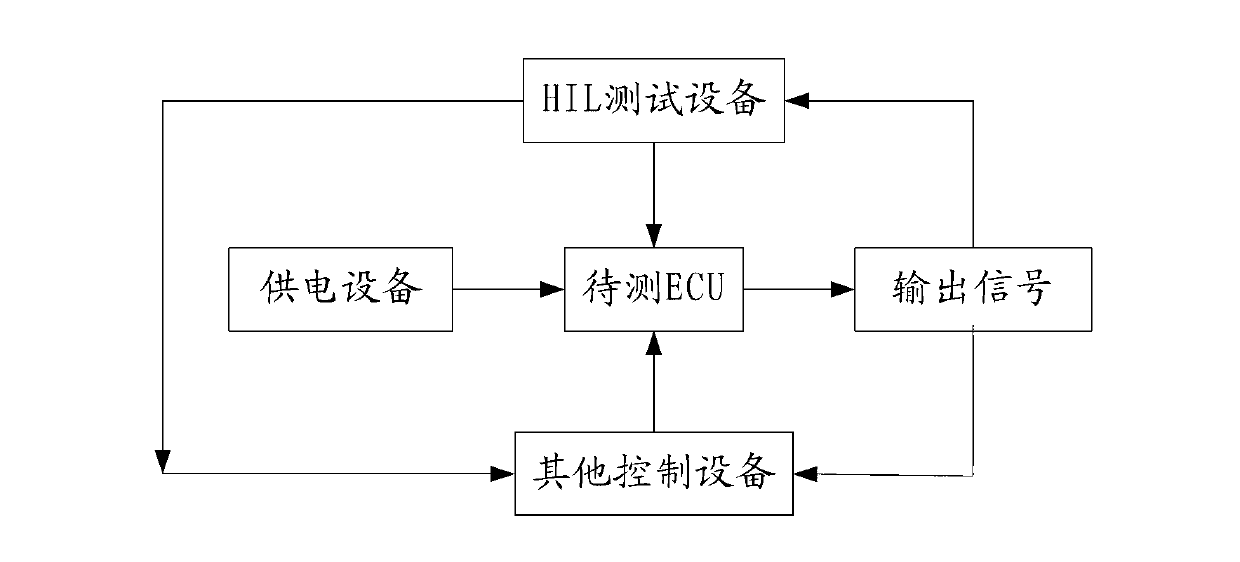
ActiveCN103020401ASolve the problem that the workload is heavy and it is difficult to obtain the results of the HIL testSpecial data processing applicationsProcess integrationSimulation
The invention discloses a method for testing a to-be-tested ECU, which is used for HIL (Hardware In the Loop) testing equipment. The invention further provides a device for testing the ECU and a system for testing the ECU. A tester integrates a large amount of analytical calculation processes carried out on requirement documents into a simulated ECU through adopting a simulation software method, signals for simulating the same testing environment are input to the simulated ECU and to-be-tested ECU to obtain real-time testing data output by the to-be-tested ECU and the simulated ECU, and real-time testing data output by the to-be-tested ECU and the simulated ECU is compared to obtain the final comparison result. The tester is prevented from carrying out a large amount of analytical calculations on data from the input condition to the requirement result in the requirement documents, and the problems that the workload in HIL test of the tester is large and of the HIL test result is difficult to obtain are solved.
Owner:BEIJING JINGWEI HIRAIN TECH CO INC
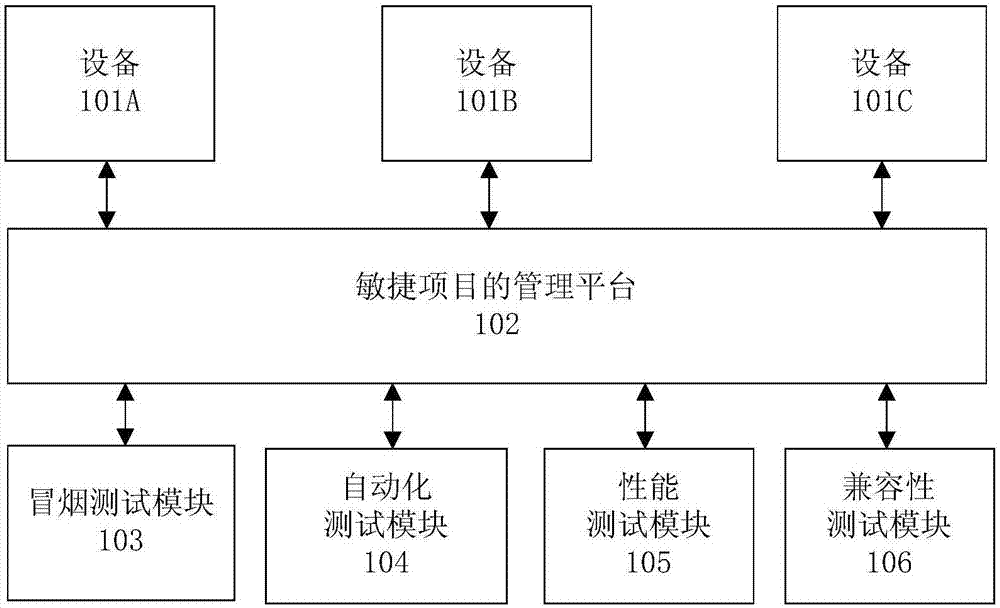
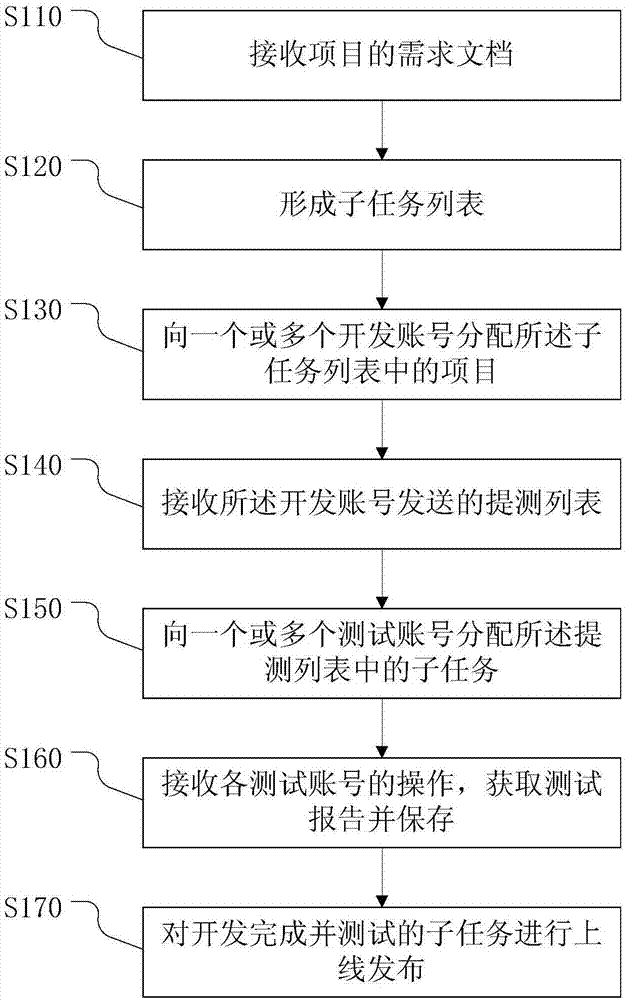
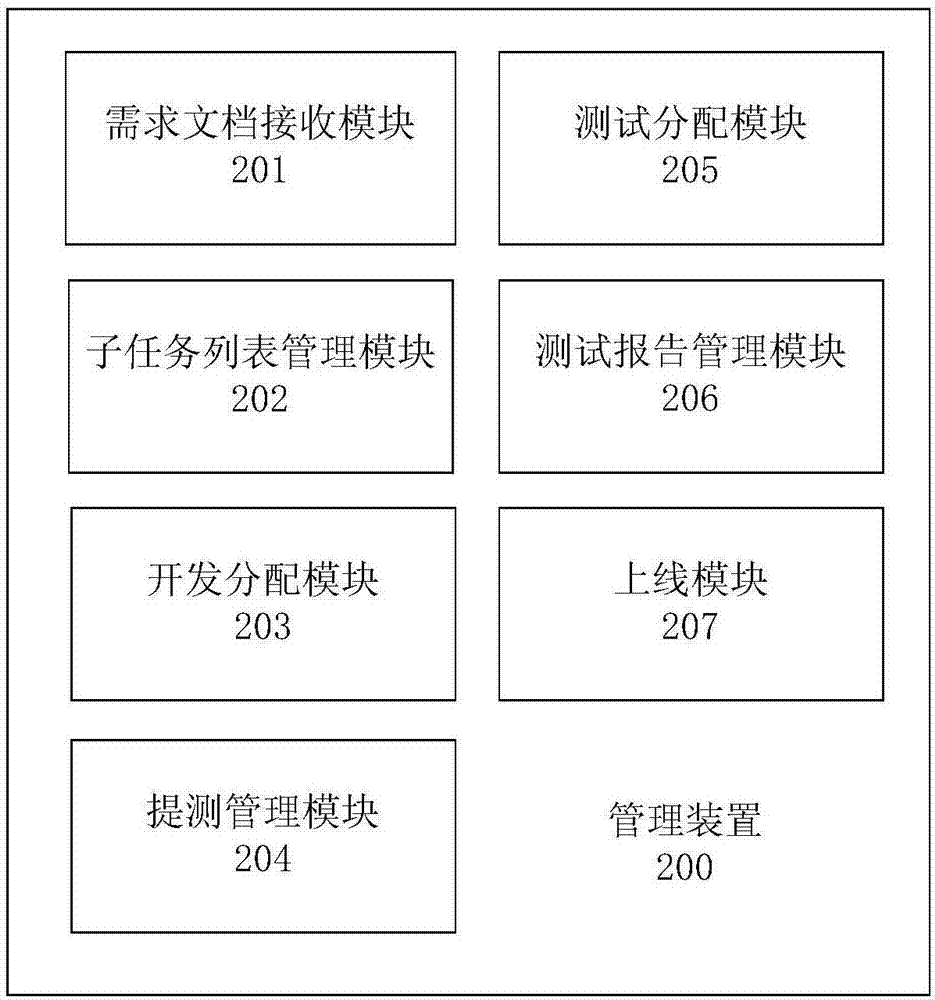
Agile project management method, device and system, electronic equipment and storage medium
ActiveCN107516192AFunction increaseImprove work efficiencySoftware testing/debuggingOffice automationProject managementDocumentation
The invention provides an agile project management method, device and system, electronic equipment and a storage medium. The management method includes: receiving a requirement document of project; splitting the project into multiple subtasks according to the requirement document to form a subtask list; according to the number of currently-uncompleted subtasks of development accounts and the scheduled releasing date of the uncompleted tasks, assigning the subtasks in the subtask list to one development account or more; receiving a test mentioning list sent by the development accounts; according to the number of the currently-untested subtasks of test accounts and scheduled releasing date of the untested subtasks, assigning the subtasks in the test mentioning list to one test account or more; receiving operations of the test accounts and acquiring one test report or more from the subtasks in the test mentioning list; releasing the subtasks completed in development and tested on line. With the method and device, integral management of the agile project is achieved.
Owner:携程旅游信息技术(上海)有限公司
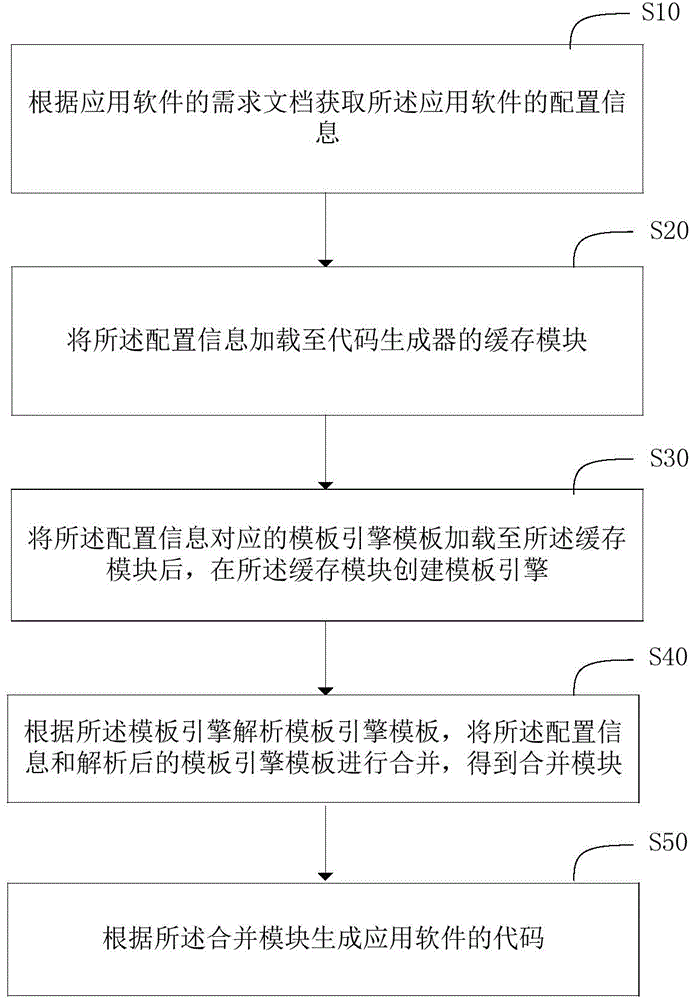
Code generation method and system of application software
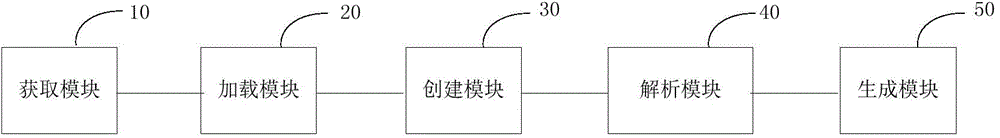
InactiveCN104965714AImprove production efficiencyRealize automatic generationSpecific program execution arrangementsComputer moduleSoftware development
The invention relates to a code generation method and a system of application software. The code generation method of the above application software comprises following steps: acquiring configuration information on the application software based on the requirement document; loading the above configuration information to a buffer module; loading a template engine template corresponding to the configuration information to the buffer module and creating a template engine at the buffer module; analyzing the template engine template according to the template engine and merge the configuration information with the analyzed template engine template in order to obtain a merge module; and generating codes of the application software according to the merge module. The code generation method and the system of application software have following beneficial effects: repeated editing and rectifying operation is unnecessarily performed by a software developer in order to achieve automatic generation of codes of the application software and to effectively increase generation efficiency of codes of the application software.
Owner:GCI SCI & TECH
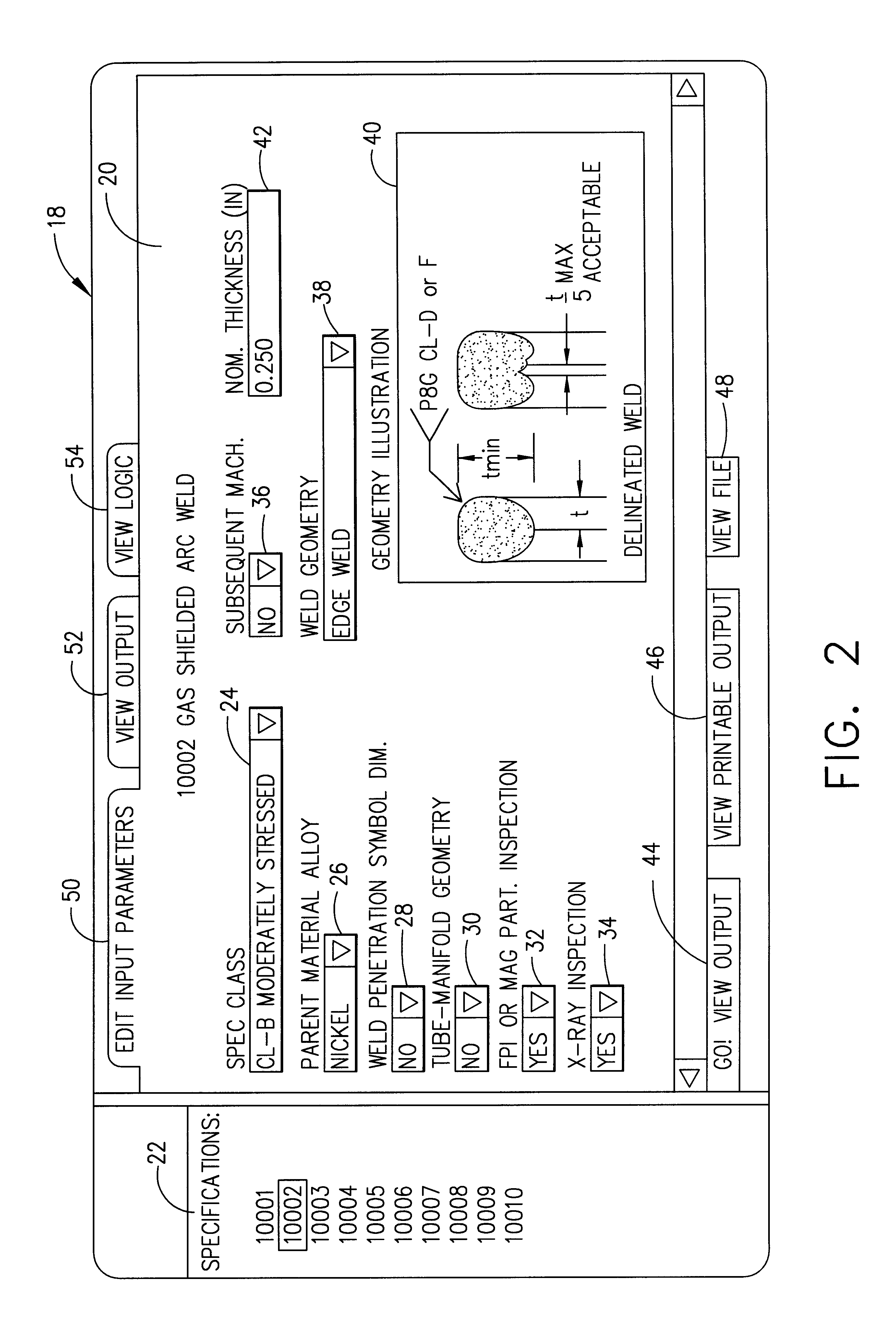
System and method for determining specific requirements from general requirements documents
A system and method of using at least one computer to determine which requirements from a general requirements document apply to a specific situation. The invention includes providing a logic model for the general requirements document and receiving data relating to the specific situation. The collected data and the logic model are used to identify which requirements apply to the specific situation. Lastly, a listing of the identified requirements is output.
