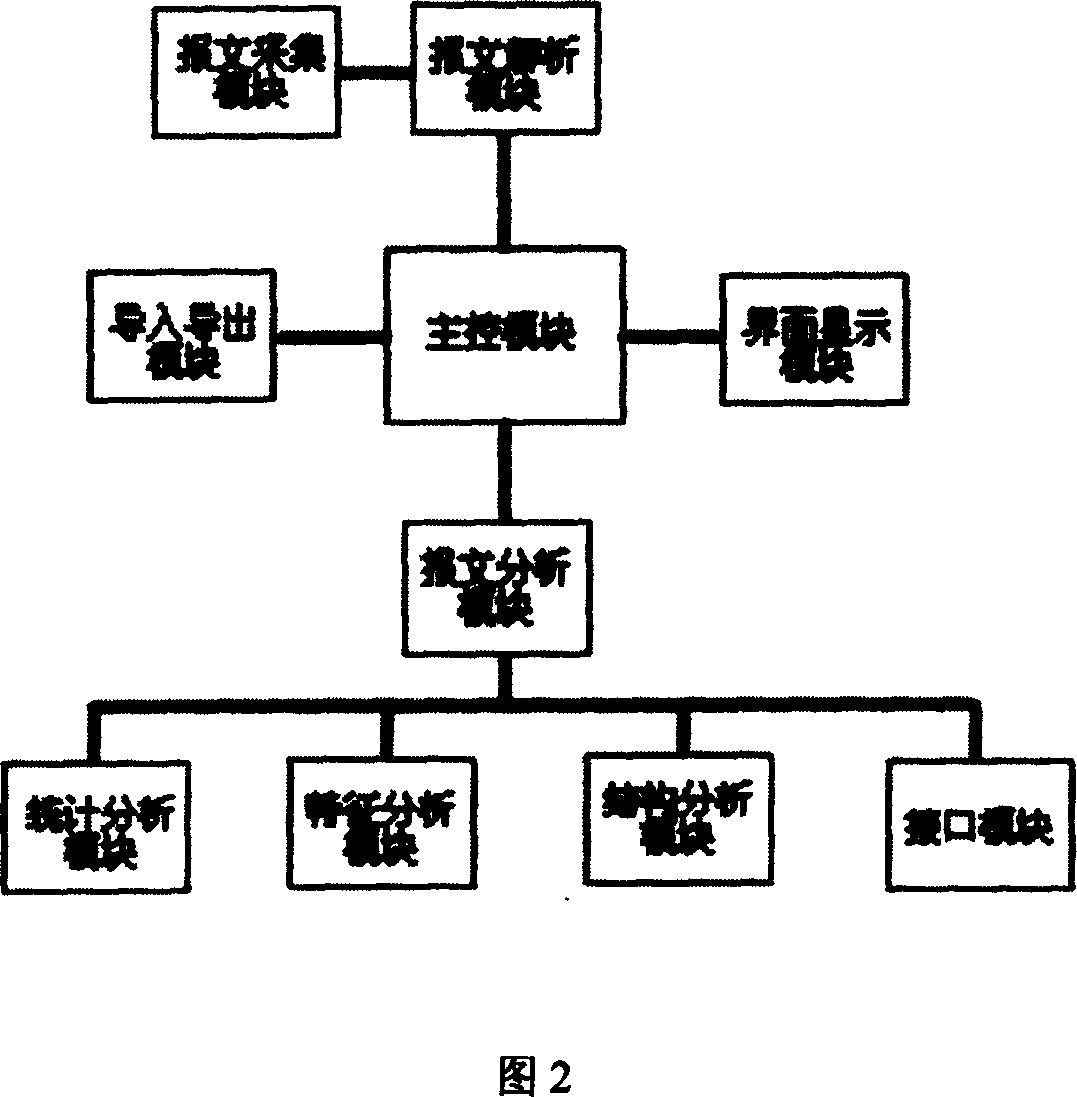
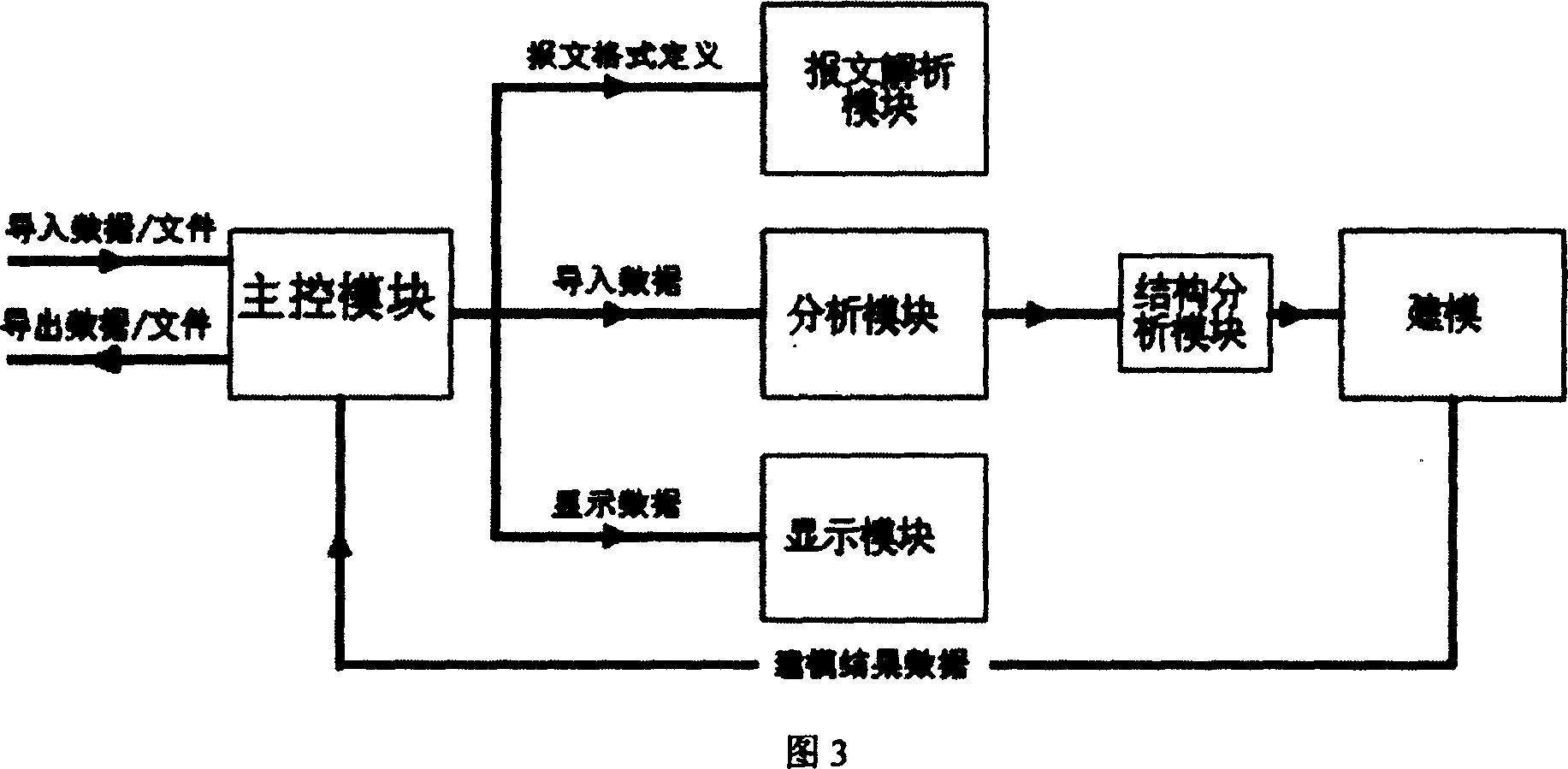
Patents
Literature
41 results about "Network detector" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network detectors or network discovery software are computer programs that facilitate detection of wireless LANs using the 802.11b, 802.11a and 802.11g WLAN standards. Discovering networks may be done through active as well as passive scanning.
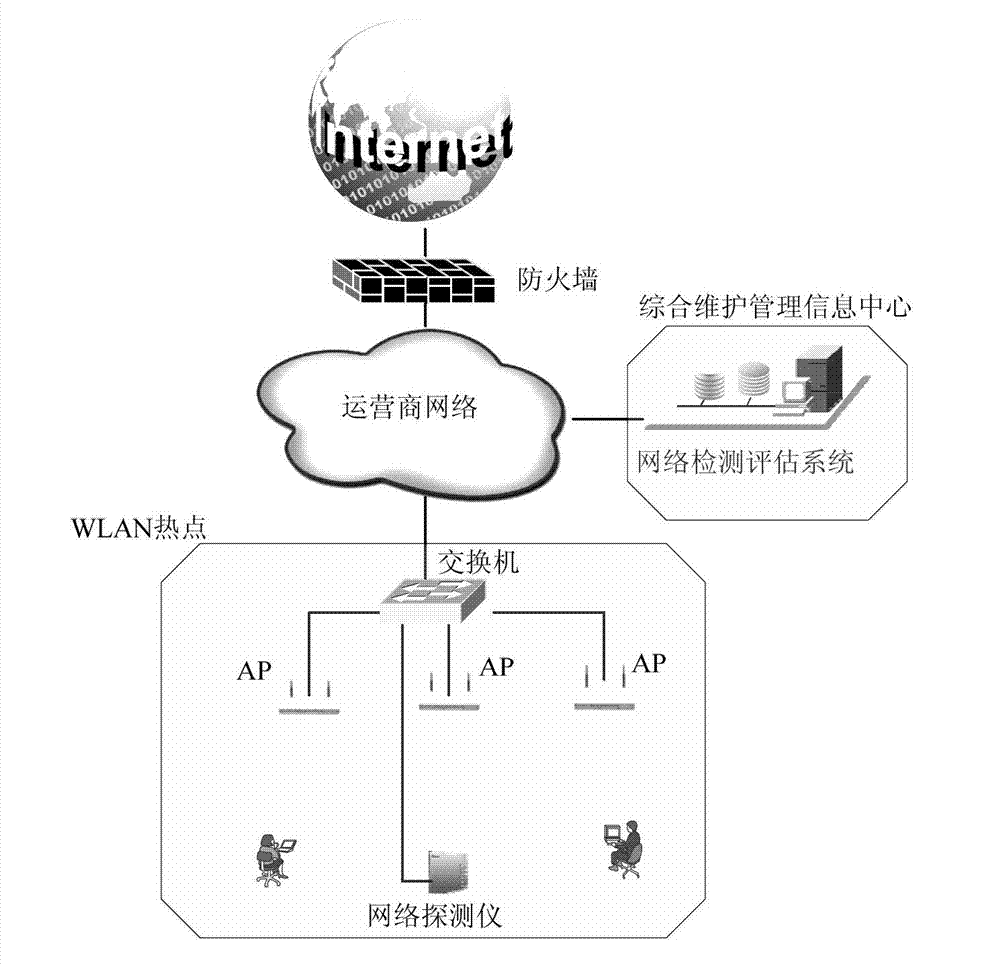
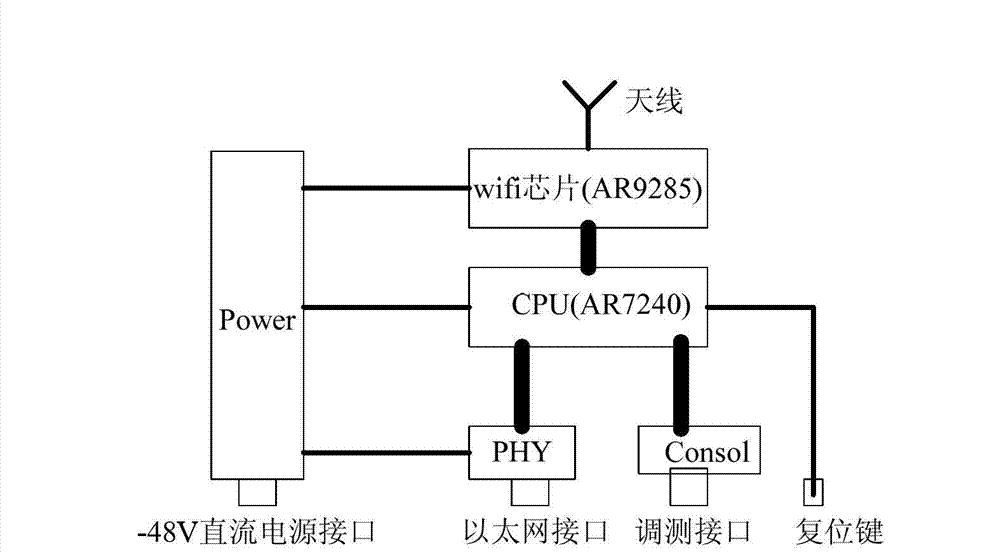
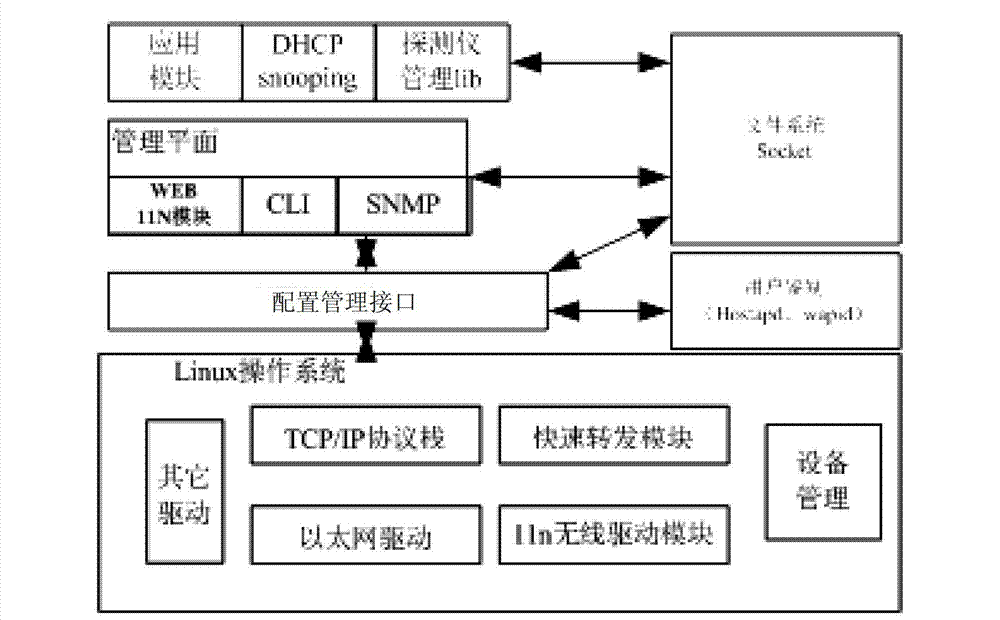
Monitoring and evaluating system of WLAN (Wireless Local Area Network) wireless network
InactiveCN102958088AQuick discoveryMaintain securityWireless communicationNetwork detectorNetwork connection
The invention discloses a monitoring and evaluating system of a WLAN (Wireless Local Area Network) wireless network, comprising a background network evaluating sever and a plurality of network detectors, wherein the network detectors are respectively distributed at all hot-spot positions of a city, and are in network connection with an operator by an Ethernet; the background network evaluating sever is provided with a network monitoring and evaluating module so as to carry out summary analysis on network-operation key index data acquired from the bottom layer, find the problems of the network and maintain the security and the performance of the network. The monitoring and evaluating system disclosed by the invention has the advantages that timed testing and acquisition are carried out on network-operation key index data by the network detectors, the size of the timed interval can be set by self; and the monitoring and evaluating system can help the operator to verify and evaluate the quality and the performance of the wifi network in a quick, objective and just manner and provides a scientific evaluating means for improving the management and maintenance level of the operator for the WLAN network and services.
