Disk lock management method and device
A management method and a technology of a management device, which are applied in the field of disk lock management methods and devices, and can solve problems such as file system read-only, data inconsistency, and server downtime
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
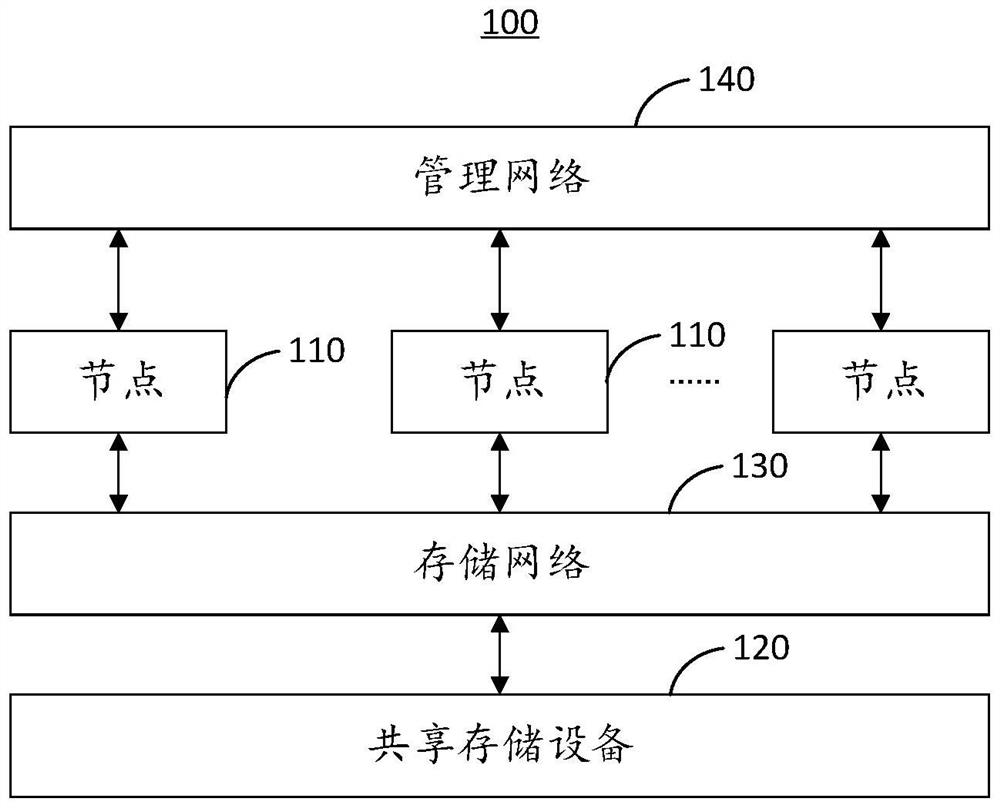
[0045] The embodiment of the present invention provides a disk lock management method, which is applied to the first node of the shared file system 100, and the first node communicates with the second node of the shared file system 100 to avoid data lock caused by processing expired messages. Inconsistencies, read-only file systems, or server downtime.
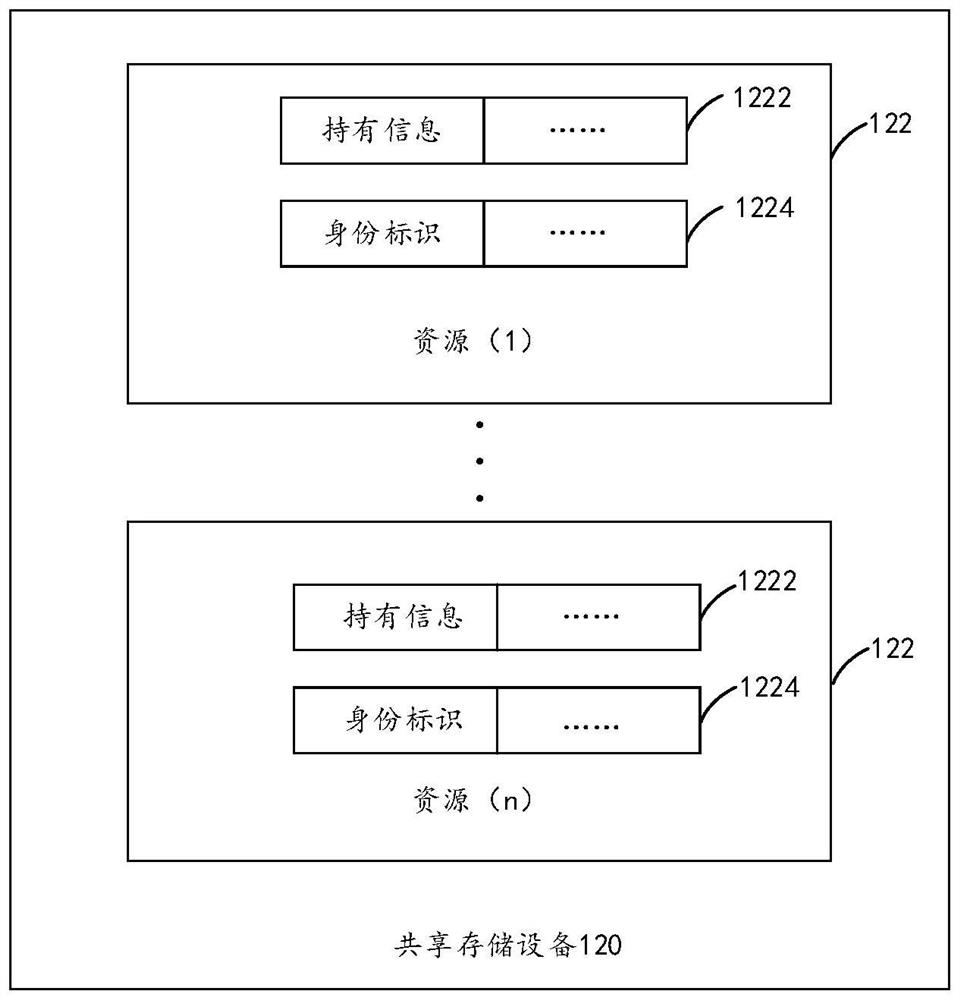
[0046] It should be noted that the second node in this embodiment is the node 110 that initiates an access request to a certain resource 122 of the shared file system 100, and the first node is the node 110 that holds the disk lock 1222 corresponding to the resource 122 .
[0047] It should also be noted that, in other embodiments, the second node may be the node 110 holding the disk lock 1222 corresponding to the resource 122, and the first node may be a resource 122 that initiates an access request to the shared file system 100 Each node 110 can be a node 110 that initiates an access request to a certain resource 122 of the...
no. 2 example
[0069] The embodiment of the present invention provides a disk lock management method, which is applied to the second node of the shared file system 100, and the second node communicates with at least one first node of the shared file system 100, so as to avoid data inconsistency, file system read-only, or server downtime.
[0070] It should be noted that the second node in this embodiment is the node 110 that initiates an access request to a certain resource 122 of the shared file system 100, and at least one first node is mounted on the same shared file system as the second node The nodes 110 of 100 are the nodes 110 belonging to the same cluster. In addition, there may be a node 110 holding the target disk lock corresponding to the resource 122 in at least one first node, or there may not be a node 110 holding the target disk lock corresponding to the resource 122 .
[0071] see Image 6 , is a flow chart of the disk lock management method provided by the embodiment of th...
no. 3 example
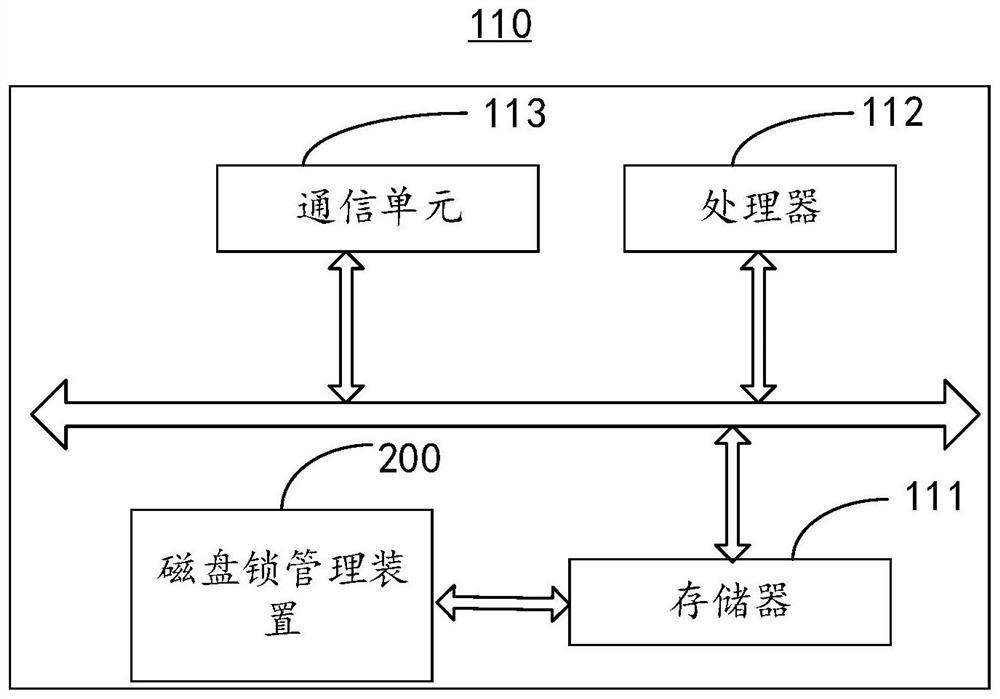
[0094] The embodiment of the present invention provides a disk lock management device 200. It should be noted that the basic principles and technical effects of the disk lock management device 200 provided in this embodiment are the same as those of the first embodiment. For a brief description, For parts not mentioned in this embodiment, reference may be made to the corresponding content in the first embodiment. see Figure 7 , is a functional block diagram of the disk lock management device 200 provided by the embodiment of the present invention, the disk lock management device 200 includes: an information receiving unit 210, an analysis unit 220, a reading unit 230, a judging unit 240, and a disk lock management unit 250.
[0095] The information receiving unit 210 is configured to receive an unlock request transmitted by the second node based on the logical block address of the target disk lock and the first identifier of the resource 122 corresponding to the target disk l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com