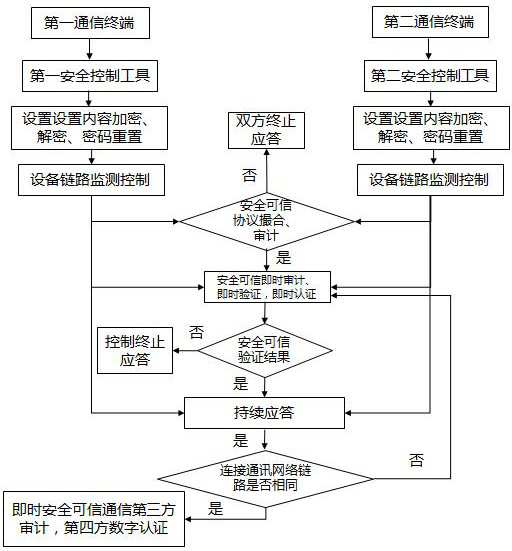
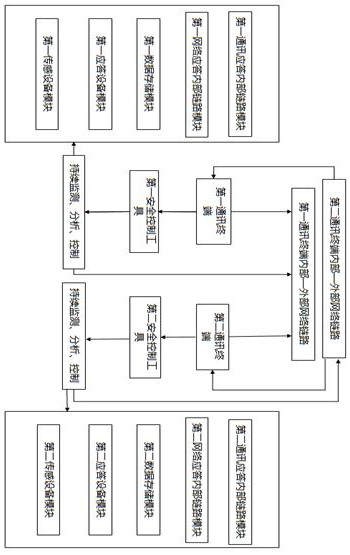
Today's network servers all use dynamic IP, which makes the
information transmission and information verification links uncertain, and the information response link is easy to be tampered with. It is difficult to trace the spatial location of the starting point and end point of the information of both parties in the dynamic IP network space. Tracing cybercriminals; for example, the
MAC address, IPV4, and IPV6 codes displayed by
smart phone terminals in multi-dimensional communication methods lack intuitive data of geographic spatial locations, and the response channels of different network communications access remote servers, so that when displaying the same remote content or accessing In the case of the same remote
server, there is uncertainty in the response link of
cellular communication and
wireless LAN communication inside the communication terminal, and the response link can be tampered with as the IP changes dynamically, making it difficult to trace the real response link and response equipment;
Internet communication through WWW. The address analyzed by the communication protocol is a discrete mathematical code, and the
information transmission and information verification between communication terminals are missing. The security control method based on the geographical space location link, the information verification communication usually adopts the short message channel, and the short message information verification link and The inconsistency of APP data network transmission links does not take security control on the starting point and end point of the response link, and there is no security
control measure in the interception state; at present, 2G SMS
communication channel verification is widely used, and the verification information is easily intercepted and the verification result is easily tampered with. Fraudsters intercept and obtain the 2G data of APP users by luring and sniffing the SIM card
mobile phone number and identity information bound to APP users, illegally making fake base stations, and blocking the 3G, 4G, and 5G signals of SIM card mobile phones bound to users. The short message verification code of the
communication channel implements financial infringement on APP users, and cannot trace the source to make it more serious;
[0004] 2) Lack of automatic
continuous monitoring that can realize
adaptive security protection based on information response and verification link consistency, information security control link consistency technology solution trend, information response, verification, and transmission process have potential safety hazards of tragic tampering of communication channels
At present, the whole process
security management security control technology scheme for the link of internal response and external response of intelligent communication terminals has not been made public; the
information transmission (network, cellular channel) and information verification link (SMS channel) are inconsistent
Verification and
password retrieval are ubiquitous; in the face of intelligent communication terminals, it is compatible with multi-mode response of network information, response of
multimedia sensor information, reading of various data storage devices, and response of saved information, compatible with multi-communication cards of different operators. Standard mobile phones face
information security management blind spots such as separate operations of
mobile phone manufacturers,
telecom operators, and
network service providers. Smart terminals have blind spots in the security management of internal information response links and external information response links; overlord clauses involved in APP downloads The private information of the
mobile phone holder is stolen and leaked, especially the
smart phone has a multi-mode channel mode, compatible with 2G, 3G, 4G, 5G, WIFI,
satellite communication, camera,
microphone,
infrared,
Bluetooth, NFC,
flash memory, plug-in Hard disk and other external multi-mode communication responses, multi-mode
information storage and reading responses internally, and multi-channel sensing and sensing
signal responses through sound, image, etc., there are hidden dangers of self-
adaptive security management of information security, such as through Incidents of property being transferred due to the use of free public WIFI often occur; communication products and security protection products related to the
general method of self-
adaptive security control have no substantive breakthroughs and popularization and application; verify that the SMS channel is blocked during the peak period of concurrent messages, and the verification information
Verification is delayed and sending is delayed, and the
valid time of
user input verification code is often invalid due to acceptance waiting
timeout, which affects the experience effect;
[0005] 3) At present, the general communication verification technology scheme is difficult to realize the communication technology of safe and credible real-time verification in the public communication network, and there is a lack of real-time safe and credible verification technology support for blockchain verification
In terms of passive response, the unfamiliar active response request is in an unsafe and unreliable instant response and communication state; the existing
instant messaging information response lacks the online
continuous monitoring and security of the information transmission link and verification link consistency of the location space of both parties. Self-adaptive security control measures,