Owner:DATANG TELECOM TECH CO LTD
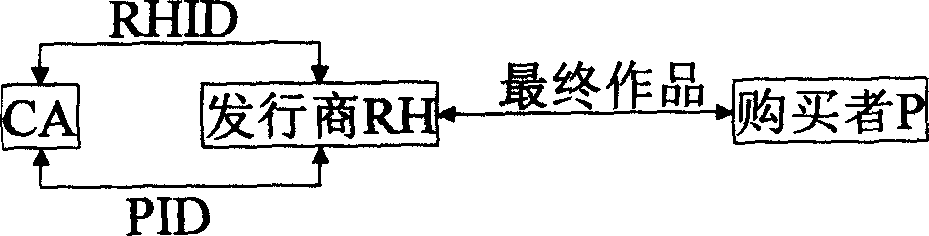
Digital watermarking infrastructure
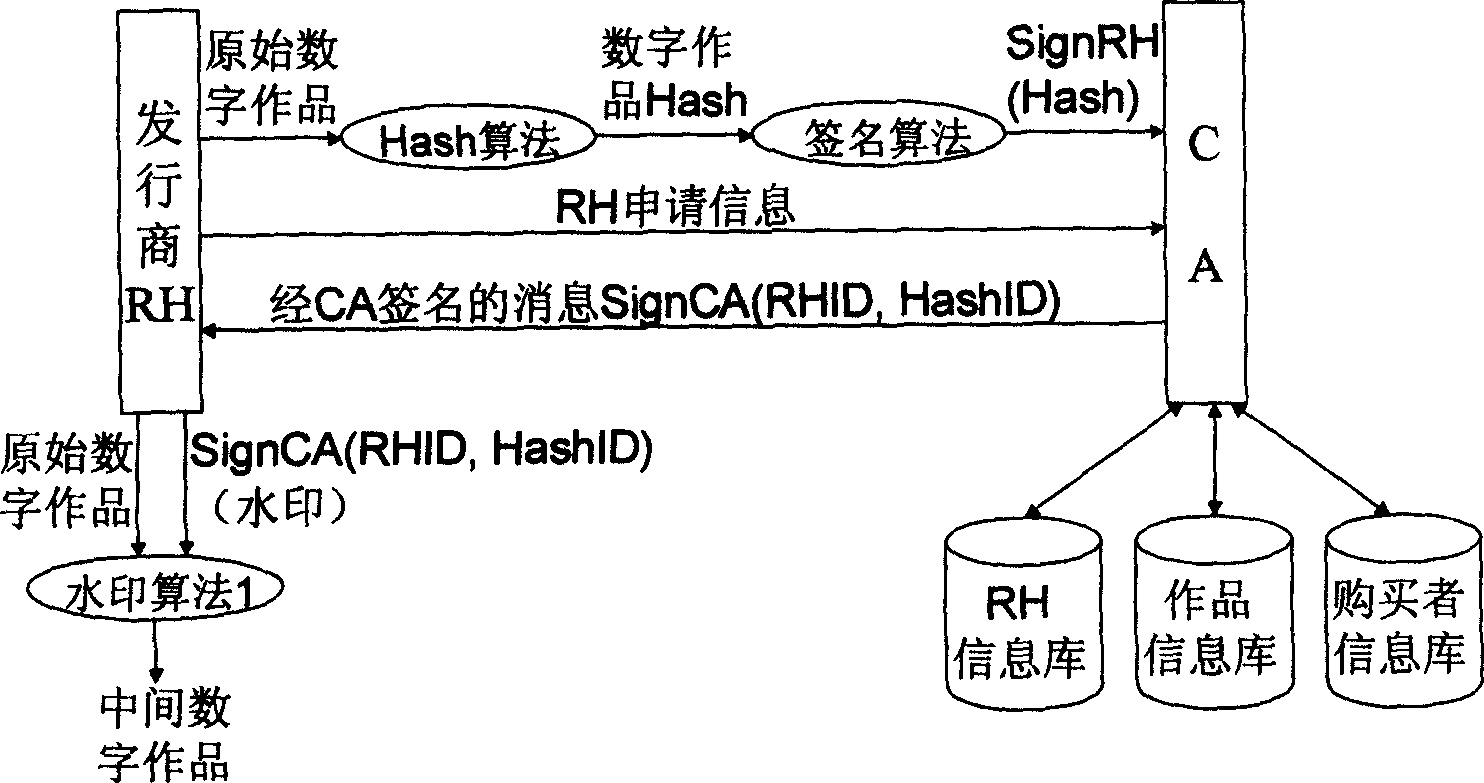
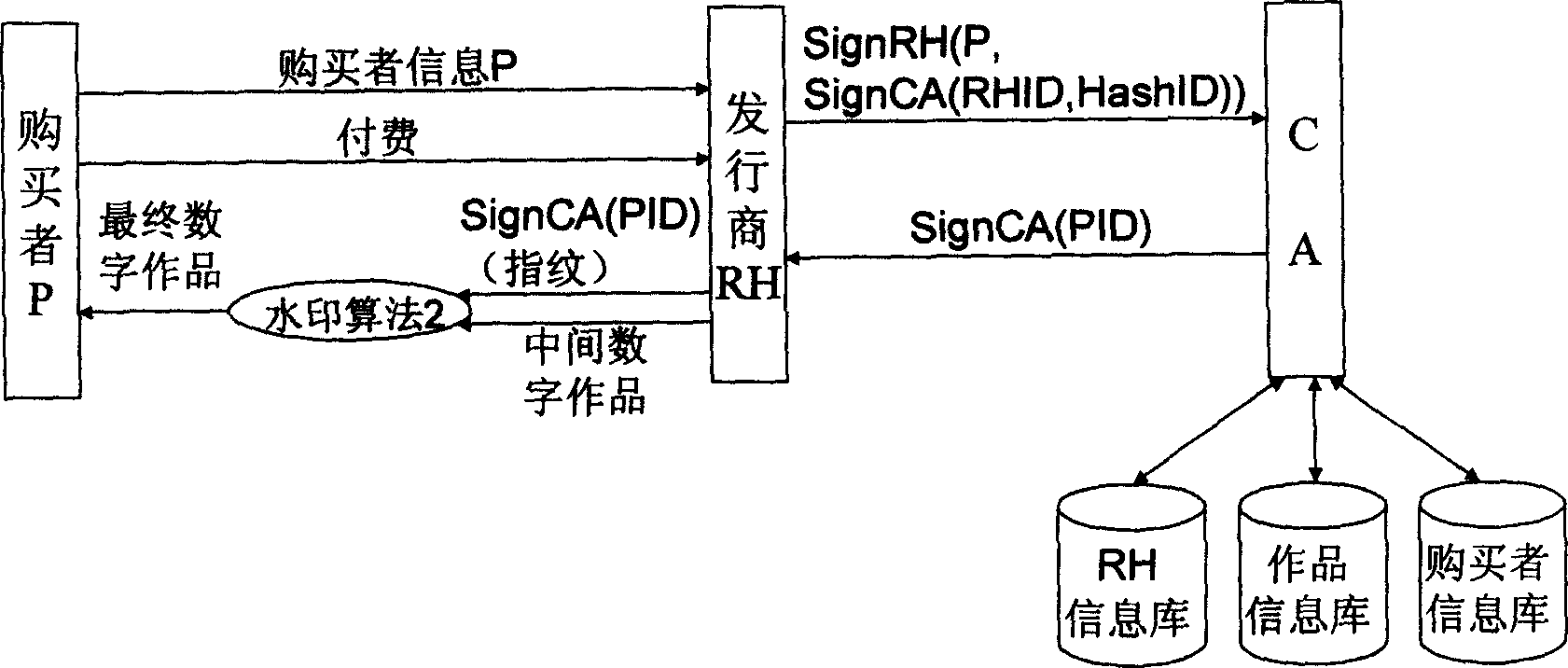
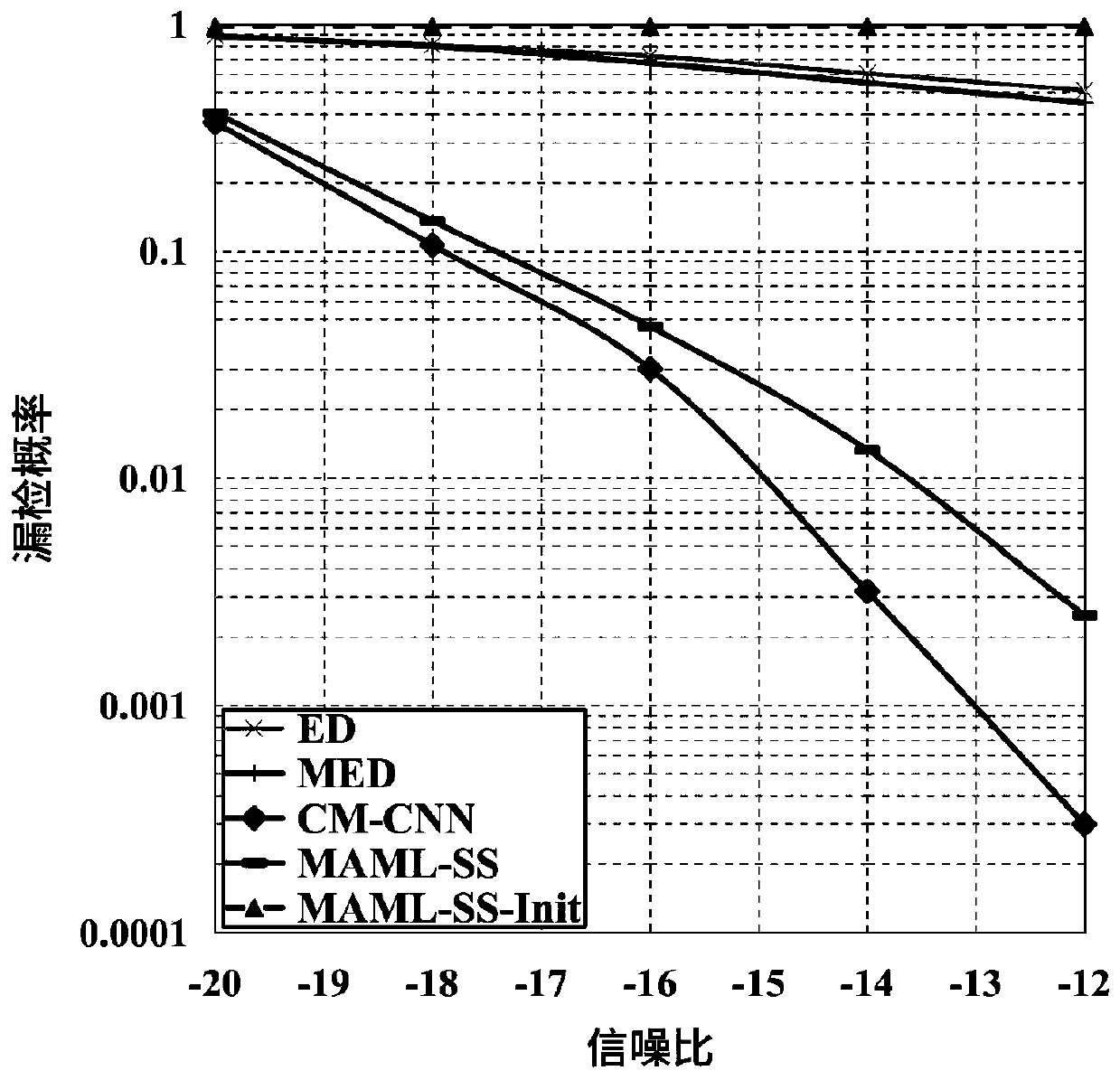
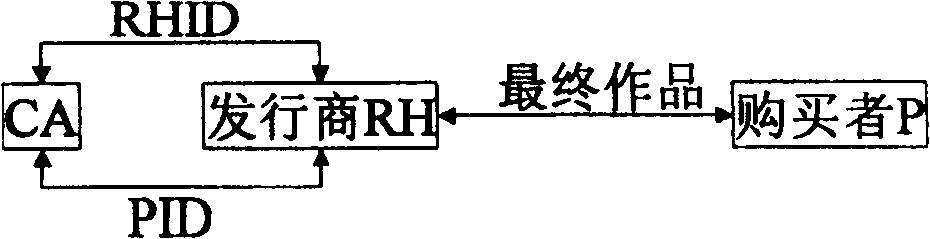
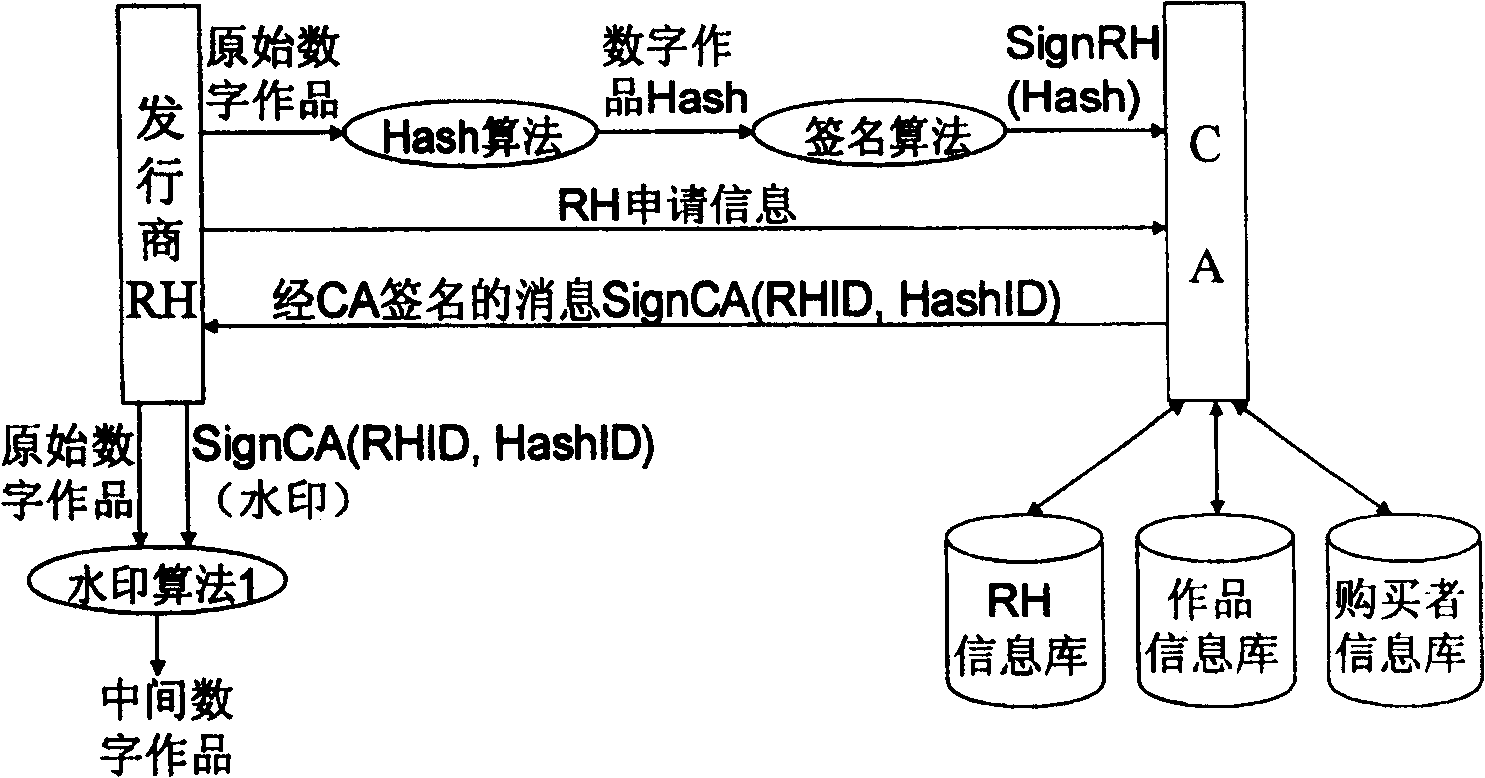
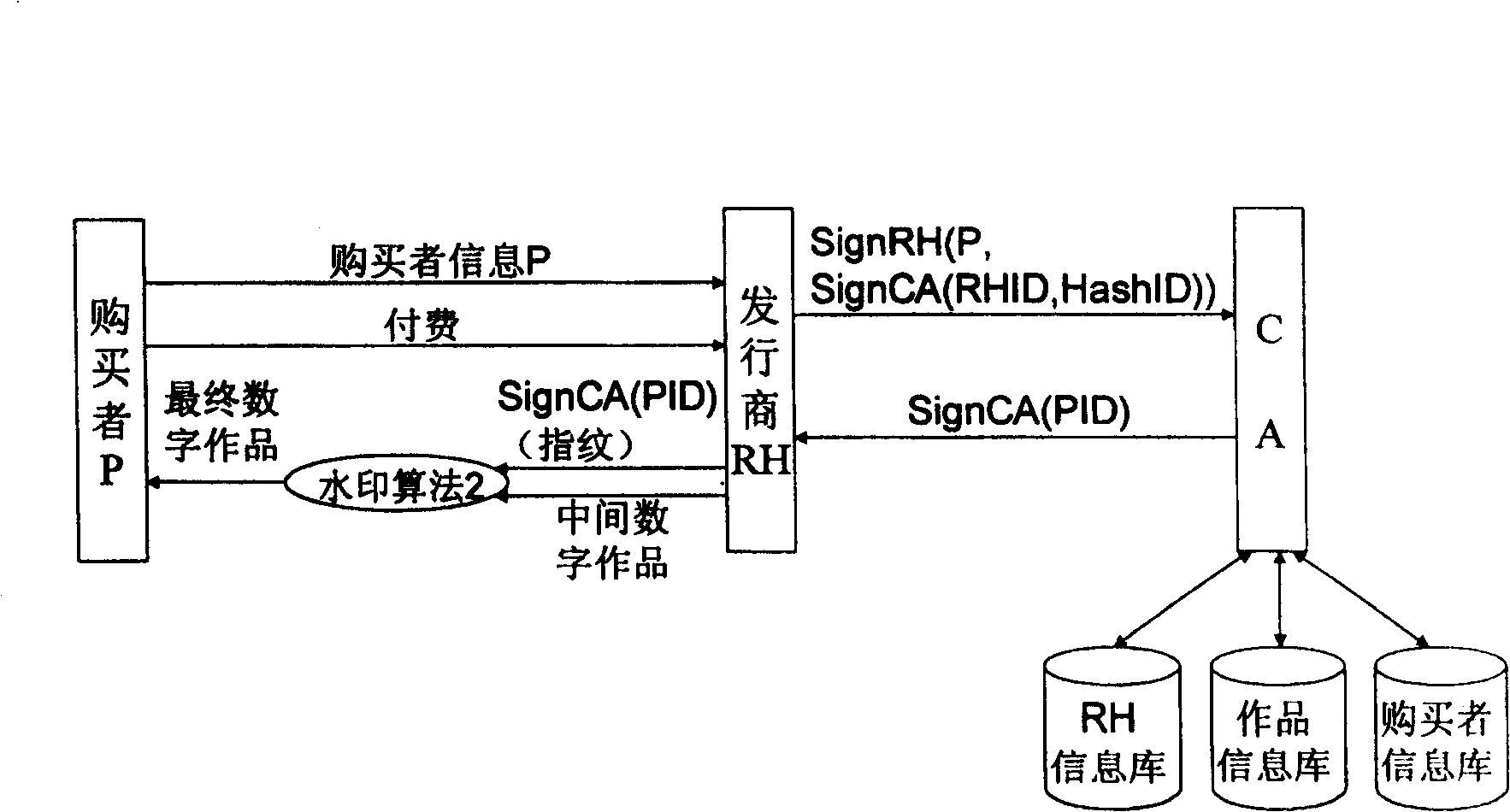
InactiveCN1558303ANo leaksNo risk of leaking original digital workDigital data processing detailsNetwork detectorPropagator
The present invention discloses basic watermark facility, and is one digital work copyright protecting system based on digital watermark. The user purchased legal digital work has two CA signature watermarks embedded, one identifying the publisher and the other identifying the purchaser. When illegal copying is found out with the network detector or memory medium based on movable deputy, the illegal propagator may be determined based these two watermark. The copyright information watermark of the publisher includes the publisher ID and the work ID, the digital fingerprint of the purchaser includes the purchaser ID, and these two watermarks are random sequence produced with the corresponding ID and through CA signature. The present invention uses the correlated concept of PKI system for tracing illegal copying and is simple, practical, reliable and expandable.
