A security threat monitoring and defense system and method for an Internet of Things system
An IoT system and threat detection technology, applied in the field of IoT system security threat monitoring and defense systems, can solve problems such as poor compatibility, difficulty in deploying security threats, and no support for multiple traffic security detections.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
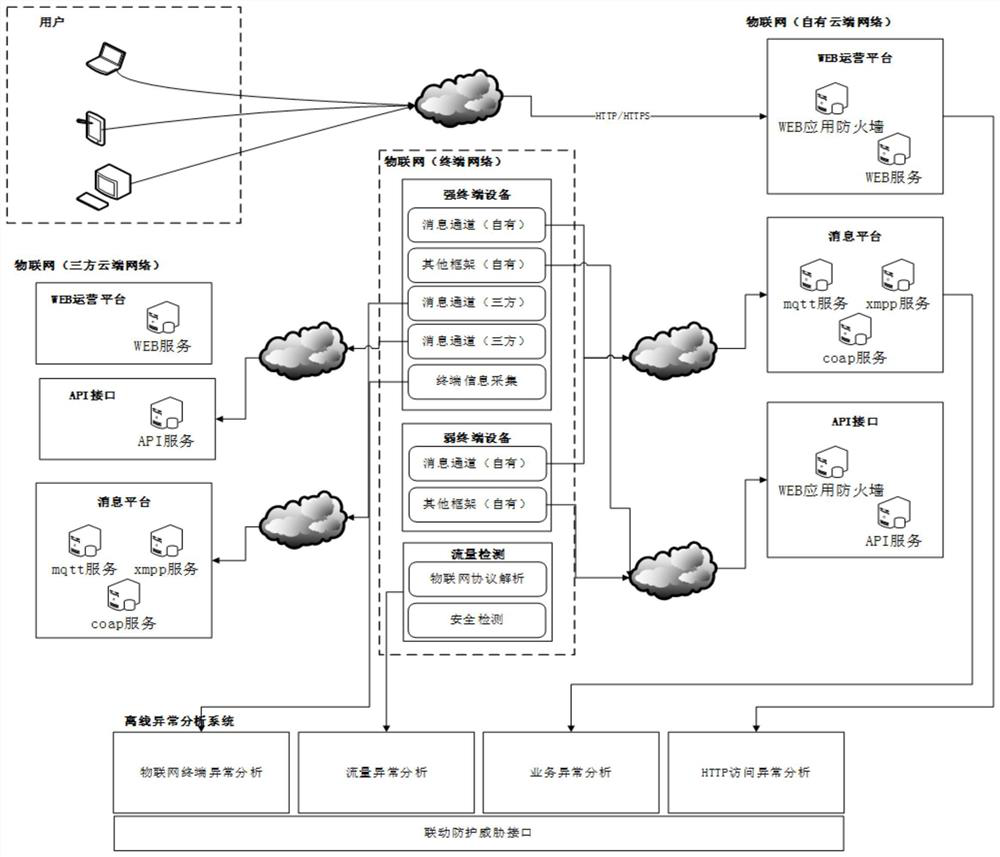
[0069] Such as figure 1 As shown, an Internet of Things system security threat monitoring and defense system includes a traffic anomaly analysis system, an Internet of Things terminal anomaly analysis system, a business anomaly analysis system, an HTTP anomaly analysis system, and a threat detection and intelligence generation system. The intelligence generation system is connected with the traffic anomaly analysis system, the IoT terminal anomaly analysis system, the business anomaly analysis system, and the HTTP anomaly analysis system respectively.
[0070] Specifically, the traffic anomaly analysis system is used to realize asset discovery, traffic security detection, and threat analysis by analyzing traffic data, and report the analyzed security threat events to the threat detection and intelligence generation system; and in this embodiment, the The traffic anomaly analysis system includes a traffic anomaly analysis unit and a number of traffic detection devices, and the ...
Embodiment 2
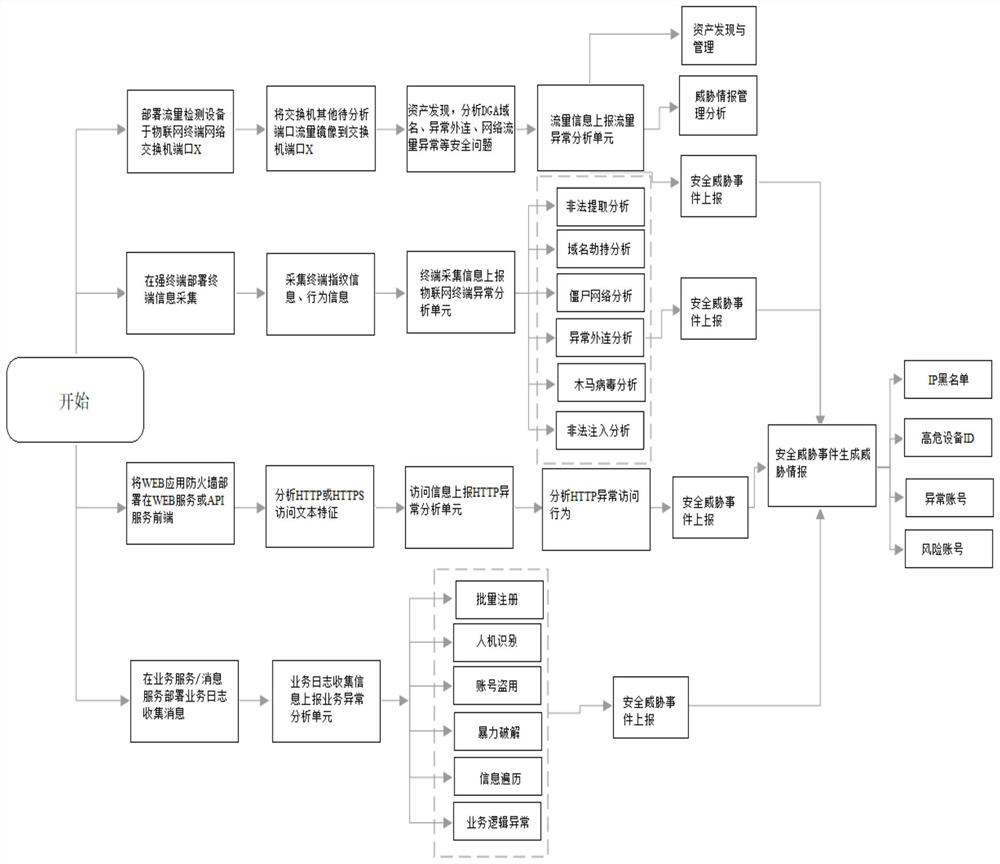
[0076] Such as figure 2 As shown, a method for monitoring and defending against a security threat of an Internet of Things system is realized through the above-mentioned system for monitoring and defending against a security threat of an Internet of Things system, and specifically includes the following steps:
[0077] A1. Deploy traffic detection equipment on port X of the IoT terminal network switch, so as to mirror the traffic of other ports to be analyzed on the IoT terminal network switch to switch port X;
[0078] A2. The traffic detection device analyzes and obtains the asset attribute information of the protocol according to the protocol identification feature library, asset service feature library, mac address prefix feature library, and the obtained IoT protocol information. The asset attribute information includes at least source information and destination mac Information, source IP information, destination IP information, asset service information;
[0079] As a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com