An authentication configuration method, device and computer-readable storage medium
A technology of identity verification and configuration method, which is applied in the field of information security, can solve problems such as not being identical, business systems accessing each other is complicated, etc., to solve development problems, avoid the process of version release, and reduce the effect of high error rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Embodiments of the identity verification configuration method, device and computer-readable storage medium of the present invention will be described below with reference to the accompanying drawings. Those skilled in the art would recognize that the described embodiments can be modified in various ways or combinations thereof without departing from the spirit and scope of the invention. Accordingly, the drawings and description are illustrative in nature and not intended to limit the scope of the claims. Also, in this specification, the drawings are not drawn to scale, and like reference numerals denote like parts.
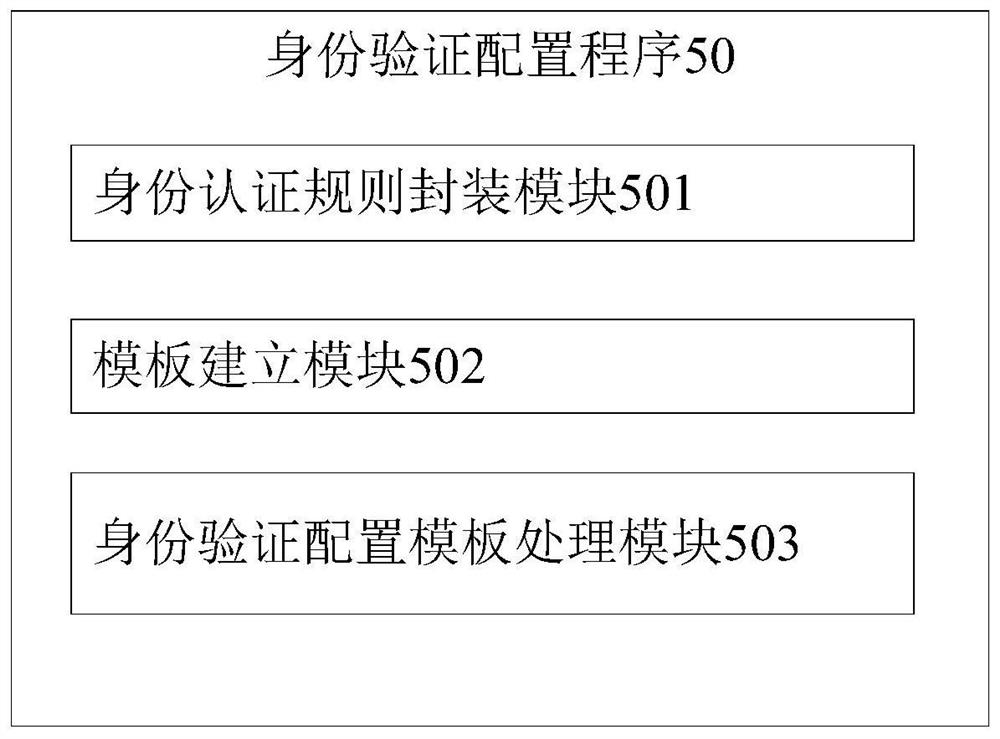
[0020] An authentication configuration method such as figure 1 shown, including the following steps:
[0021] Step S10, encapsulating the data models of the encryption rules, decryption rules, signature rules, and signature verification rules in the FreeMarker template engine, so as to replace the content in the interpolation symbol ${} in the later stag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com