Owner:BEIJING UNIV OF POSTS & TELECOMM
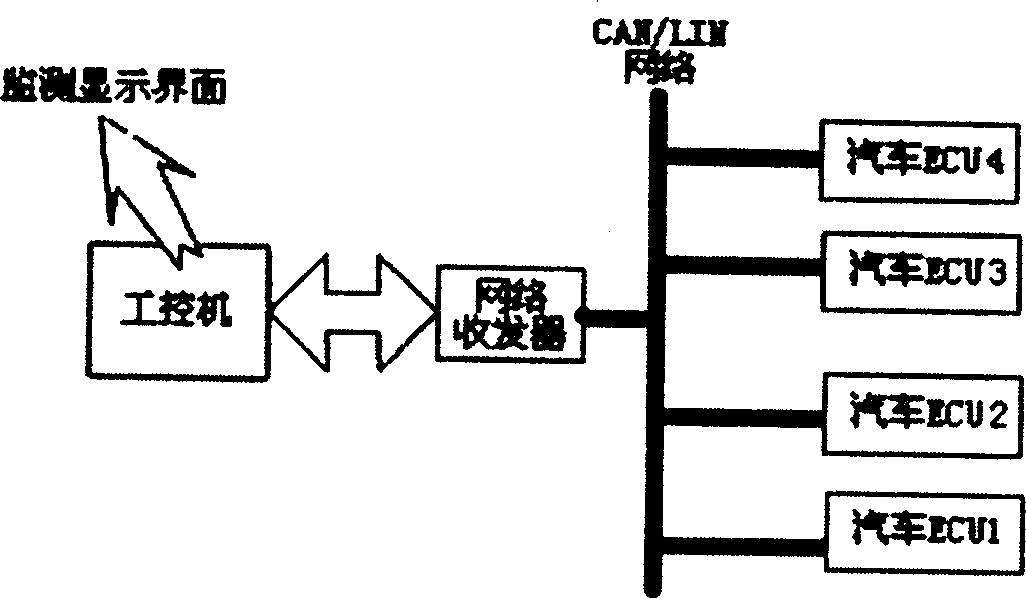
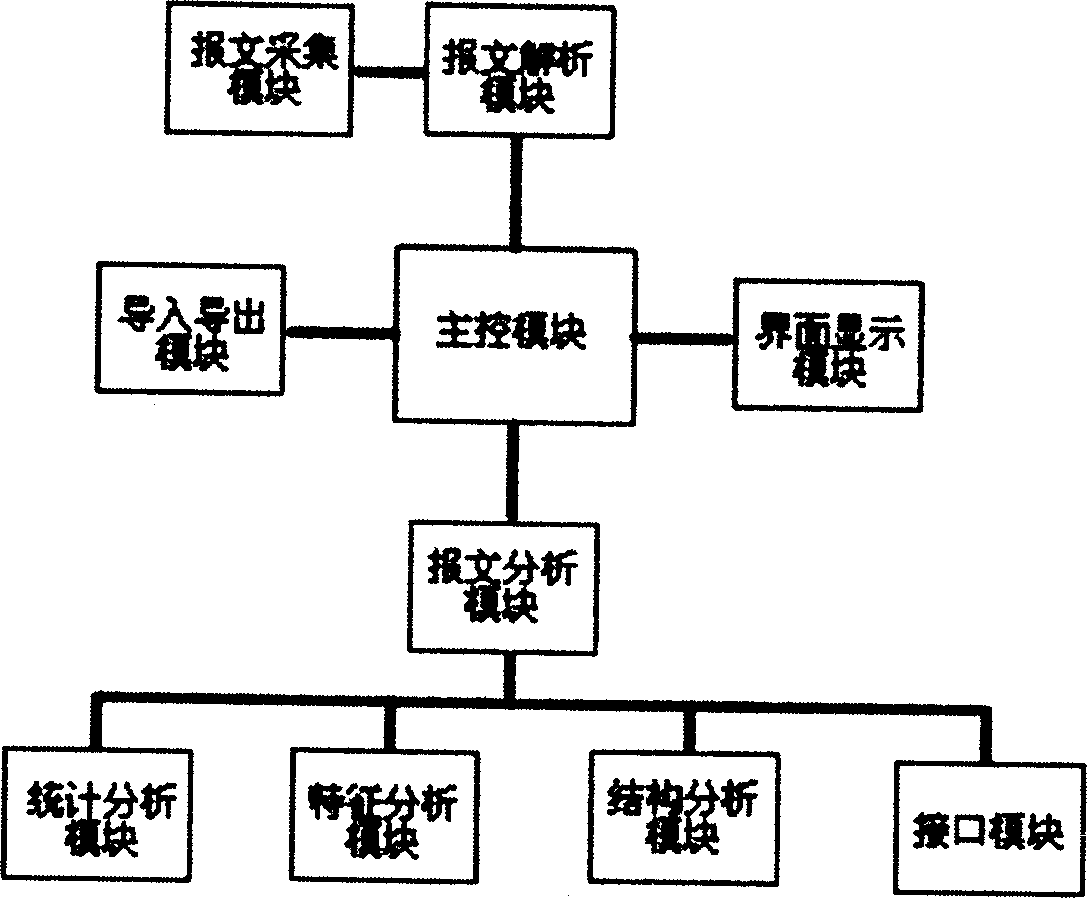
Monitoring instrument of vehicle control system CAN/LIN network and its test method
InactiveCN1794123AReal-time accurate node work efficiencyAccurate analysisElectric testing/monitoringData switching networksNetwork detectorTransceiver
A CAN / LIN network detector of vehicle control system is prepared as using industrial control computer to form detector, connecting CAN / LIN network transceiver to vehicle electric interface for collecting network message information and sending it to industrial control computer through serial bus interface or USB interface; applying modularization structure on industrial control computer to analyze node working efficiency, network node state, network load state and so on in real time accurately.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
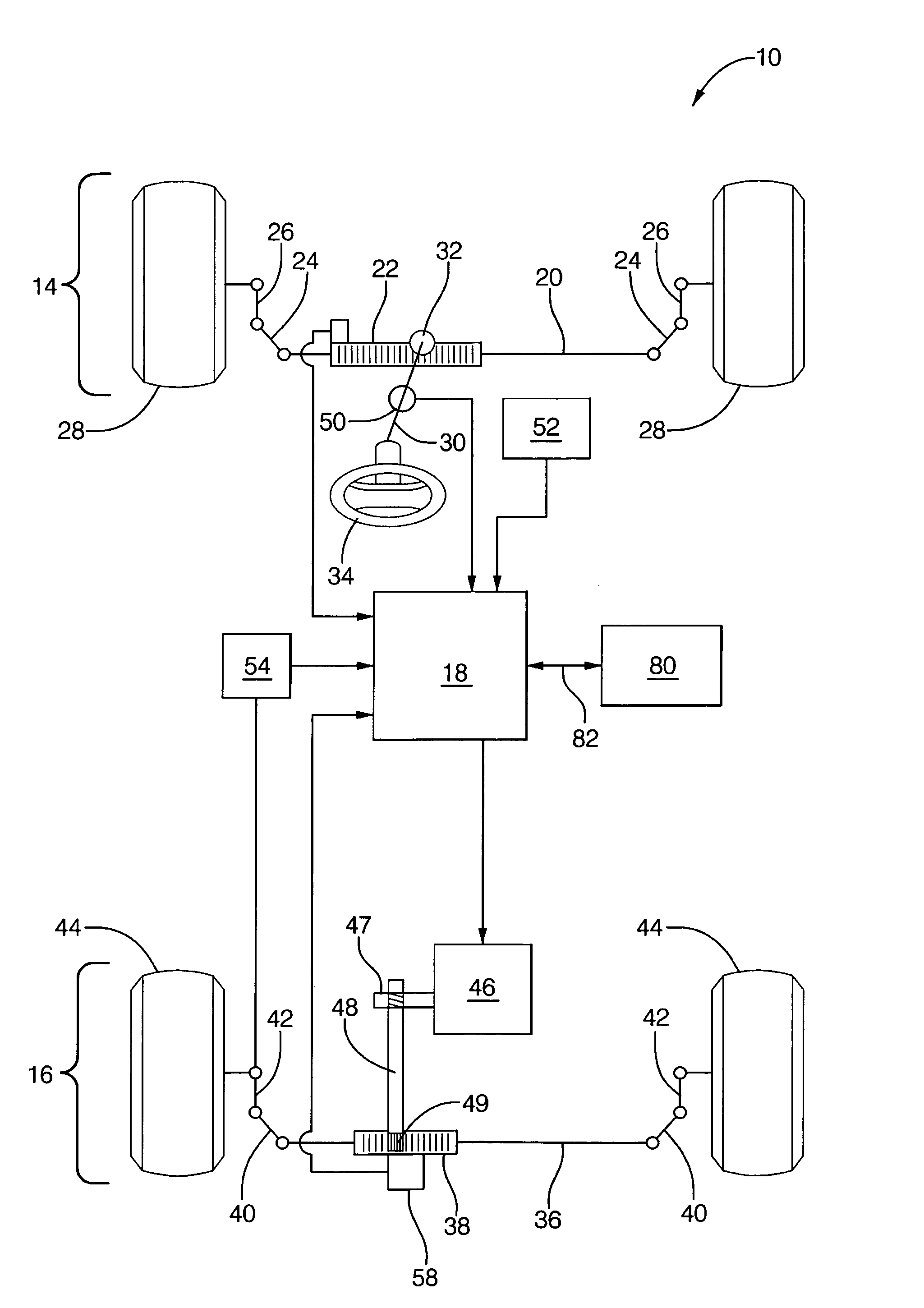
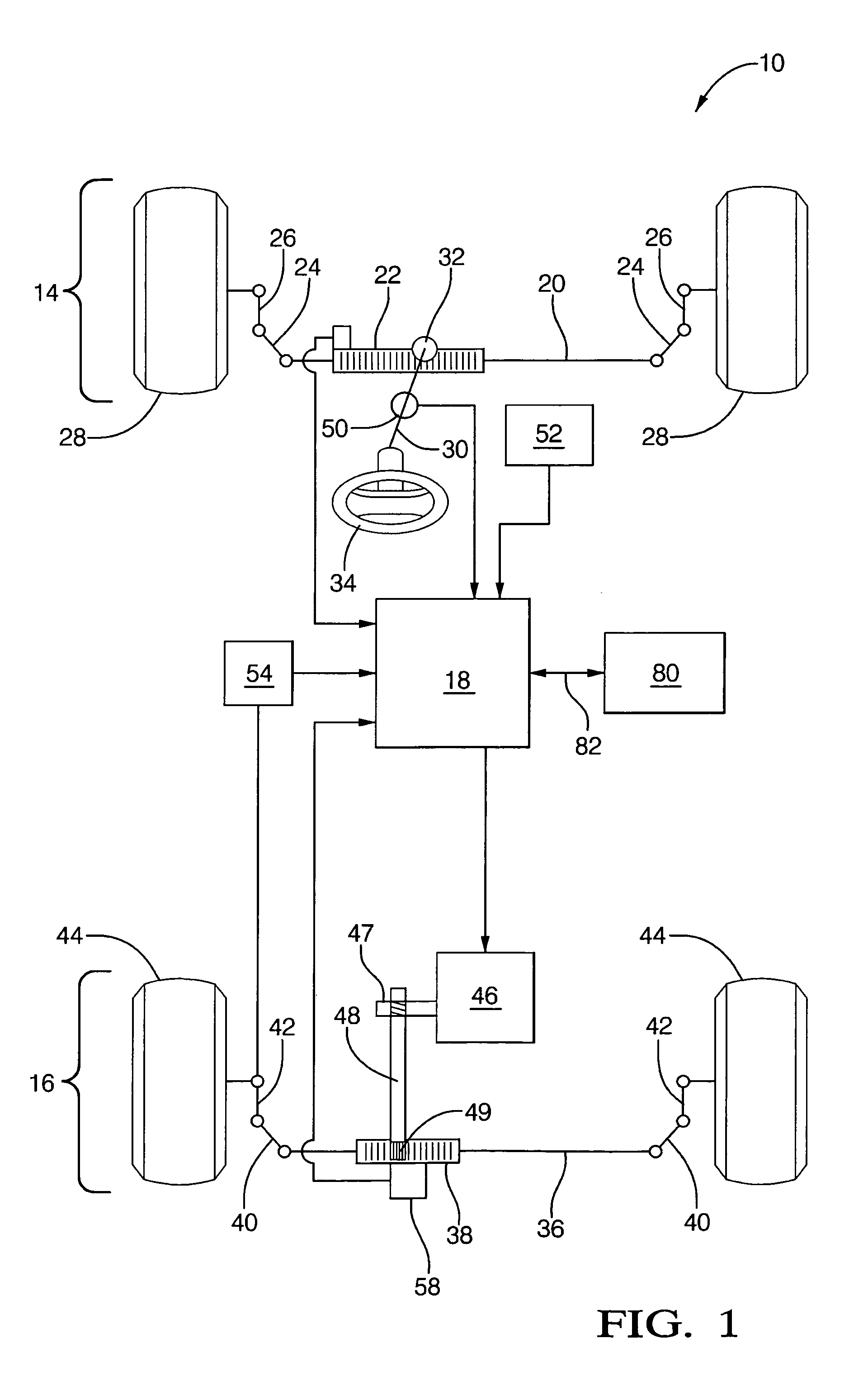
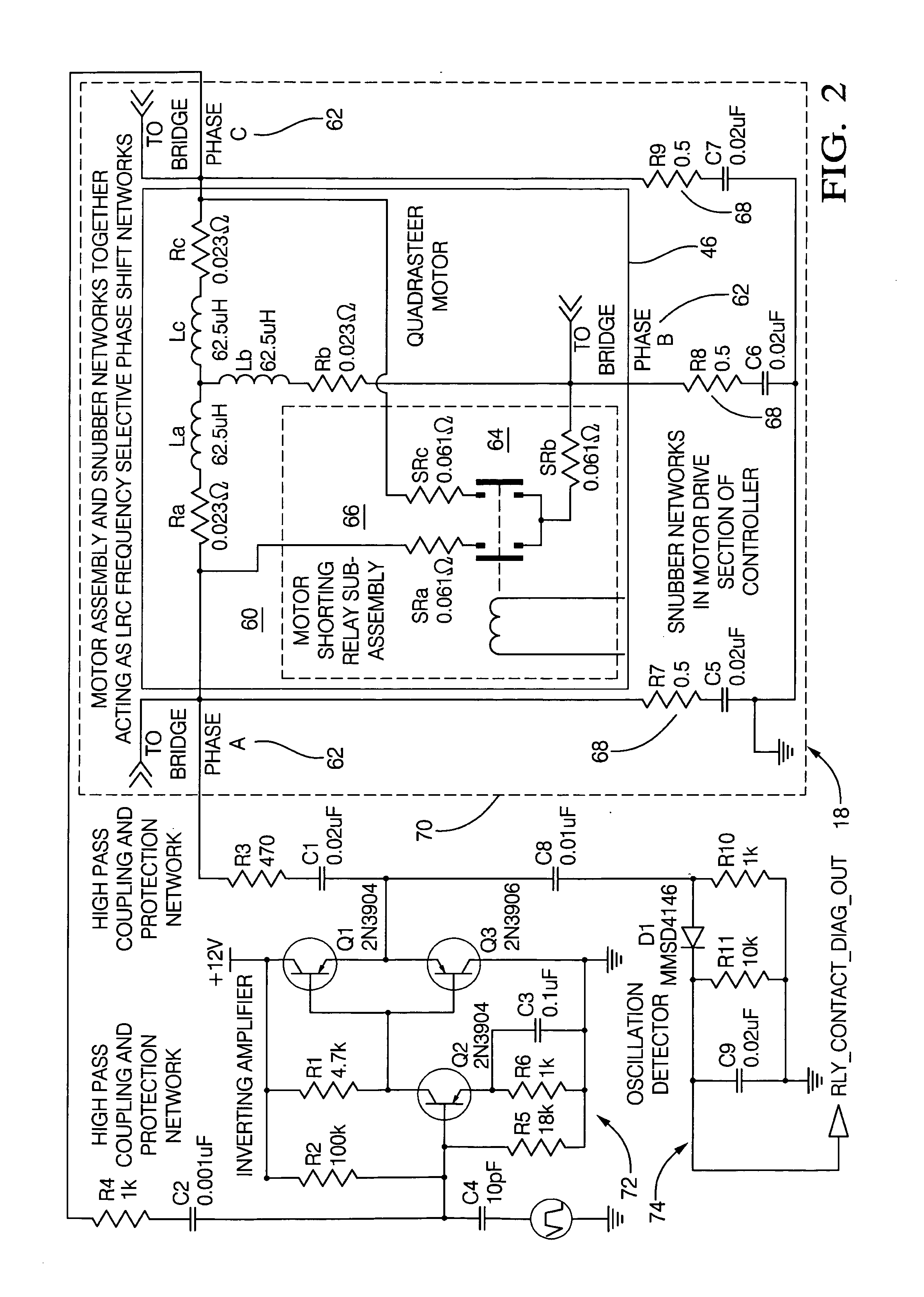
Method and apparatus for diagnosing motor damping network integrity
InactiveUS20060271336A1Electric devicesResistance/reactance/impedenceDetector circuitsNetwork detector
An apparatus for diagnosing motor damping network integrity, the motor damping network configured for selective short-circuiting of the windings of a motor in a motor control system. The apparatus includes a motor controller with a motor drive portion thereof electrically isolated from the windings of the motor. A resonant network is based on the windings of the motor, the damping network, and a remaining non-isolated portion of the controller. An amplifier circuit applies an excitation signal to the resonant network. A detector circuit detects a response of the resonant network based on the excitation signal. A state of the damping network is determined based on the response.