online security responses between responding parties, trusted real-time verification technical solutions are not disclosed, verification communication channels are inconsistent with
software data transmission channels, and verification links can be tampered with, causing great security risks
The online credible verification of empirical
big data carried out by enterprises such as Number Bestone is a
big data application collected offline, and there is an information security problem that the successful time of offline
big data collection is seriously delayed and the online
application time is delayed, which cannot meet the requirements of information security for real-time security. The real-time conditions for letter verification, safe and reliable
instant messaging cannot provide services online in the existing communication service network; it is precisely because there is no safe and reliable instant messaging service, and the existing information response link and information verification link are not real-time The technical solution cannot ensure the value transfer of online safe and credible real-time verification of the blockchain, and the lack of real-time safe and credible verification technology in response to the instant messaging links relied on by both parties further leads to telecom fraudsters relying on the current
network communication to carry out crimes, and the traces of crimes are difficult to detect. retrospective;
However, in the face of the emergence of tamperable IP addresses, tamperable device codes, dynamic IP, distributed
server architecture, smart phones that support multi-mode, multi-dimensional, multi-channel, and intelligent communication terminals, in response to the inconsistency of the IP addresses of the devices at both ends Change, the address of the physical response device remains the same as the logical deduction of the "three-way communication
handshake" communication logic and safe and credible real-time verification. This will directly lead to the lack of verification of the uniqueness of the communication network link
transponder in the traditional secure and trusted instant messaging through the "three-way communication
handshake" communication method, and the network transmission link between communication terminals cannot be proactive. The whole link and the whole process
security monitoring between the responder node of the requesting party and the responder node of the passive responder, there are serious security risks that the information response equipment can be tampered with, and the information response and information verification link can be tampered with; communication The transmission link of verification information between terminals cannot achieve the full link and whole process
security monitoring between the responder node of the active requester and the responder node of the passive responder. During the information transmission process, the information transmission chain The road and information verification link have potential safety hazards that can be tampered with in the middle; the network link of information transmission is inconsistent with the verification link of information security and credible instant verification! In the face of dynamic IP and distributed architecture
server layout, the traditional "three-way communication
handshake" method lacks the uniqueness of the response equipment at both ends, and the uncertain security logic basis, the traditional "three-way communication handshake" method logic and Theoretically, the pre-unique security premise cannot be guaranteed and the whole process monitoring and security control cannot realize the real safe and trusted channel verification! At the same time, network IP and device addresses are symbolic addresses, not geographical spatial locations. In the traditional "three-way communication handshake" method, the responding device can be tampered with, the network transmission link can be tampered with, and the communication terminal participating in the response can be tampered with. The uniqueness, authenticity, and non-tamperable modification of the information transmission link and information verification link cannot be guaranteed! Since the
computer design framework only has the time dimension, and the keyboard does not exceed 108 symbols, the technical ideas of information security experts are running along the
keyboard design scheme and the traditional computer
physical design framework scheme. The information security technology scheme does not jump out of the computer framework. The security problem of lack of geographical location in design, the fundamental problem of the
security design of missing
password design and storing passwords, and retrieving password geographic location! In the face of the experimental use of digital renminbi, if the traditional "three-way communication handshake" method is further used for secure instant verification technology solutions and the traditional
security design idea is followed, it cannot fundamentally solve the possible existence of two different transponders corresponding to any two communication terminals. Changes in "True and False Monkey King" and technical issues in the identification of real and fake communication terminal subjects!
[0008] 6) The
virus database update technology of the existing firewall is not updated immediately. It is common to update the
virus database every few days. The security of the firewall is delayed due to the update of the
virus database, and there are technical shortcomings in ensuring the security of the network space. Hidden dangers
 Login to View More
Login to View More  Login to View More
Login to View More