A keyword-based network trajectory classification method and device
A trajectory classification and keyword technology, applied in the field of information security, can solve problems such as heavy workload and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
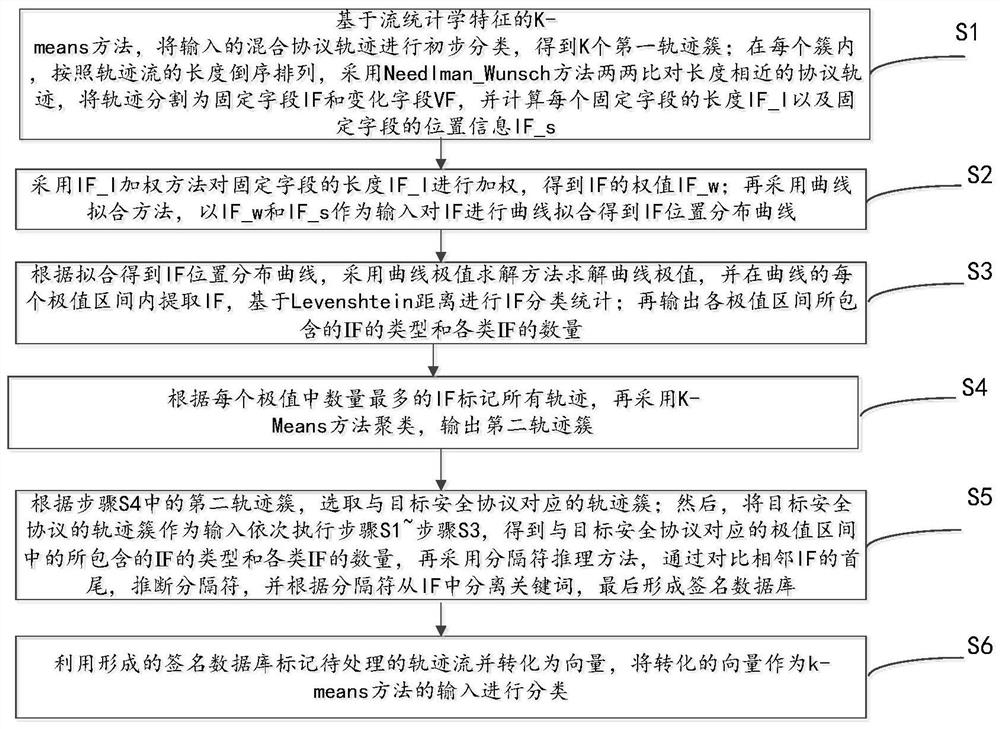
[0073] This embodiment provides a network track classification method based on keywords, please refer to figure 1 , the method includes:
[0074] Step S1: Based on the K-means method of flow statistical characteristics, the input mixed protocol trajectory is initially classified to obtain K first trajectory clusters; in each cluster, the length of the trajectory flow is arranged in reverse order, and the Needlman_Wunsch method is used for two The two compare the protocol traces with similar lengths, divide the traces into fixed field IF and variable field VF, and calculate the length IF_l of each fixed field and the position information IF_s of the fixed field.
[0075] Specifically, step S1 is to use a trajectory segmentation method to obtain a preliminary classified first trajectory cluster. The input of the trajectory segmentation method is the trajectory flow of the mixed network. First, the K-means method based on the statistical characteristics of the flow initially div...
Embodiment 2
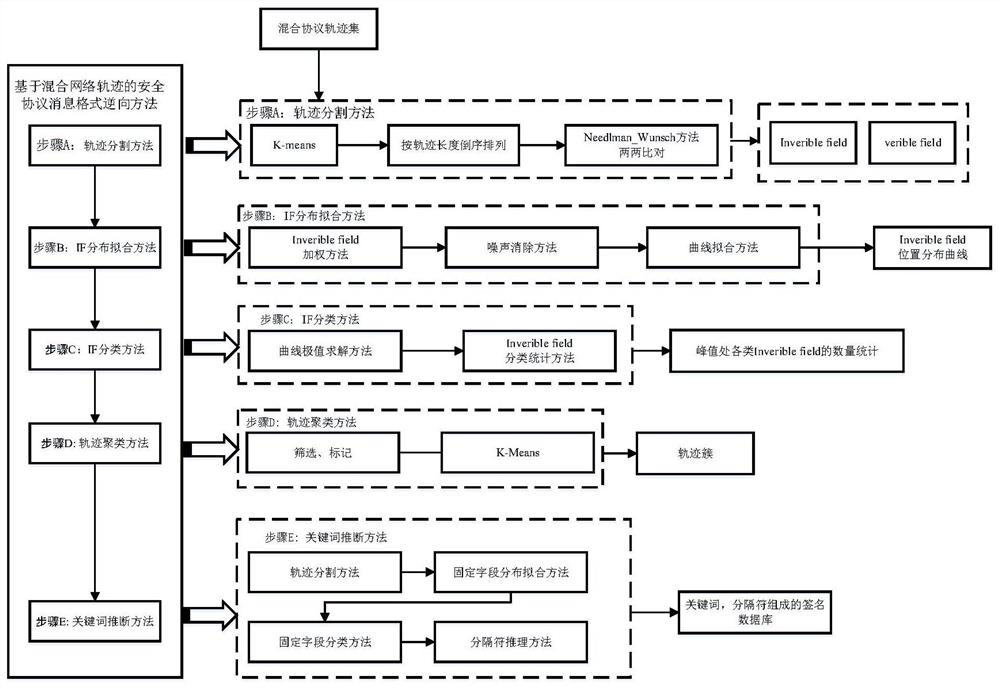
[0131] This embodiment provides a device for classifying network traces based on keywords, please refer to Figure 11 , the device consists of:
[0132] The trajectory segmentation module 201 is used for the K-means method based on the flow statistical characteristics, and initially classifies the input mixed protocol trajectory to obtain K first trajectory clusters; in each cluster, arrange in reverse order according to the length of the trajectory flow, Use the Needlman_Wunsch method to compare protocol trajectories with similar lengths in pairs, divide the trajectories into fixed field IF and variable field VF, and calculate the length IF_l of each fixed field and the position information IF_s of the fixed field;
[0133] The IF distribution solving module 202 is used to use the IF_1 weighting method to weight the length IF_1 of the fixed field to obtain the weight IF_w of the IF; and then use the curve fitting method to perform curve fitting on the IF with IF_w and IF_s as...
Embodiment 3
[0164] Based on the same inventive concept, the present application also provides a computer-readable storage medium 300, please refer to Figure 12 , on which a computer program 311 is stored, and the method in Embodiment 1 is implemented when the program is executed.
[0165] Since the computer-readable storage medium introduced in the third embodiment of the present invention is the computer-readable storage medium used to implement the keyword-based network trajectory classification method in the first embodiment of the present invention, it is based on the introduction in the first embodiment of the present invention method, those skilled in the art can understand the specific structure and deformation of the computer-readable storage medium, so details are not repeated here. All computer-readable storage media used in the method of Embodiment 1 of the present invention belong to the scope of protection of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com