Handling sensitive data in application using external processing
A technology for sensitive data and applications, used in digital data protection, electrical digital data processing, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
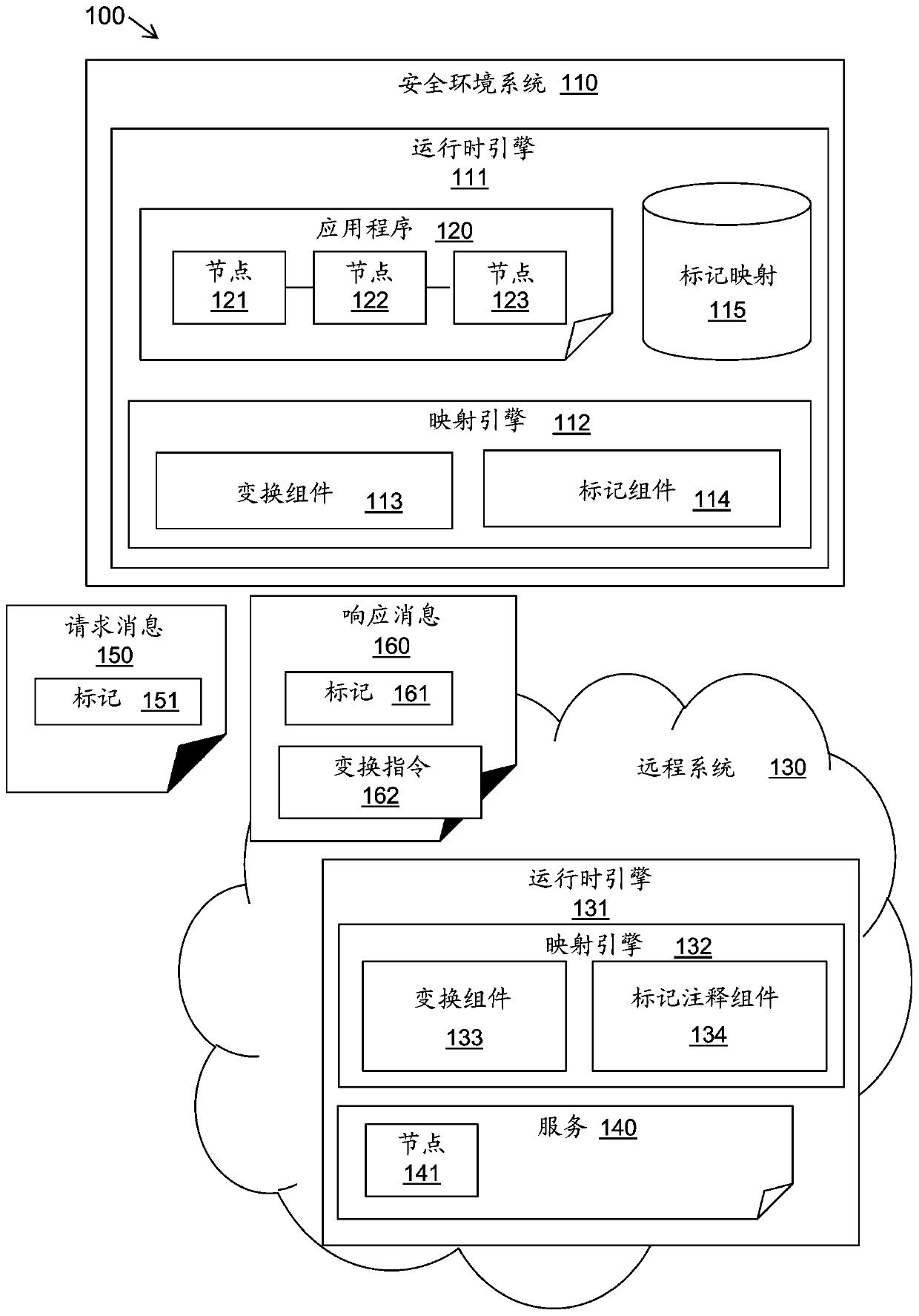
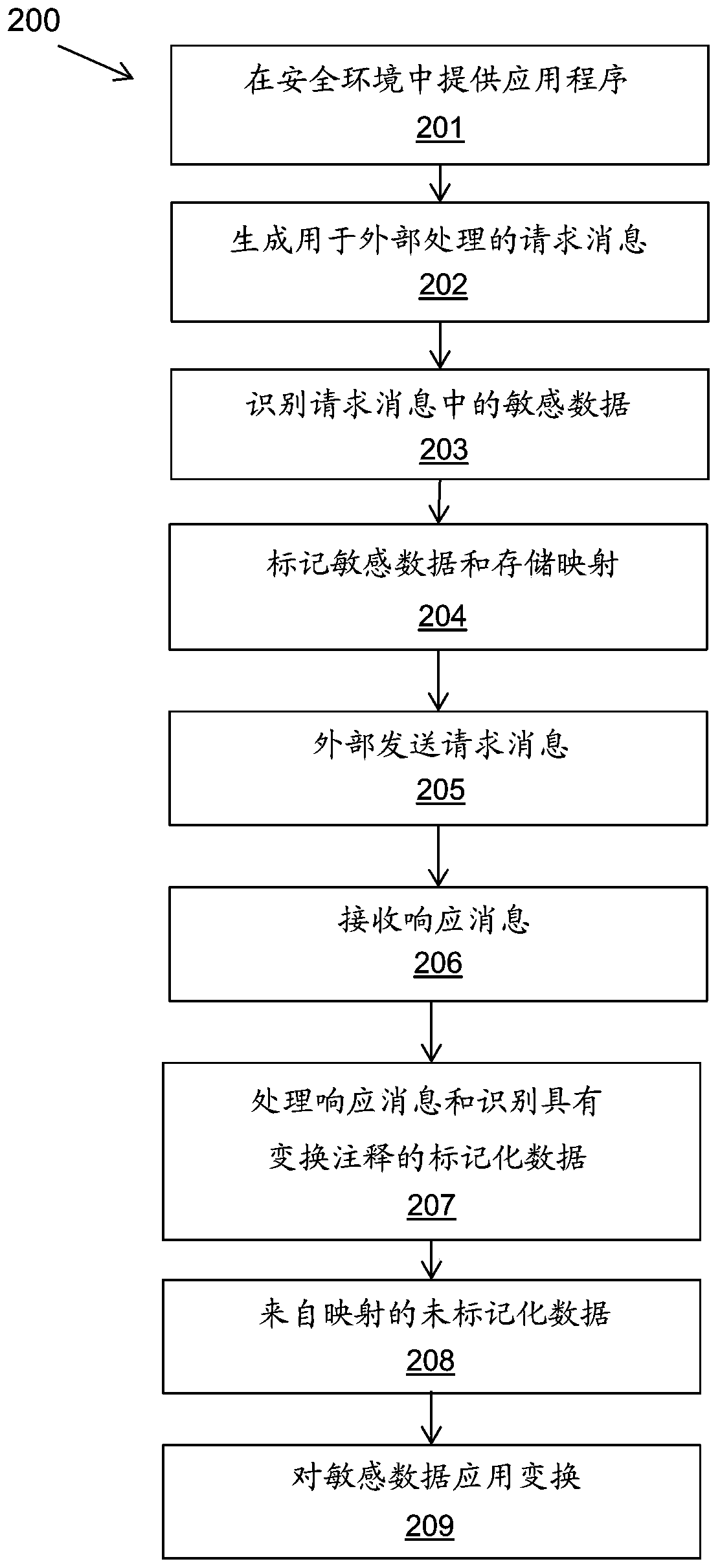
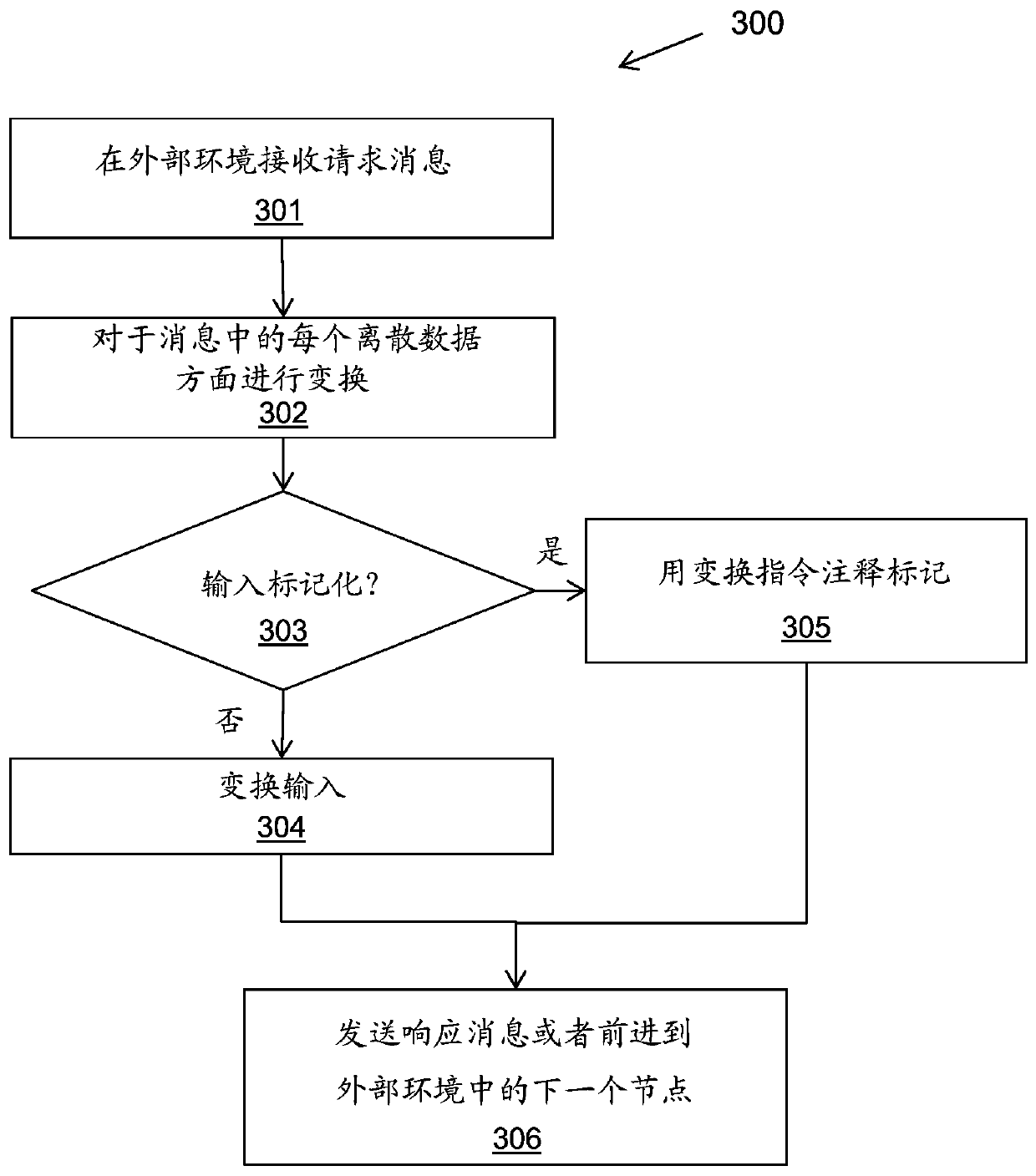
[0038] The described methods and systems enable the use of external processing to process sensitive data in applications. The method enables the use of a remote entity, such as in a cloud, distributed environment or other external processing environment, to perform processing of the integrated stream without any sensitive data leaving the secure processing environment.
[0039] In one embodiment, cloud-provisioned compute instances can be used to perform bulk processing of existing integration flows without any sensitive data leaving the enterprise's on-premises data center.
[0040] refer to figure 1 , a block diagram illustrating an example environment 100 in which the described system may be implemented. The secure environment system 110 may be provided, for example, in the form of a locally deployed computing system or a network of systems. Such a secure environment system 110 may be protected by firewalls and other security measures to ensure that confidential or sensit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com