Owner:GENERAL ELECTRIC CO
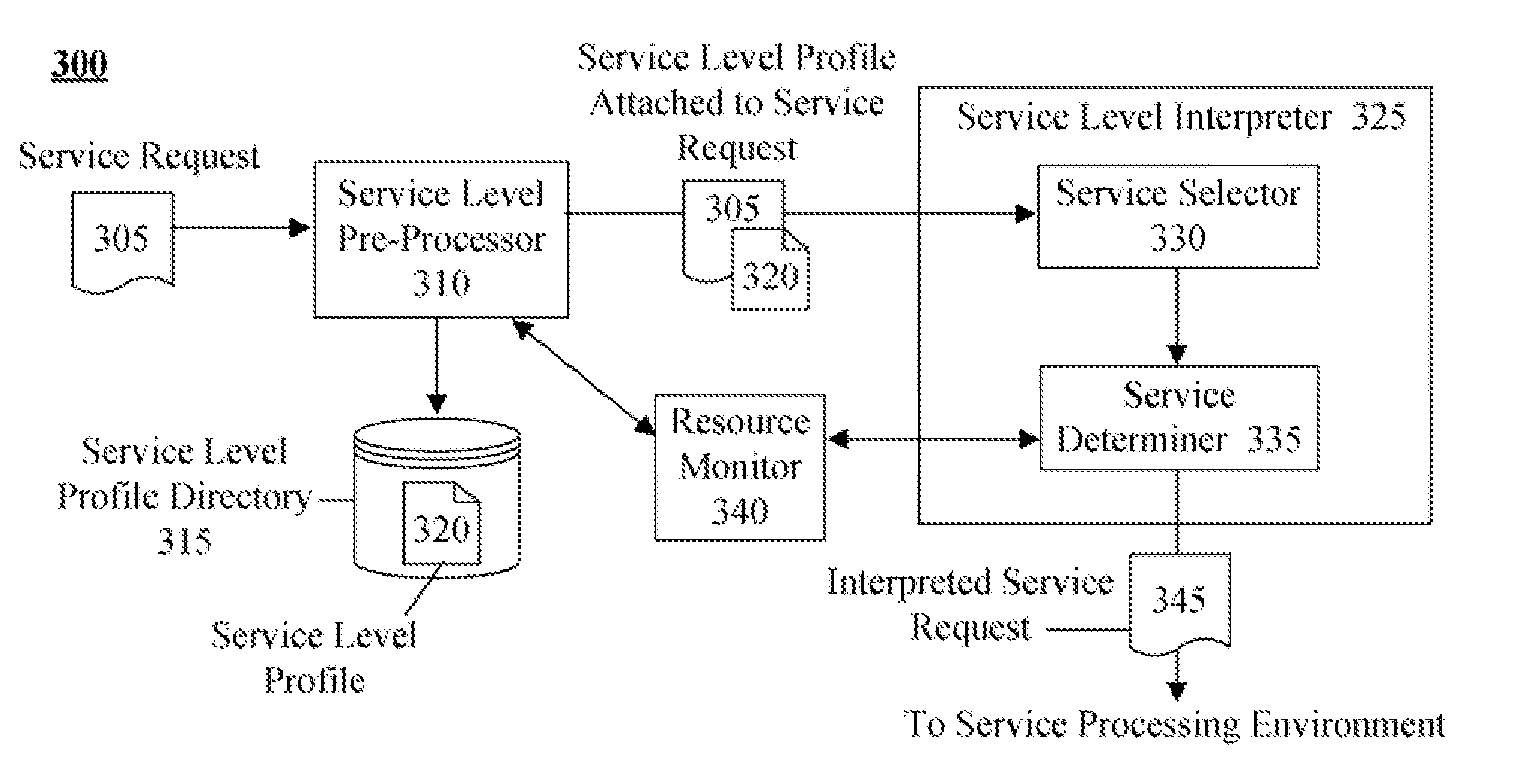
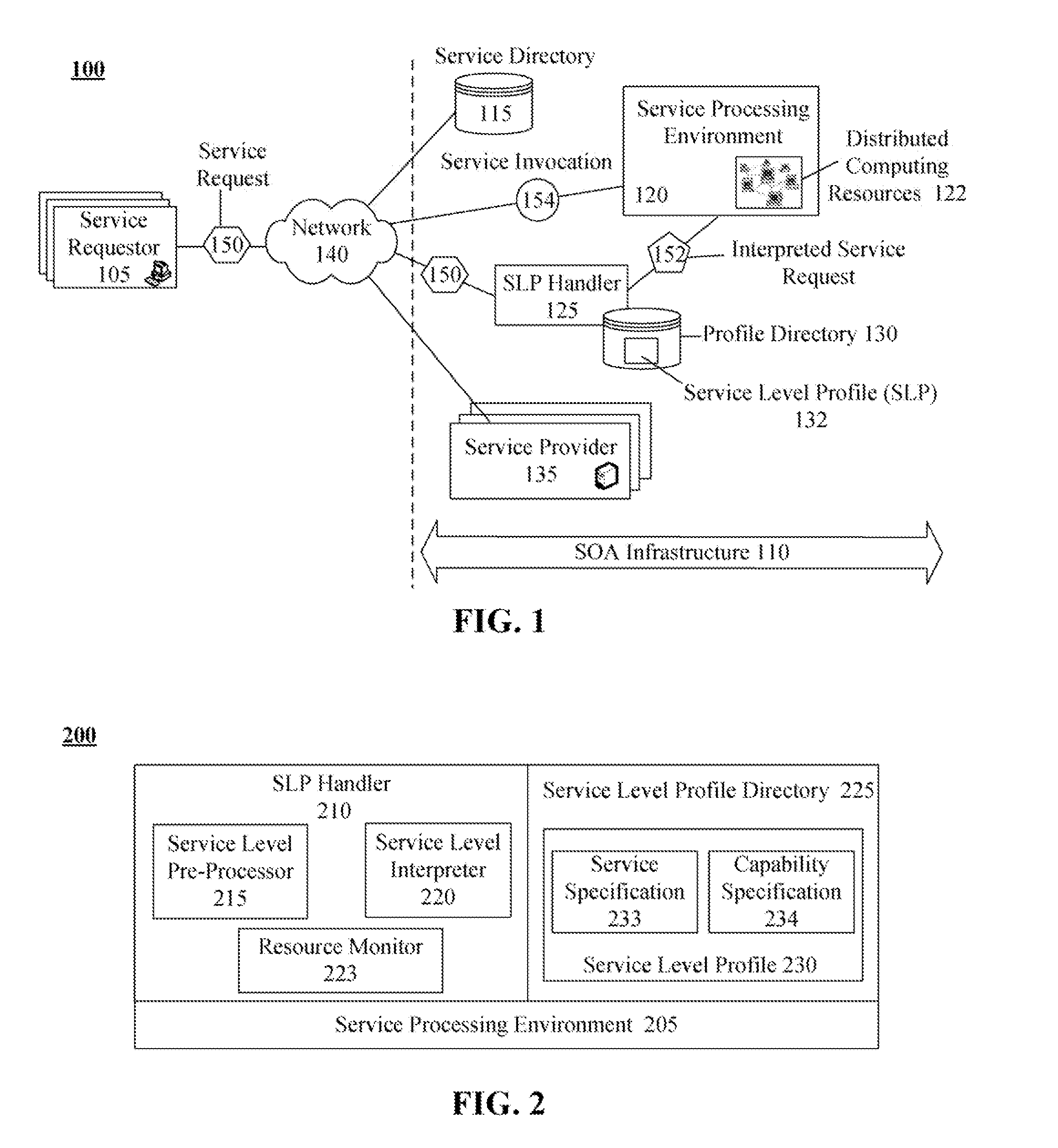
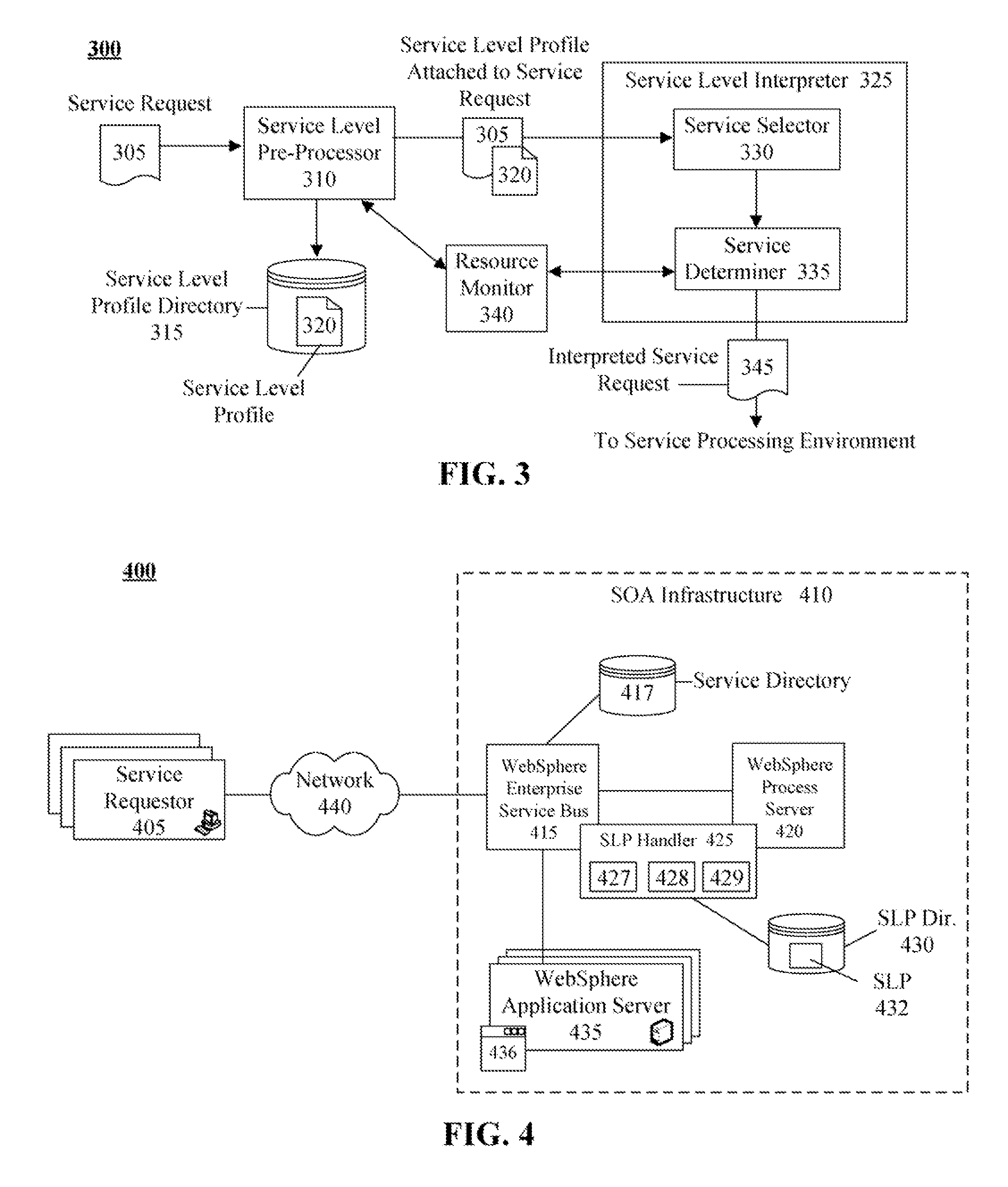
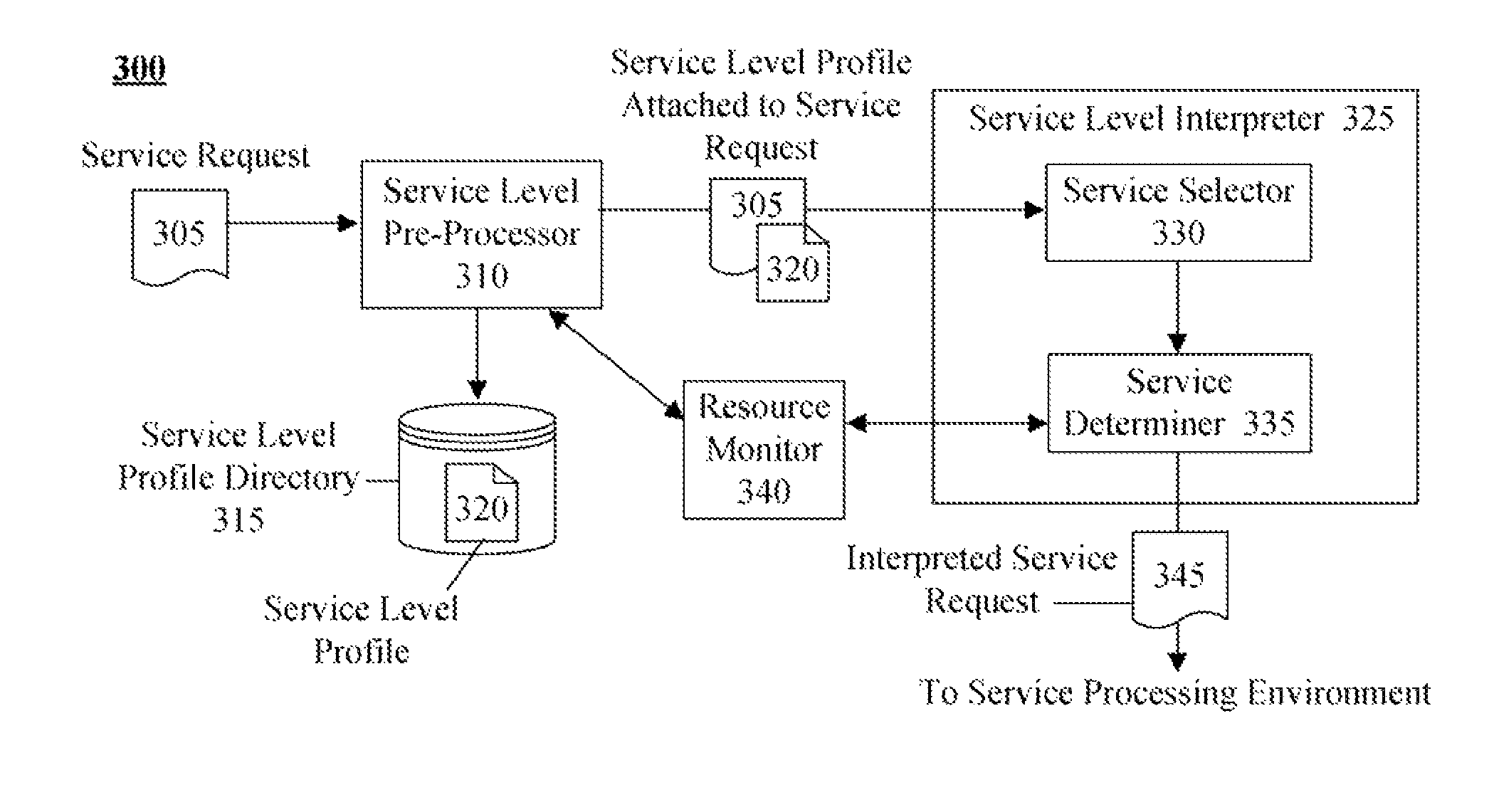
Technique for defining and dynamically enabling service level requirements in a service oriented architecture
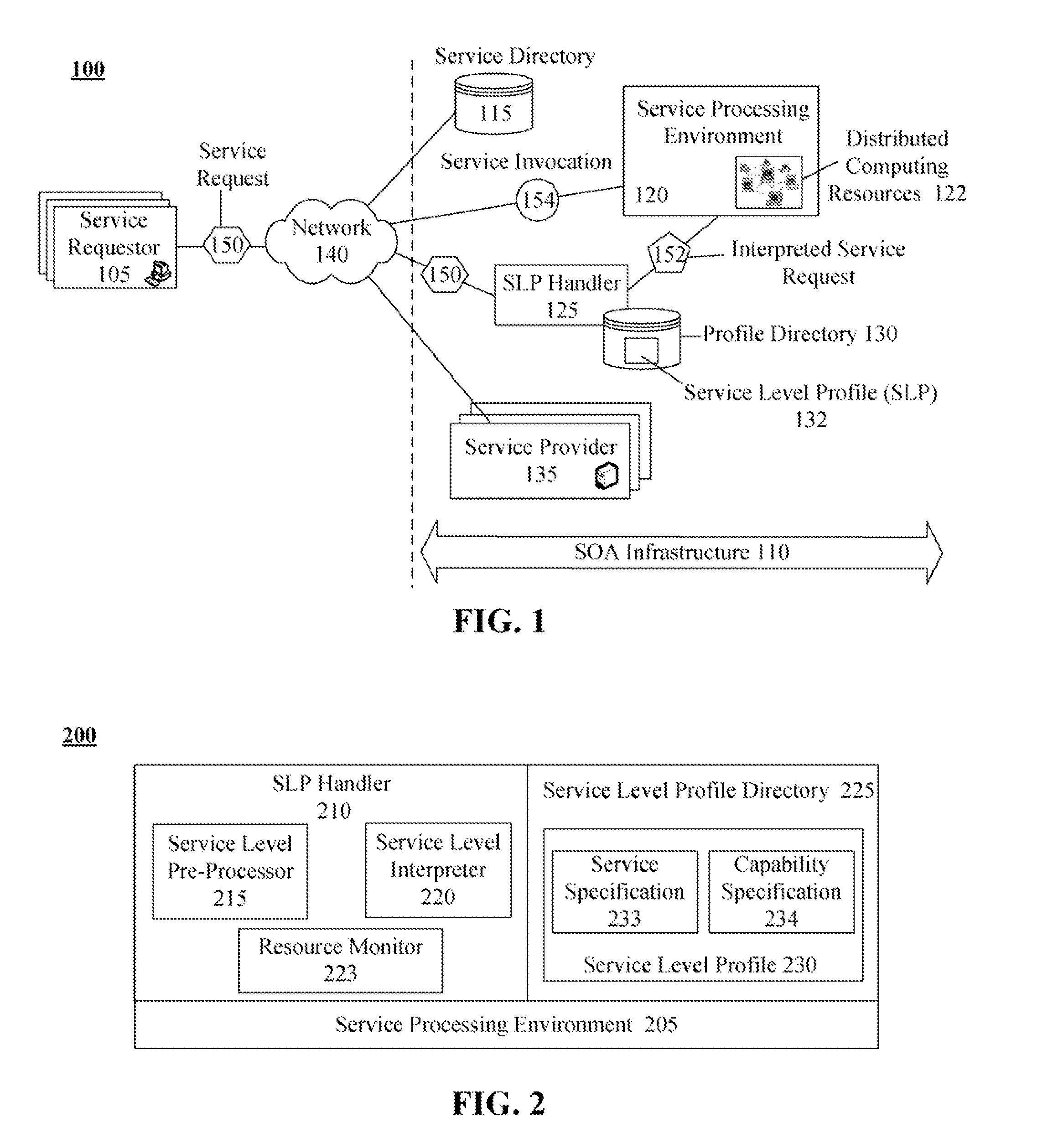
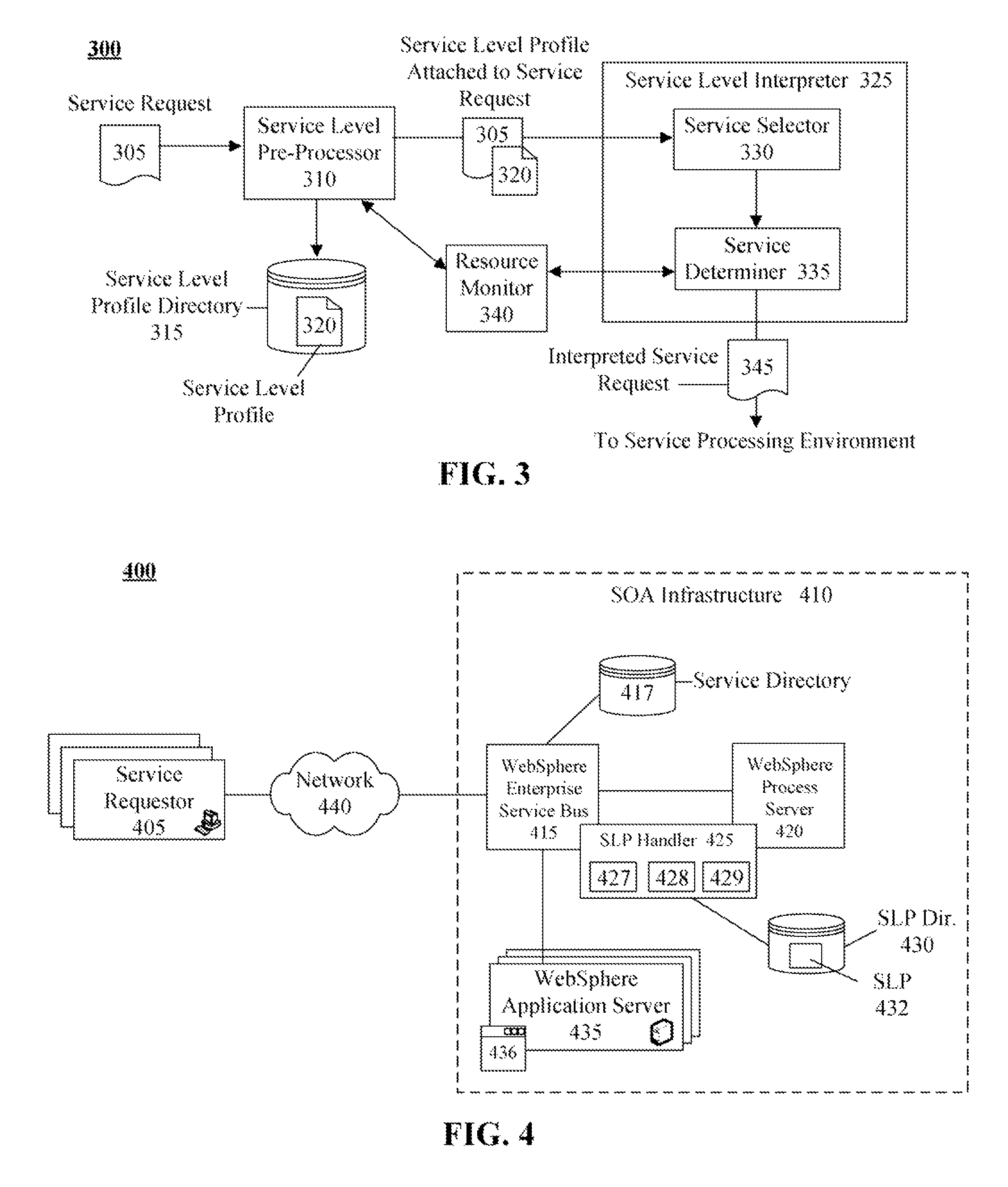
InactiveUS20080285481A1Error preventionTransmission systemsService-level agreementService level requirement
The present invention discloses a document for formally defining service level requirements in a service oriented architecture (SOA). This document can include a service specification that defines functional attributes and a capability specification that defines performance requirements. These functional attributes and performance requirements can influence the response of the SOA to a service request. For example, a dynamic interpreter of the requirements document can dynamically adjust SOA resources to ensure performance requirements specified in the requirements document are met.
Owner:LINKEDIN
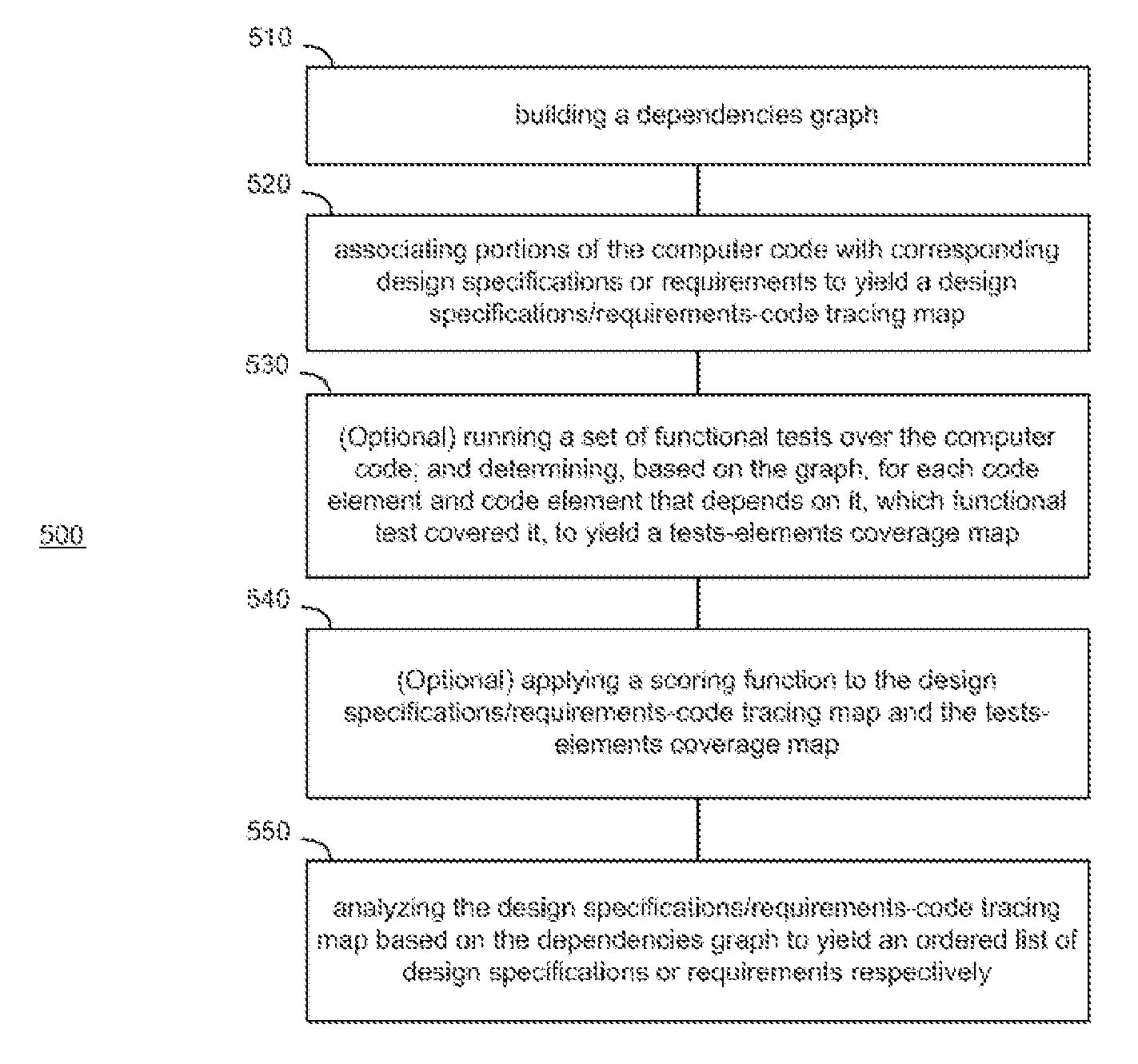
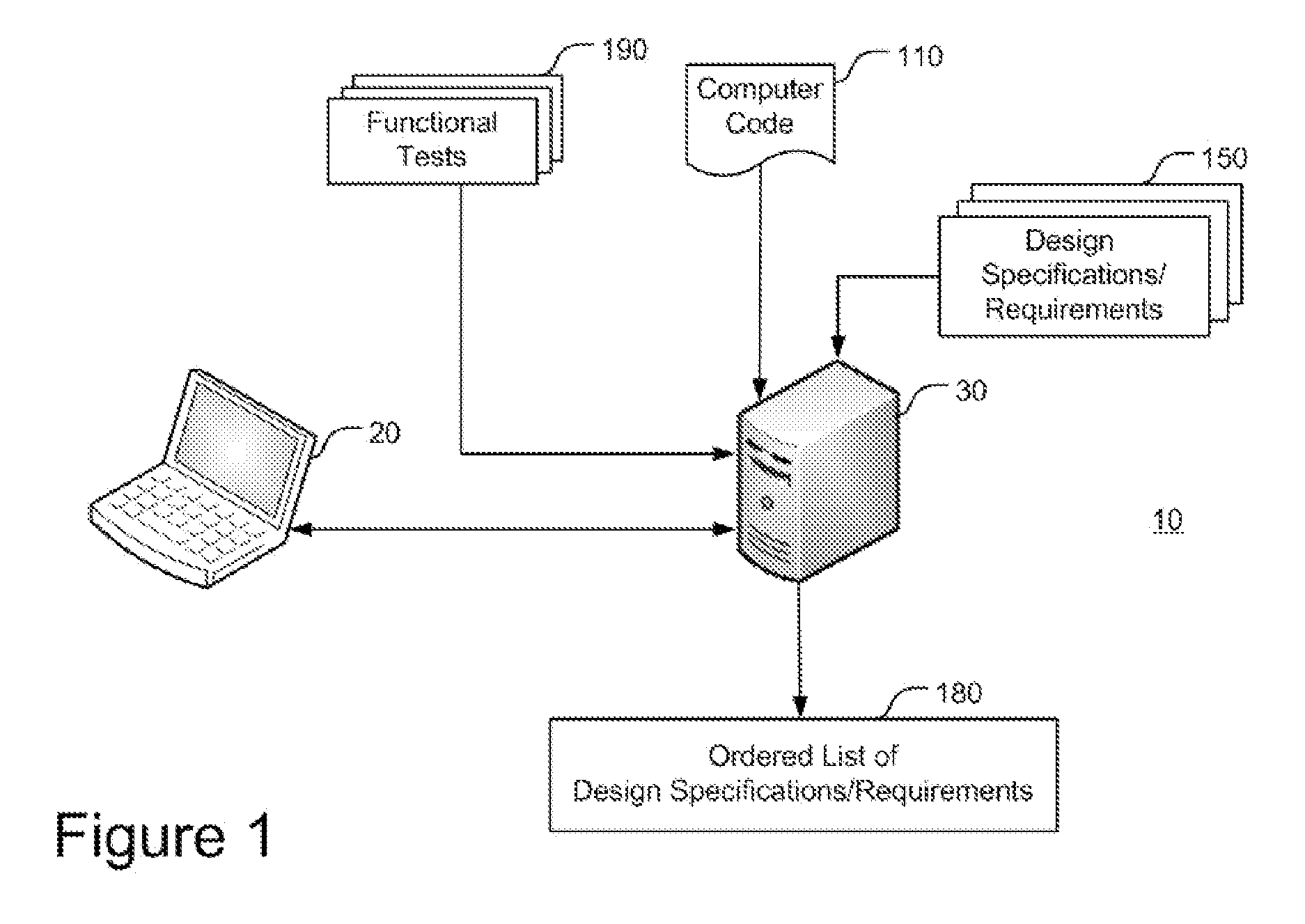
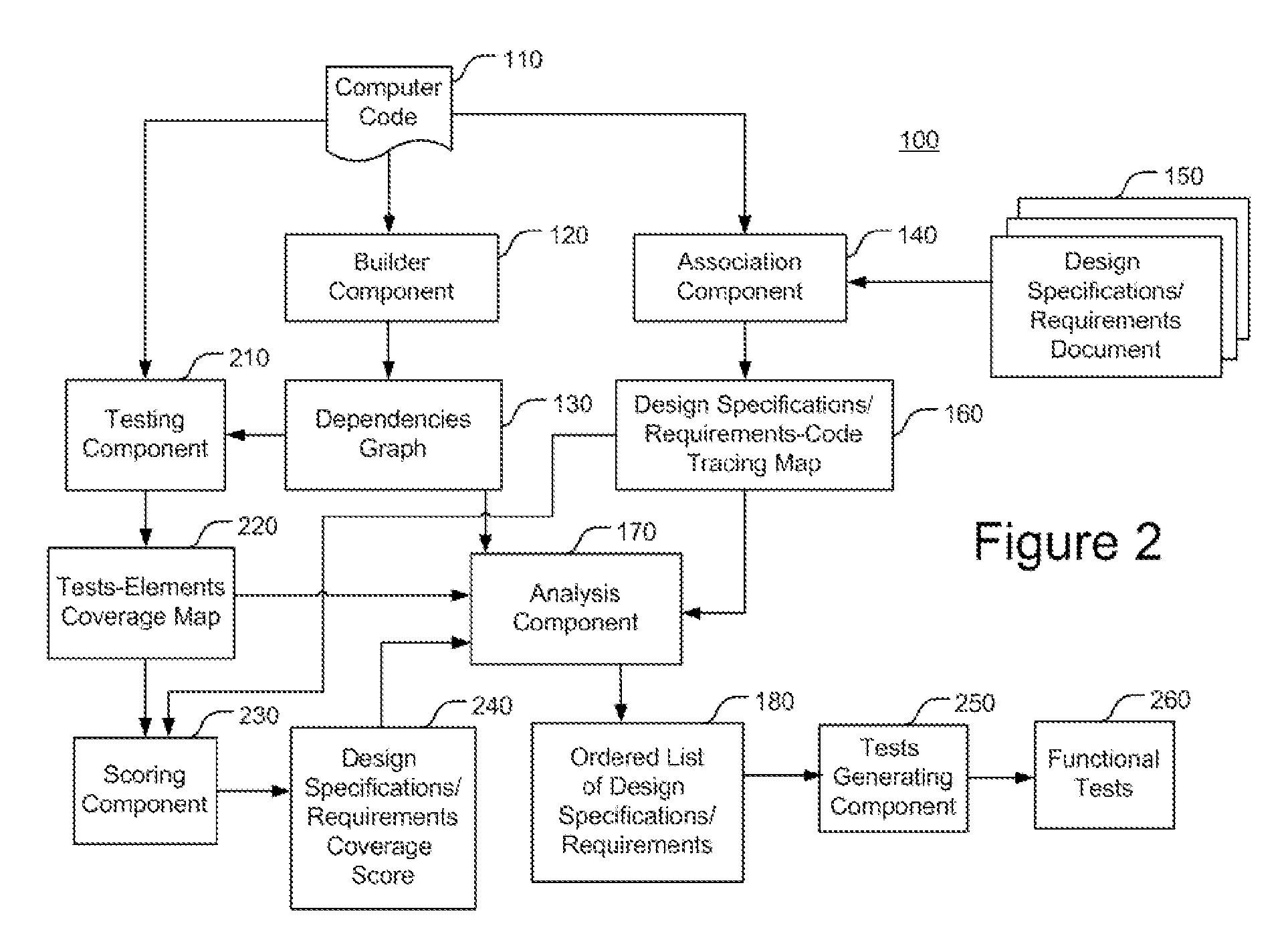
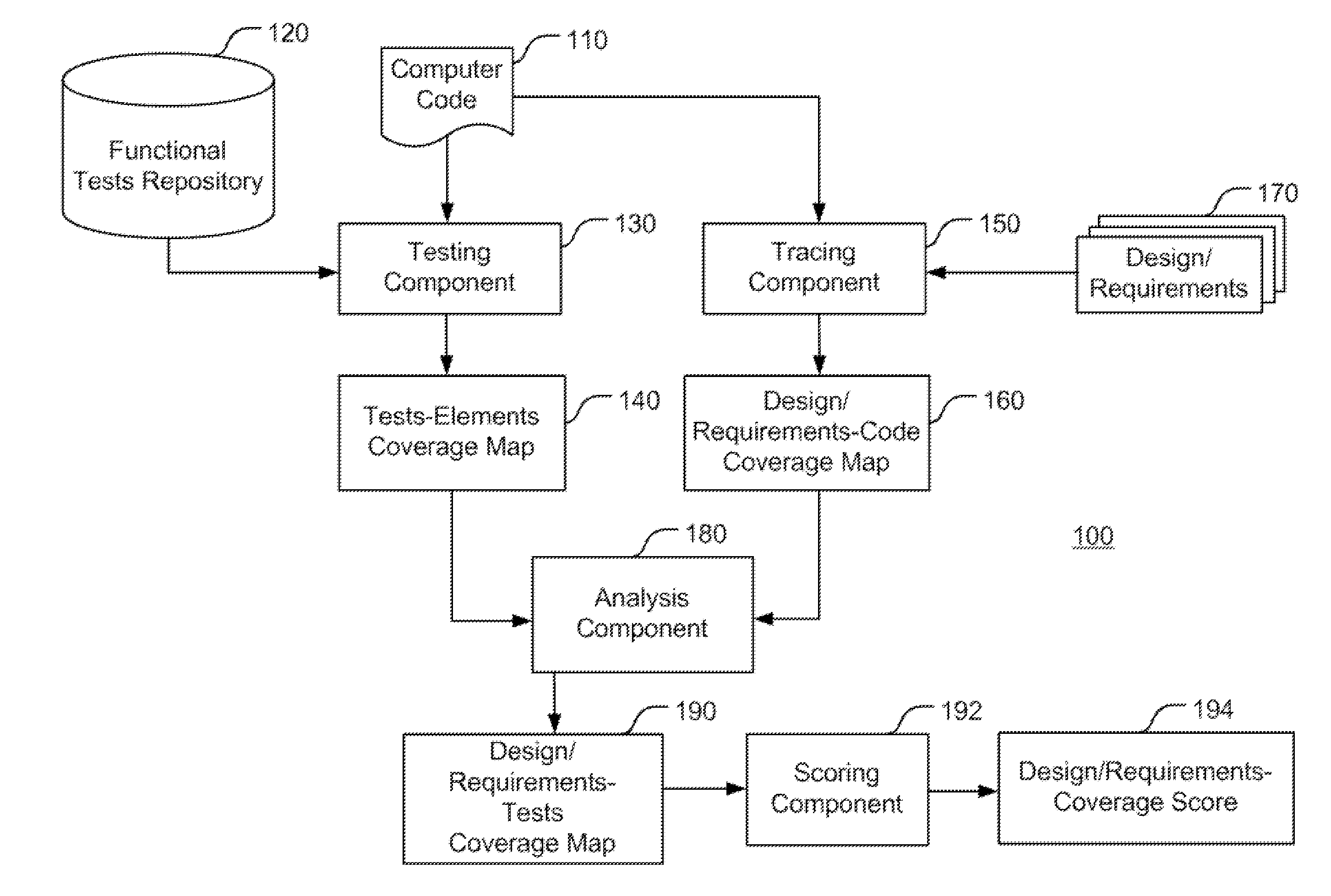
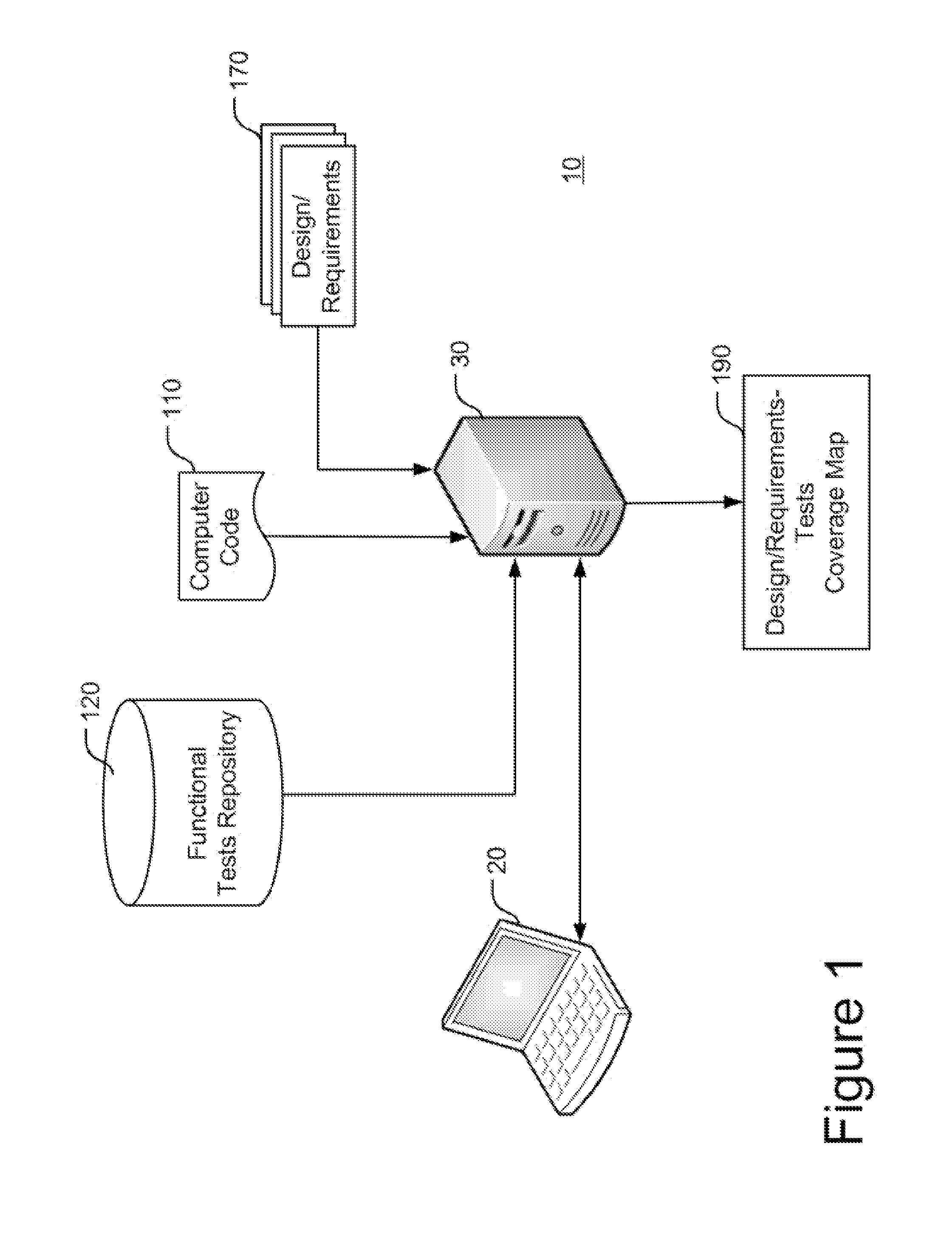
Enhancing functional tests coverage using traceability and static analysis
InactiveUS20110271253A1High level of functionImprove code coverageError detection/correctionProgram documentationStatic timing analysisCode writing
A method that may include: building a dependencies graph representing dependencies between code elements of a computer code; associating portions of the computer code with corresponding design specifications or requirements derived from a design specifications document or a requirements document respectively which is associated with the computer code, to yield a design specifications or requirements-code tracing map; and analyzing the design specifications or requirements-code tracing map based on the dependencies graph to yield an ordered list of design specifications or requirements respectively, wherein the order is selected such that functional tests written for the computer code and addressing design specifications or requirements of a higher order, will yield a higher level of functional test coverage of the computer code in terms of design specifications or requirements.
Owner:IBM CORP
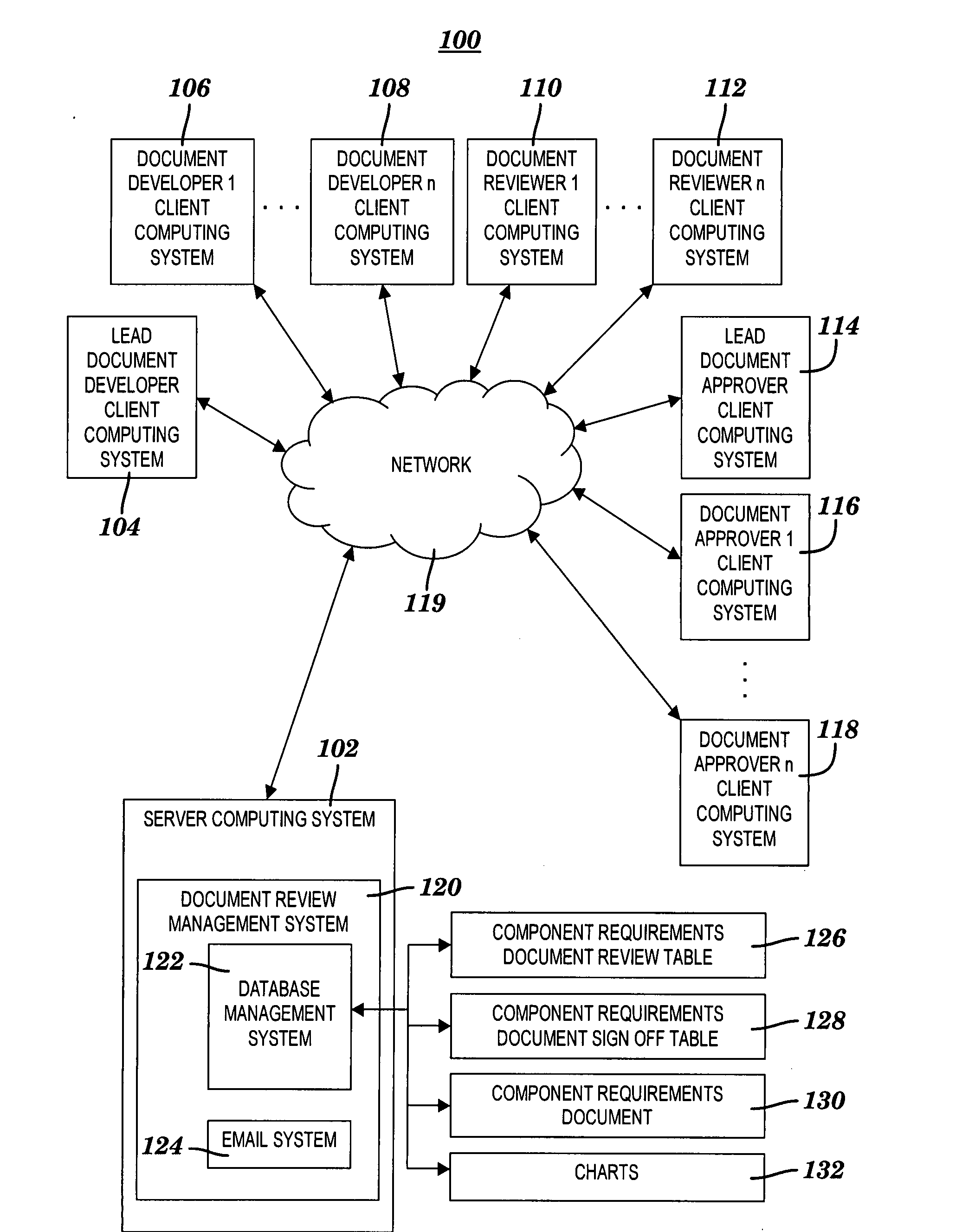
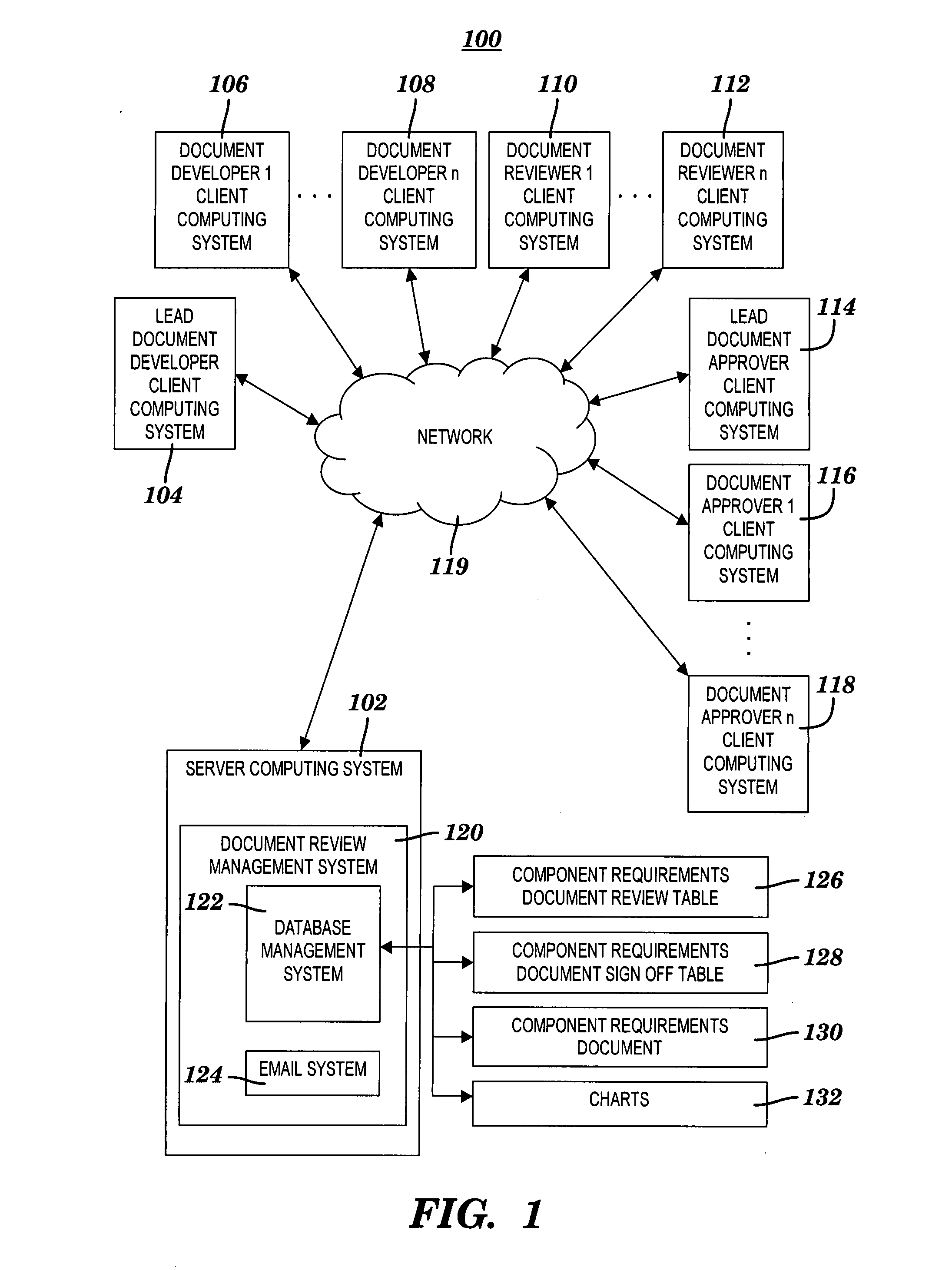
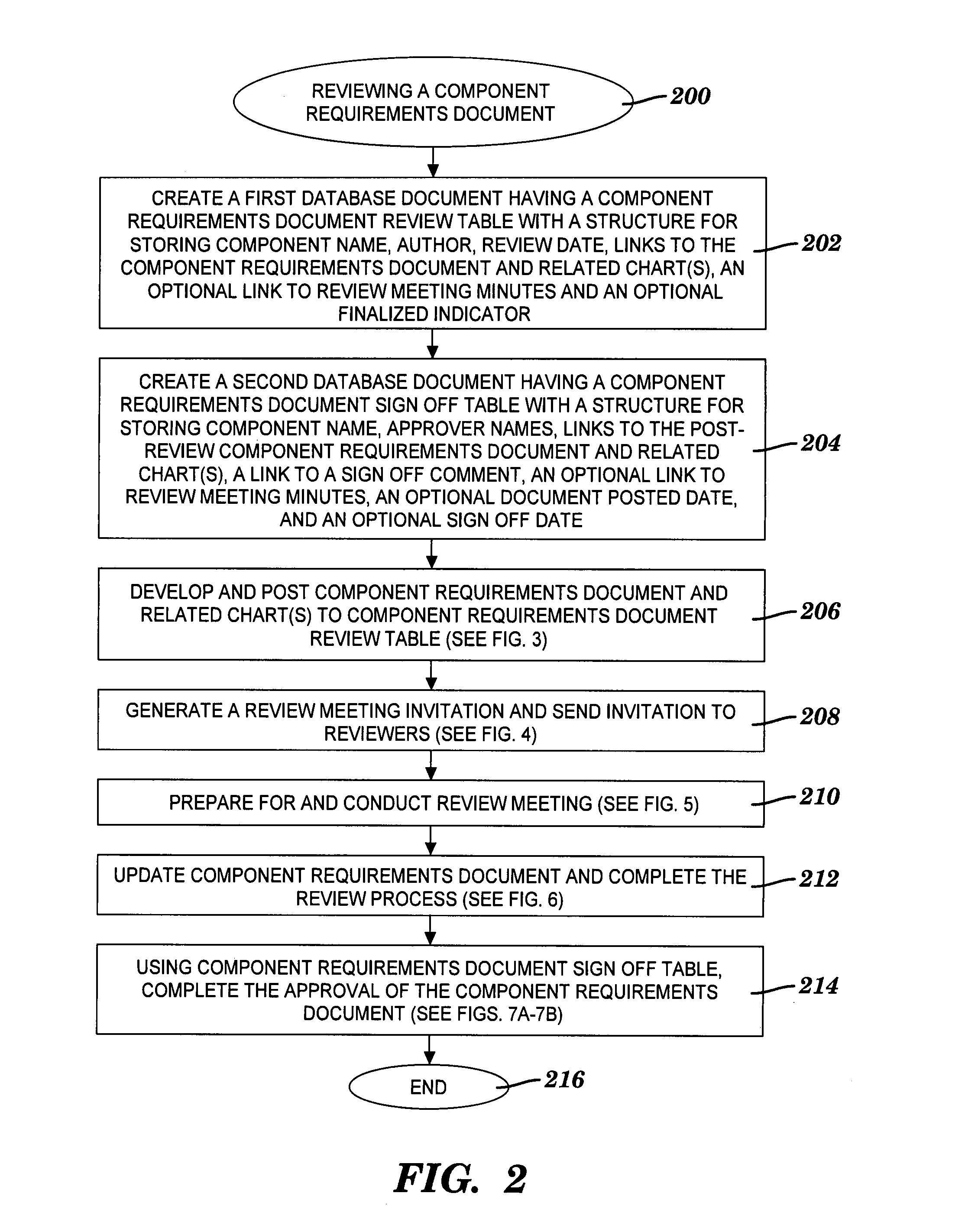
Method and system for reviewing a component requirements document and for recording approvals thereof
InactiveUS20090094530A1Simple and economical to implementMaintaining controllabilityOffice automationInput/output processes for data processingDocumentation procedureDocument preparation
A method and system for reviewing and recording approvals for a component requirements document (CRD). A document link to a CRD and a chart link to a condensed version of the CRD are inserted into a review database table. The CRD describes changes required for a software application component. Prior to a review meeting, reviewers activate the document link to display the CRD. During the review meeting, the reviewers activate the chart link to display the condensed version of the CRD for a review of the required changes. An annotation is inserted into the review database table in response to completing the review. The annotation indicates a readiness for an approval process in which the CRD is approved by approvers. A comment link to a sign off comment is inserted into a sign off database table. The sign off comment indicates an approval of the CRD.
