HTTP flood attack defense method and system
A flood attack and defense system technology, applied in transmission systems, electrical components, etc., can solve problems such as inability to effectively defend against flood attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
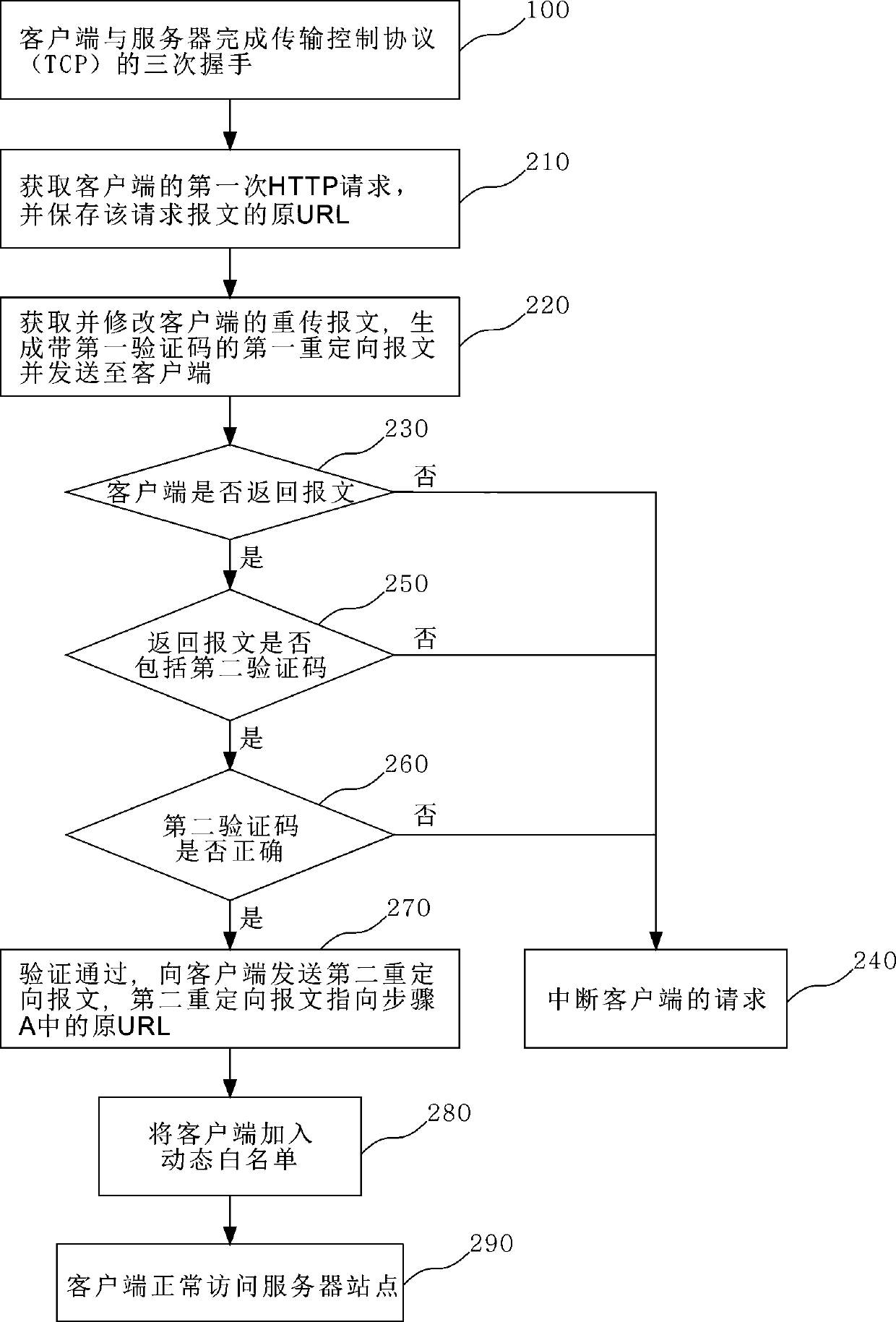
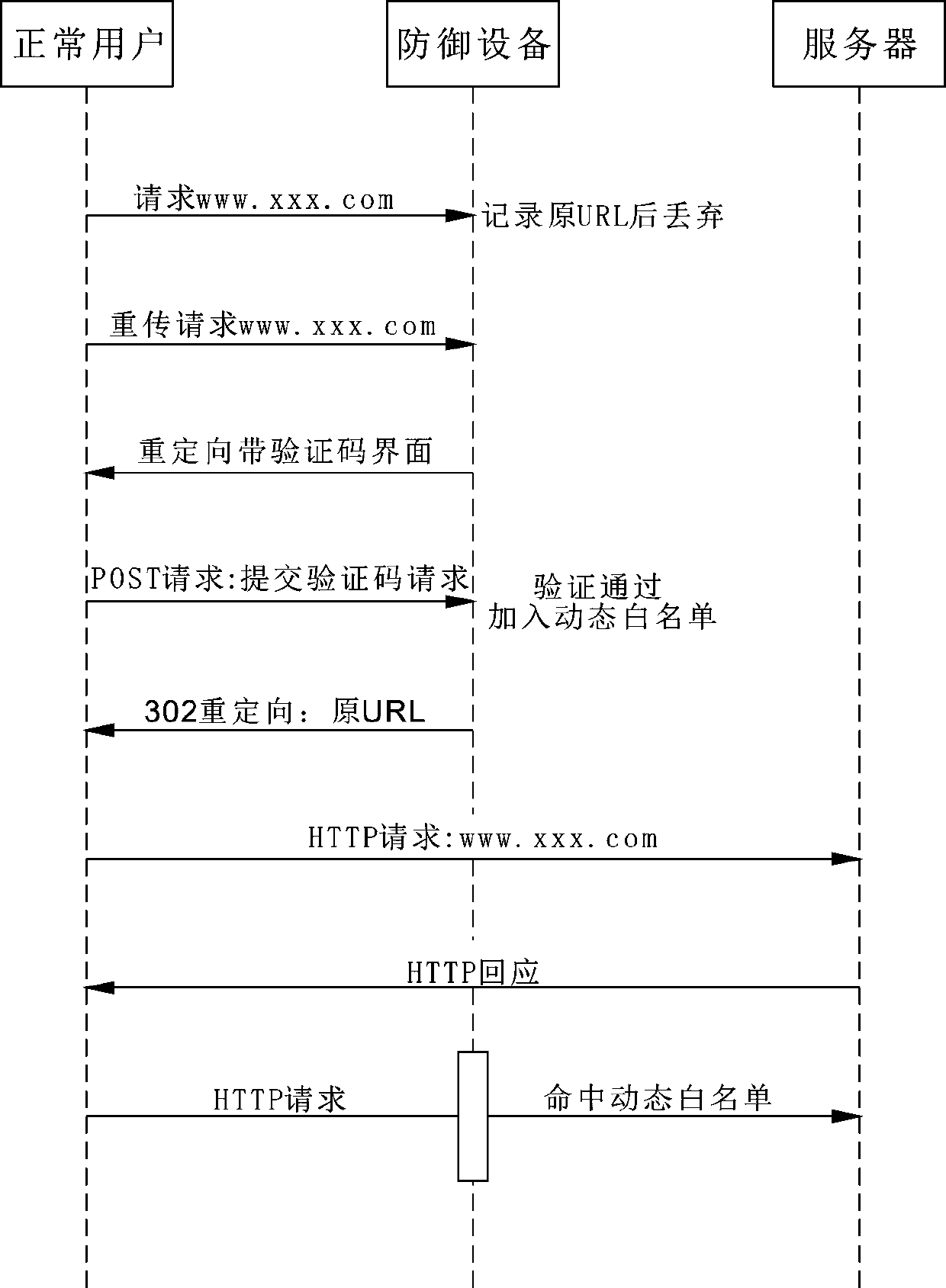
[0049] Such as figure 2 As shown, the verification process for normal users,
[0050] First, the defense device intercepts the first HTTP request of a normal user (request to visit "www.xxx.com"), records the original URL and discards the message.
[0051] Second, the verification process includes:
[0052] After a normal user re-initiates a request, the defense device transforms the retransmitted message, adds a random verification code, and redirects the request to the verification interface;
[0053] Normal users enter the correct verification code in their browser and submit it to the defense device for verification. If the verification passes, the normal user (device) information will be added to the dynamic white list;
[0054] The defense device redirects the saved original URL (initial target URL) of the normal user to the user.
[0055] Finally, normal access is realized between the user and the server, because the user (device) has been added to the whitelist, an...
