A comprehensive monitoring system and method for illegal outreach
A comprehensive monitoring system and outreach technology, applied in transmission systems, electrical components, etc., can solve problems such as inability to monitor off-network outreach, weak real-time performance, complex program structure, etc., and achieve the effect of avoiding monitoring and illegal access to the Internet
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] This embodiment provides a comprehensive monitoring system for illegal outreach, including an intranet support and guarantee platform, a monitoring client service module, and an extranet detector;
[0037] Described intranet support guarantee platform is used for storing the binding information between the model of monitored intranet computer, IP address and MAC address, configures the monitoring strategy of monitoring client service module and will monitor strategy through intranet and corresponding The monitoring client service module synchronizes, and receives and manages alarm information; the monitoring strategy includes the length of interval between each monitoring, the legal IP address and MAC address of the intranet computer where the monitoring client service module is located, and external network detection address of the device;
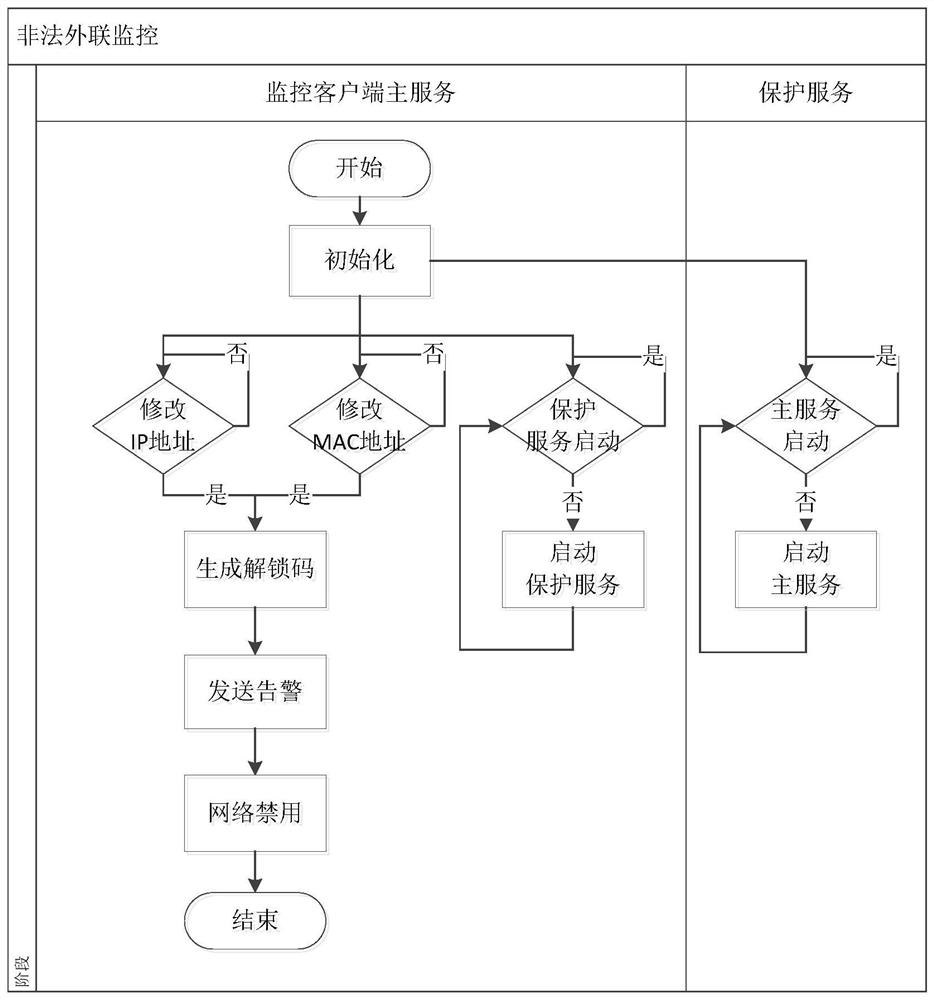
[0038] The monitoring client service module is installed in the monitored intranet computer, and is used to try to connect to the...
Embodiment 2
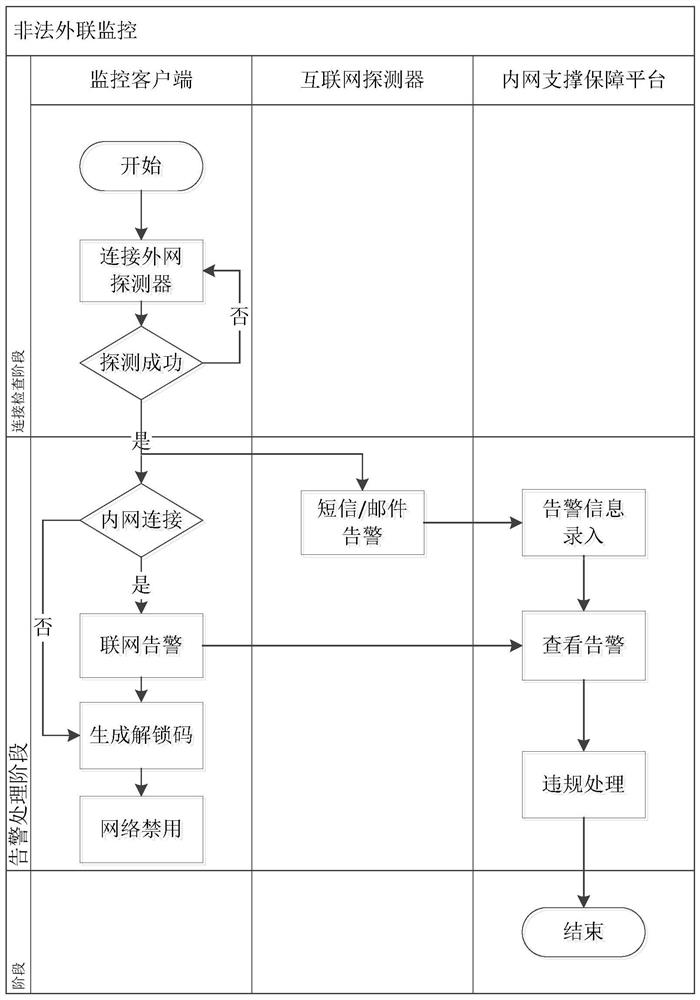
[0044]This embodiment provides a method for comprehensive monitoring, blocking and warning of illegal outreach by using the system described in Embodiment 1, such as figure 1 shown, including the following steps:
[0045] S1. Install a monitoring client service module on the monitored intranet computer, install an external network detector on the Internet server, and deploy an intranet support guarantee platform on the intranet;
[0046] S2, storing the binding information between the models, IP addresses and MAC addresses of all monitored intranet computers in the intranet support guarantee platform;
[0047] S3, configure the monitoring strategy of each monitoring client service module in the intranet support guarantee platform, and the monitoring strategy is synchronized with the corresponding monitoring client service module through the intranet; the monitoring strategy includes the duration of the interval between each monitoring , the address of the external network det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com