Owner:STEERING SOLUTIONS IP HLDG +1
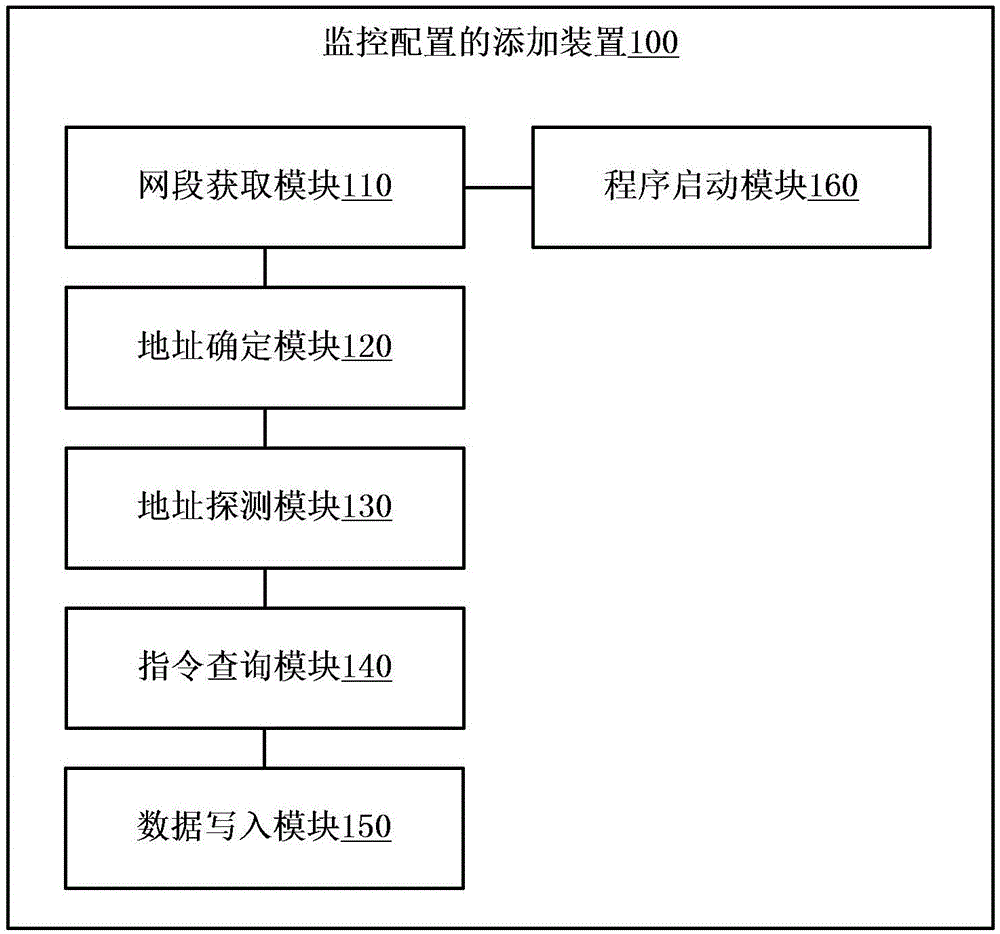
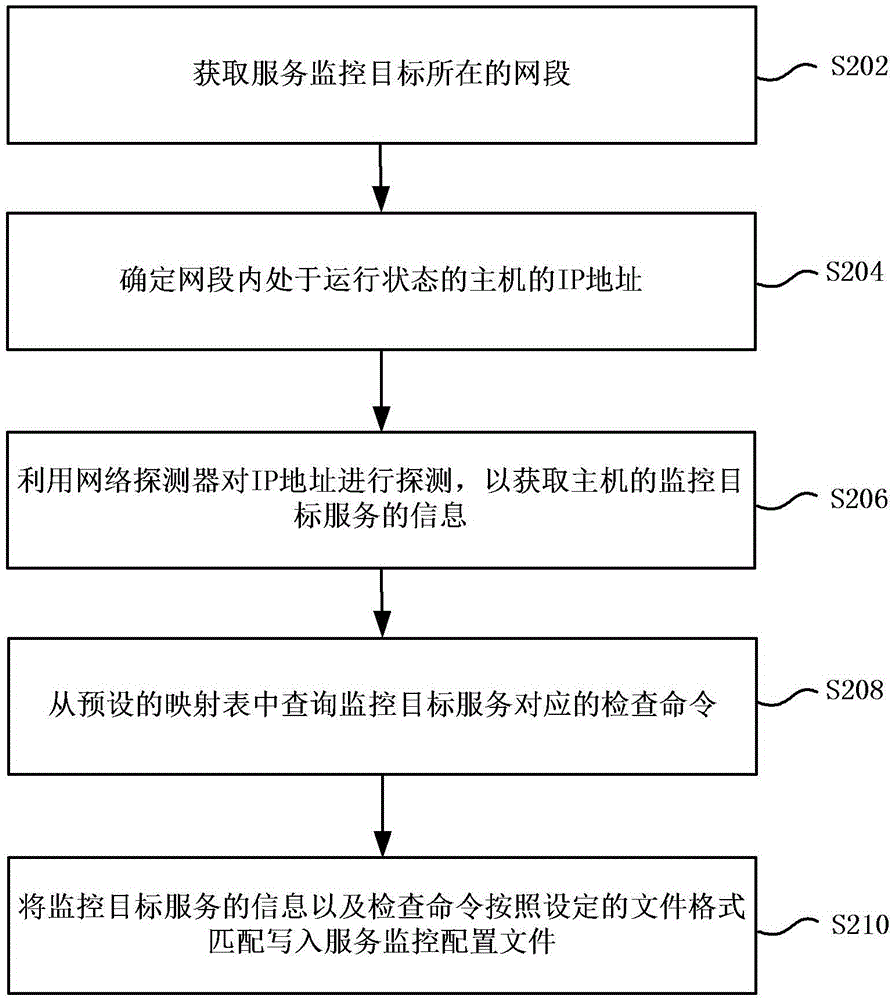
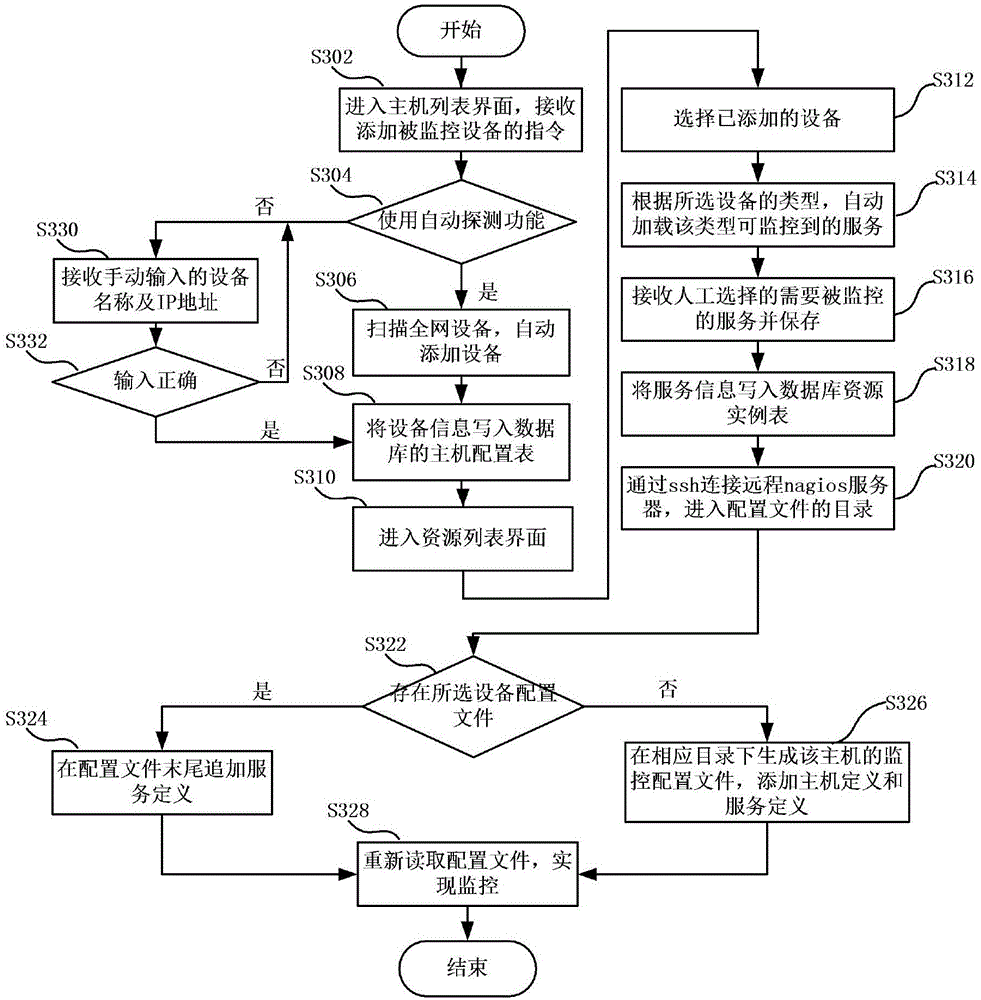
Addition method and device for monitoring configuration
InactiveCN105141449AEasy to configureReduce waiting timeData switching networksNetwork detectorIp address
The invention provides addition method and device for monitoring configuration. The addition method for monitoring configuration comprises the following steps of: acquiring a network segment wherein a monitoring target is located; determining an internet protocol (IP) address of a hose in a running state in the network segment; detecting the IP address by using a network detector to acquire information of monitoring target service of the host; inquiring a detection command corresponding to the monitoring target service in a predetermined mapping table, wherein the detection command information corresponding to each type of service is stored in the mapping table; and writing the information of the monitoring target service and file format matching set according to the detection command into a service monitoring configuration file so that a monitoring server performs service monitoring according to the service monitoring configuration file. With the adoption of the scheme provided by the invention, the configuration time is greatly reduced, the workload of a network management person is reduced, and the service monitoring configuration on the various types of the hosts is facilitated.
Owner:CHINA STANDARD SOFTWARE
Airplane engine air compressor stall detection method
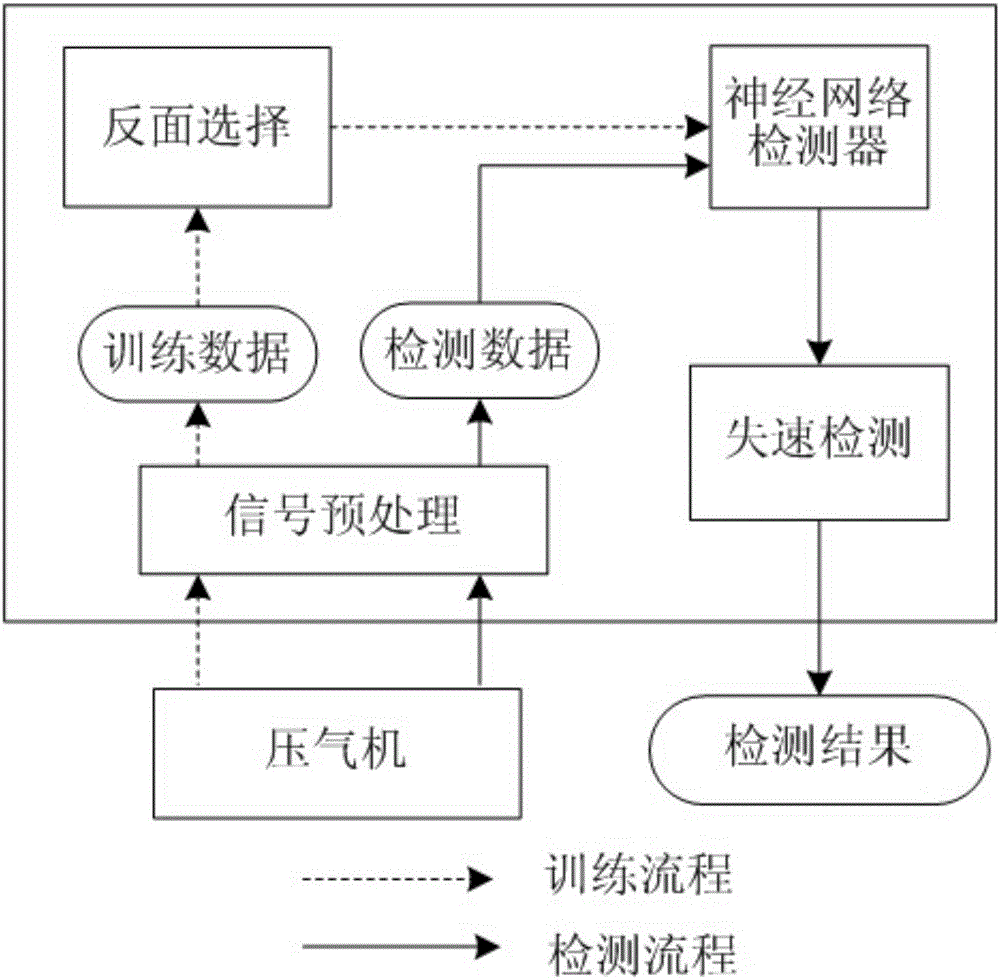
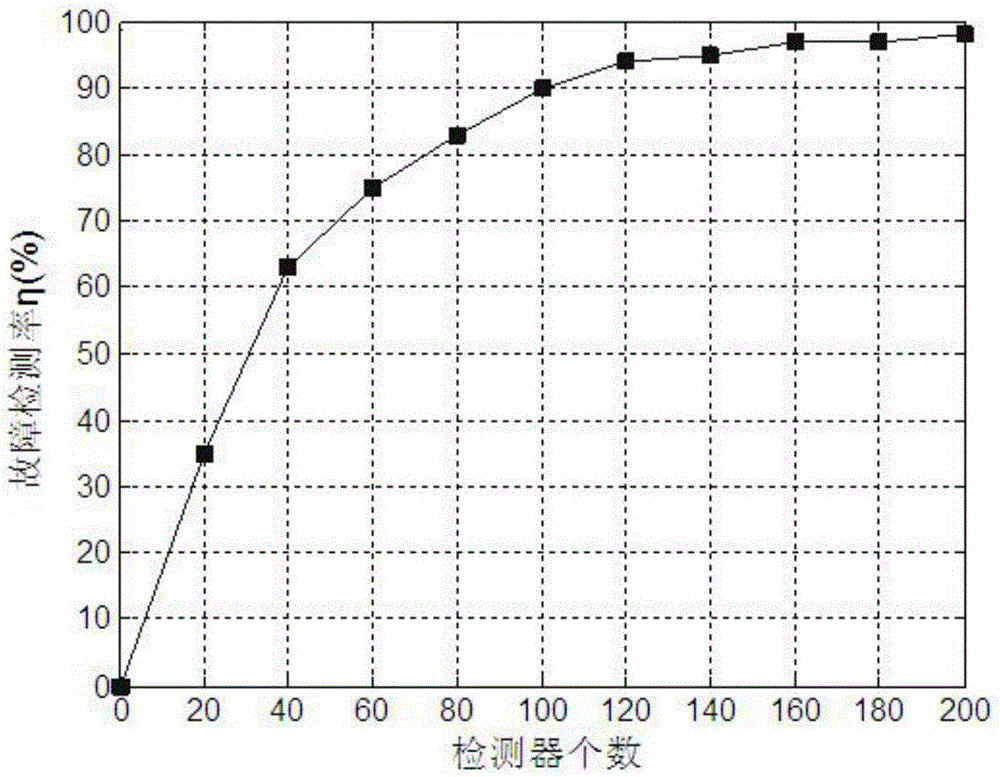
InactiveCN105094118AAccurate and effective detectionEasy fault detectionElectric testing/monitoringAxial compressorArtificial immune system
The invention discloses an airplane engine air compressor stall detection method. The method comprises steps: a sensor is firstly used for collecting pressure signals when the air compressor is in a normal working condition or in a stall condition, and pretreatment is carried out; a negative selection principle in an artificial immune system is then used for building a neural network detector, and the fault detection ability of the detector is improved through training; and finally, stall detection is carried out on the acquired airplane engine air compressor pressure fluctuation signals with a fault label. The negative selection principle in the artificial immune system is used for building the neural network detector, abnormal mode information of the air compressor is stored in the distributed detector through training, fault is found out according to activation of the detector, stall signals can be detected instantly when stall happens, and the detection speed is improved; existing historical data are fully used through training, and the detection rate is improved; and stall of the airplane engine air compressor can be accurately and effectively detected.