Owner:IBM CORP
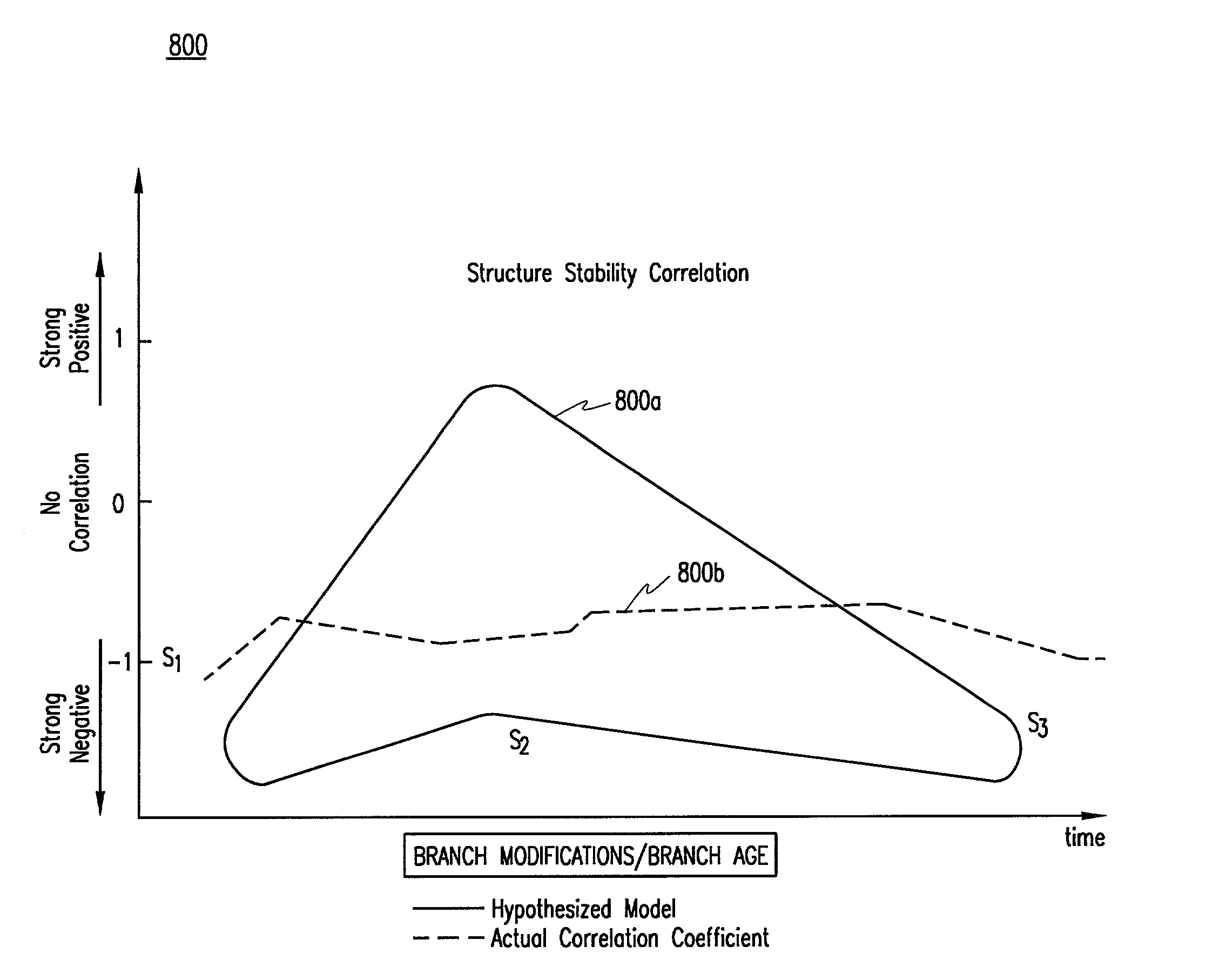
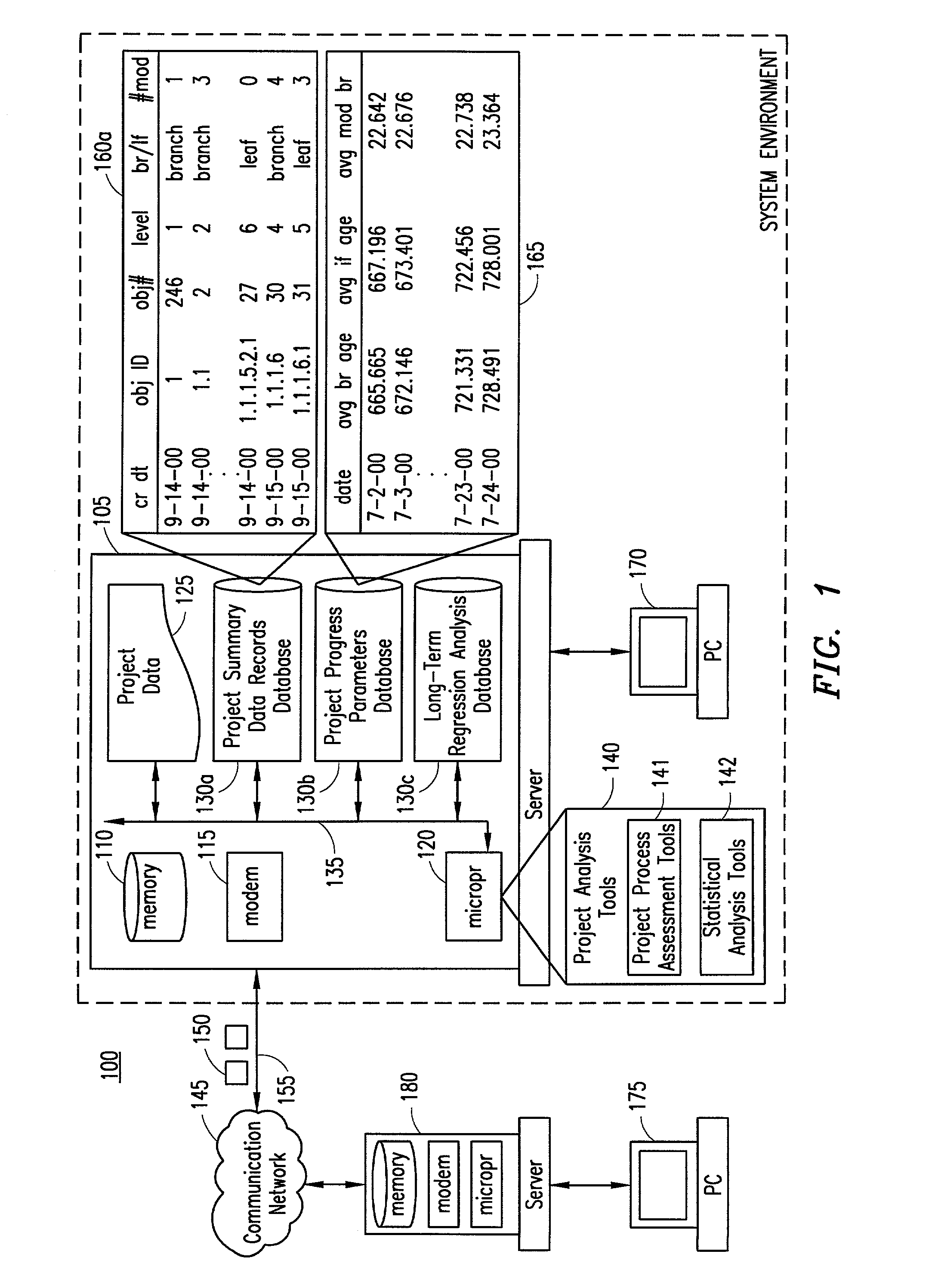
Method and system for assessing stability of a project application by performing regression analysis of requirements document metrics
InactiveUS7092895B2ResourcesSpecial data processing applicationsCorrelation coefficientRegression analysis
A system and method for determining the stability of a project. One embodiment includes computing at least two project progress parameters of a project for numerically describing elements of the project. Regression parameters are computed based upon the project progress parameters and correlation coefficients are computed utilizing the regression parameters. The correlation coefficients describe the strength of the correlation of the project progress parameters for indicating the stability of the project as project develops.
Owner:PEROT SYSTEMS
Interface test method and device
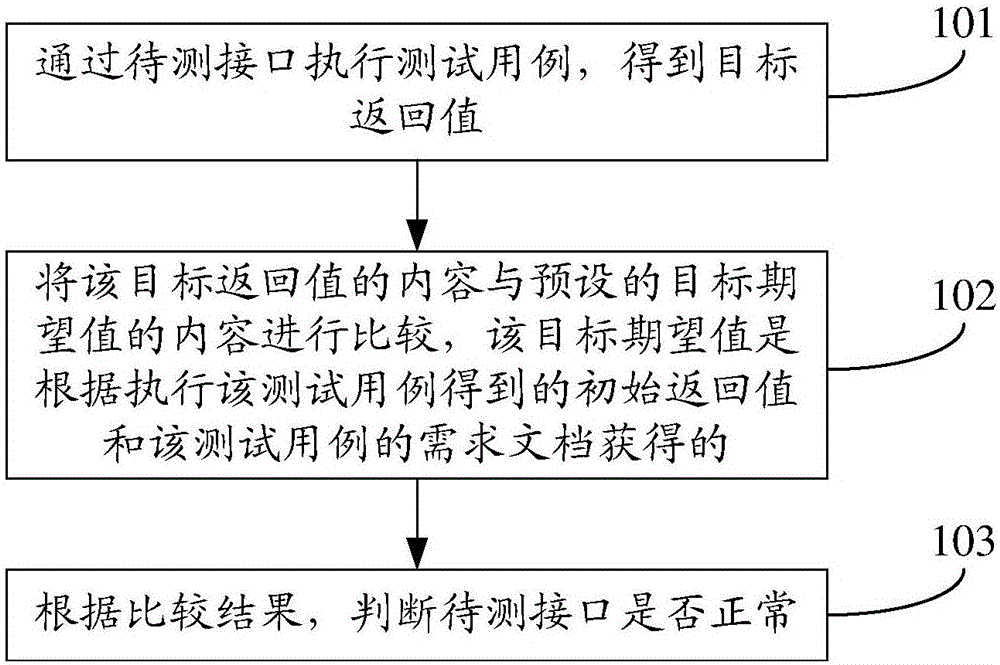
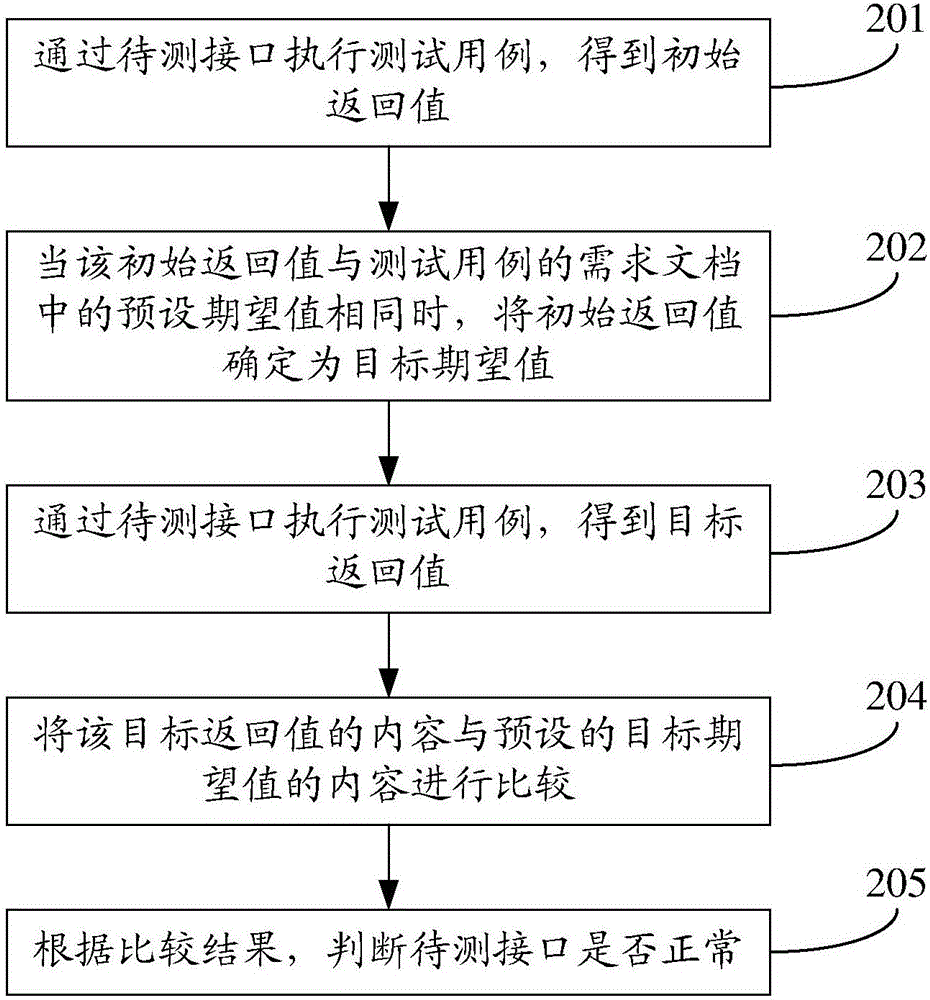
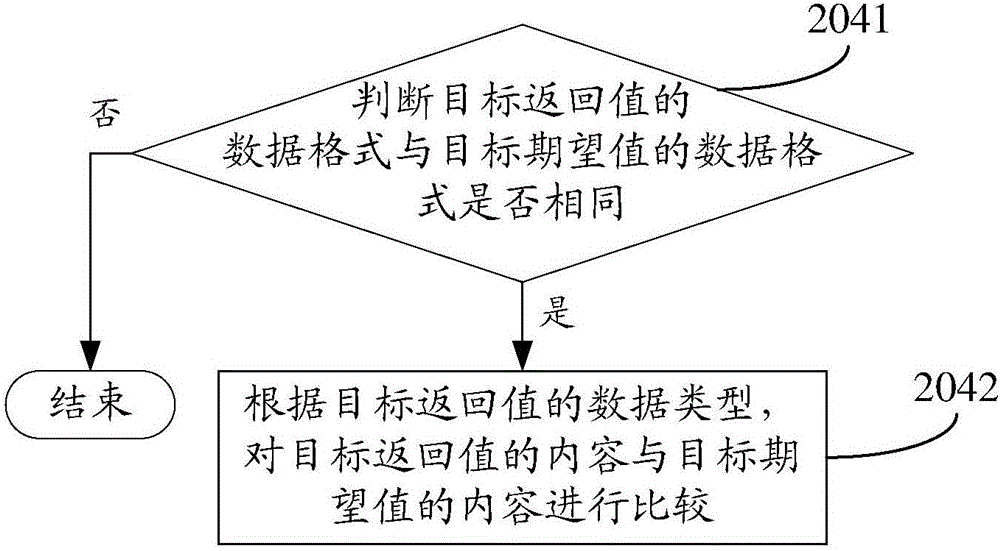
InactiveCN106776324AImprove reliabilityAvoid missing detectionSoftware testing/debuggingDependabilityRequirement document
The invention discloses an interface test method and device, and belongs to the technical field of computers. The method comprises the following steps: executing a test case through an interface to be tested to obtain a target return value; comparing a content of the target return value with a content of a preset target expected value, wherein the target expected value is obtained according to an initial return value obtained by executing the test case and a requirement document of the test case; judging whether the interface to be tested is normal or not according to a comparison result. The interface test method disclosed by the invention solves the problems that a missing measure phenomenon is easily caused by the fact that not all the contents in the return value can be verified, and the interface test reliability is relatively low in the prior art, so that the interface test reliability is improved. The interface test method is used for interface testing.
Owner:GUANGZHOU KUGOU TECH
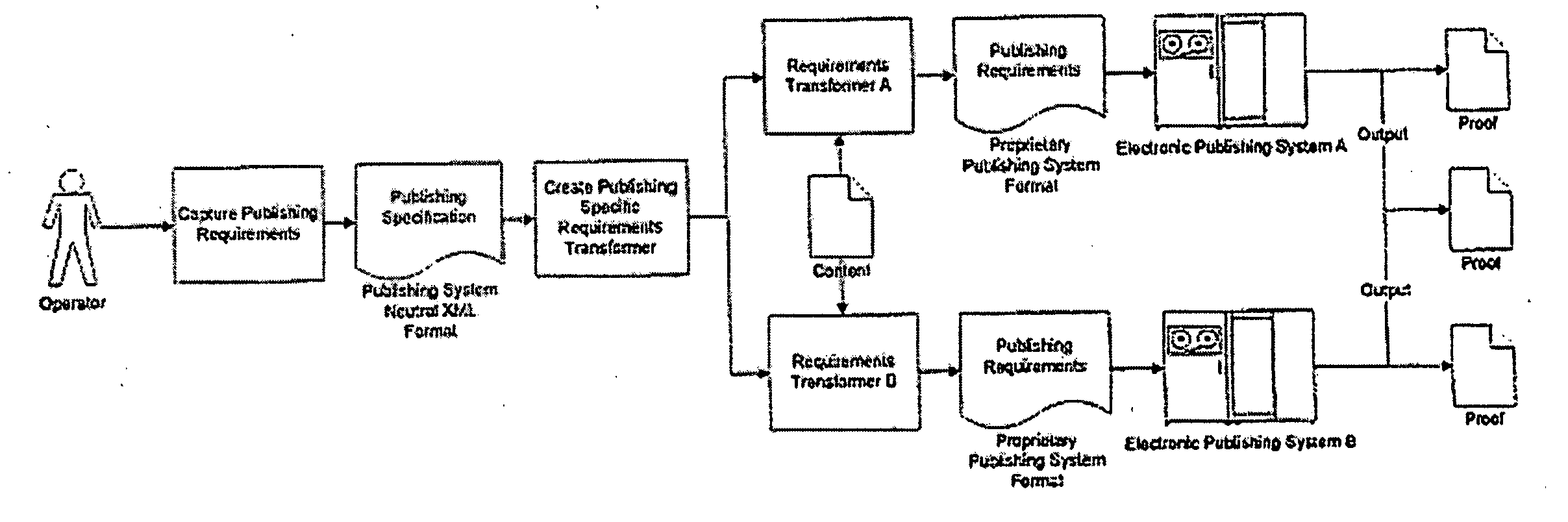
Electronic publishing system and method for managing publishing requirements in a neutral format
InactiveUS20070067336A1Digital data processing detailsNatural language data processingPaper documentDocument preparation
An exemplary embodiment of the present invention provides a method of publishing that includes extracting a design specification from a document of a user, the design specification including at least one of page size, page margins, paragraph style, and font style. The method further includes creating a master format specification from the design specification, the master format specification being content neutral and unique to the user. A master format specification is provided that includes a design specification extracted from a document. The master format specification is adapted to generate a first requirements file unique to a user, and the first requirements file is adapted to process a composition file including content from the document to create a first output file. The first output file is adapted to be processed by a first publisher's formatting engine to create the document. A system for publishing documents is also provided.
Owner:INNODATA ISOGEN
Methods and apparatus for data transfer in networks using distributed file location indices
ActiveUS20080208996A1Multiple digital computer combinationsTransmissionComputerized systemData shipping
Methods and apparatus for data transfer according to various aspects of the present invention operate in conjunction with a peer-to-peer (p2p) network associated with distributed file location index. For example, a system according to various aspects of the present invention may identify a high-demand file item according to communications on the p2p network and store a copy of the high-demand file item. The system may assign a non-random node identifier to the system for identifying the computer system in the p2p network. The system may then respond to requests for the high-demand file item.
Owner:SOLID STATE NETWORKS
Code generation method and device based on requirement document
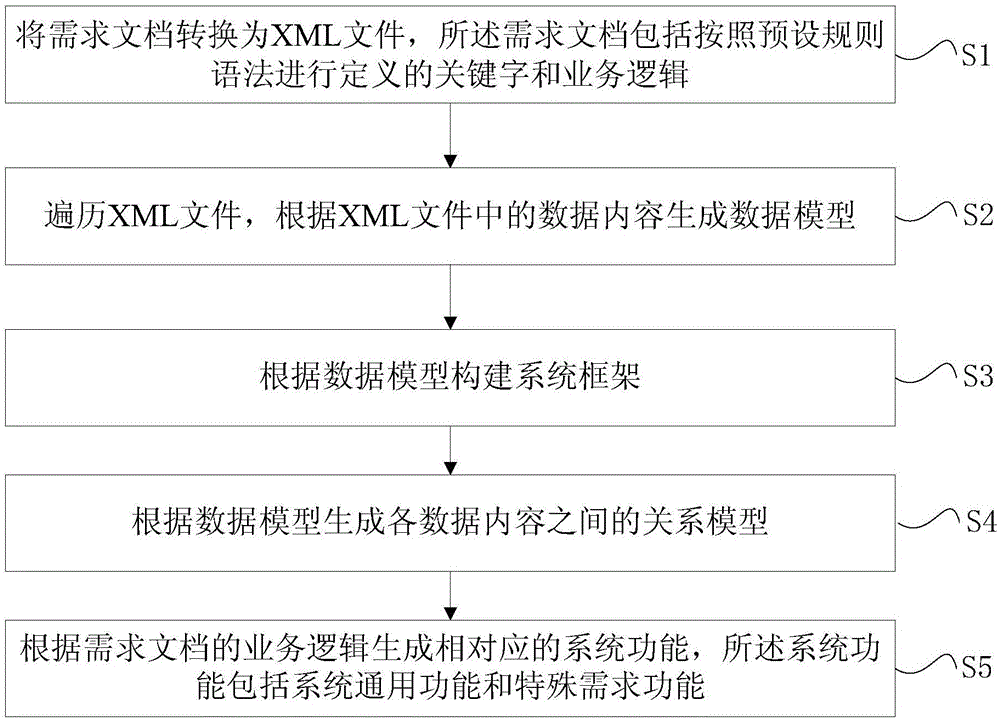
InactiveCN106250164ARespond quickly to changing requirementsProgramming languages/paradigmsFile access structuresRelational modelData content
The invention discloses a code generation method and device based on a requirement document. The method comprises the steps of S1, converting the requirement document into an XML file; S2, traversing the XML file and generating a data model according to data contents in the XML file; S3, establishing a system framework according to the data model; S4, generating a relationship model among the data contents according to the data model; and S5, generating corresponding system functions according to service logic of the requirement document, wherein the system functions comprise system universal functions and special requirement functions. According to the method and the device, code can be generated directly by the requirement document and most of the functions described by the requirement document can be satisfied. The method and the device have the following significance that the working focus of a developer is transferred to the service logic and algorithm, requirement changes can be rapidly responded and some requirement changes can be set by modifying characters in the document by a demander.
