A kind of NFC key update method, terminal and system
A key update and terminal technology, applied in the NFC field, can solve the problems of identity information leakage, cumbersome operation process, key leakage and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
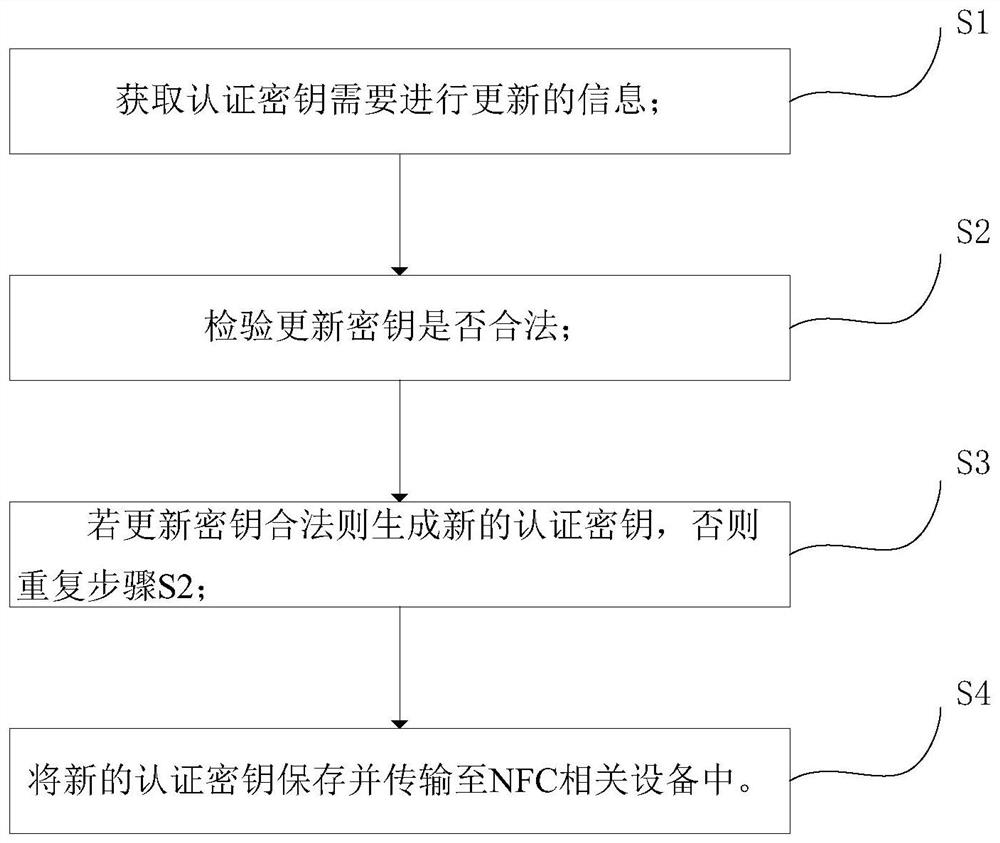
[0049] Embodiment 1: The update key is stored in the external NFC card; at this time, there are two ways to trigger the update of the authentication key.
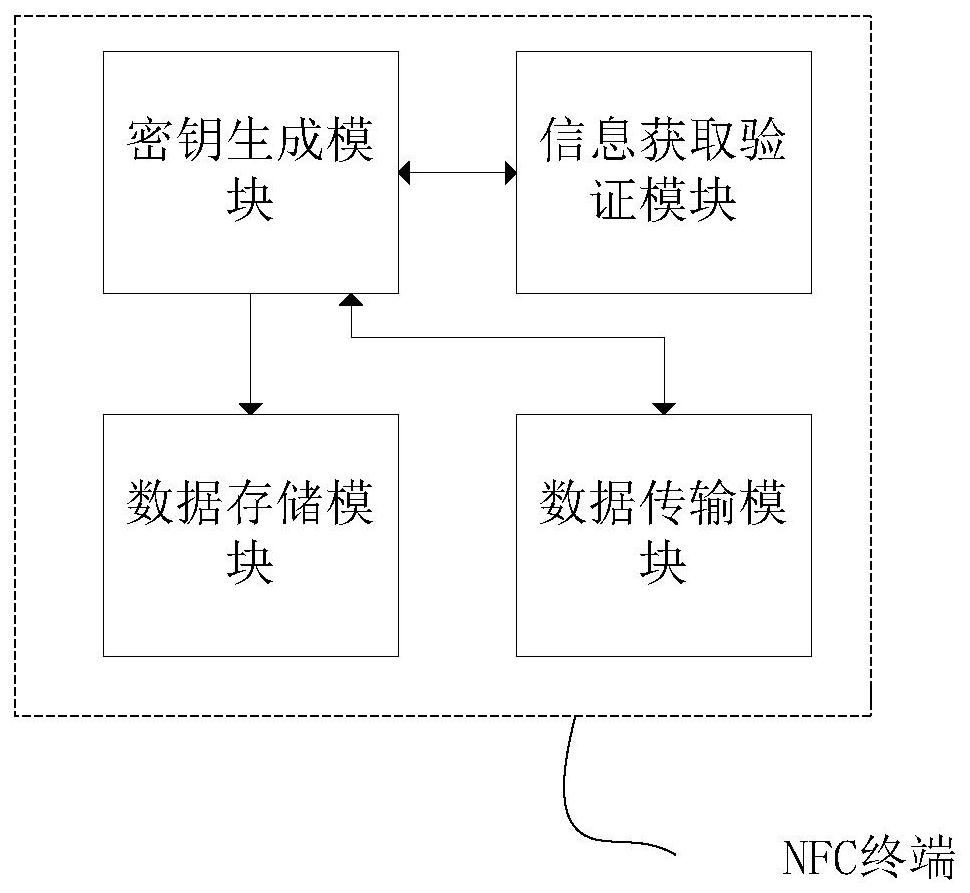
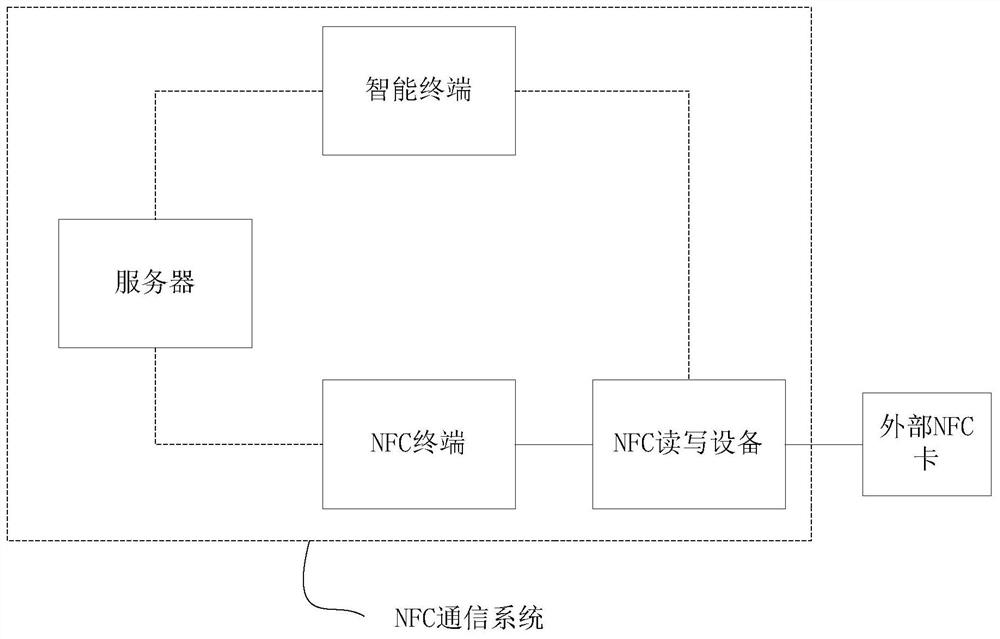
[0050] 1. Reference figure 2 and image 3 After the NFC read-write device is connected to the NFC terminal, it communicates with the NFC terminal through an external NFC card with an update key. Since the NFC card in the NFC terminal stores an update key, it triggers an authentication key update (only with an update key key external NFC card can only trigger the update of the authentication key but cannot open the NFC terminal, the NFC terminal can be a smart door lock in this embodiment), the key generation module generates a new authentication key, and then stores the key in the data storage module The new authentication key is encrypted by SHA256 and stored, and then the encrypted new authentication key is transmitted to the server by HMAC through the data transmission module for storage (covering the original authenti...
Embodiment 2
[0052] Embodiment 2: The update key is not stored in the external NFC card;
[0053] At this time, the update of the authentication key cannot be triggered by the external NFC card with the authentication key. Therefore, the update operation of the authentication key can only be triggered after logging in to the NFC key software service platform through the smart terminal to communicate with the server. After the authentication key is updated, the subsequent work of the NFC communication system includes the whole process of processing the new authentication key after the authentication key is updated in the first embodiment. But, because the NFC card in the NFC terminal is stored as the authentication key at this moment, when the key generating module generates a new authentication key, the authentication key of the NFC card (that is, the information acquisition verification module) in the NFC terminal is also covered as The new authentication key can be written into the exter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com