Owner:中国人民解放军空军勤务学院
Electronic detonator network detector and detection method
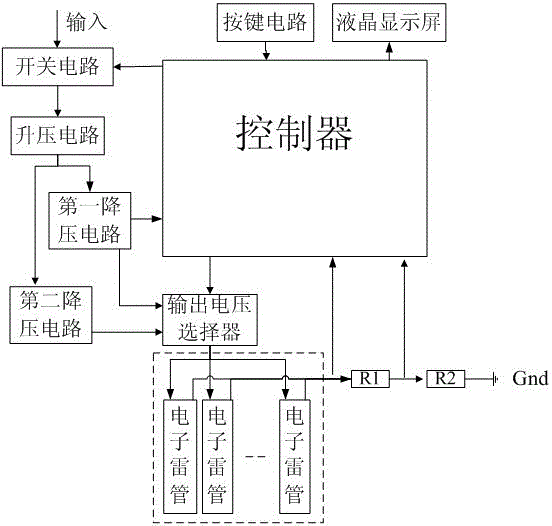
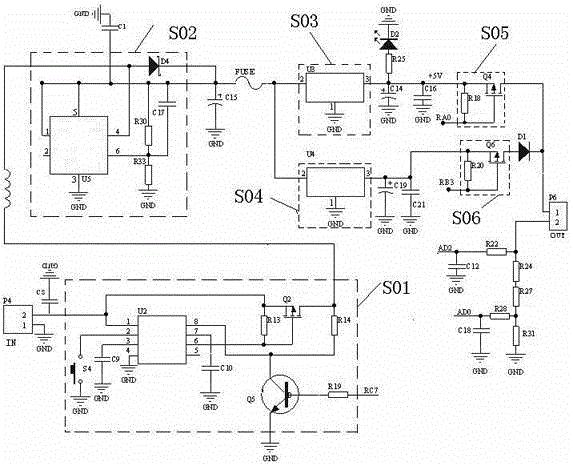
ActiveCN102980451AAvoid false triggeringEasy to troubleshootAmmunition fuzesNetwork detectorLow voltage
The invention relates to the field of detection of electronic detonators and particularly relates to a detonator network detector and detection method. The detonator network detector aims at solving the problems of network state detection before the blasting of electronic detonators. The electronic detonator network detector can detect short circuit, circuit breakage, creepage and other situations of an electronic detonator network with low voltage and low current, and the electronic detonators are intrinsically safe during the whole detection process. According to the electronic detonator network detector and detection method, the state detection of the electronic detonators of the electronic detonator network can be completed by a power supply unit, an output voltage selector, a sampling circuit, a display control unit, a processor and the like which are matched for treatment. The electronic detonator network detector and detection method disclosed by the invention are mainly applied to the field of state detection of the electronic detonators.
Owner:WUXI SHENGJING ELECTRONICS TECH CO LTD
Automatically configuring of a lighting
ActiveUS20130293115A1Automatic lighting configuration more robustNoise robustElectrical apparatusElectric light circuit arrangementComputer hardwareLearning based
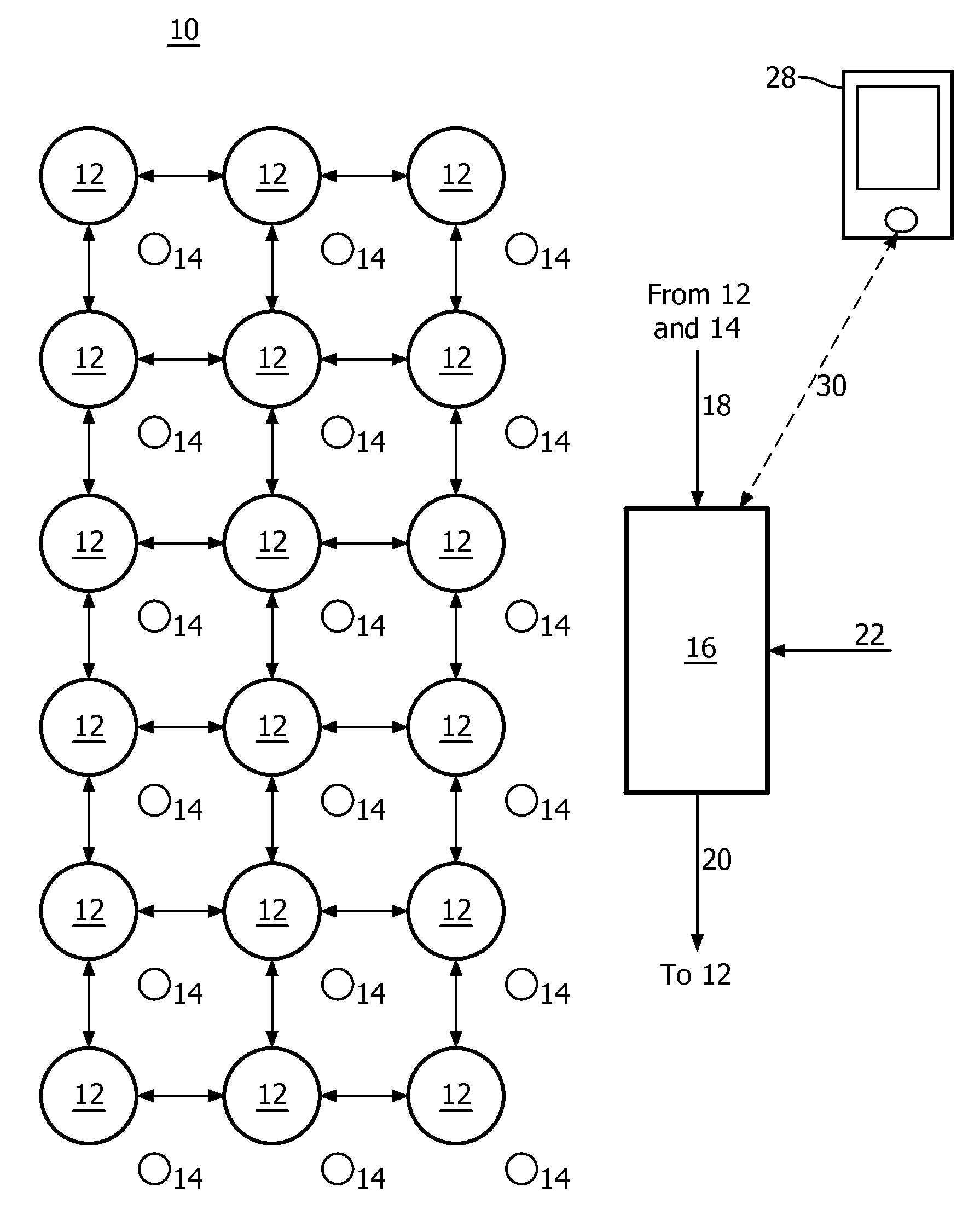
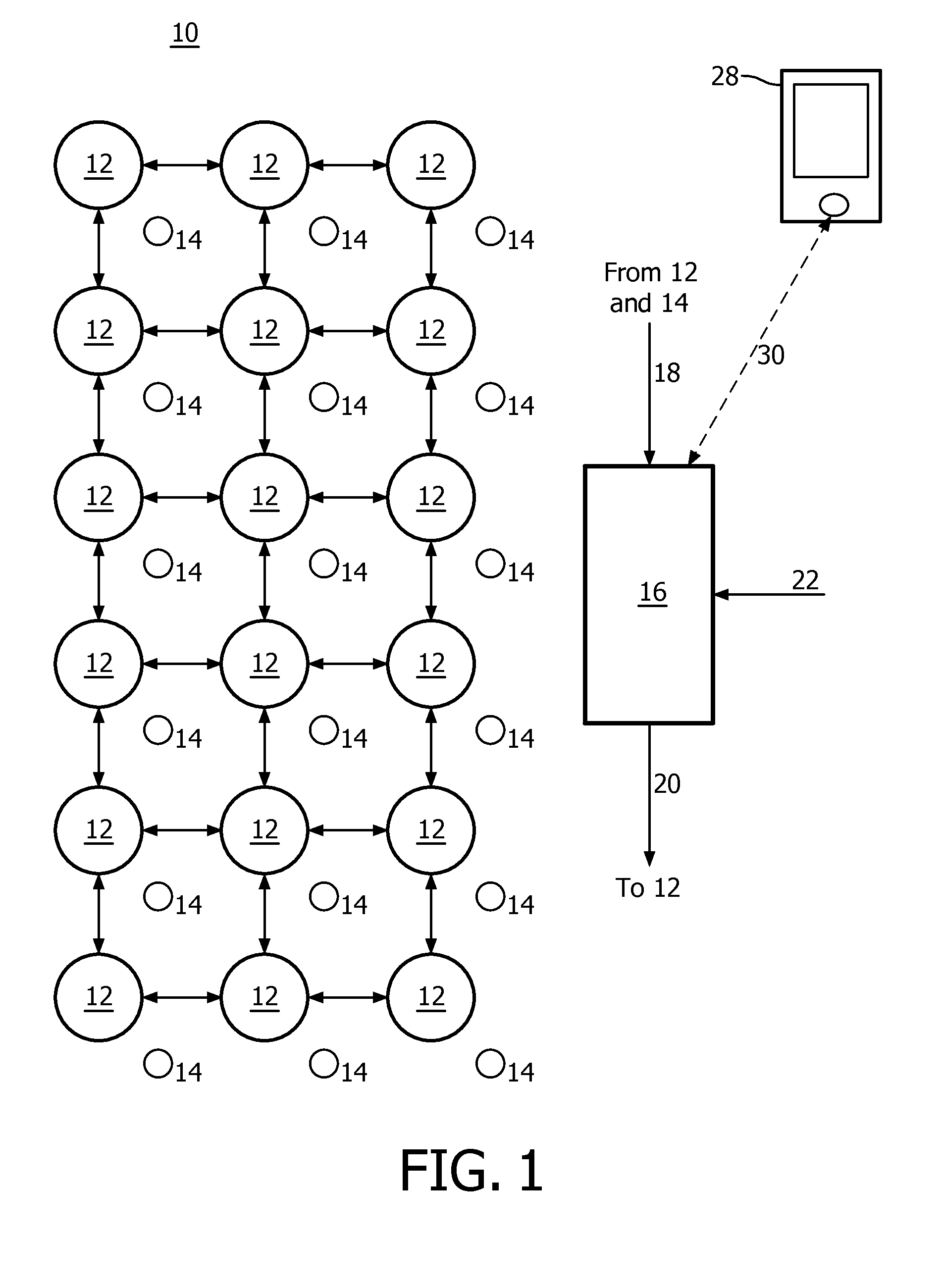
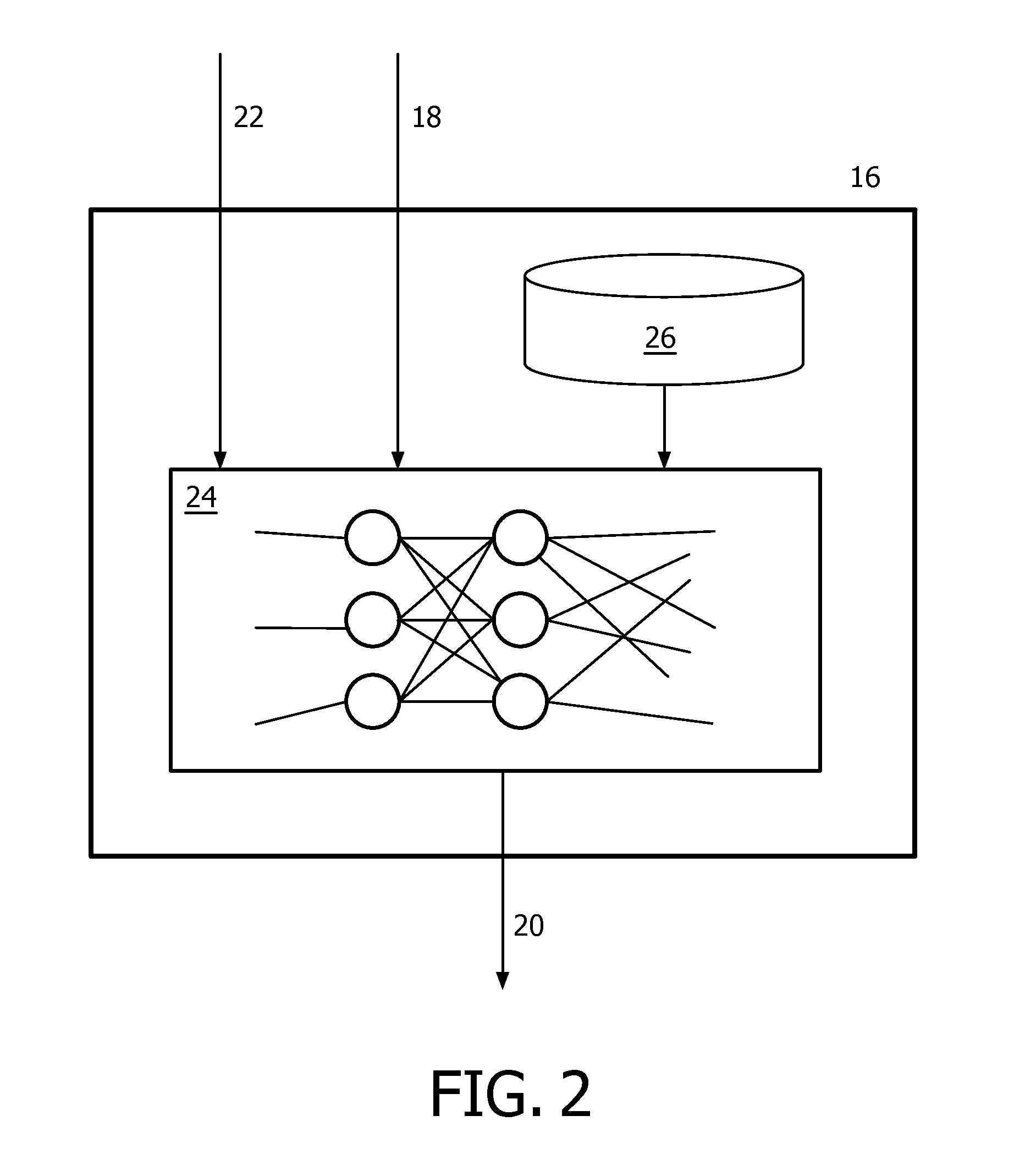
The invention relates to automatically configuring of a lighting created by a lighting system, particularly to creating a lighting, which follows a person, with a networked lighting system. A basic idea of the invention is to adapt the learning based processing of activations of lamps and presence detectors received as input data to changes in a system for automatically configuring lighting with a variable adaptation rate in order to make the automatic lighting configuration more robust with regard to system changes. An embodiment of the invention relates to a system (10) for automatically configuring a lighting, wherein the system comprises—a network of lamps (12), wherein each lamp is activated by a control signal and outputs its activation,—a network of presence detectors (14), wherein each presence detector is activated by detecting an activity and outputs its activation, and—a lighting configurator (16) for processing activations of lamps and presence detectors received as input data (18) based on learning and outputting control signals (20) for lamps depending on the processed input data for configuring the lighting, wherein the processing of input data by the lighting configurator can be adapted to changes in the system with a variable adaptation rate (22).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Traffic flow statistical method in intelligent traffic
InactiveCN110009023AAccurate Traffic DataStrong data supportImage enhancementImage analysisNetwork detectorVehicle detection
Owner:杭州电子科技大学上虞科学与工程研究院有限公司 +1
Organizing computer network identifications and concurrent application of policy selectors
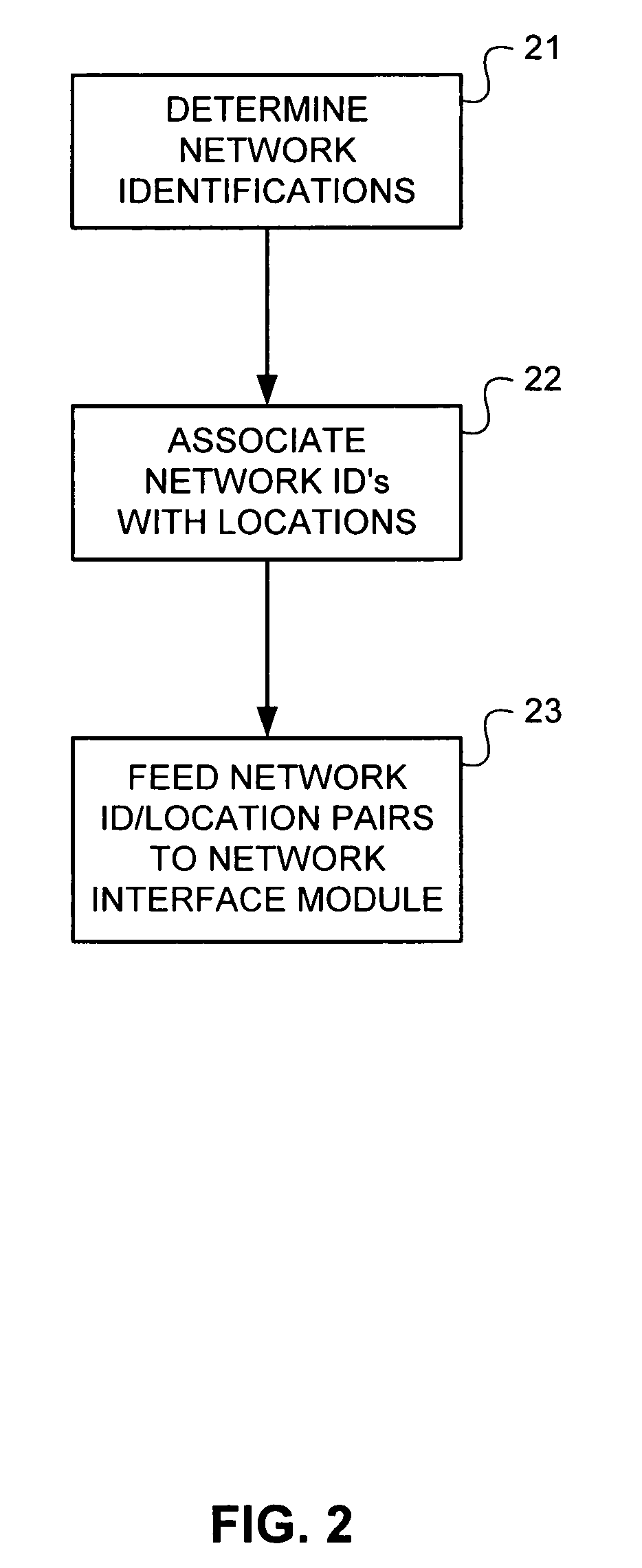
InactiveUS7870297B1Multiple digital computer combinationsPlatform integrity maintainanceNetwork detectorClient machine
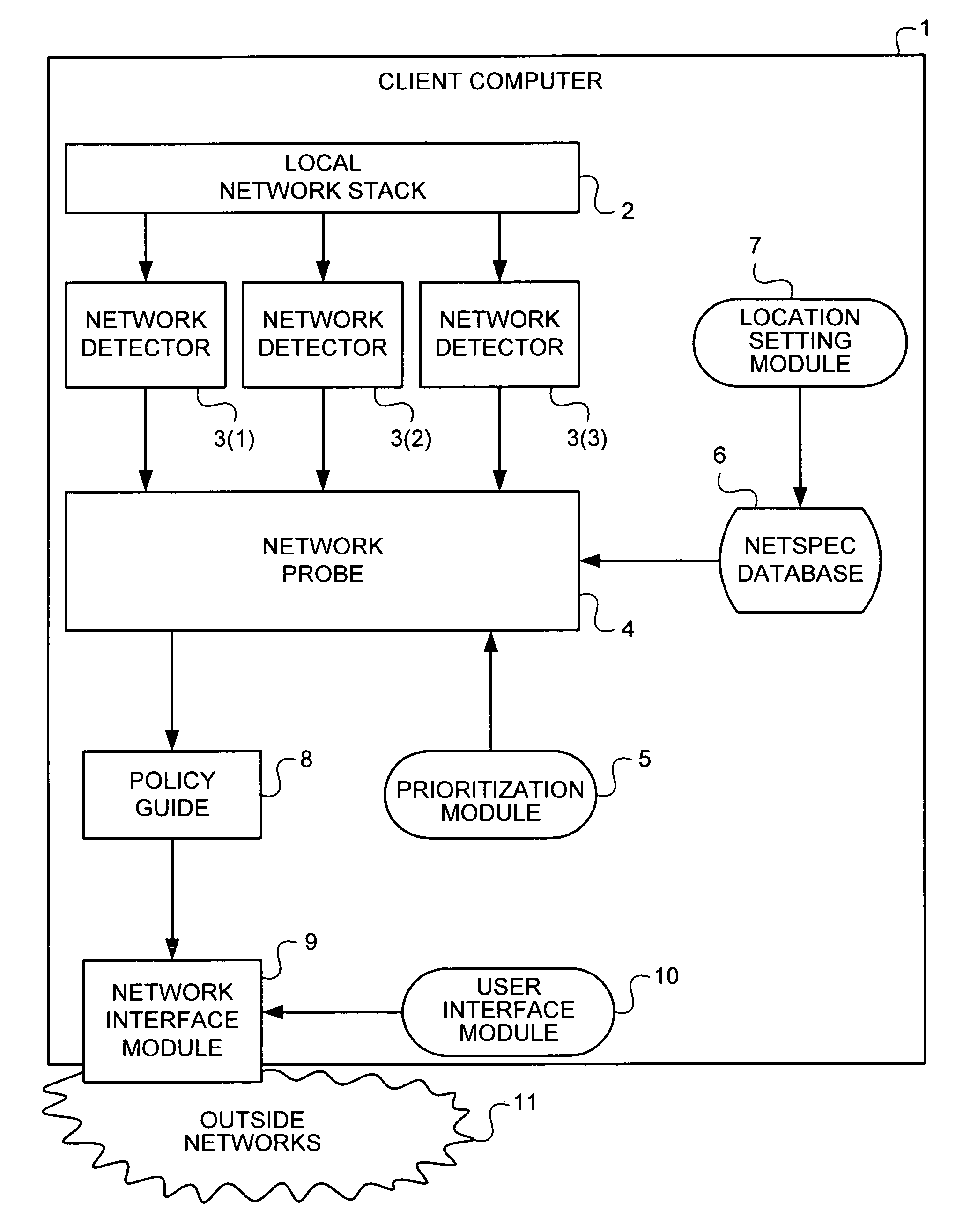
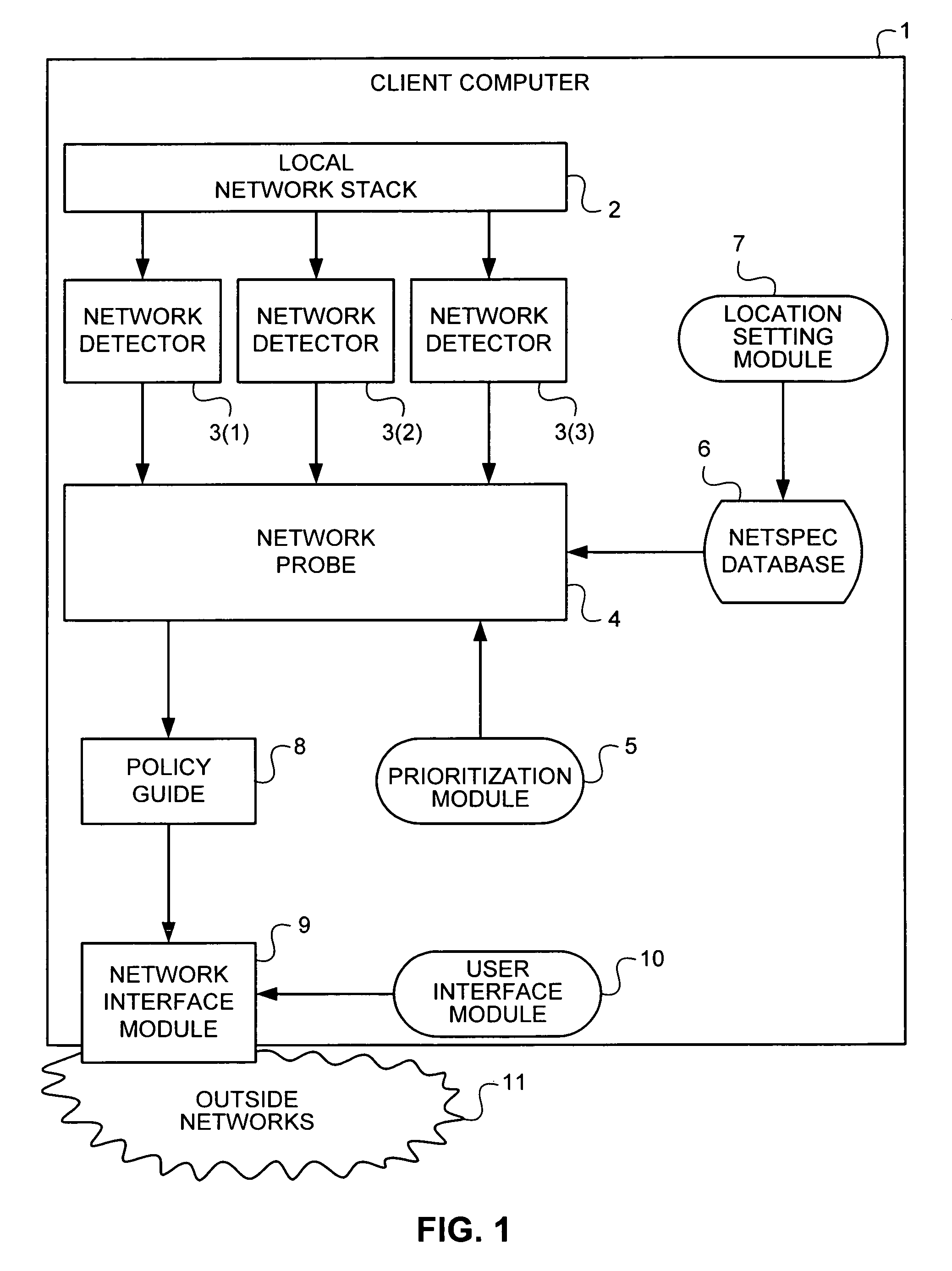
Methods, apparati, and computer-readable media for associating computer network identifications with network policies. A plurality of network detectors (3) are coupled to a client computer (1). A network probe (4), coupled to the network detectors (3), associates each network identification revealed by a network detector (3) with a netspec. A netspec database (6), coupled to the network probe (4), associates netspecs with locations. A policy guide (8), coupled to the network probe (4), associates network identifications with locations. A network interface module (9), coupled to the policy guide (8), implements network policies based upon locations.
