Persistent identity authentication method and system based on different contexts
An identity authentication and context technology, applied in the field of continuous identity authentication methods and systems, can solve problems such as the inability to effectively verify the current user, and achieve the effect of ensuring authentication accuracy and improving responsiveness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] Judging whether the current user is a new user according to the user login information, first judge whether the current user is a new user, if it is a new user, construct a user model of a legal user based on legal context information, keystroke behavior and mouse behavior, and then construct a legal user's user model User models include:
[0043] Read the standardized feature vector corresponding to the user ID in the database, and construct a label for the user according to the standardized feature vector; use the user label attribute and user ID to construct three training sets: the training set of the user's keystroke behavior characteristics, and the user's mouse behavior characteristics. The training set and the feature-level fusion training set of user keystrokes and mouse behavior features; use the training set of user keystroke behavior features, the training set of user mouse behavior features, the training set of user feature-level fusion and user context info...
Embodiment 2
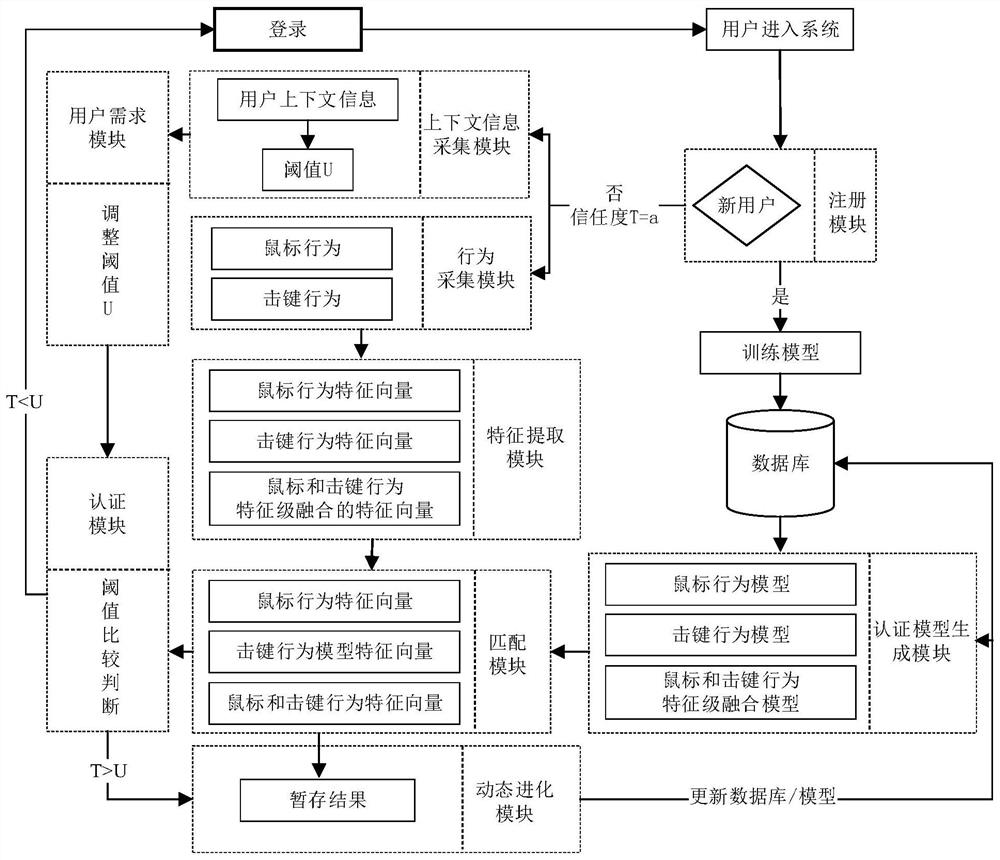
[0054] Such as figure 1 , the identity authentication system used in the present invention includes a user's PC device and a server.
[0055] The user's PC device includes: a registration module, a context information collection module, a behavior collection module, a feature extraction module, a matching module, a user requirement module, an authentication module and a dynamic update module.