Owner:广州南方仕通网络科技有限公司
Supply scheduling
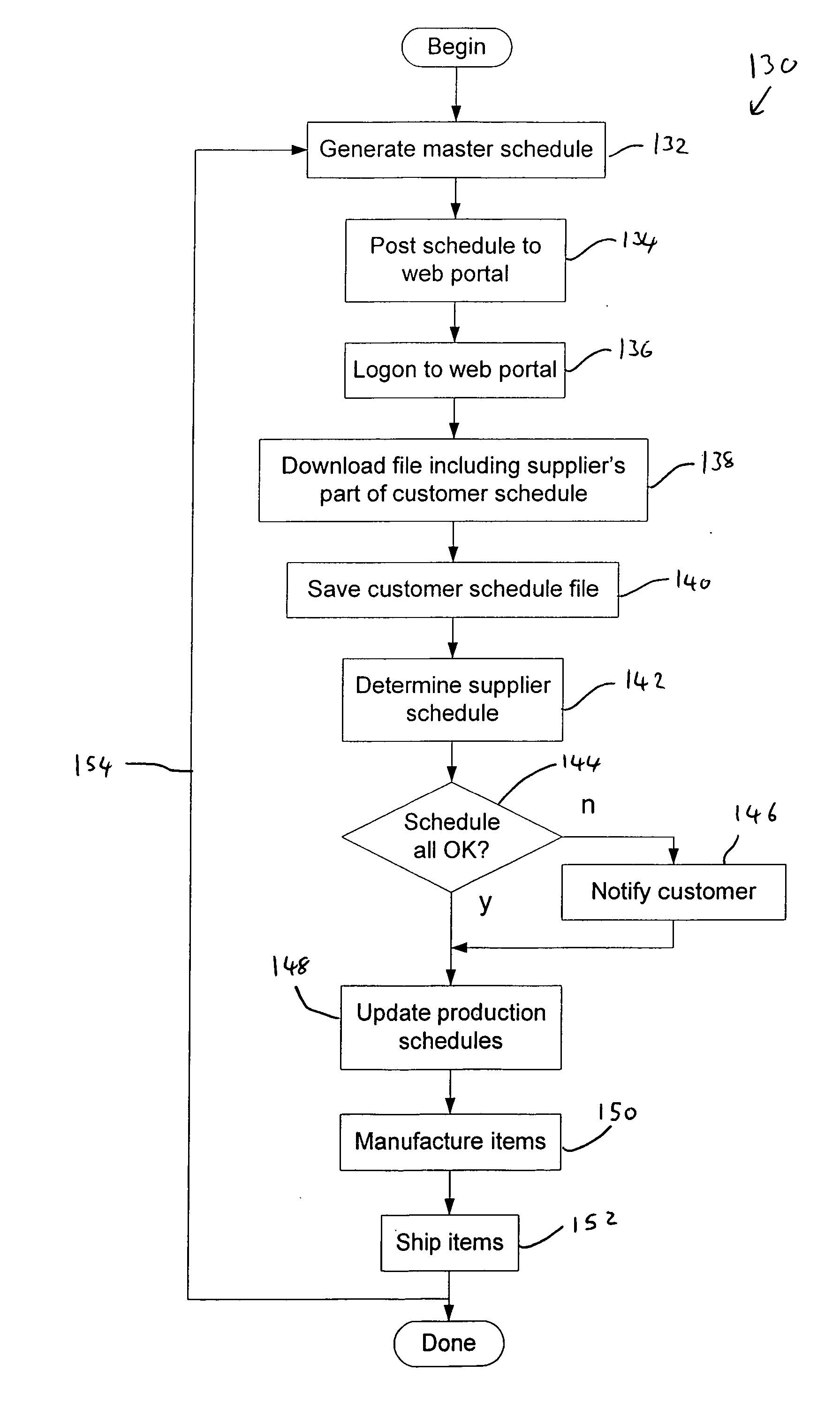
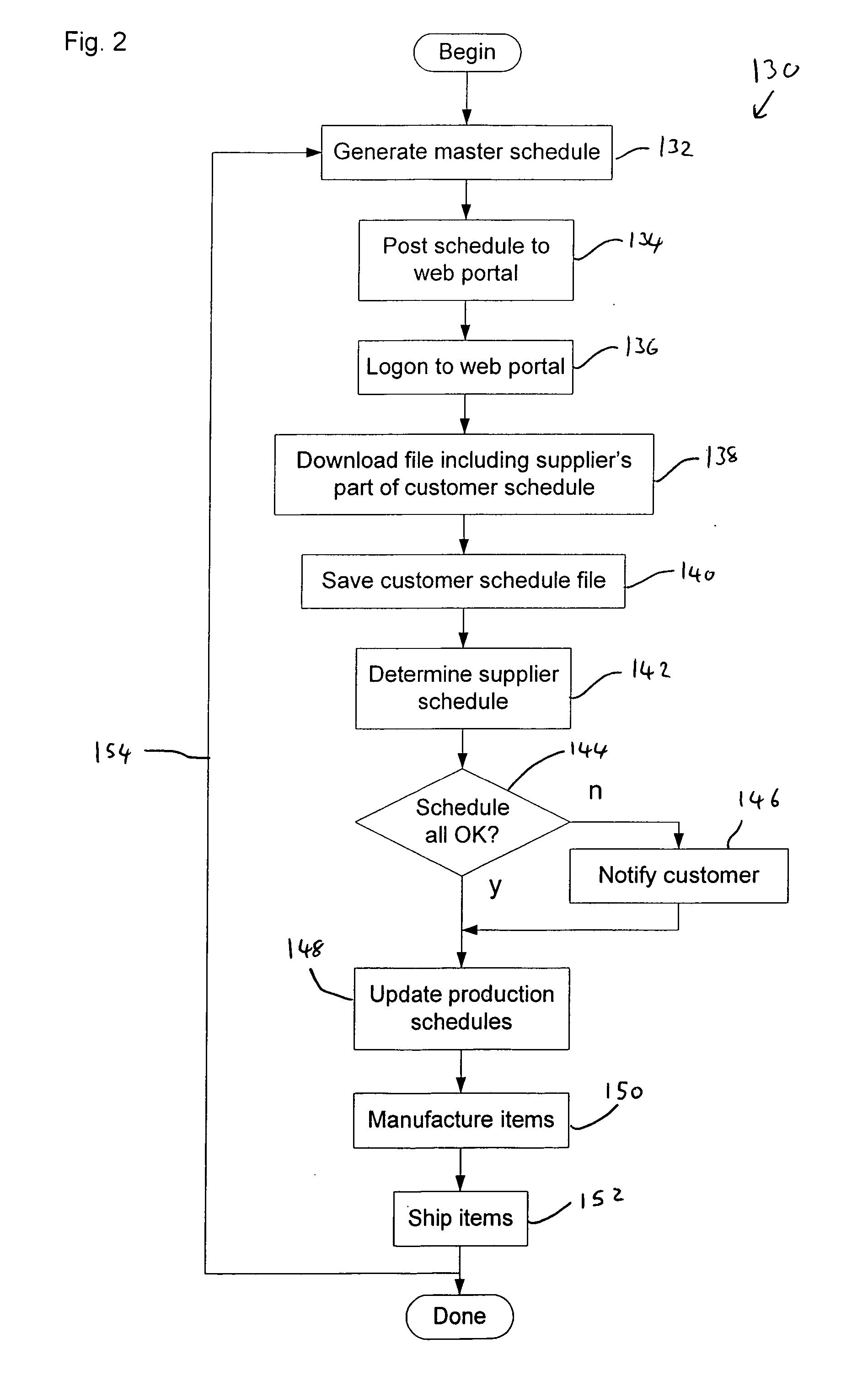
InactiveUS20070016319A1Sure easyEasily viusualizableResourcesSpecial data processing applicationsCustomer requirementsComputer science
Computer implemented methods, data processing apparatus and manufacturing systems for determining or using current supplier schedule are described. A current customer requirement file is received including data items specifying a customer's current requirement of different parts each having associated supply dates from the supplier. The total quantity of each different type of part for each of a plurality of different time periods is determined. Data items specifying the total quantity of each different part and respective associated supply dates are stored in a current supplier schedule file. The current supplier schedule file is exported and can be displayed. A current net change in the supplier schedule based on the current supplier schedule and a previous supplier schedule can also be determined.
Owner:FIRTH RIXSON
Method for business process mapping, design, analysis and performance monitoring
InactiveUS20060111950A1Sufficiently accurateSufficiently detailedPayment architectureResourcesData streamBusiness process mapping
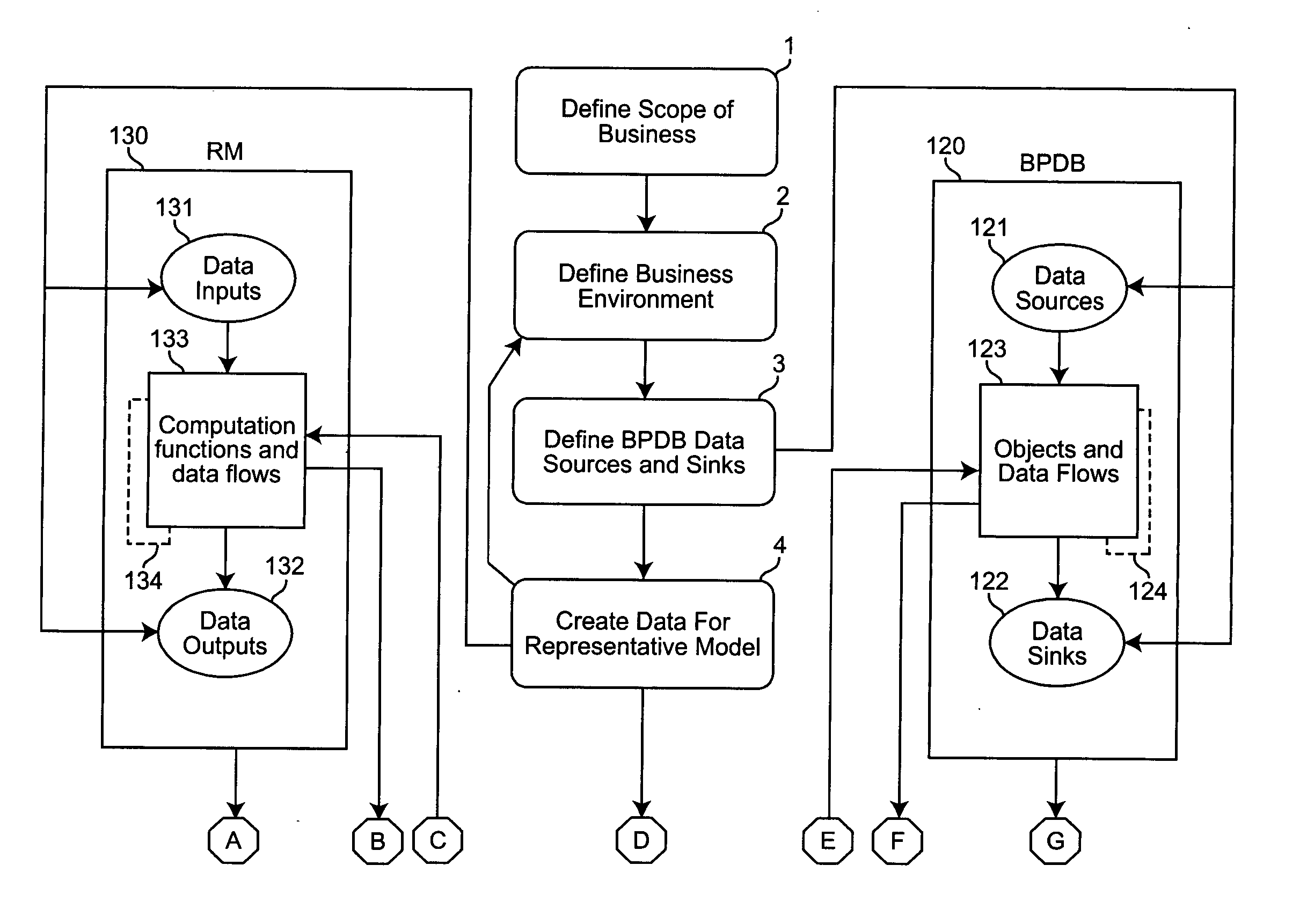
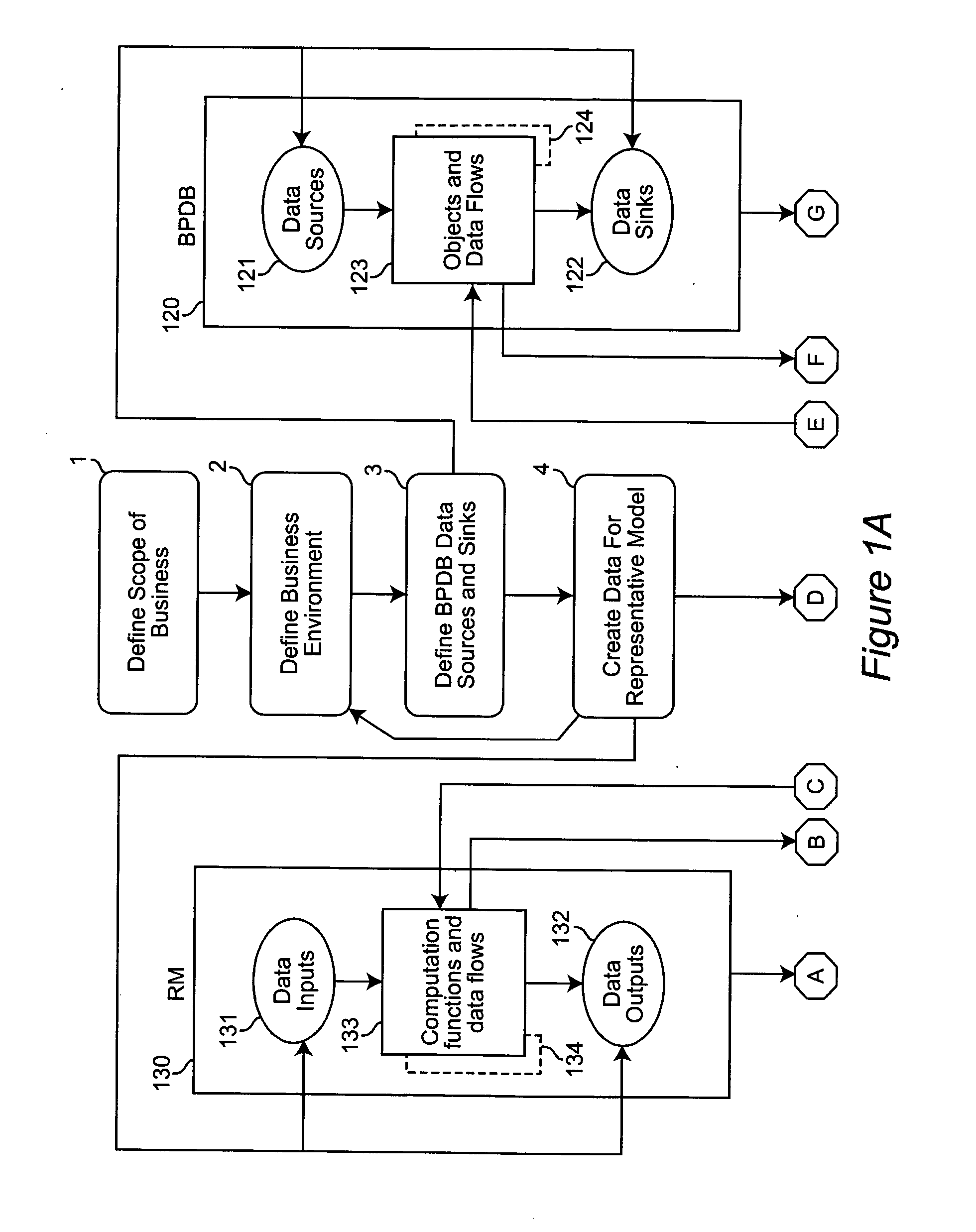
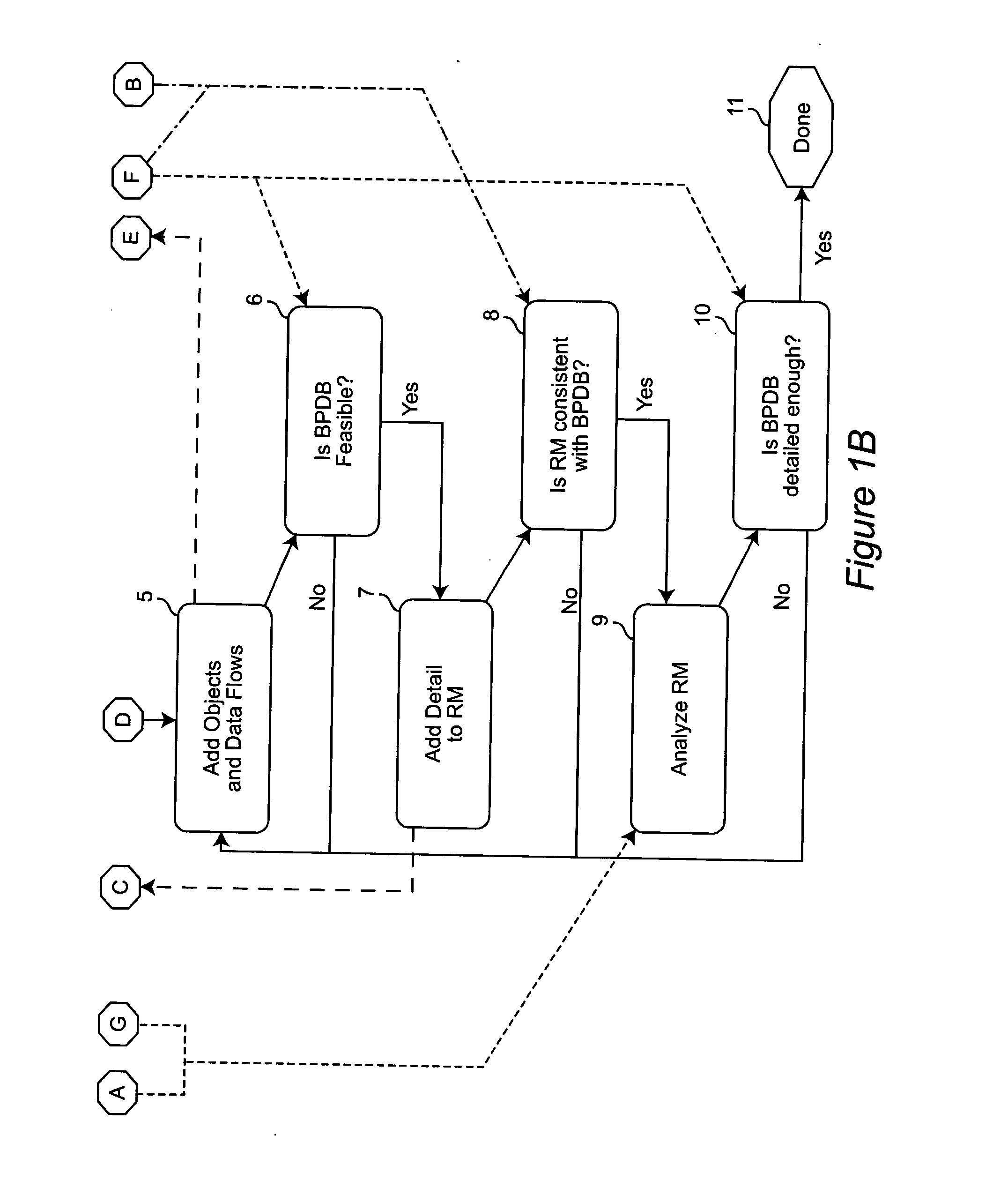
A method of creating a systems requirement document by using a numerical modeling tool, such as a spreadsheet, to prototype an operational process in terms of a numerical picture of the goals, metrics, performance targets and constraints used by managers of the operational process. A process design blueprint is defined for the operational process, including data sources and data sinks. A representative model of the process design blueprint is created. If the model is not detailed enough for implementation by IT professionals, model objects and data flows are added to the blueprint and the representative model is modified to be consistent with the blueprint. Surrogate calculations may be made for computational task objects or, alternatively, separate process design blueprints may be generated for such computational task objects. This cycle is repeated until the model is detailed enough for implementation.
Owner:IBM CORP
Script-based method for implementing service configuration
ActiveCN102147726ASimplify complexityGuaranteed correctnessSpecific program execution arrangementsStreaming dataInternal memory
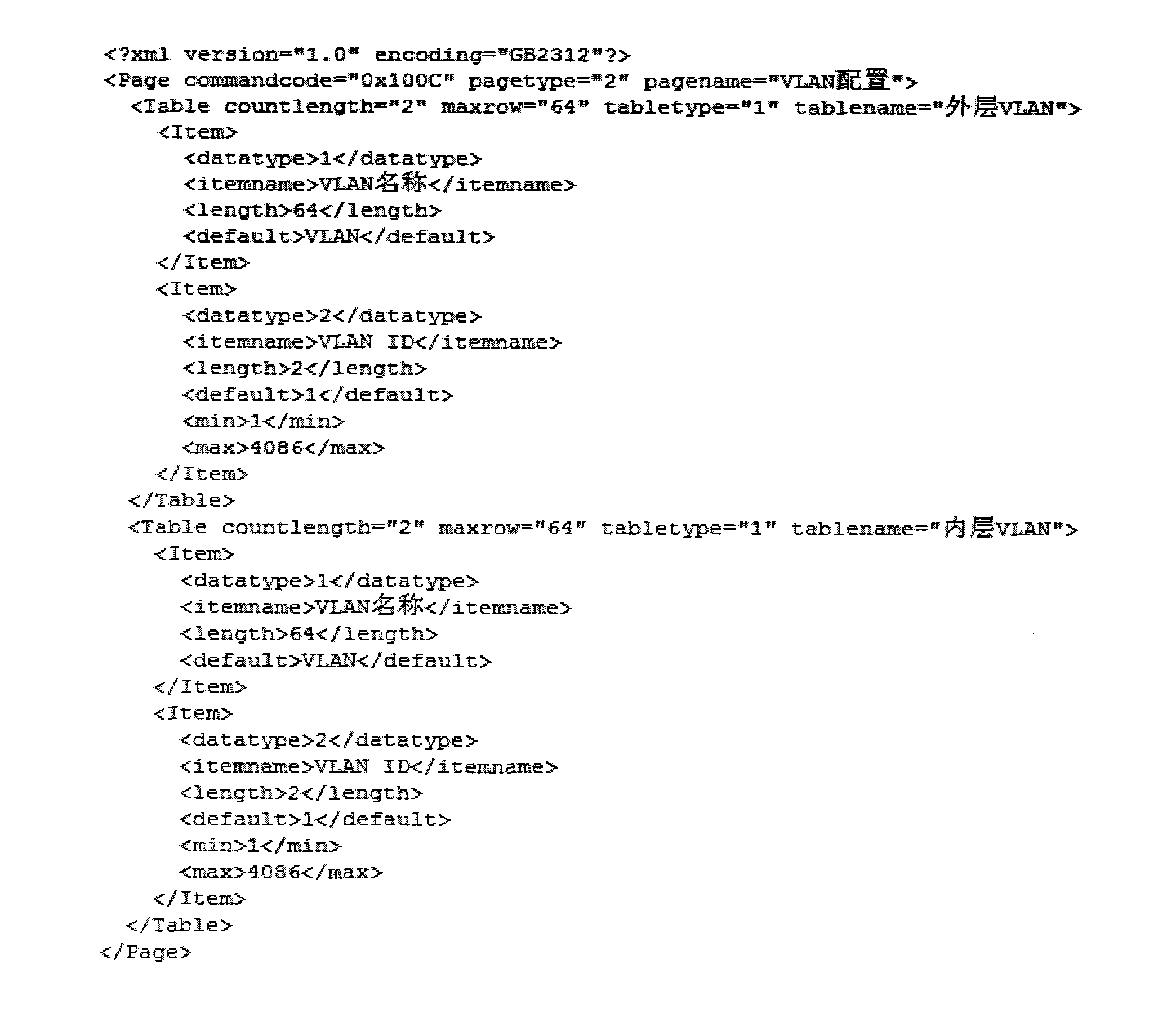
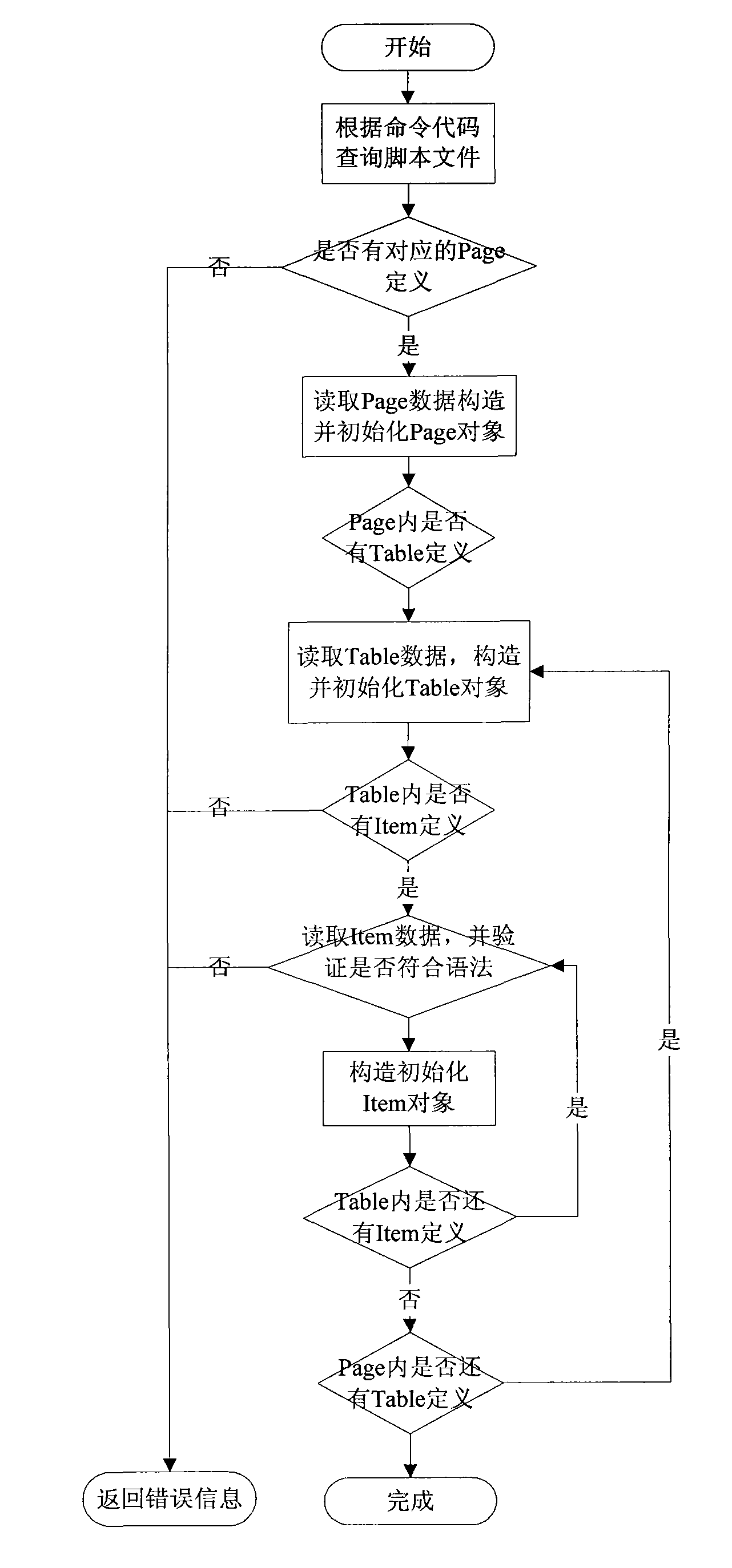
The invention relates to a script-based method for implementing service configuration, comprising the following steps: carrying out grammatical definition on scripts; analyzing the scripts; analyzing service configuration data; firstly analyzing requirement documents for each service configuration and allocating fixed service configuration command codes; and compiling the script definition files describing the service configuration. Analysis of the scripts refers to reading the script definition files corresponding to the service configuration and writing the scripts in line with the grammatical definition into corresponding objects in an internal memory, the analysis is terminated if scripts not in line with the grammatical definition appear; analysis of the service configuration data requires the following steps: analyzing byte stream data acquired from the device into service configuration item data according to the definitions of the service configuration scripts and carrying out accuracy verification on the service configuration item data. The method in the invention is based on XML (extensive makeup language) script language and defines the service configurations by descriptions, thus simplifying complexity in implementing service configurations and ensuring accuracy in service configurations.
Owner:FENGHUO COMM SCI & TECH CO LTD
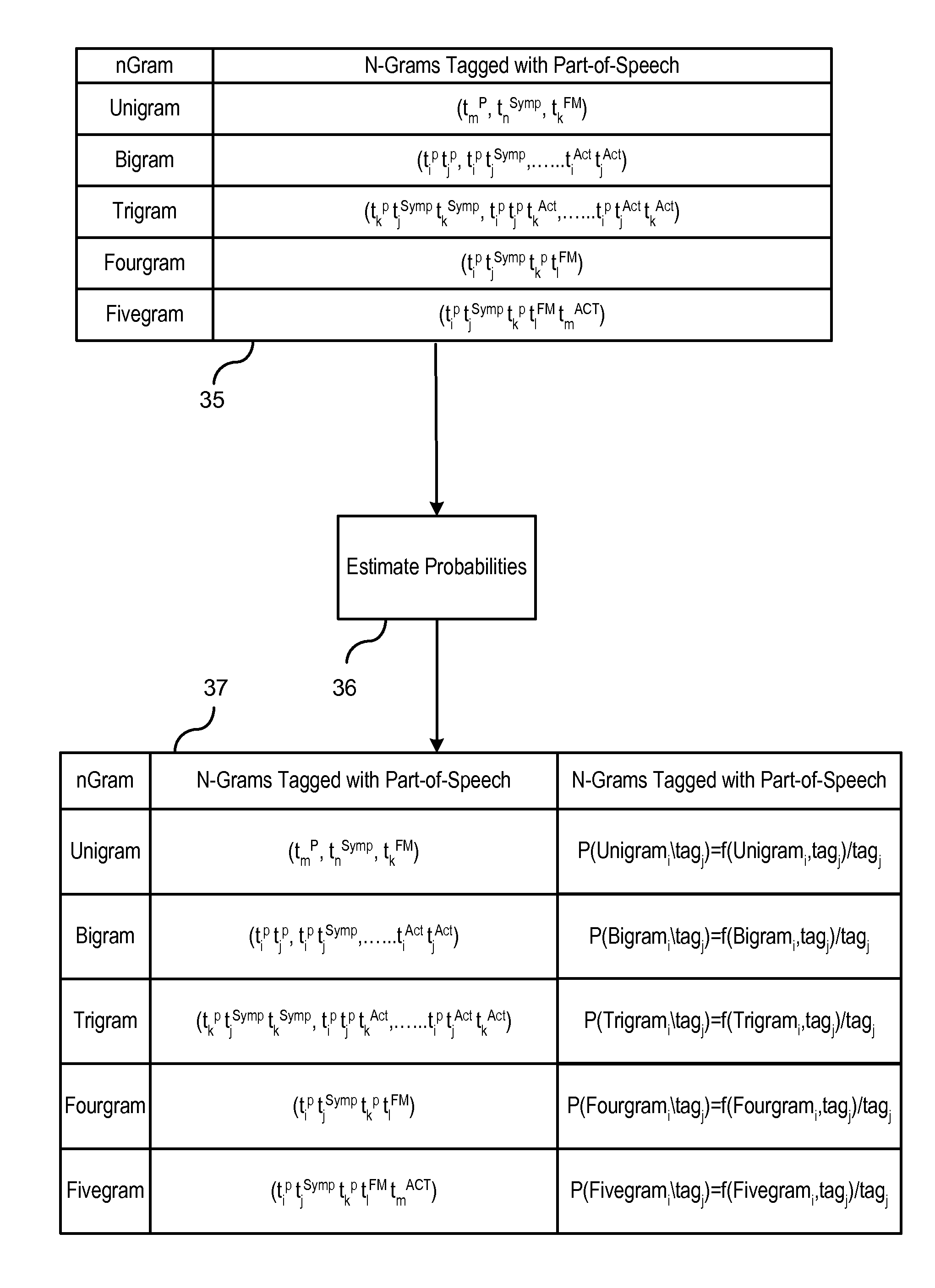
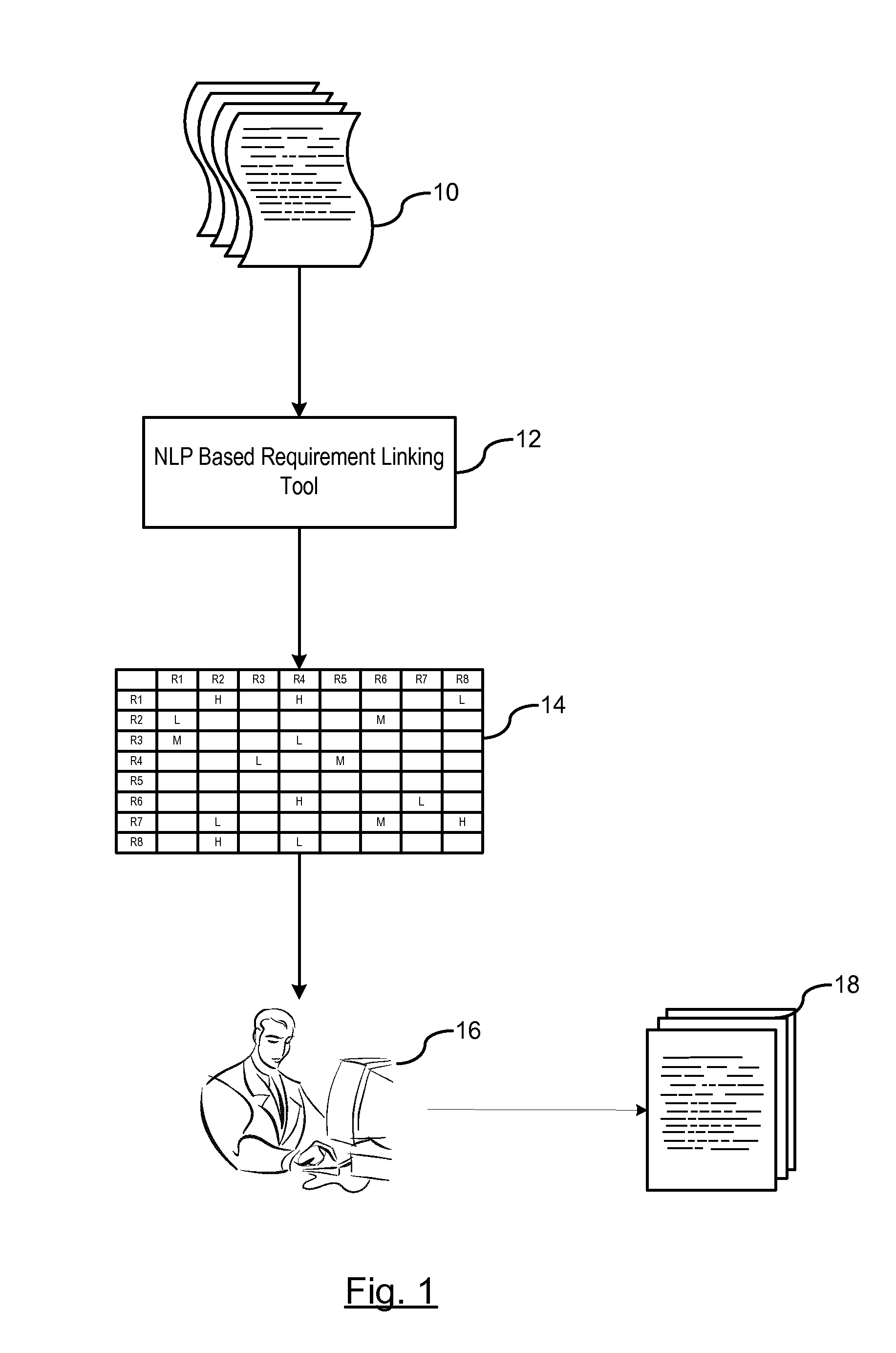
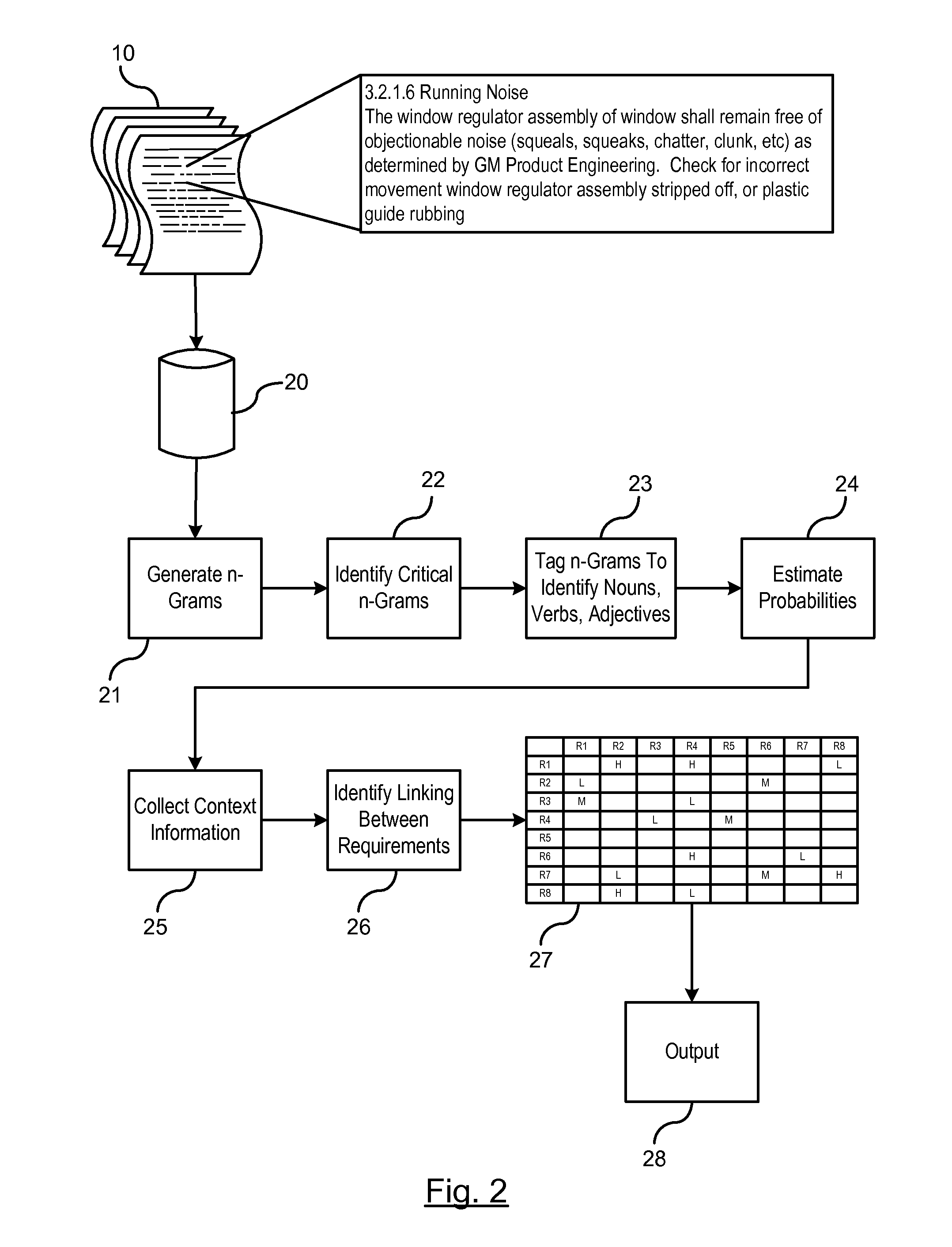
Automatic linking of requirements using natural language processing
ActiveUS20150286631A1Quality improvementEffective warranty based trackingSemantic analysisSpecial data processing applicationsPart of speechData mining
Owner:GM GLOBAL TECH OPERATIONS LLC
Method for identifying requirements for designing information technology systems
A method for generating specification requirements for an Information Technology development project has been developed. First, a framework is created for decomposing and categorizing organizational information into data elements that include project design requirements. These data elements are then stored in a data repository. A relationship is defined between the data elements and corresponding project information provided by the end-user. These defined relationships are also stored in the data repository. Next, a guided facilitation process is used to elicit objective information from the end-user regarding objectives for new technology. Also, specification information is collected from the end-user based upon the objective information. The requirements for the project are determined from the end-user based upon the specification information. This continues until informational needs pertinent to the various types and categories of requirements have been specified. Then the data elements in the data repository are mapped with the corresponding informational needs. Finally, a standards requirement document for the project is generated using the mapped data elements from the data repository.
Owner:FACILITAIRE
Determining functional design/requirements coverage of a computer code
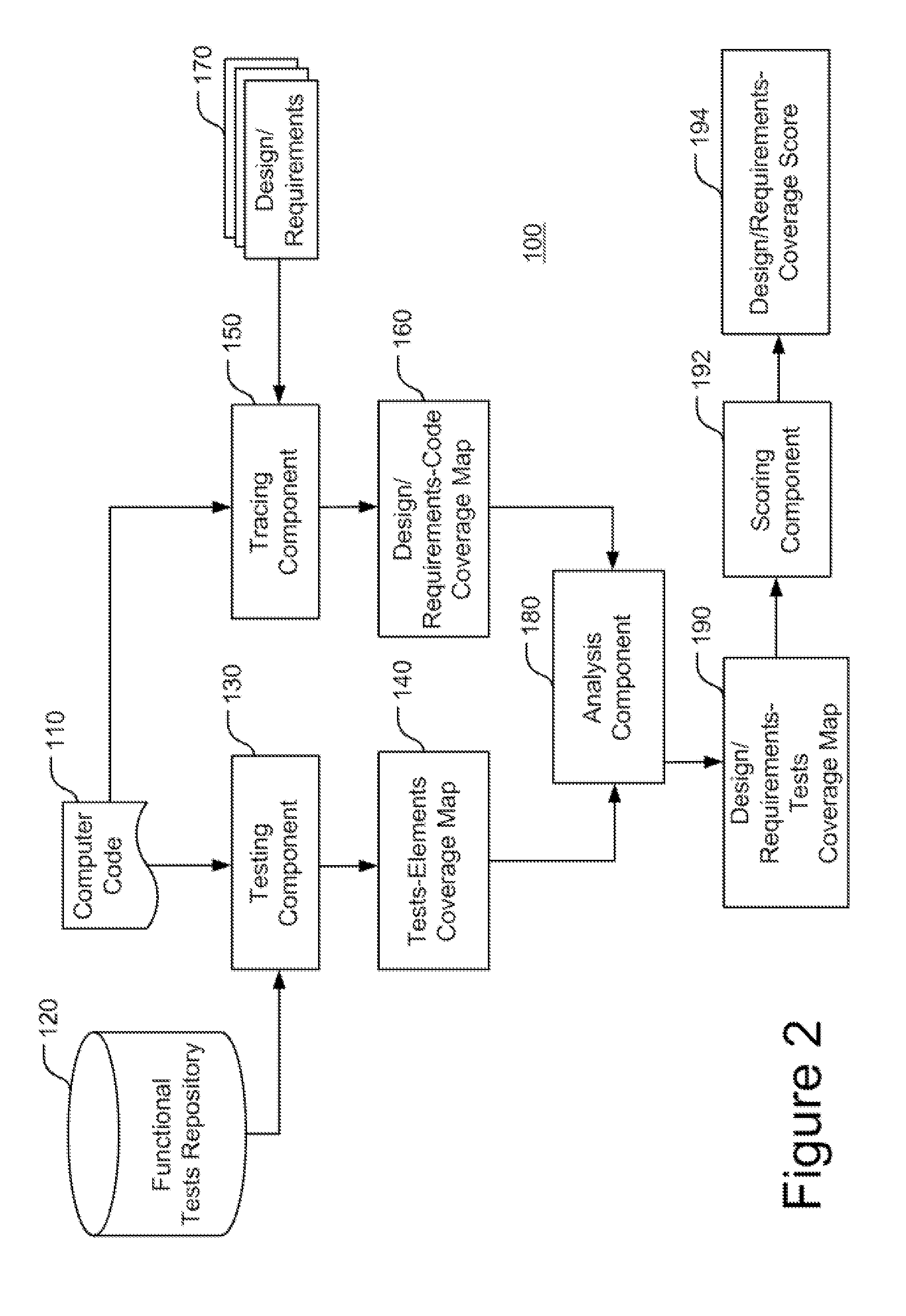
InactiveUS20110271252A1Error detection/correctionRequirement analysisFunctional testingCode coverage
A method that includes: running a set of functional tests over a computer code; determining, for each code element of the computer code, which functional test covered it, to yield a tests-elements coverage map; associating portions of the computer code with corresponding design portions or requirements derived from a design document or a requirements document respectively, associated with the computer code, to yield a design / requirements-code tracing map; deriving, from the tests-code coverage map and the design / requirements-code tracing map, a design / requirements-tests coverage map, exhibiting coverage of the computer code by the functional tests, in terms of the design or the requirements, wherein at least one of the running, the determining, the associating, and the deriving is executed by at least one processor.
Owner:IBM CORP
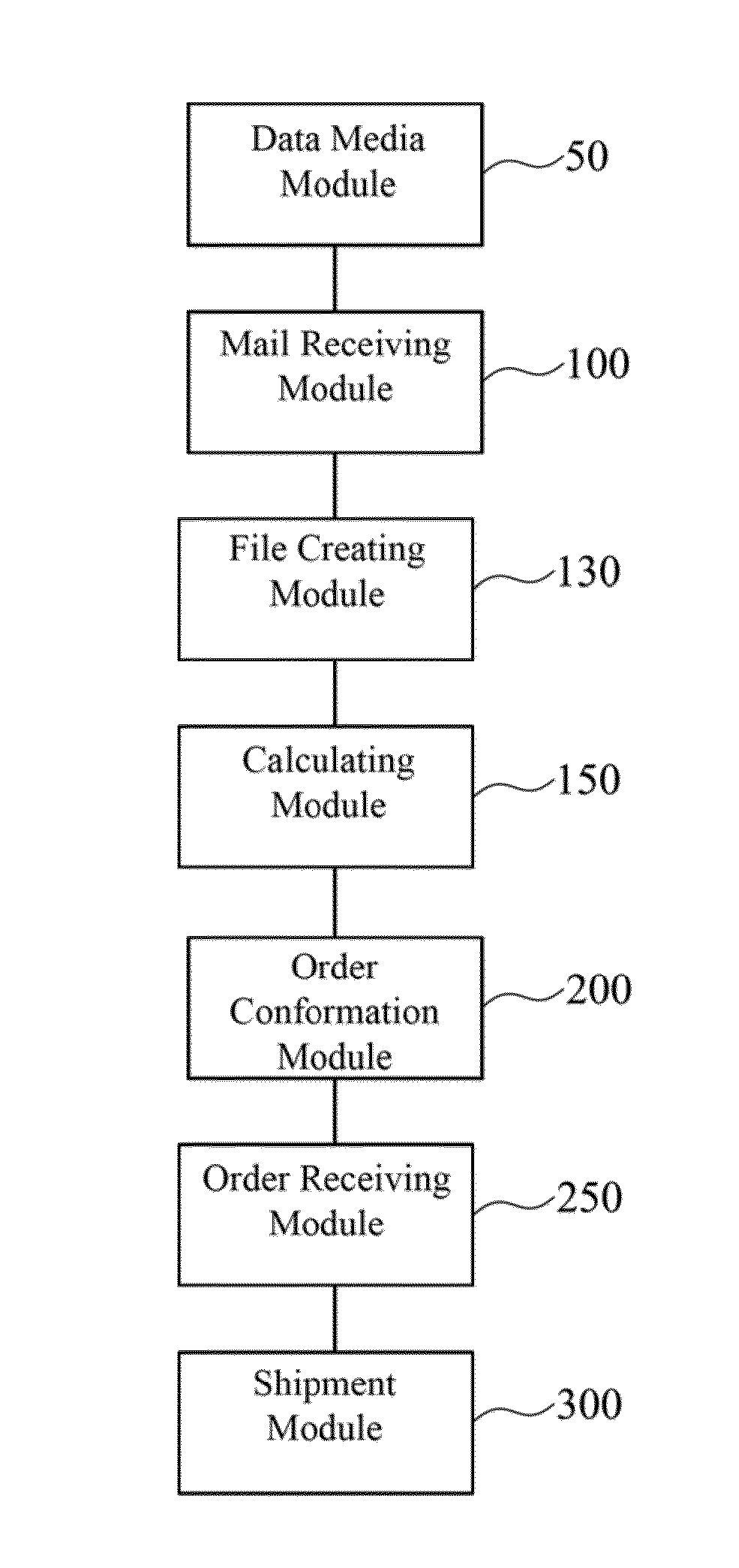
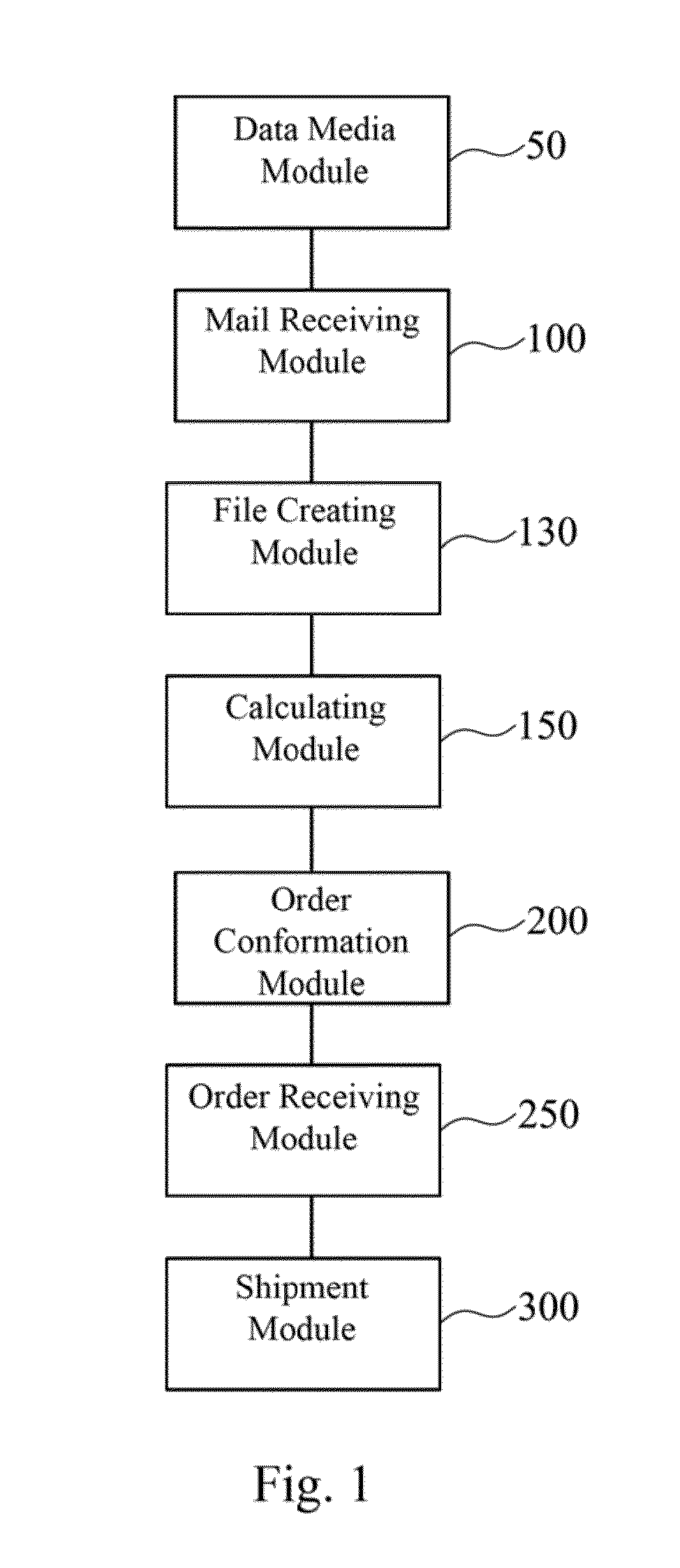
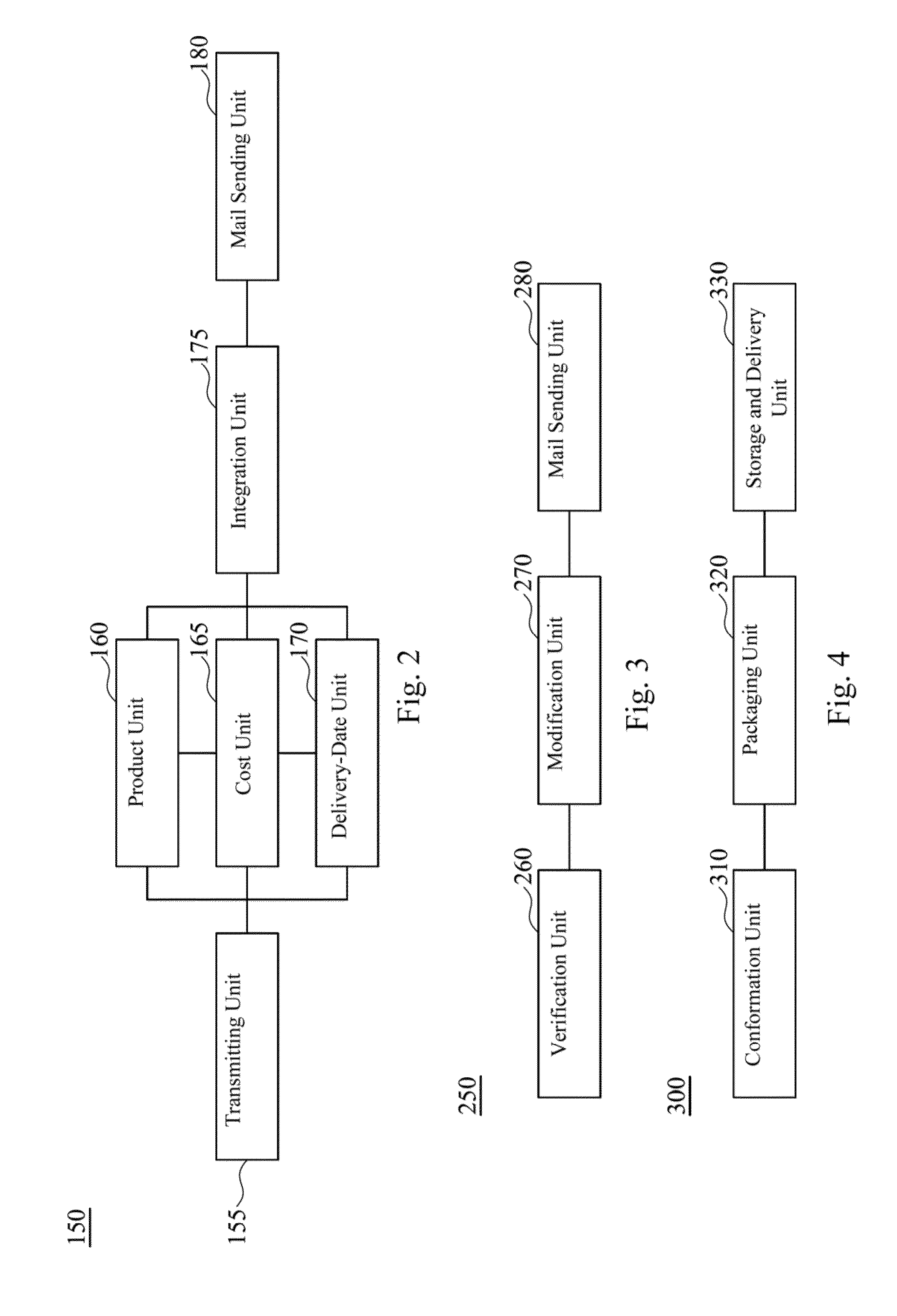
Order management system and order management method thereof
A computer implemented order management system includes a data media module, a mail receiving module, a file creating module, a calculating module, an order confirmation module, an order receiving module, and a shipment module. The data media module is for providing a product requirement application form to be downloaded by a customer. The mail receiver module is for receiving the product requirement application form filled out by the customer. The file creating module is for creating a requirement file. The calculating module is for estimating and providing a delivery date, a quantity, and a quotation. The order confirmation module is for confirming whether the customer accepts the delivery date, the quantity, and the quotation. The order receiving module is for receiving and confirming an order form provided by the customer. The shipment module is for arranging shipment to the customer according to the order form.