Owner:CA TECH INC
Device and method for point-to-point (P2P) downloading based on internetwork protocol standards
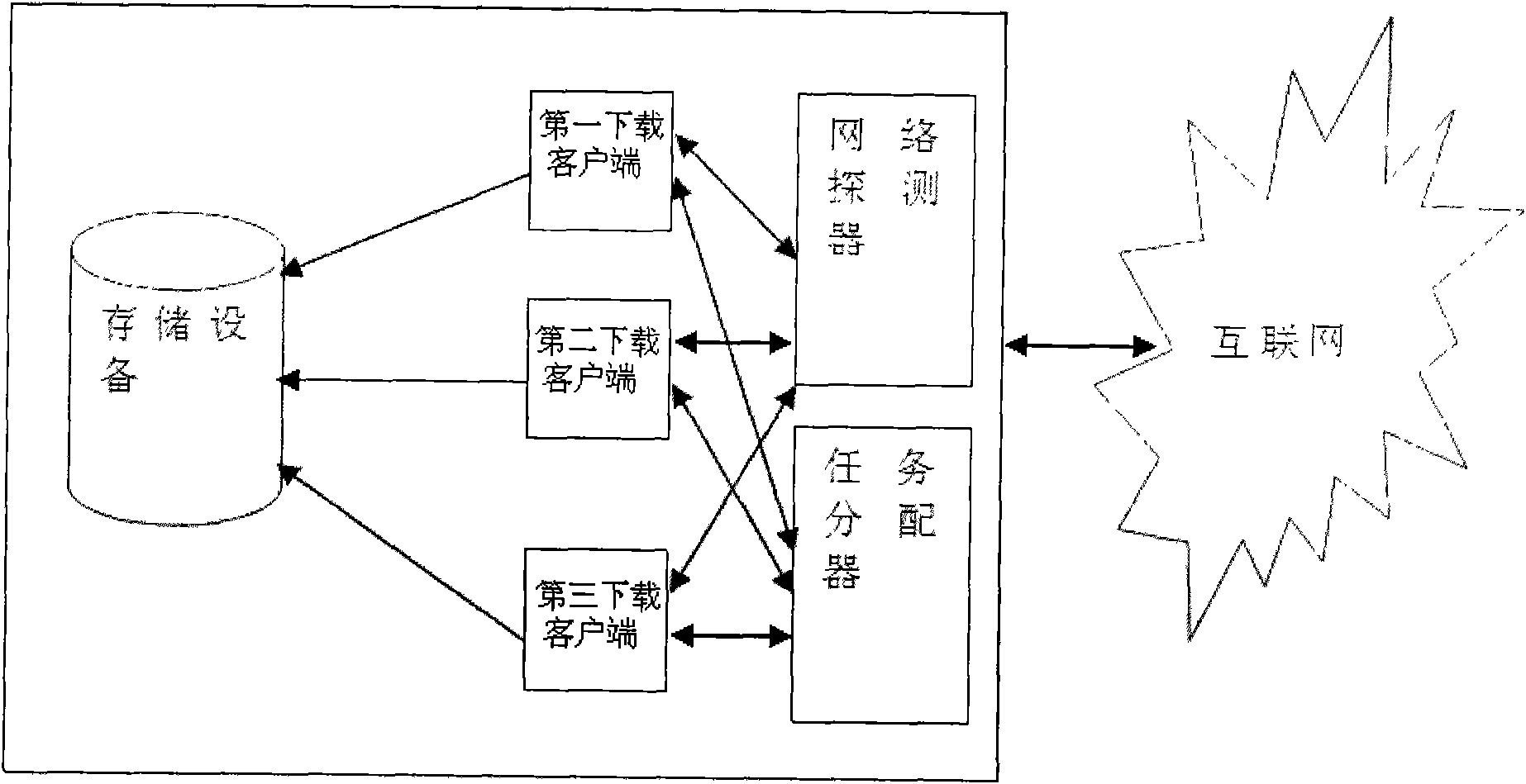
InactiveCN102055805AImprove download performanceImprove download speedTransmissionNetworking protocolNetwork detector
The invention belongs to the technical field of network downloading, and in particular relates to a device and method for point-to-point (P2P) downloading based on internetwork protocol standards. The device for point-to-point (P2P) downloading based on the internetwork protocol standards comprises a storage device, at least one downloading client, a network detector and a task distributor, wherein the storage device is used for storing network resources downloaded by the downloading client; the network detector and the task distributor are respectively connected with the downloading client; the network detector is used for detecting and calculating the network resource downloading speeds of different downloading clients; the task distributor is used for distributing downloading tasks in accordance with the network resource downloading speeds counted by the network detector, of the different downloading clients; and the downloading clients are used for downloading in accordance with the downloading tasks distributed by the task distributor. The technical scheme in the invention has the advantages or beneficial effects that the downloading capacity of the downloading clients for the resources is improved maximally, and the whole downloading speed is strengthened maximally.
Owner:TCL CORPORATION
Computer network safety control device for teaching
InactiveCN106325340AStrong security reminderImprove cooling effectSimultaneous control of multiple variablesNetwork detectorSafety control
The invention discloses a computer network safety control device for teaching, comprising a control box body, wherein the top end in the control box body is provided with a fan and the middle is provided with a thermal baffle, a controller is set at the top end of the thermal baffle, one side of the controller is provided with a humidity sensor, one side of the controller is provided with a data storage of which one side is provided with a signal projector, inner power is set at one side of the signal projector, one side of the inner power is provided with a temperature sensor, the bottom end in the control box body is provided with a network transmission line, a network detector is set in the middle of the network transmission line, and one side of he network detector is provided with a relay. The computer network safety control device for teaching can radiate and dehumidify to improve the service life of the control device, meanwhile, when the network occurs unsafe factors,the computer can be disconnected for the first time, so the control device has stronger network safety reminding effect.
Owner:四川联同创新科技有限公司
Cloud platform malicious behavior detecting system and method
InactiveCN106713293AScan accuratelyReliable identificationTransmissionNetwork detectorNetwork attack
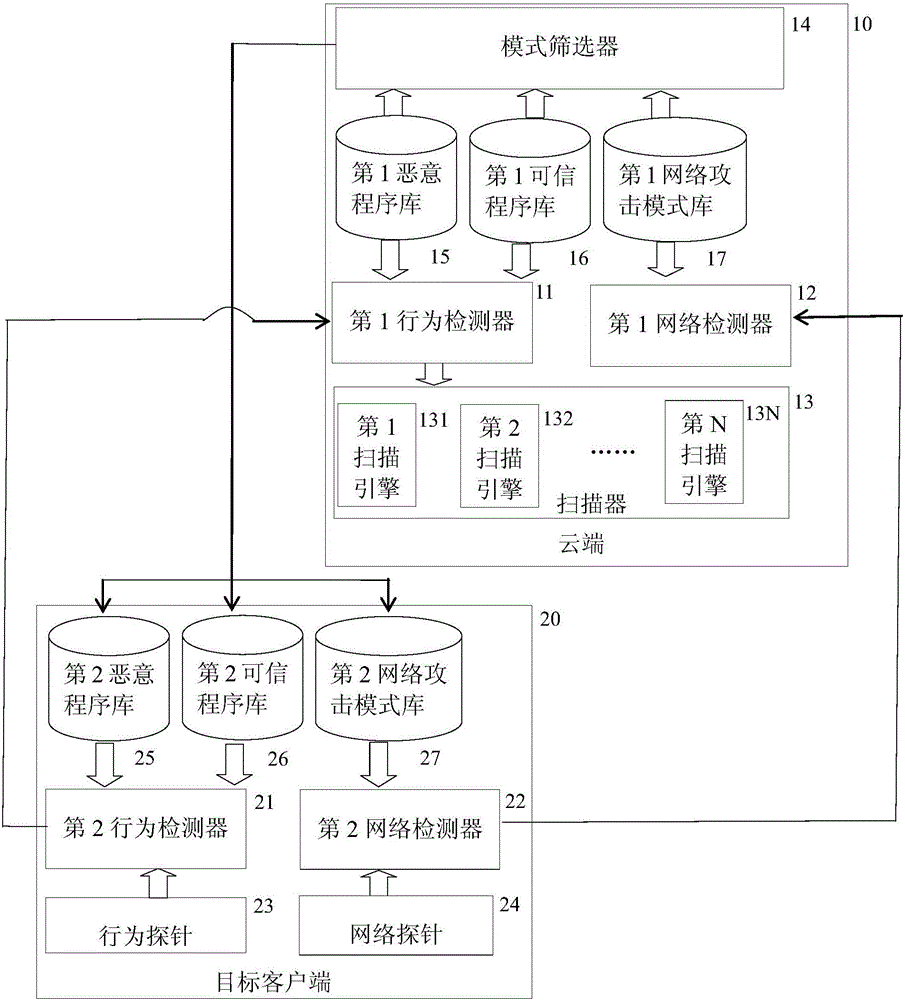
The invention discloses a cloud platform malicious behavior detecting system and method, and relates to the field of malicious behavior detection. The cloud platform malicious behavior detecting system comprises a cloud end (10) and a target client (20); the cloud end (10) comprises a first behavior detector (11), a first network detector (12), a scanner (13), a mode sieving device (14), a first malicious program library (15), a first trusted program library (16) and a first network attack mode library (17); the target client (20) comprises a second behavior detector (21), a second network detector (22), a behavior probe (23), a network probe (24), a second malicious program library (25), a second trusted program library (26) and a second network attack mode library (27). The cloud platform malicious behavior detecting system and method has advantages of high efficiency, accuracy, rapidity, expandability and wide adaptability.
Owner:WUHAN HONGXU INFORMATION TECH
Automatic switching-off device of router
InactiveCN102694737AExtended service lifeSave powerData switching networksNetwork detectorNetwork connection
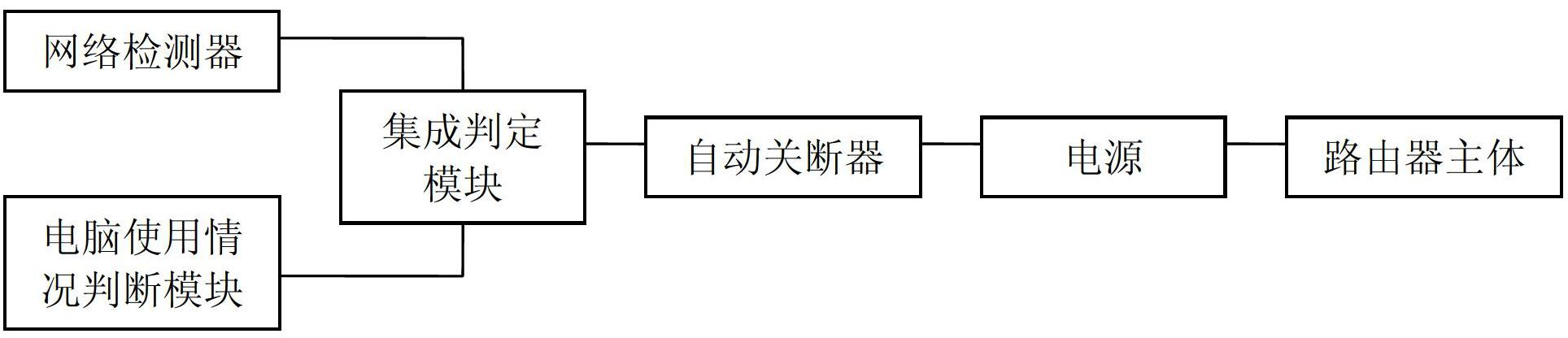
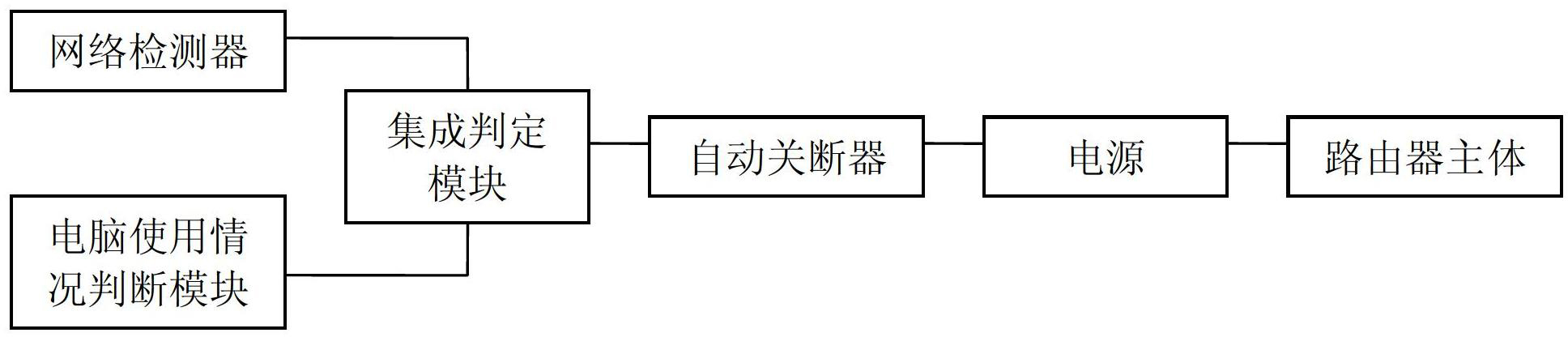
The invention discloses an automatic switching-off device of a router and belongs to the technical field of automatic switching-off. The automatic switching-off device comprises a router and a power supply connected with the router; the automatic switching-off device further comprises an automatic switching-off machine connected with the power supply and an integration judging module connected with the automatic switching-off machine; and the integration judging module is further connected with a network detector and a computer use condition judging module. The device can perform automatic judgment and switch off the power supply of the router according to the condition whether a network is connected or not and whether a computer is used or not, so that the electric energy and the network flow are saved and the service life of the router is prolonged.
Owner:XUZHOU HAOWEI MINING EQUIP
Web browser security
InactiveUS8230060B2Multiple digital computer combinationsPlatform integrity maintainanceNetwork detectorWeb browser
Owner:INT BUSINESS MASCH CORP
Intelligent pipe gallery information management method and system based on cloud processing
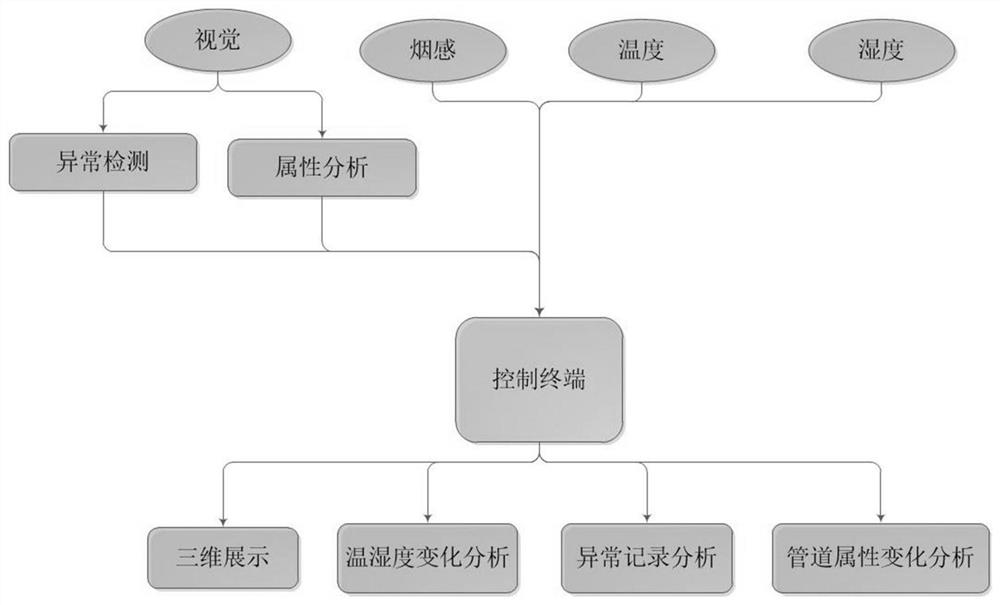
PendingCN112766795AEffective integrated analysis managementFast daily operation and maintenanceCharacter and pattern recognitionNeural architecturesVision processingCloud processing
The invention discloses a pipe gallery intelligent information management method and system based on cloud processing. The method comprises the following steps: acquiring an anomaly detection and attribute analysis data set; training a pipe gallery anomaly detection deep neural network model; training a pipe gallery attribute analysis deep neural network model; acquiring information such as smoke sensing, temperature, vision and humidity transmitted by the sensor group; for the visual information, using a deep network classifier to carry out anomaly detection on a newly obtained to-be-identified image; for the visual information, performing attribute analysis on a newly acquired to-be-processed image by using a deep network detector; and carrying out attribute set modification on all sensing information and visual processing information on the basis of the three-dimensional BIM model. According to the method, the pipe gallery can be effectively monitored and analyzed in real time, the maintenance and operation efficiency of the pipe gallery can be improved, and the human resource cost is saved.
Owner:长兴云尚科技有限公司
Alarm router optimizing strategy in target alarm system
ActiveCN105684394ALower latencyData processing applicationsTelephonic communicationNetwork detectorTerminal equipment
Described is a target alarm system which comprises a network detector which sends test data to terminal devices connected to a network and receives reliable data from the network. When target alarm information has to be sent, the system identifies a target terminal based on the reliable data so as to send the target alarm information. The invention also discloses related method, apparatus and non-provisional computer-readable media.
Owner:DRAGERWERK AG
Router convenient for network detection
The invention discloses a router convenient for network detection, and relates to the technical field of routers. A control main board is arranged in a casing body through a mounting column. A network input connector, a number of network output connectors and a USB connector are respectively arranged on the front end in the casing body. The network input connector is connected with one end of a network detector. The other end of the network detector is connected with the input end of the control main board. The output end of the control main board is connected with a number of network output connectors. The control end of the network detector is connected with an alarm. A power supply module and a power supply conversion module are arranged in the casing body. The power supply module is connected with the power supply end of the control main board and the input end of the power supply conversion module. The output end of the power supply conversion module is connected with the USB connector. The router provided by the invention is convenient for real-time network detection, has the advantages of convenient use, easy operation and time saving, is able to convert a power supply, and is convenient for carrying out charging at any time.
Owner:HENAN ECOSTOR ELECTRONICS TECH CO LTD
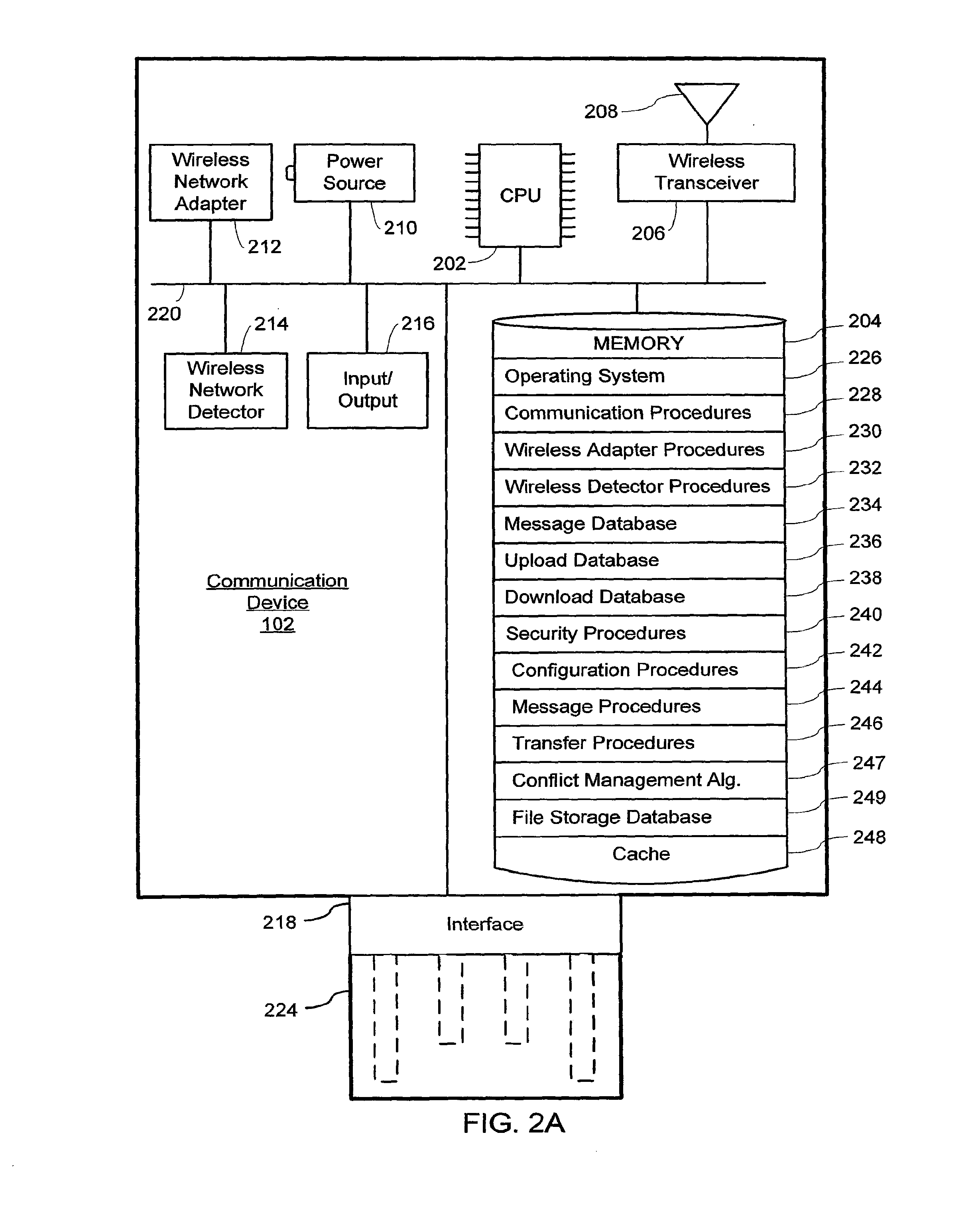
Wireless Detector and Adapter
ActiveUS20150133192A1Convenient wireless communicationEnhanced stand-aloneAssess restrictionSubstation equipmentNetwork detectorTransceiver
The handheld wireless network detector and adaptor includes a housing at least partially enclosing a processor, a self-contained power source, an interface, a wireless transceiver, a wireless network detector and a wireless network adapter. The interface is configured to communicate with an external computing device. The wireless transceiver is configured for transmitting and receiving radio signals. The wireless network detector is configured to use the wireless transceiver to detect a presence of a detected wireless network. The wireless network adapter is configured for facilitating real time communication between the external computing device and the detected wireless network via the interface and said wireless transceiver.
Owner:BORN JOSEPH
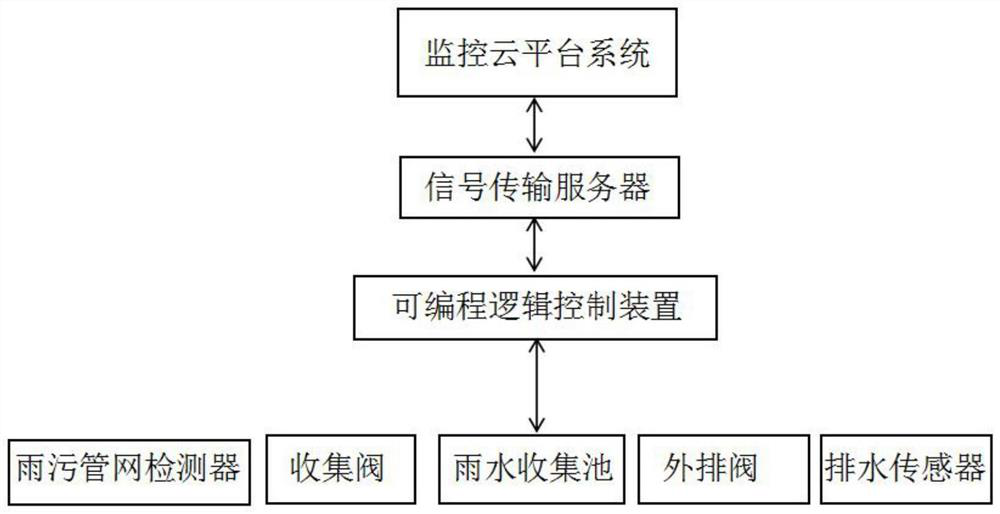
Municipal monitoring system for rainwater drainage
PendingCN113296550ARealize automatic regulationReduce labor costsLevel controlTransmissionNetwork detectorMonitoring system
A municipal monitoring system for rainwater drainage relates to the technical field of environment monitoring and comprises a rainwater and sewage pipe network detector, a collection valve, a rainwater collection pool, a programmable logic control device, a signal transmission server, a drainage valve, a drainage sensor and a monitoring cloud platform system. The rainwater and sewage pipe network detector, the collection valve, the rainwater collection pool, the programmable logic control device, the signal transmission server, the discharge valve and the drainage sensor are in circuit connection; and the programmable logic control device collects information of the rain and sewage pipe network detector, the rainwater collection pool and the drainage sensor. Signal transmission can be realized through the monitoring cloud platform system, an instruction is sent to the programmable logic control device, the operation of the whole system is controlled, the accumulation capacity of the rainwater collection pool is automatically regulated and controlled, and the labor cost is saved.