Embodiment 2
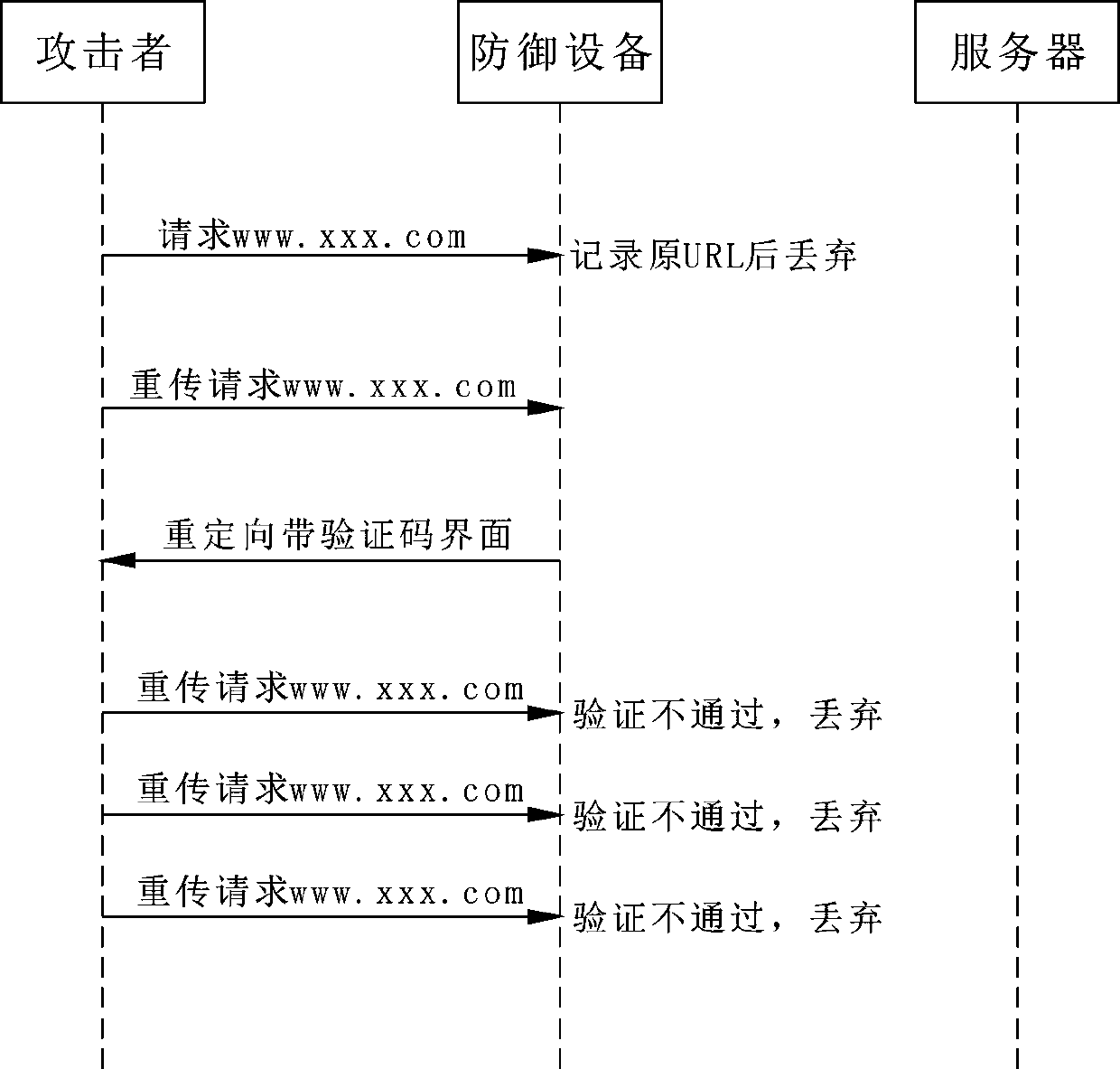
[0057] Such as image 3 As shown, the defense process against attackers.
[0058] First, the defense device intercepts the attacker's first HTTP request (request to visit "www.xxx.com"), records the original URL and discards the message.
[0059] Second, the defense process includes:
[0060] After the attacker re-initiates the request, the defense device transforms the retransmitted message, adds a random verification code, and redirects the request to the verification interface;
[0061] Because the HTTP flood message sent by the attacker does not have the function of viewing the corresponding verification code or returning the correct random verification code, but repeatedly initiates requests to access "www.xxx.com";
[0062] Because the correct verification code was not sent back, the attacker (device) could never pass the verification of the defense device, and the defense device discarded the request packets initiated by it;
[0063] If the attacker (device) still fa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com