User access method
An access method and user technology, applied in the communication field, can solve problems such as high wireless resource overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
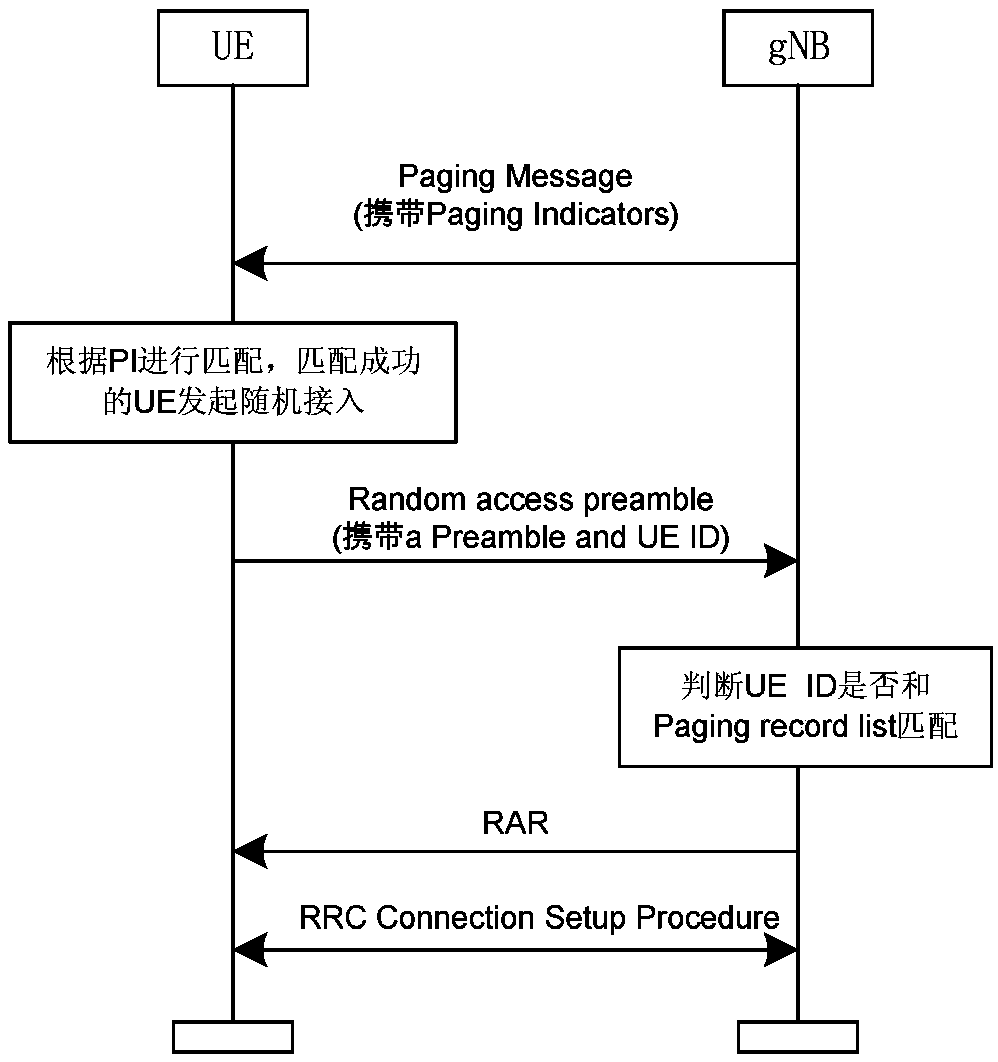
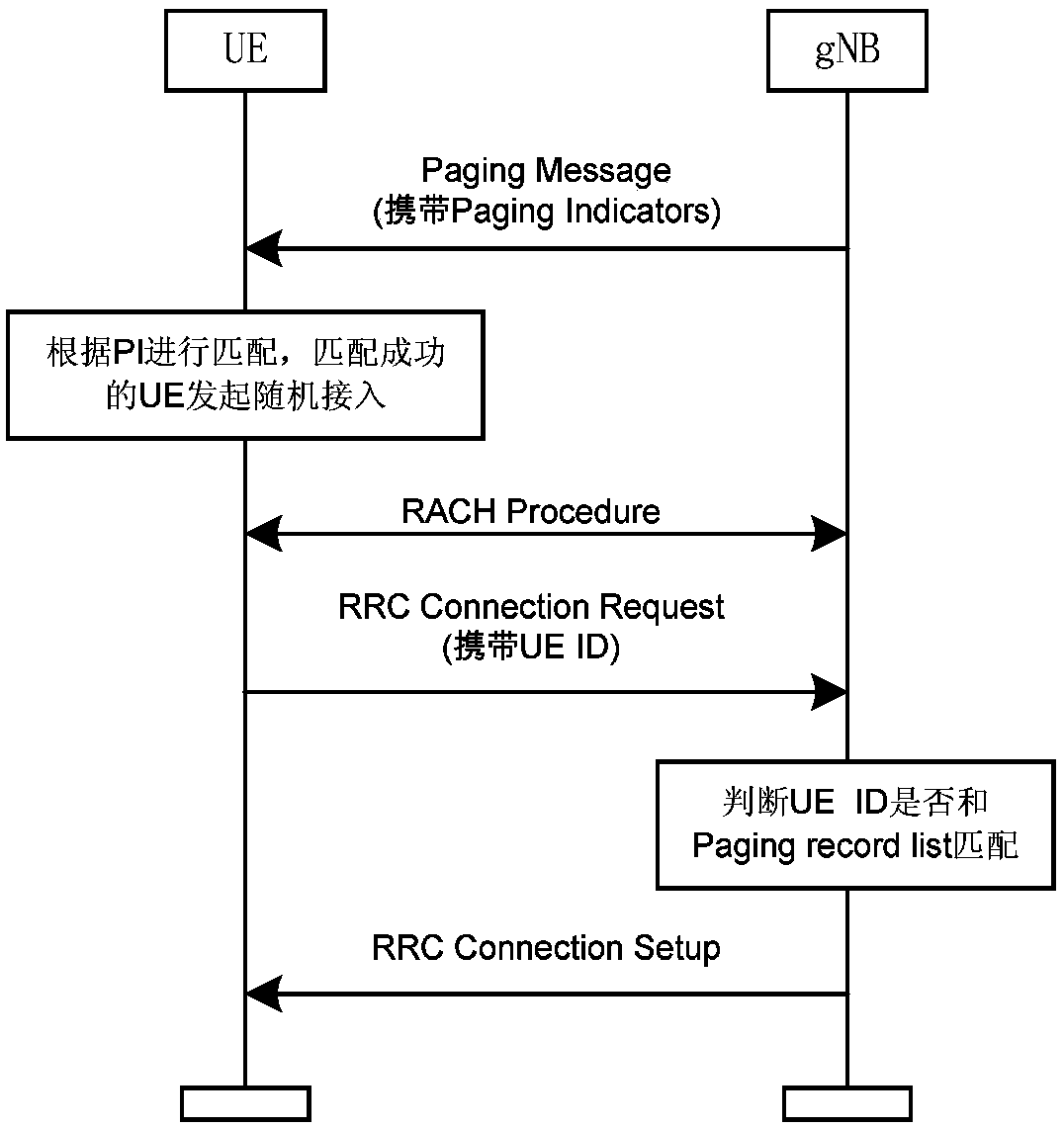
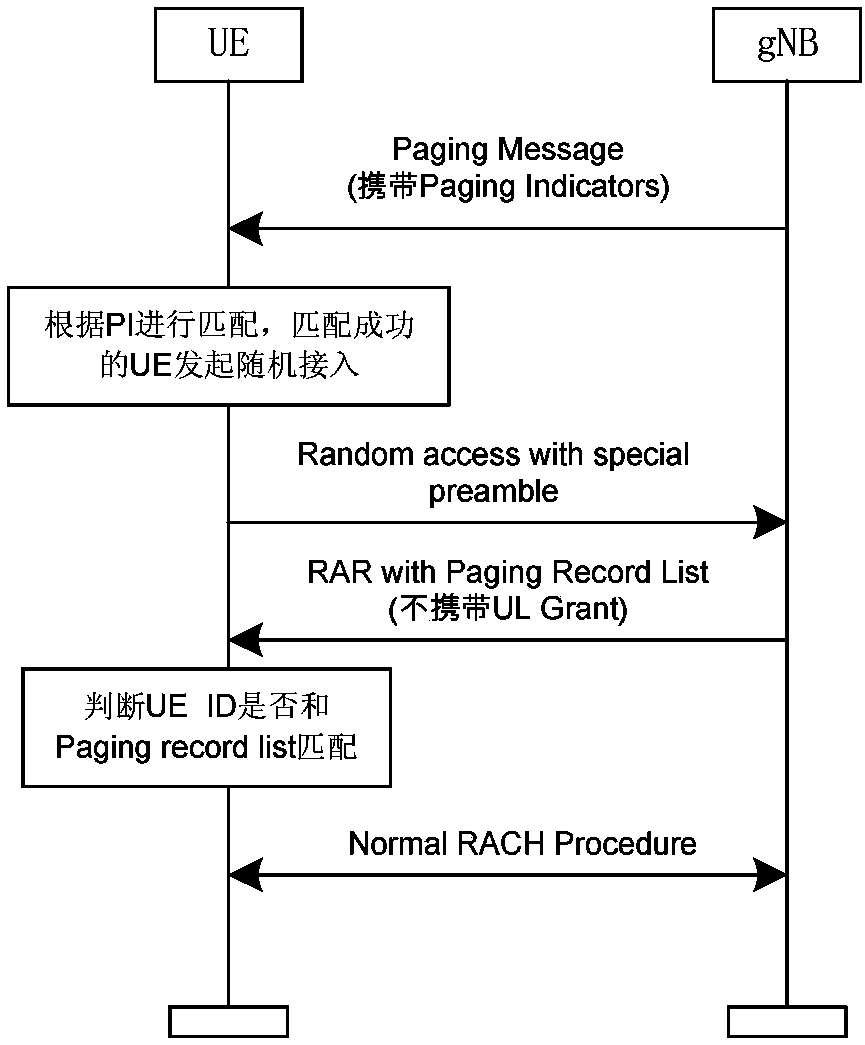
[0059] In order to make the purpose, technical means and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings.
[0060] For solution 2 described in the background technology, here is an analysis of the reasons for the large downlink wireless resource overhead: in solution 2, it is necessary to send the complete PagingRecordList or the complete UE ID list corresponding to the specified Preamble in the beam responding to the PI (depending on whether A common Preamble is allocated to all UEs responding to PIs or a dedicated Preamble is allocated to each PI). Based on this processing, it can be seen that the size of the downlink overhead depends on the number of beams responding to PIs. If the UEs responding to the PI are distributed in different beams, the downlink overhead will be greatly affected. At the same time, in solution 2, UEs in the same beam that respond to PI may ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com