Owner:INTERFACE OPTOELECTRONICS SHENZHEN
Method and system for extracting requirements from narratives
InactiveUS20130227382A1Natural language data processingResourcesDocumentation procedureREMS Stakeholder
Owner:SIEMENS AG
Embedded automation development method
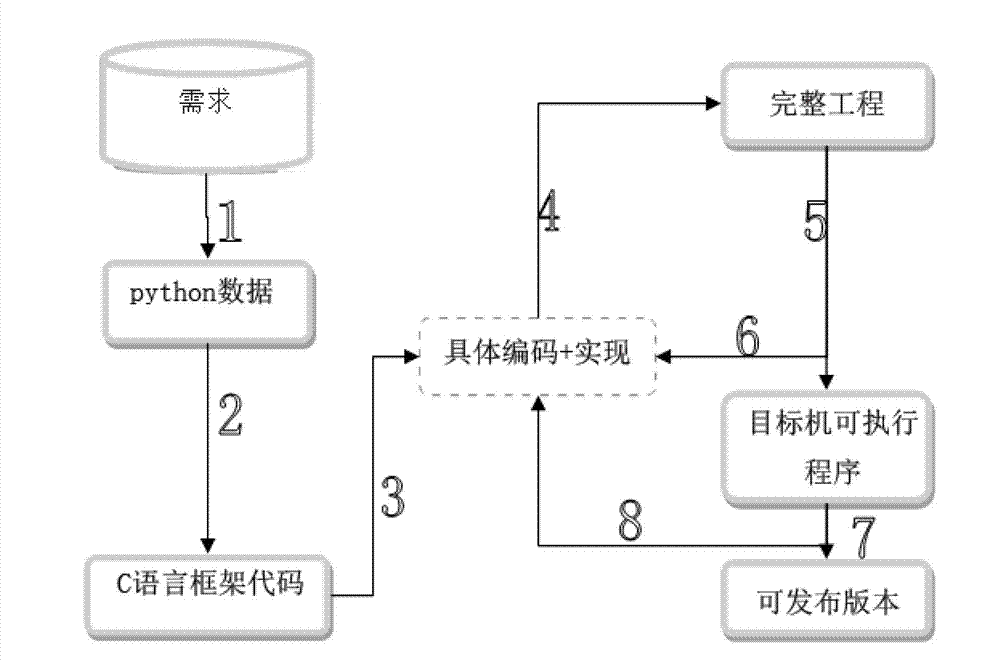
InactiveCN102902540AFree laborImprove stabilitySpecific program execution arrangementsVisual BasicDocumentation procedure
The invention discloses an embedded automation development method which comprises the following steps of: parsing a requirement document into a data format which can be understood by python through VB (Visual Basic); translating the generated Python data to generate a related frame code of a C programming language or C++ programming language again by the python according to the actual customization needs, and supplying the frame code to a coder to use; carrying out writing by the coder on the basis of the frame code so as to realize the needed features and functions; uploading the code after writing to a code server to finish a complete code project; formulating a compiling specification and a compiling time of an item through an automatic compiling tool bamboo; if compiling succeeds, generating an executable program, introducing the executable program into a target machine through a script, carrying out automation test based on robot framework, and finally issuing a version through the test; and if the compiling fails, carrying out mail notification on the coder with a revise history on the code server, and in addition, recording an error reason and an error causing person.
Owner:ZHEJIANG CHUANGJIA DIGITAL TECH
System and method for consistency checking in documents
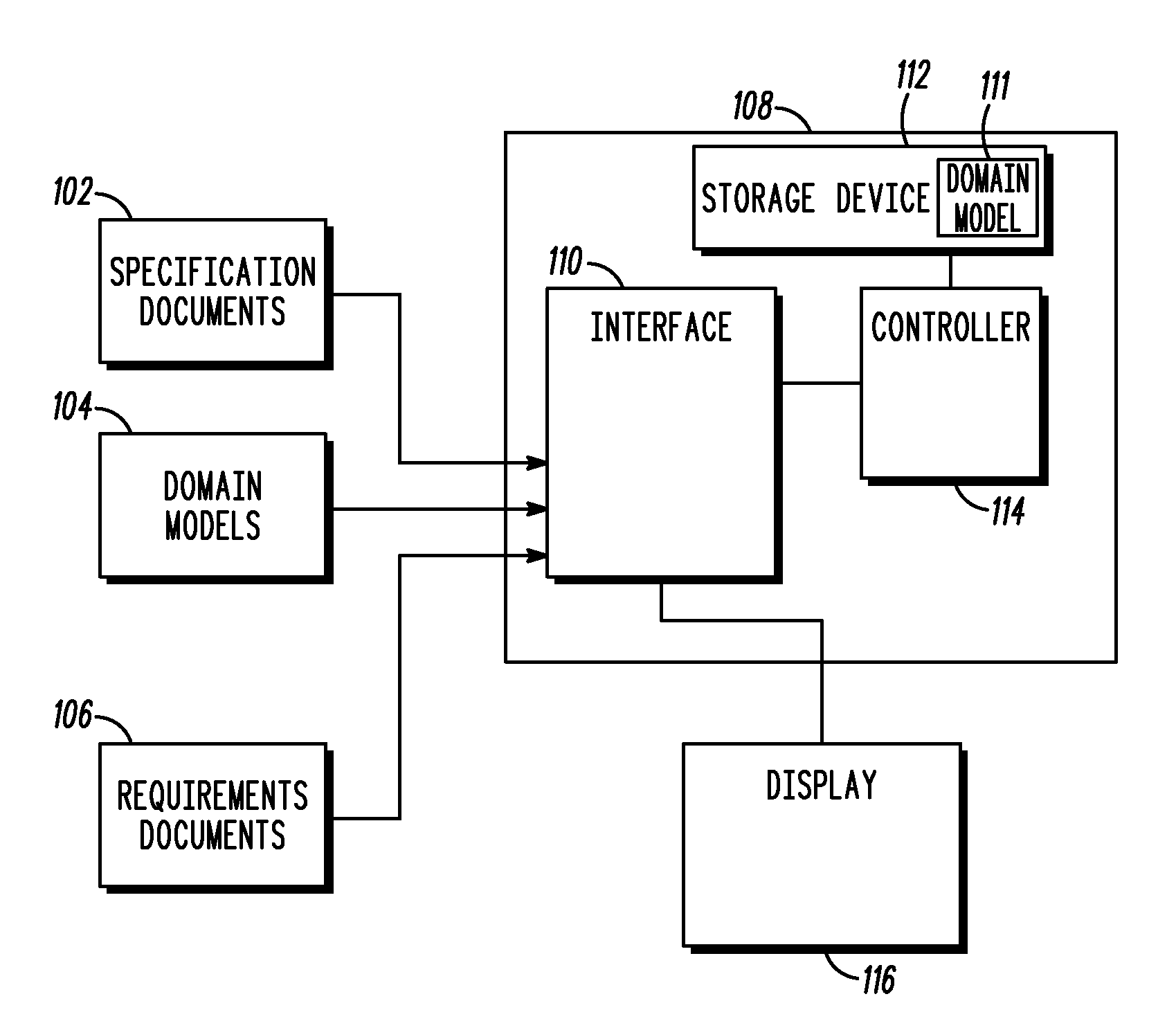
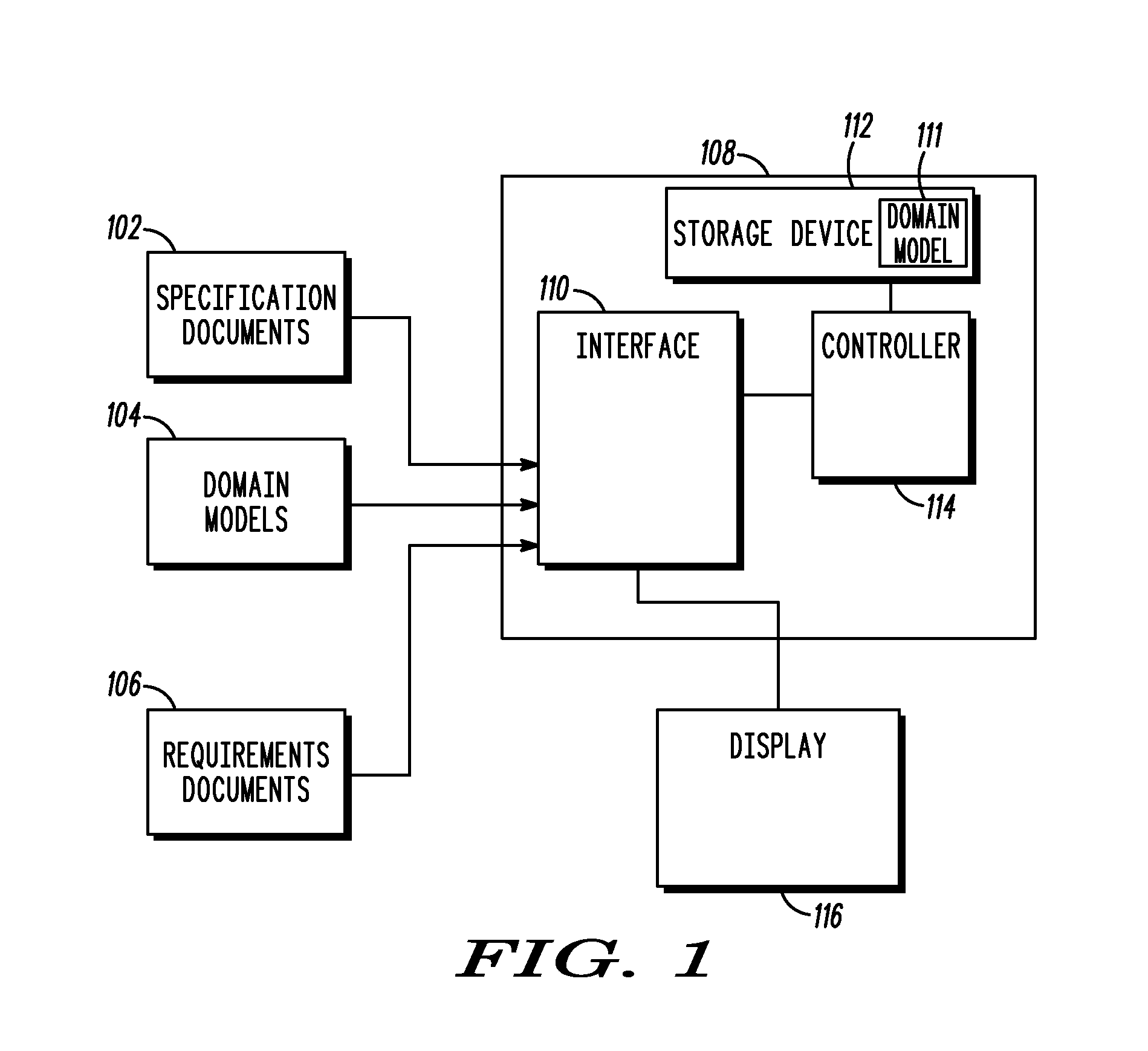
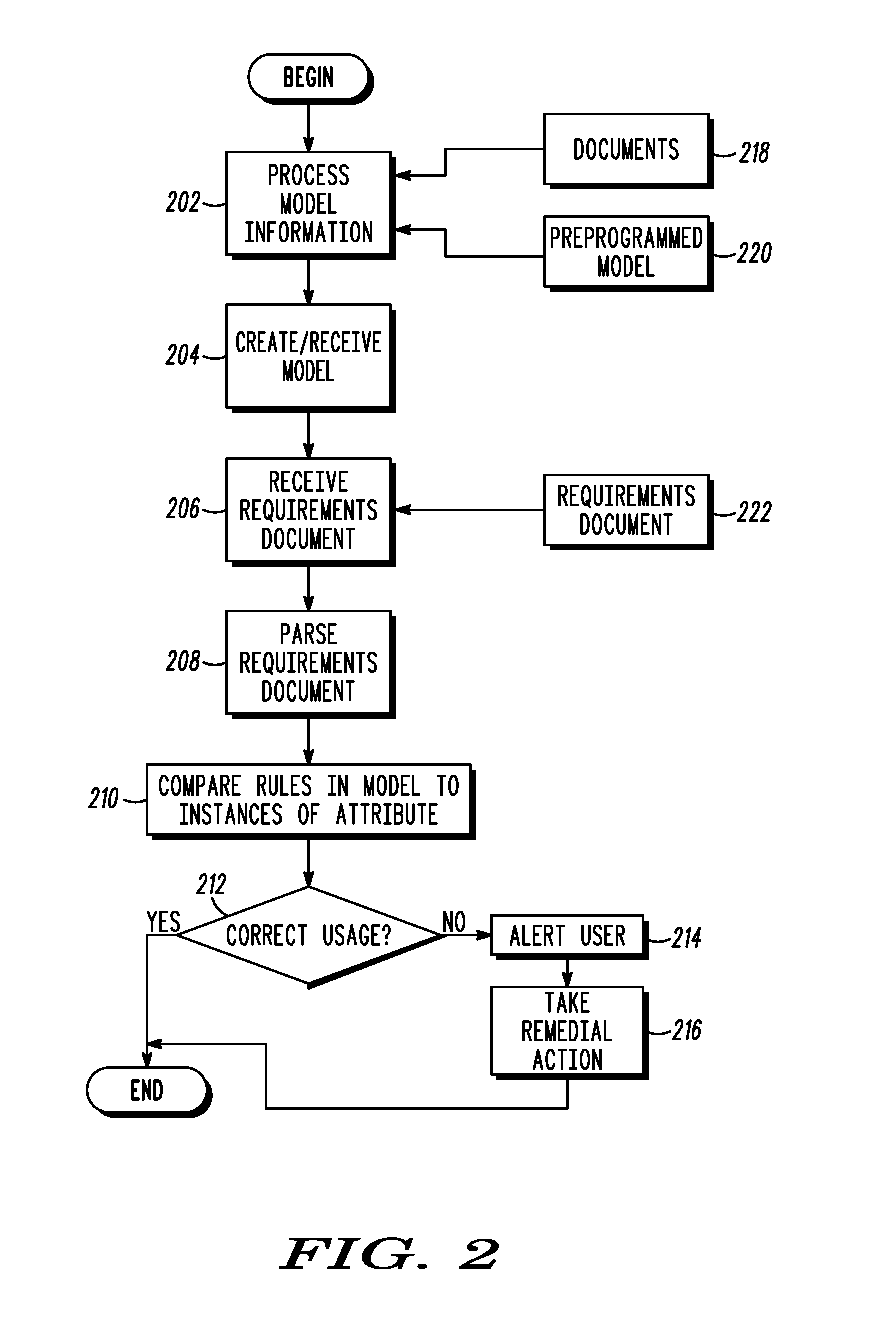
A domain model (104) is created. The domain model (104) specifies a relationship between a first attribute and a second attribute. A requirements document (106) is parsed. As the requirements document (106) is parsed, at least one usage of the first attribute with the second attribute is located within the requirements document (106). A mapping is also provided between the first attribute, second attribute, and the relationship in the domain model (104). Thereafter, the at least one usage of the first attribute with the second attribute is compared to the relationship. Based upon the comparison, a correctness of the at least one usage in the requirements document (106) is determined.
Owner:MOTOROLA INC
P2P (Peer-to-Peer) mode based PSRD (Program Support Requirements Document) universal service resource discovery method
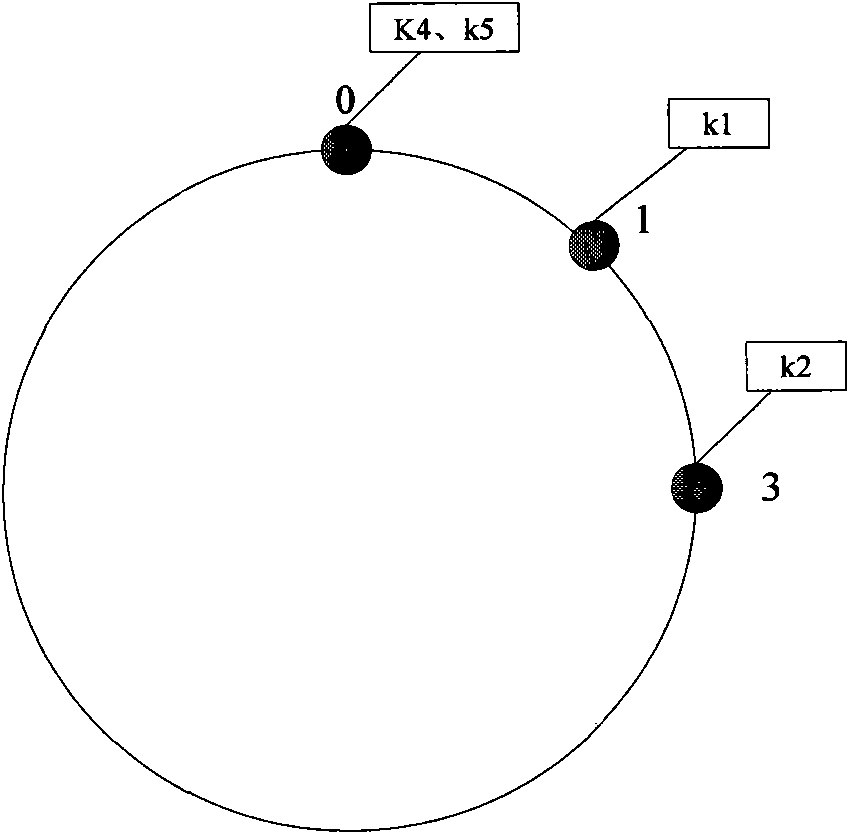
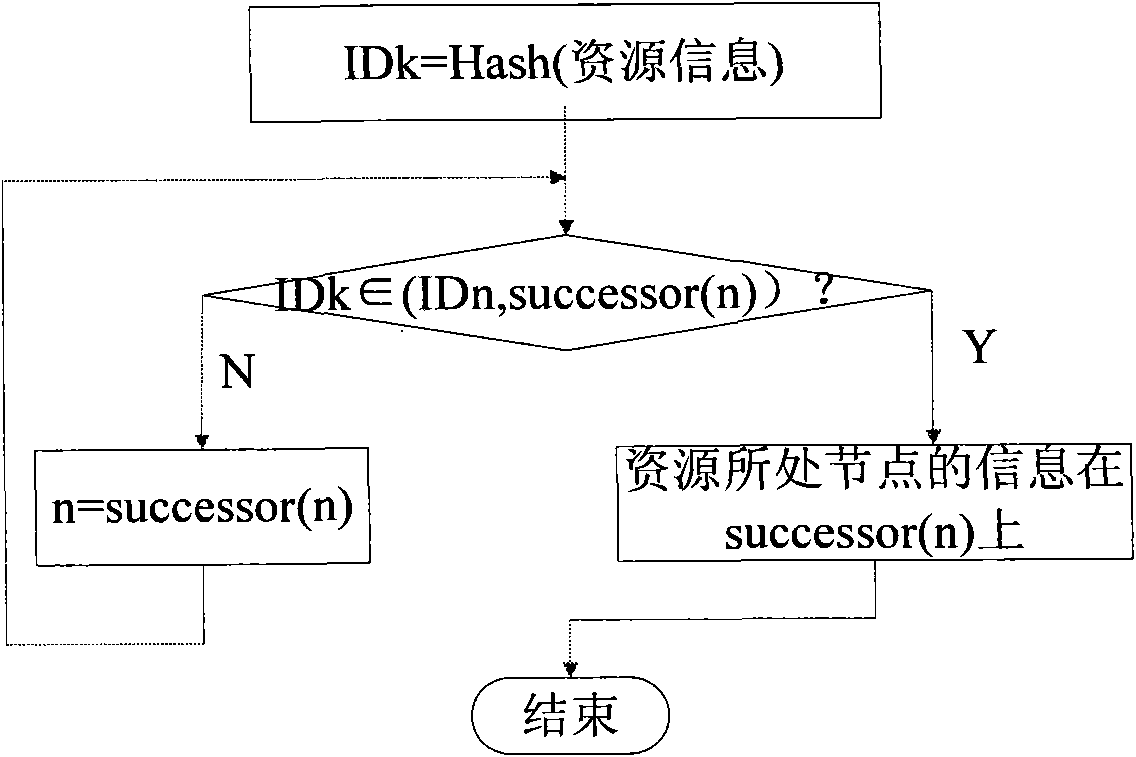
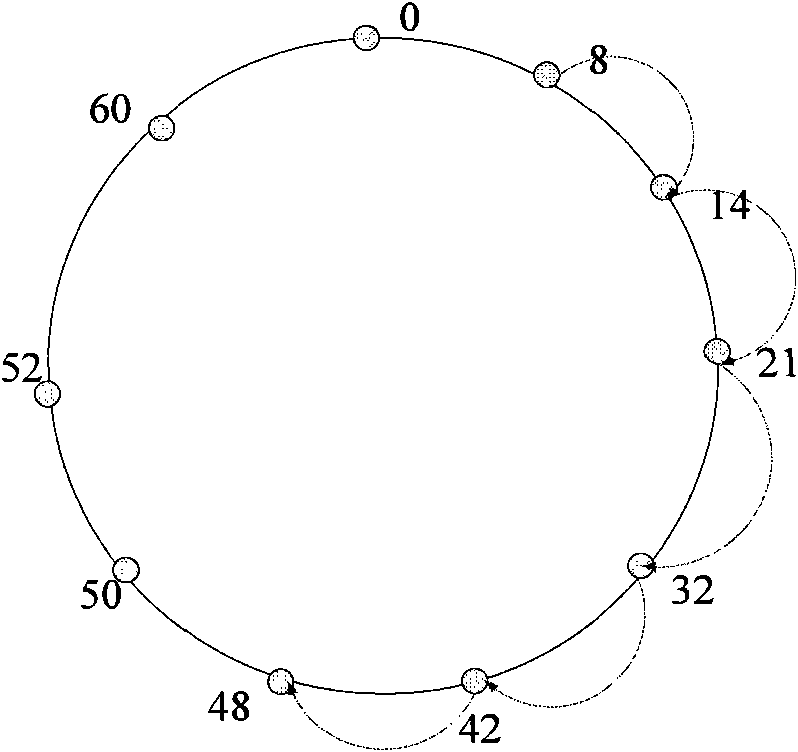
InactiveCN101917475ADoes not increase in lengthComputational work simplifiedTransmissionHash functionPeering
The invention relates to a P2P (Peer-to-Peer) mode based PSRD (Program Support Requirements Document) universal service resource discovery method, comprising the following steps of: carrying out hash operation on targets (names or descriptions of resources and IP addresses of nodes) through hash functions, wherein the result of the hash operation is an m-digit binary identifier ID which is respectively recorded as IDk=Hash (the names or the descriptions of the resources) and IDn=Hash (IP), and the value range of the IDn is [0, 2m-1]; arraying the IDn from 0 to 2m-1 into a circle according to a sequence from large to small so as to form distributed structuring network node rings, wherein each structuring network node ring stores a subsequent node; mapping a given target to a certain peering point of a network, wherein the peering point stores a (IDk, Value) pair, the IDk is a hash value of a resource to be searched, and the Value is the actual storage position of the resource to be searched; when searching the resource, directly inquiring in a local pointer gauge, and directly spanning a plurality of nodes to reach a destination node or a node near the destination node till the resource is found or corresponding error handling is carried out.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
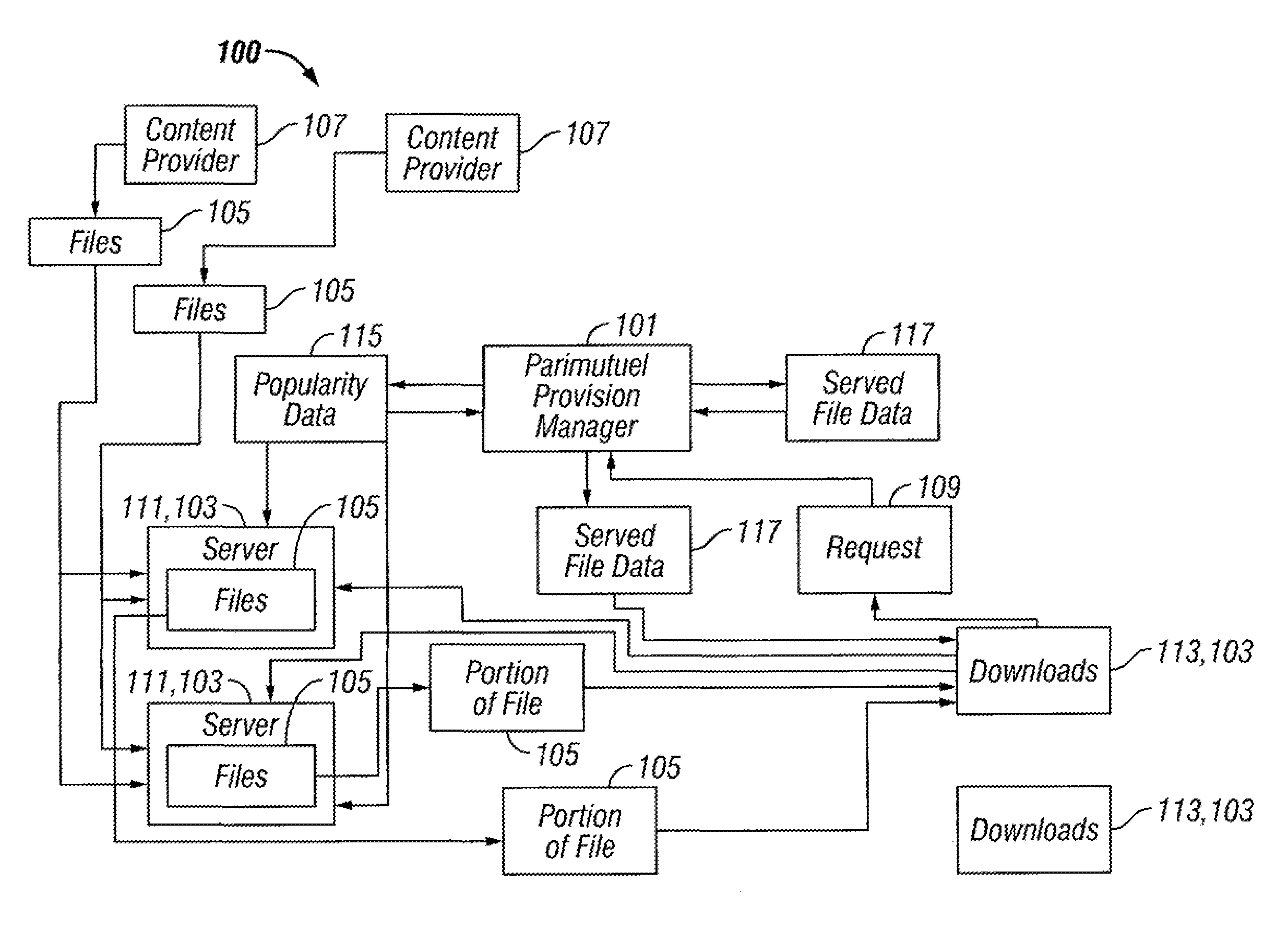
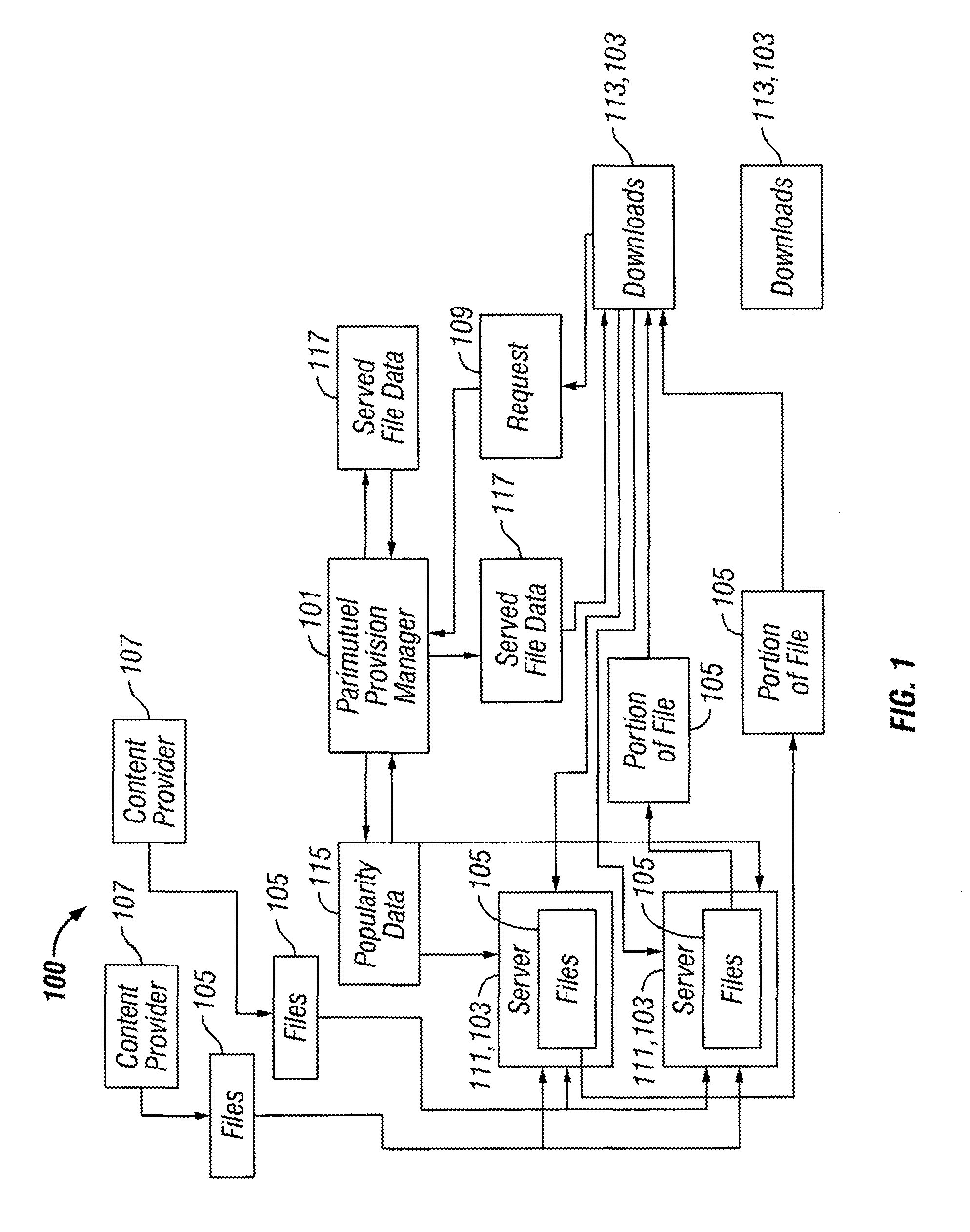
Parimutuel content provisioning
ActiveUS7707215B1Significant revenueWide diversityDigital data information retrievalDigital data processing detailsSupply managementData mining
A parimutuel provision manager provides an efficient incentive mechanism for content provision on peer-to-peer systems. The parimutuel provision manager generates a wide diversity of content offerings while responding adaptively to customer demand. Files are served and paid for through a parimutuel market similar to that commonly used for betting in horse races. An analysis of the performance of such a system shows that there exists an equilibrium with a long tail in the distribution of content offerings, which guarantees the real time provision of any content regardless of its popularity.
Owner:VALTRUS INNOVATIONS LTD +1
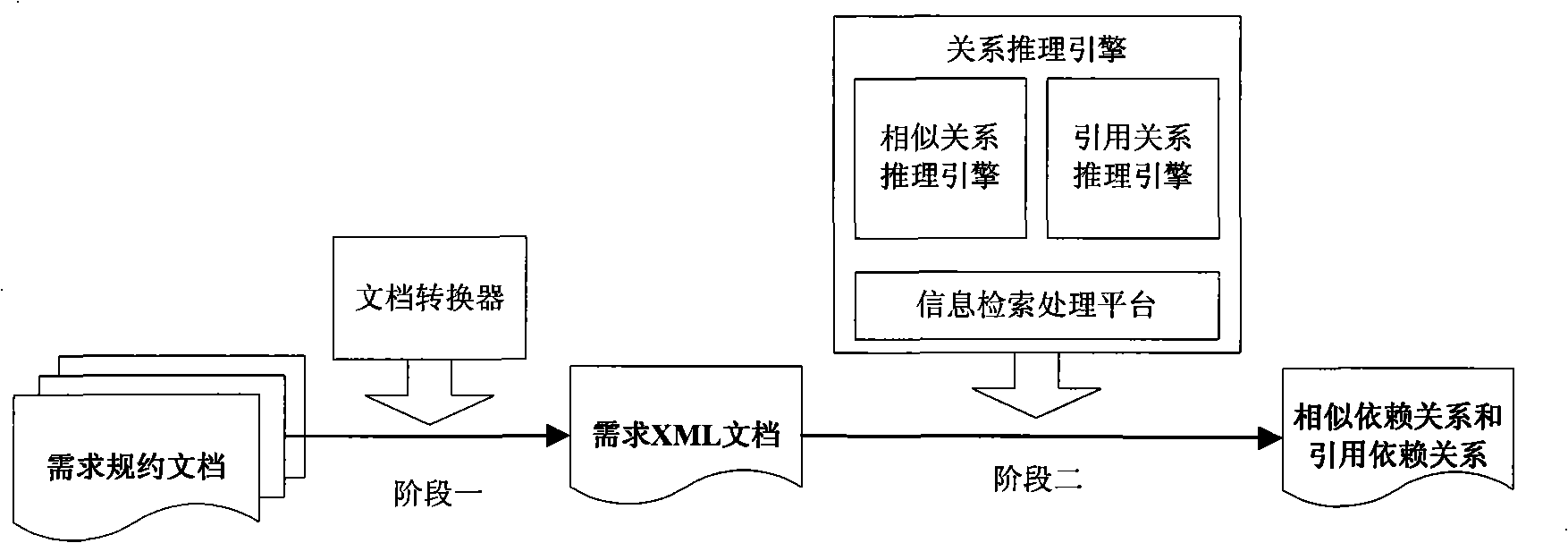
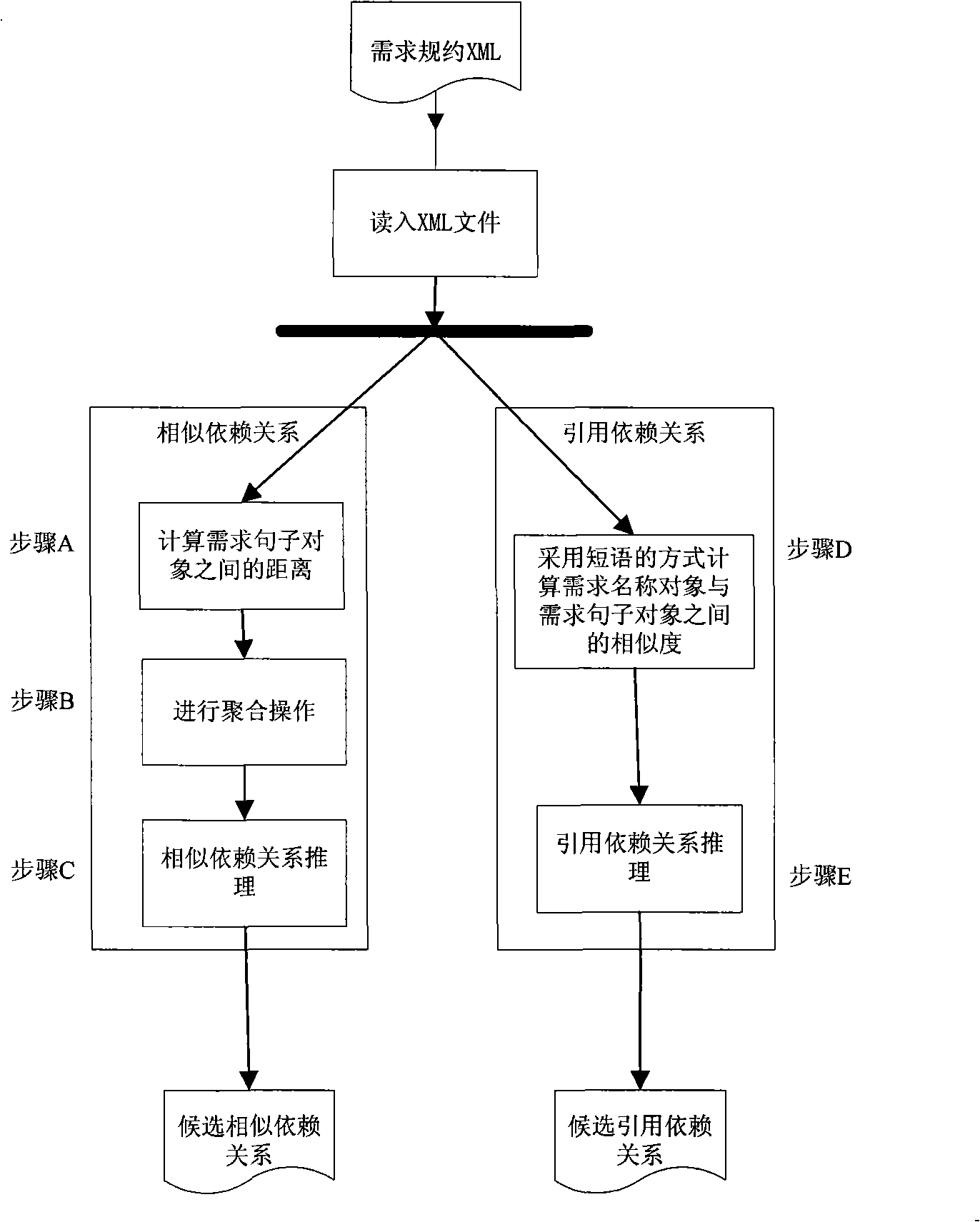
Method for automatic recognition for dependency relationship of demand
InactiveCN101334793AImprove efficiencySpecific program execution arrangementsSpecial data processing applicationsComputer Software EngineeringSpecification document
The invention belongs to the computer software engineering field and particularly relates to a method adopting an information searching technique to automatically identify dependencies between requirements from requirement specification documents described in natural language. The invention mainly focuses on the requirement document specification described in natural language to analyze and generalize the type of dependencies specially associated with requirement evolution and simultaneously puts forward a method used for automatically identifying the dependencies between requirements. The invention automatizes the identifying of requirement dependencies, which largely enhances the labor efficiency and reduces work intensity while identifying the requirement dependencies and greatly eliminates mistakes easily made by people during identifying process and also enhances the accuracy and stability of the identified dependencies.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
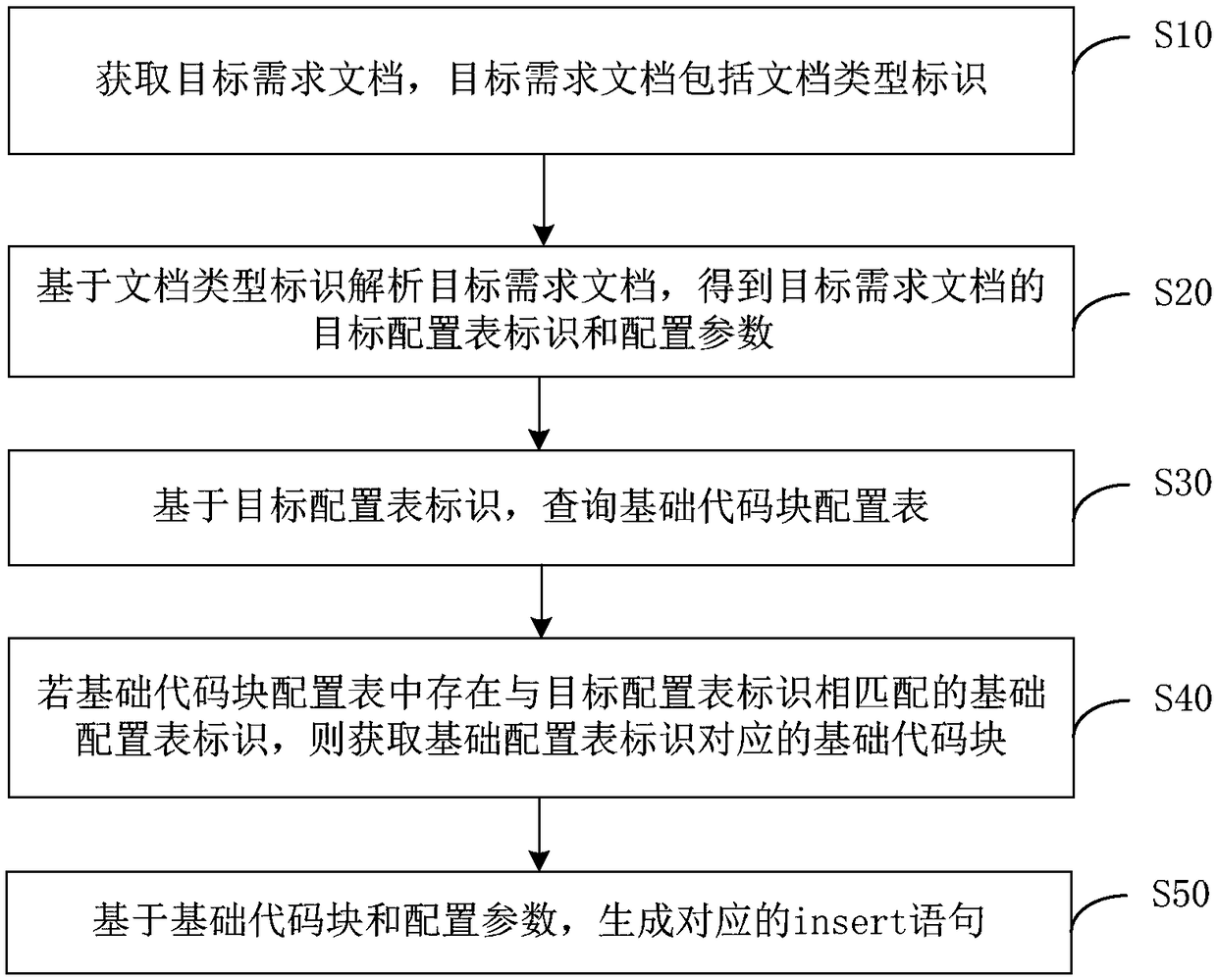
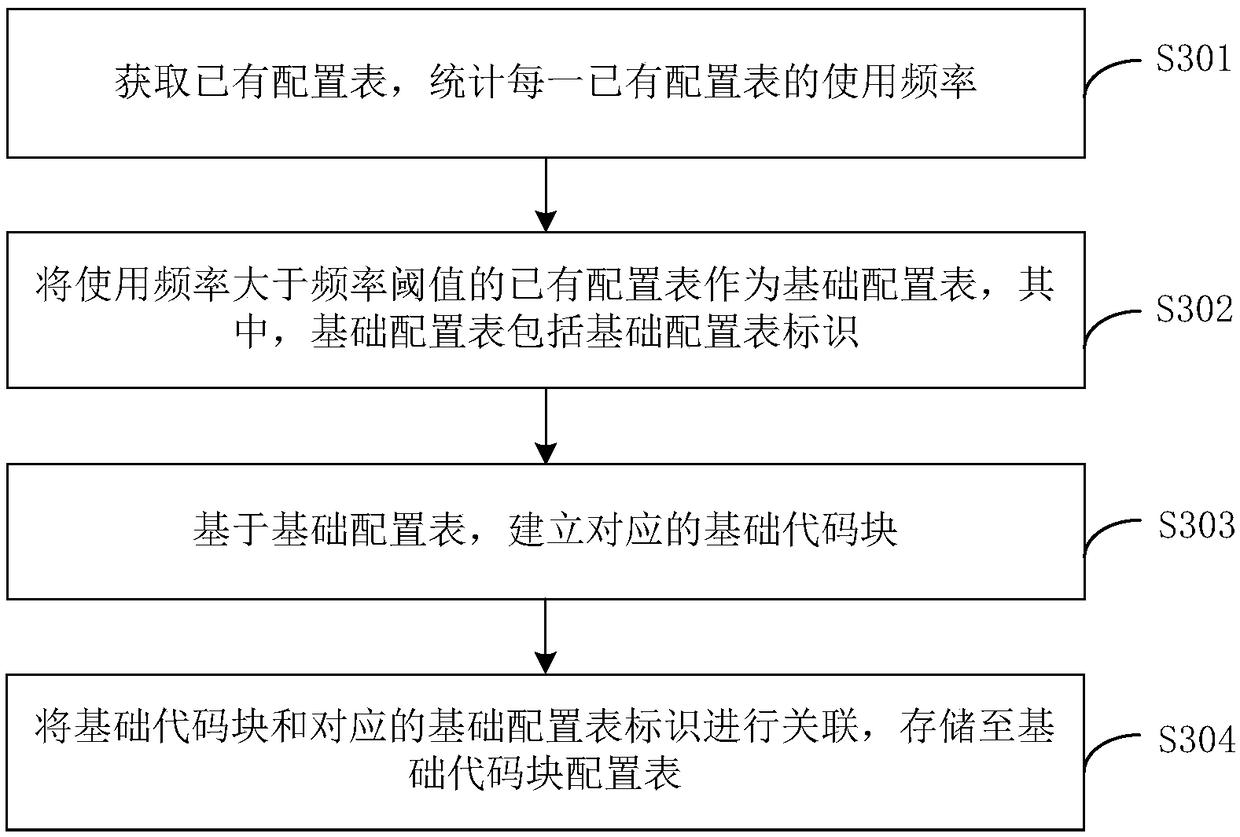
Method, apparatus, computer device and storage medium for automatically generating insert statement
ActiveCN109062925AImprove reusabilityImprove efficiencySpecial data processing applicationsCoding blockReusability
The invention discloses a method, a device, a computer device and a storage medium for automatically generating an insert statement. The target requirement document is parsed based on the document type identification, and the target configuration table identification and configuration parameters of the target requirement document are obtained. The method comprises querying a basic code block configuration table based on a target configuration table identifier; obtaining a basic code block corresponding to the basic configuration table identifier if there is a basic configuration table identifier matching with the target configuration table identifier in the basic code block configuration table; based on the underlying code block and configuration parameters, the corresponding insert statement being generated. The technical proposal of the invention achieves the effect of improving the efficiency of generating insert statements by adopting the method of automatically generating insert statements based on the configuration parameters and the basic code blocks, thereby effectively improving the reusability of the basic code blocks.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com