Security risk identification method and device, equipment and storage medium
A security risk and risk identification technology, applied in the network field, can solve problems such as company losses, and achieve the effect of accurate analysis results, convenient risk control and management optimization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
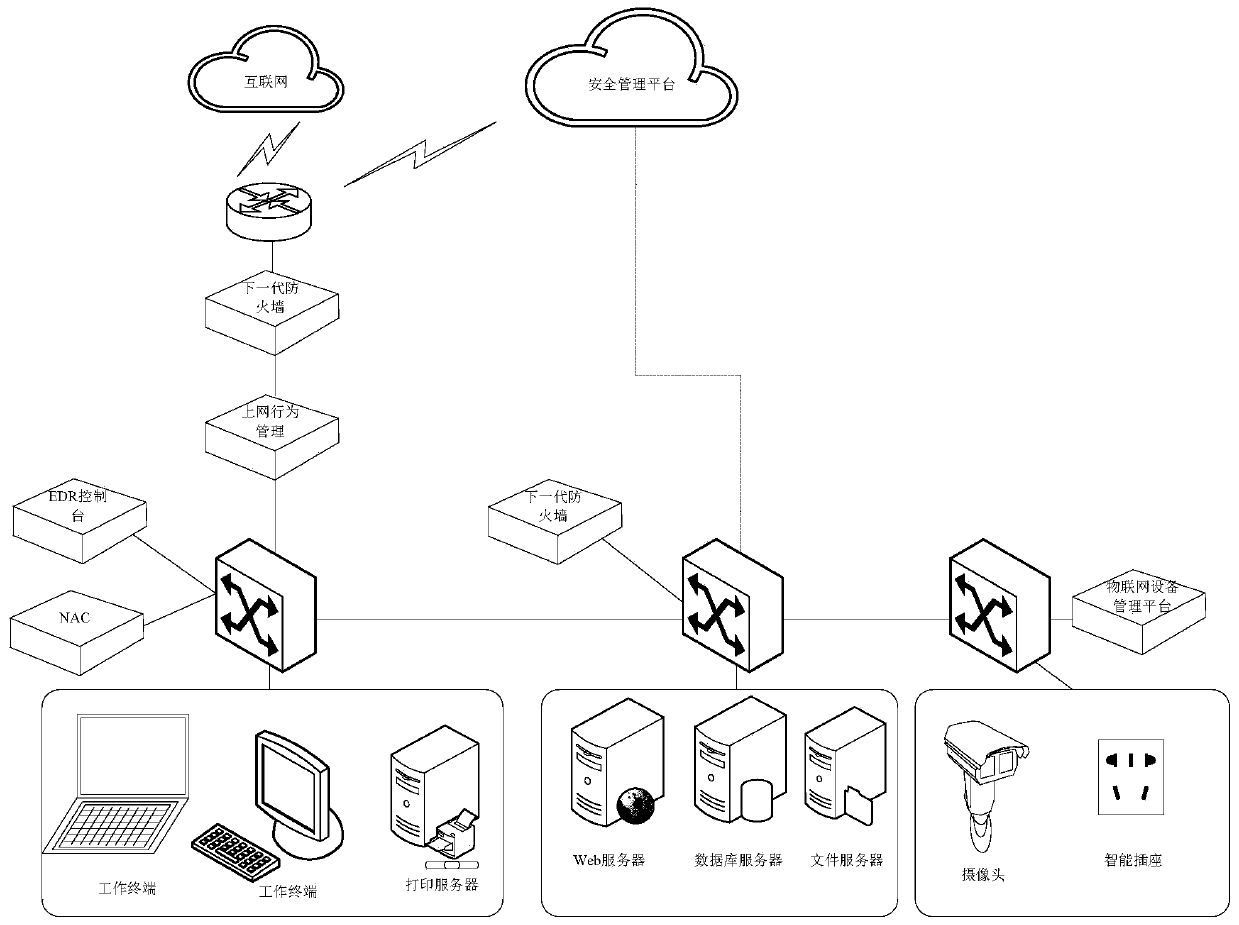
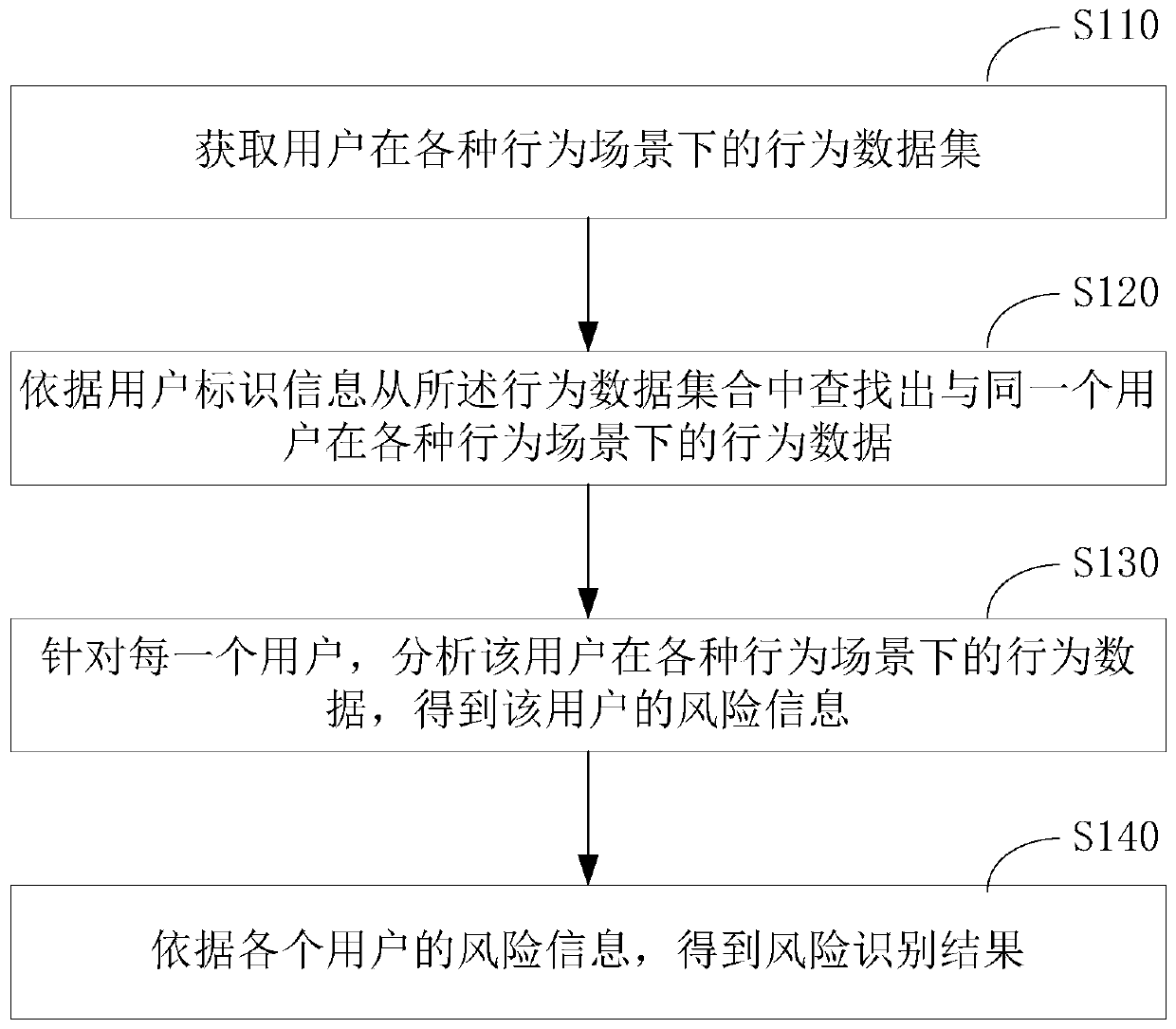
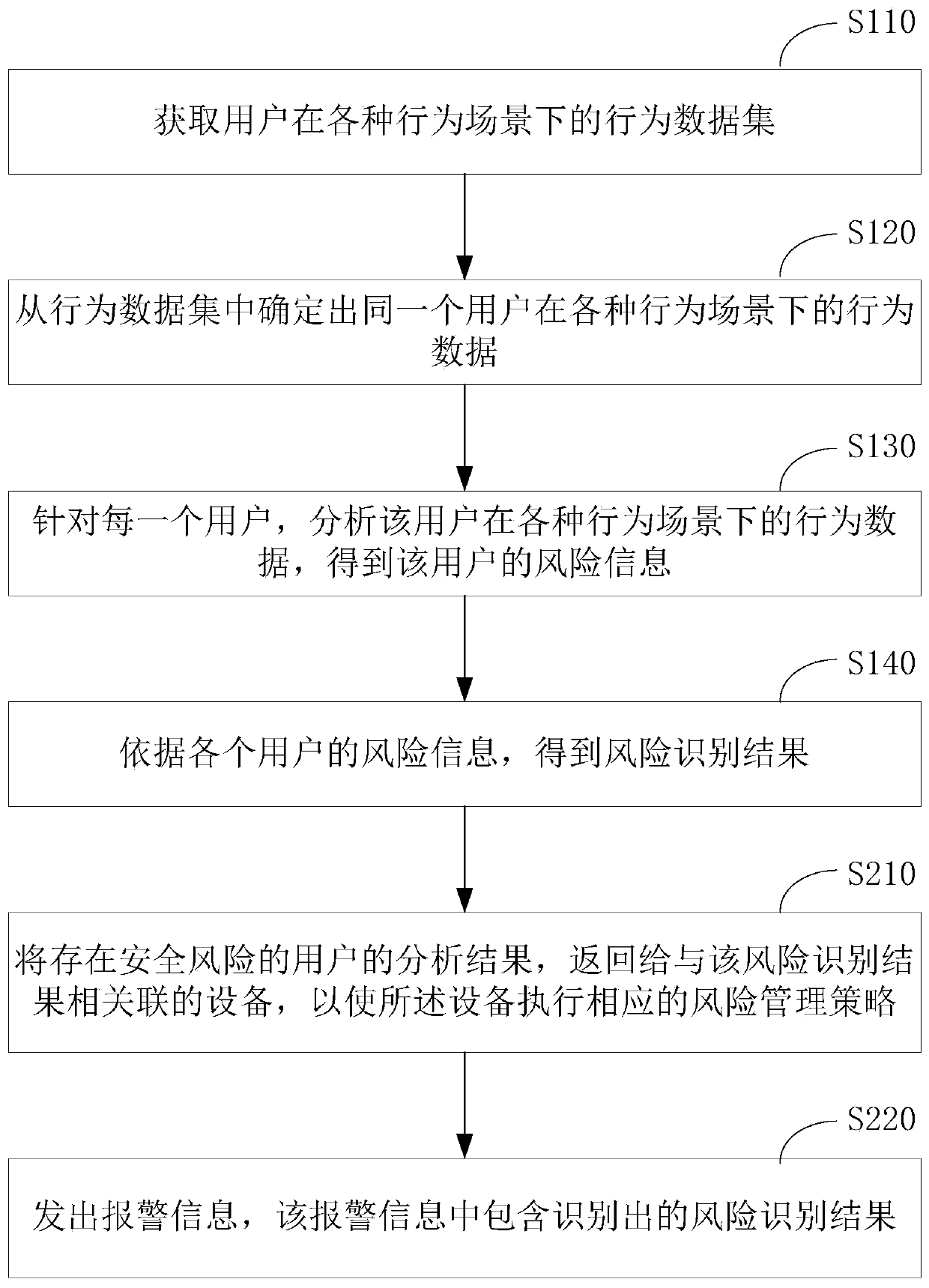
[0065] Employees of the company walk into the workplace every day until they leave after get off work. During this period, they will use various access control systems, access various servers and systems, access the Internet, enter various work-related areas, print files, use peripherals such as mobile storage devices, and use other Office equipment or IoT devices. These behaviors can be divided into three scenarios, namely accessing the Internet, accessing the intranet, and accessing office areas and devices. Security risks exist in all three scenarios, such as leaking, stealing, and sabotage. The security risks in these scenarios are all based on "people", and the current technical solutions only analyze the behavior of a person in one or part of the scenarios when analyzing whether there is a security risk in a person's behavior and trends, and do not Comprehensive analysis of the person's behavior in all scenarios, therefore, misjudgment is prone to occur. For example, em...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap