Domain name hijacking defense method and device, computer device and storage medium
A domain name hijacking and domain name technology, applied in the field of computer networks, can solve problems such as network security threats, achieve the effect of defending against domain name hijacking and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
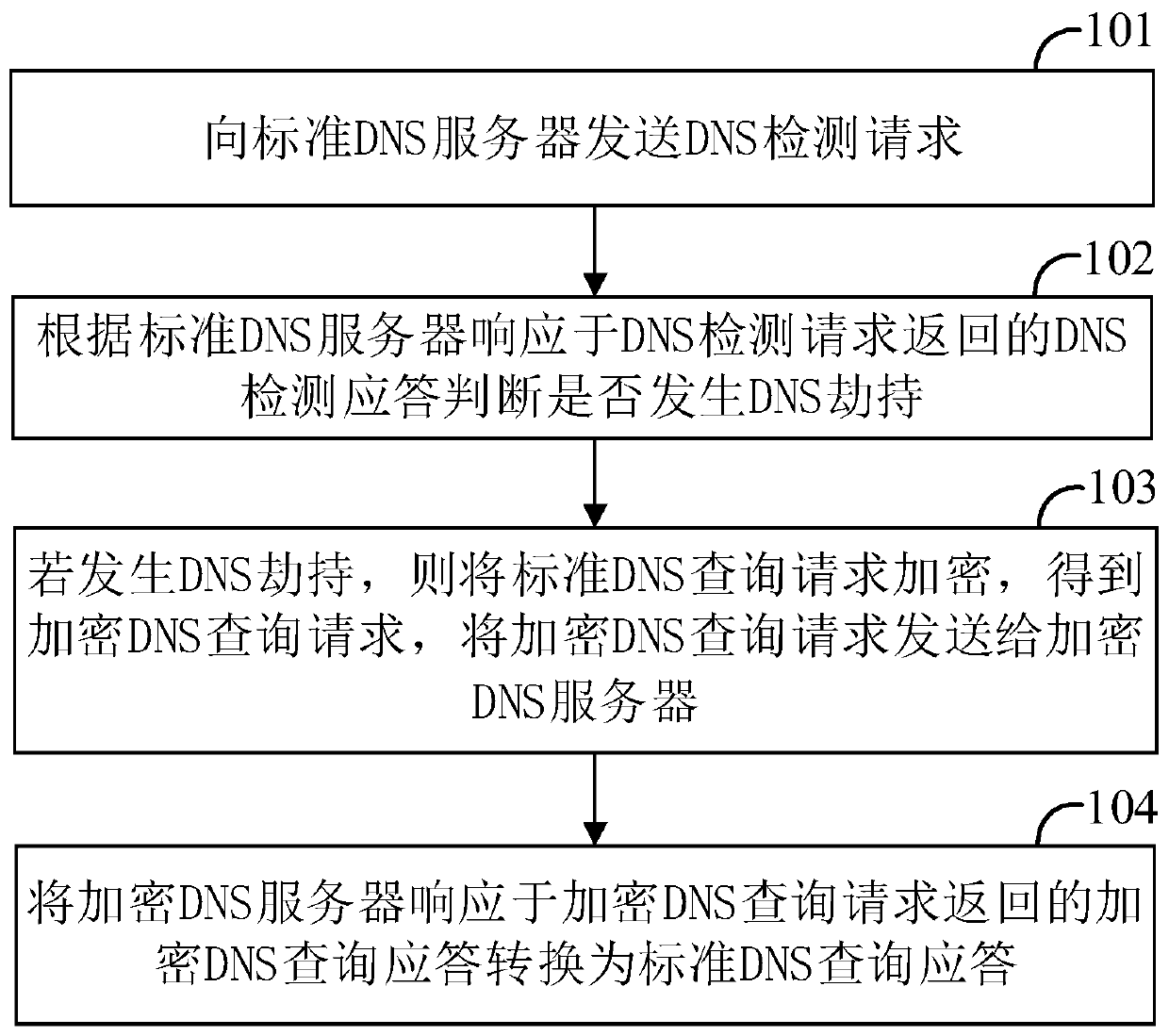
[0069] figure 1 It is a flow chart of the domain name hijacking defense method provided by the embodiment of the present invention. The domain name hijacking defense method is applied to computer devices to defend against domain name hijacking and improve network security.
[0070] Referring to 1, the domain name hijacking defense method specifically includes the following steps:
[0071] S101. Send a DNS detection request to a standard DNS (Domain Name System, Domain Name System) server.
[0072] A DNS detection request may be sent to a standard DNS server through a standard DNS client in the computer device. The standard DNS client is built into the operating system of the computer device. The standard DNS client provides standard DNS services for the computer device based on the standard DNS protocol (RFC1035).
[0073] A DNS server list may be stored in the computer device, and the DNS server list may include one or more DNS servers. The DNS server list may be read, a...
Embodiment 2
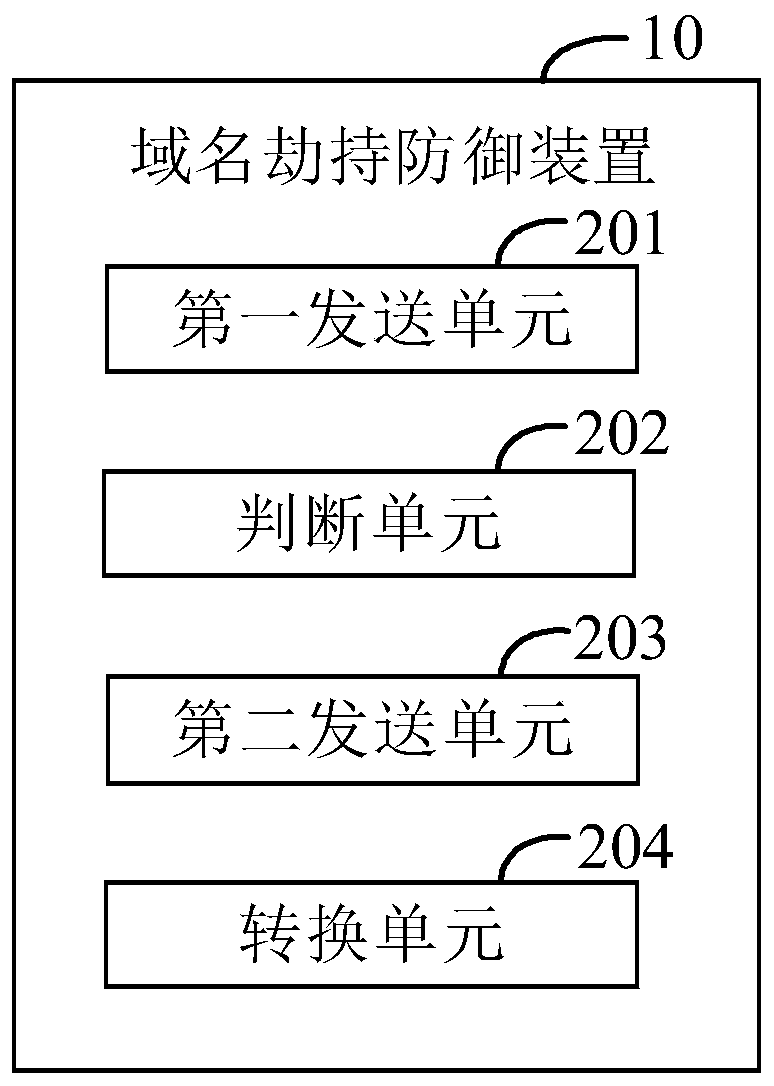
[0118] figure 2 The structural diagram of a preferred embodiment of the domain name hijacking defense device provided by the embodiment of the present invention. The domain name hijacking defense device 10 is applied to computer devices to defend against domain name hijacking and improve network security.
[0119] Such as figure 2 As shown, the domain name hijacking defense device 10 may include: a first sending unit 201 , a judging unit 202 , a second sending unit 203 , and a converting unit 204 .
[0120] The first sending unit 201 is configured to send a DNS detection request to a standard DNS server.
[0121] A DNS detection request may be sent to a standard DNS server through a standard DNS client in the computer device. The standard DNS client is built into the operating system of the computer device. The standard DNS client provides standard DNS services for the computer device based on the standard DNS protocol (RFC1035).
[0122] A DNS server list may be stored i...
Embodiment 3
[0167] This embodiment provides a computer-readable storage medium, and a computer program is stored on the computer-readable storage medium. When the computer program is executed by a processor, the steps in the above-mentioned domain name hijacking defense method embodiments are implemented, for example figure 1 S101-S104 shown:
[0168] S101, sending a DNS detection request to a standard DNS server;
[0169] S102. Determine whether DNS hijacking occurs according to the DNS detection response returned by the standard DNS server in response to the DNS detection request;
[0170] S103. If DNS hijacking occurs, encrypt the standard DNS query request to obtain an encrypted DNS query request, and send the encrypted DNS query request to an encrypted DNS server;
[0171] S104. Convert the encrypted DNS query response returned by the encrypted DNS server in response to the encrypted DNS query request into a standard DNS query response.
[0172] Alternatively, when the computer pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com