[0056] Registration module: determine whether the current user is a new user;
[0057] Context information collection module: collect the context information of user login, and calculate the threshold U of different context environments;
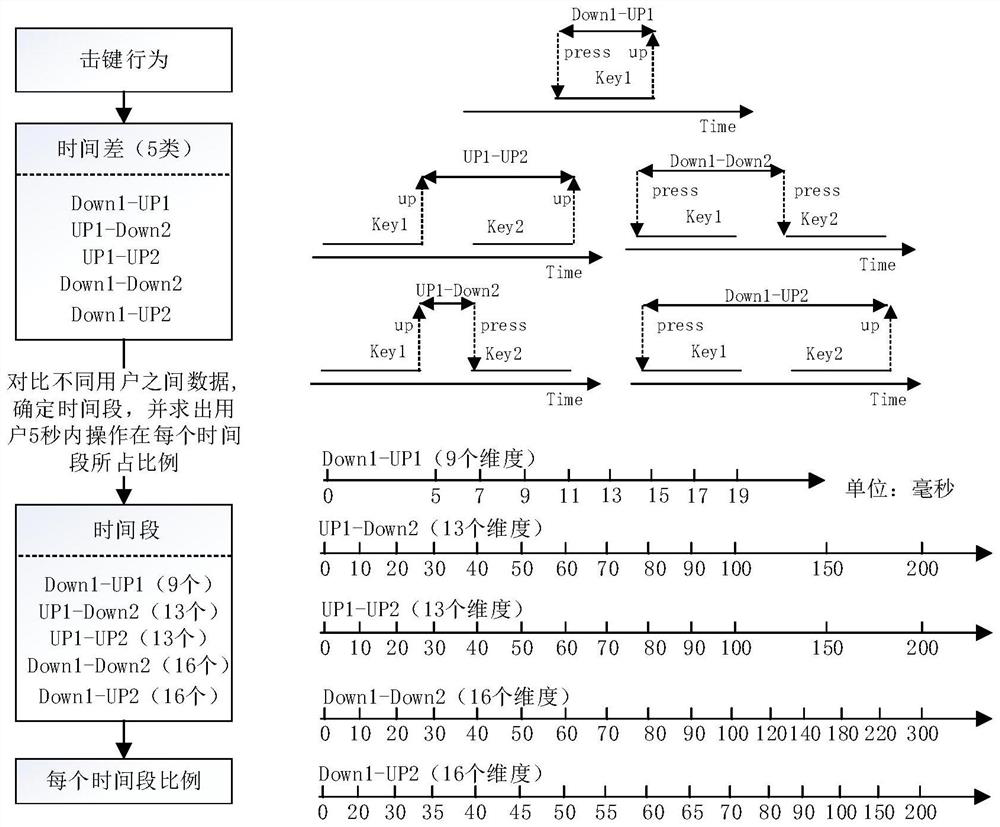
[0058] Behavior collection module: collect keystroke and mouse behavior characteristics of users in the system;
[0059] Feature extraction module: convert the user's keystroke and mouse behavior features into behavior vectors;
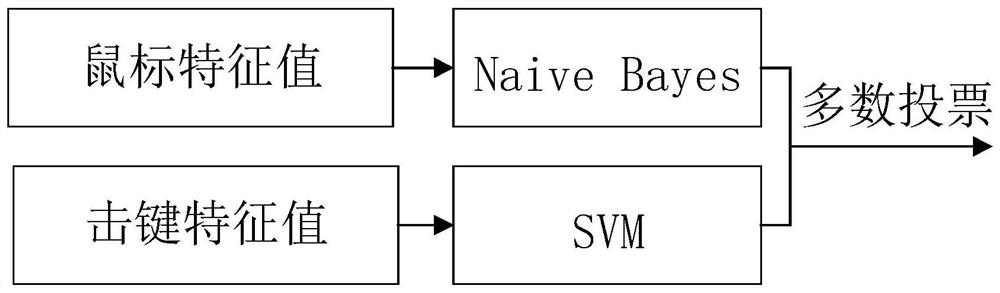
[0060] Matching module: match whether the user behavior feature vector is the current user, and calculate the credibilit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com