Owner:东营市天诚建材有限公司
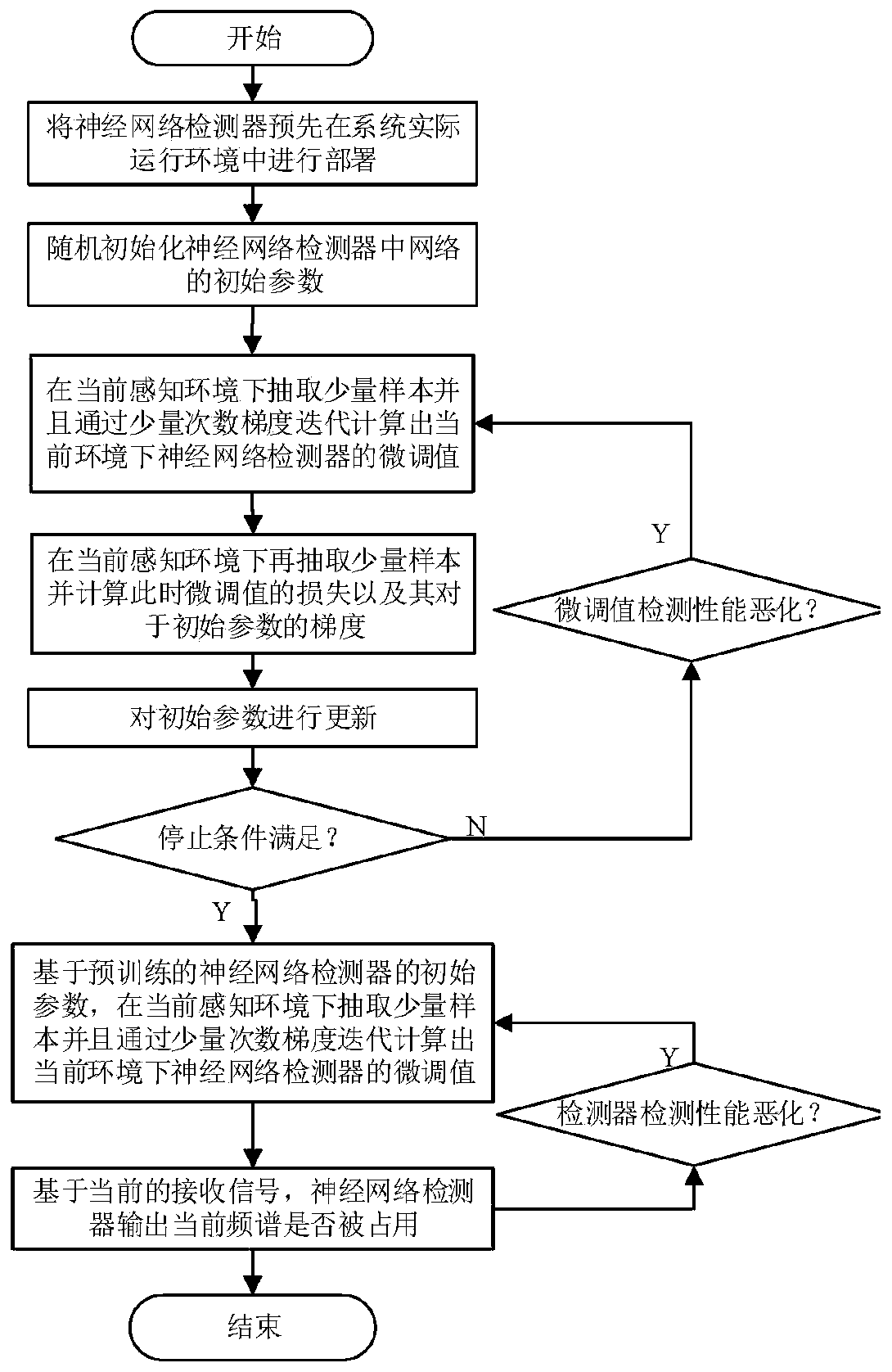
Spectrum sensing method based on small sample training neural network
ActiveCN111431645AReduce distractionsSimplify the commissioning processTransmission monitoringNeural architecturesFrequency spectrumNetwork detector
The invention provides a spectrum sensing method based on a small sample training neural network. The method comprises the following steps: pre-training a neural network detector; pre-deploying a detector in an actual operation environment of a system; calculating fine adjustment values and test loss values of the detector in different sensing environments through iteration of a small amount of data and a small amount of gradient, then calculating gradient of initial parameter corresponding to the loss value, conducting gradient updating on the initial parameter so that the initial parameter of the detector can rapidly adapt to change of the environment; performing online adjustment based on initial parameters of a pre-trained neural network detector; and inputting the sampled received signal into the adjusted neural network detector to predict the probability of whether the frequency spectrum is occupied at the moment. According to the spectrum sensing method, the detection performance similar to that of an existing neural network detector based on a large number of samples and gradient iteration can be achieved, and the calculation amount and the sample number required by detector adjustment can be effectively reduced.
Owner:NAT UNIV OF DEFENSE TECH
Digital watermarking infrastructure
InactiveCN100428107CReduce loadLower latencyDigital data processing detailsNetwork detectorPropagator
The present invention discloses basic watermark facility, and is one digital work copyright protecting system based on digital watermark. The user purchased legal digital work has two CA signature watermarks embedded, one identifying the publisher and the other identifying the purchaser. When illegal copying is found out with the network detector or memory medium based on movable deputy, the illegal propagator may be determined based these two watermark. The copyright information watermark of the publisher includes the publisher ID and the work ID, the digital fingerprint of the purchaser includes the purchaser ID, and these two watermarks are random sequence produced with the corresponding ID and through CA signature. The present invention uses the correlated concept of PKI system for tracing illegal copying and is simple, practical, reliable and expandable.
Owner:BEIJING UNIV OF POSTS & TELECOMM
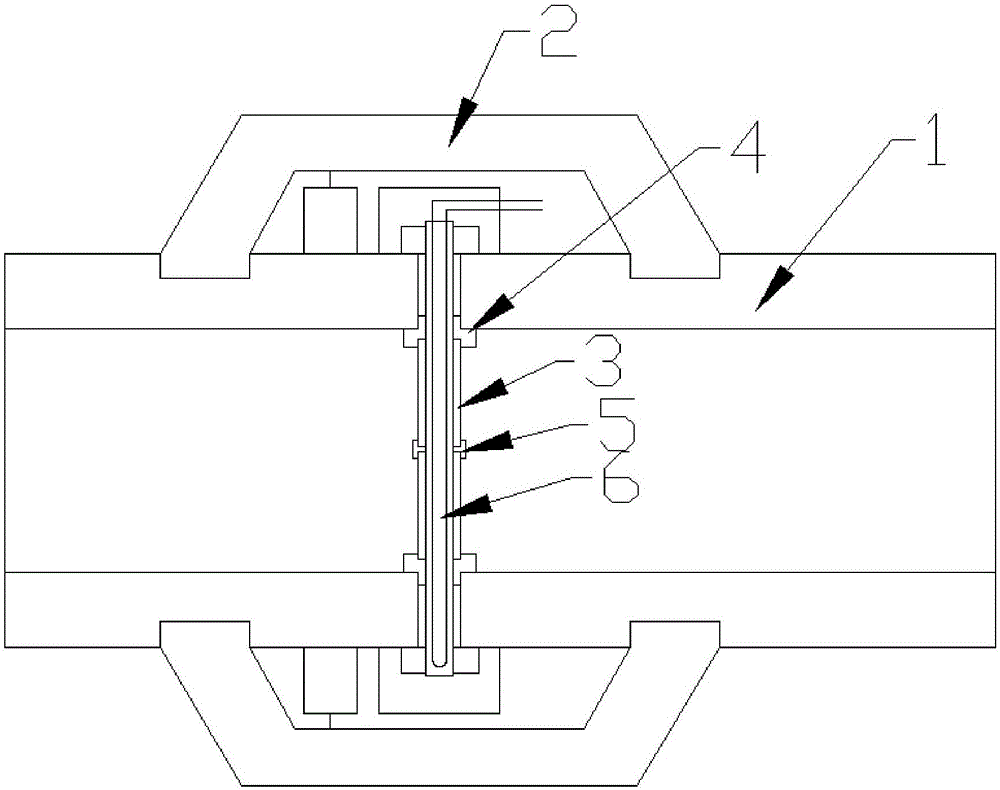
Beidou-based intelligent draining pipe network detector
InactiveCN106226790AMonitor water velocityImprove sensing sensitivityPipeline systemsSatellite radio beaconingElectrical resistance and conductanceNetwork detector
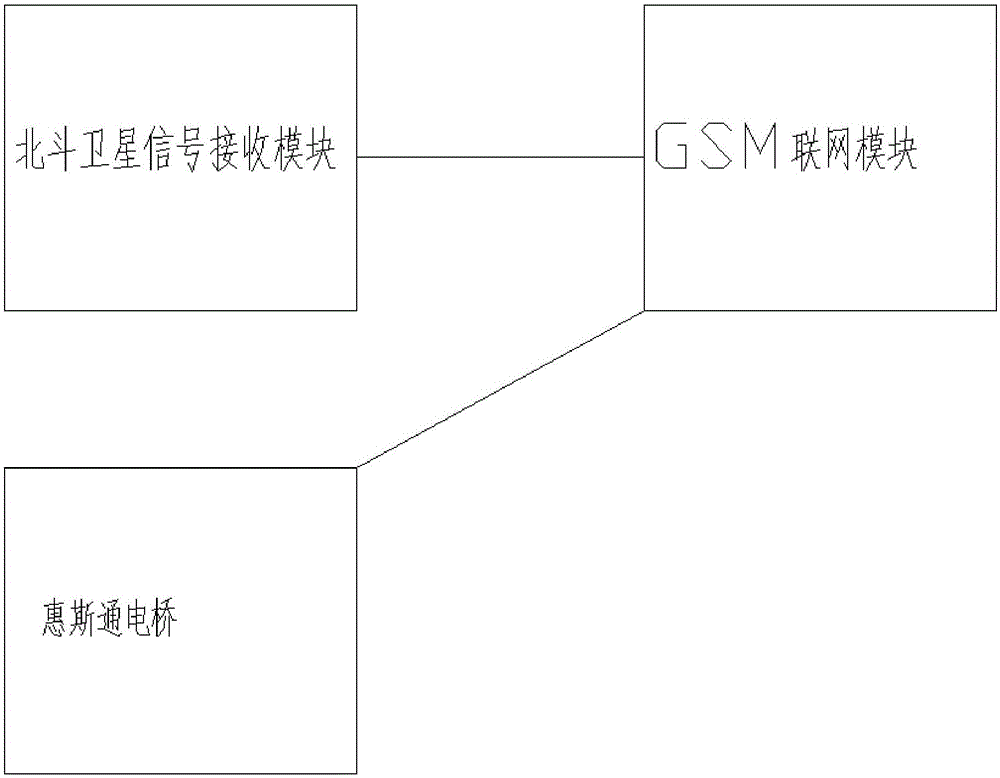
The invention relates to a Beidou-based intelligent draining pipe network detector which comprises a water flow detecting pipe connected with a draining pipe, wherein the water flow detecting pipe comprises a connecting pipe; a water blocking rod is arranged in the middle of the connecting pipe; the two ends of the water blocking rod are flexibly connected with the connecting pipe through sealing rings; a connecting hole is formed in the water-blocking rod; a strain rod is arranged in the connecting hole; the strain rod comprises a bar-shaped rubber rod; a resistance strain gage is arranged in the rubber rod; an annular pressurizing shell is arranged on the outer wall of the connecting pipe in a sleeving manner; a pressurizing chamber is formed between the pressurizing shell and the outer wall of the connecting pipe; a wheatstone bridge module, a Beidou satellite signal receiving module and a GSM internet module are arranged in the pressurizing chamber; the two ends of a loop of the resistance strain gage are connected with the wheatstone bridge module; a data output end of the wheatstone bridge module is connected with the GSM internet module; the Beidou satellite signal receiving module is connected with the GSM internet module.
Owner:江苏艾倍科科技股份有限公司
Wireless network engineering quality detection system and detection method
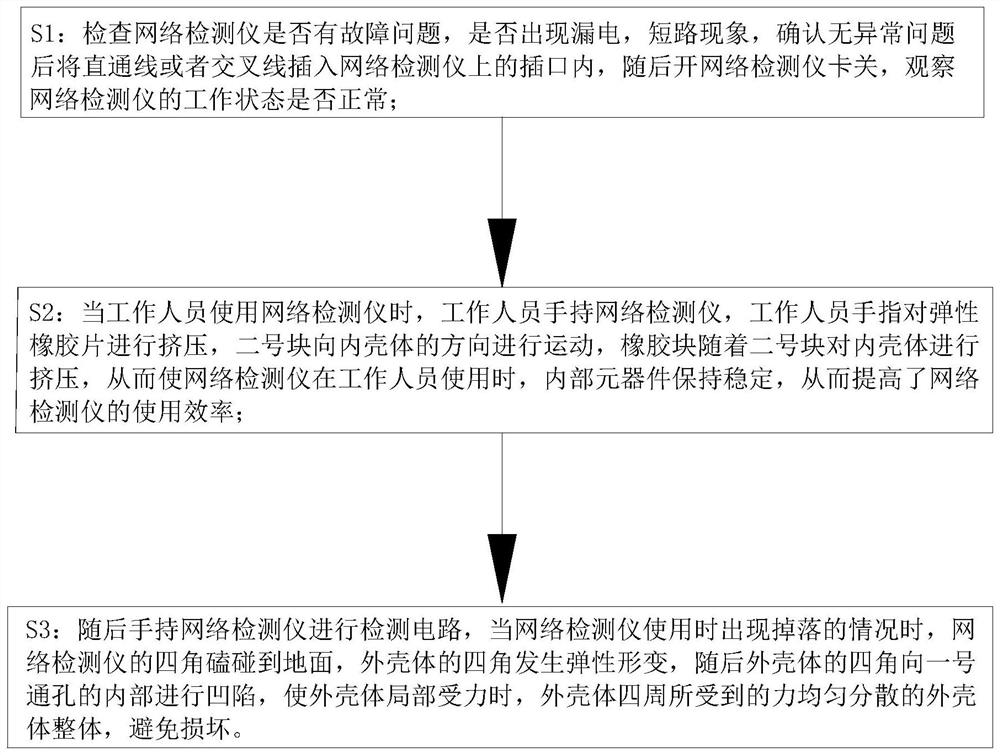
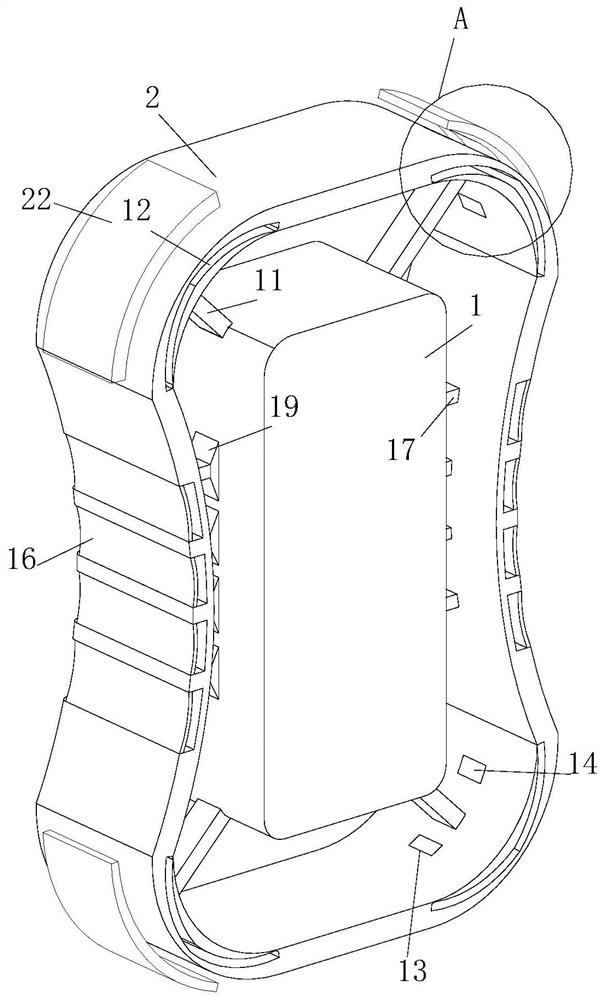
PendingCN113507330AAvoid damageImprove efficiencyWireless communicationPropogation channels monitoringNetwork detectorRubber elasticity
The invention relates to the technical field of network detection, in particular to a wireless network engineering quality detection system and method. The detection system comprises a network tester. The network tester comprises an inner shell, an outer shell, a rubber elastic sheet, a second block, a second groove and a third groove. When the network tester falls off from the air, the outer shell is in contact with the ground, the inner shell vibrates in the outer shell, and when the inner shell is in contact with the second block, the second block extrudes the elastic rubber sheet, so that force borne by the inner shell is transmitted to the outer shell through the second block, and damage to components in the inner shell is reduced; when a worker holds the network detector, fingers of the worker extrude an elastic rubber sheet, a second block moves towards the inner shell, and a rubber block extrudes the inner shell along with the second block, so that internal components are kept stable when the worker uses the network detector, and the use efficiency of the network detector is improved.
Owner:朱浩
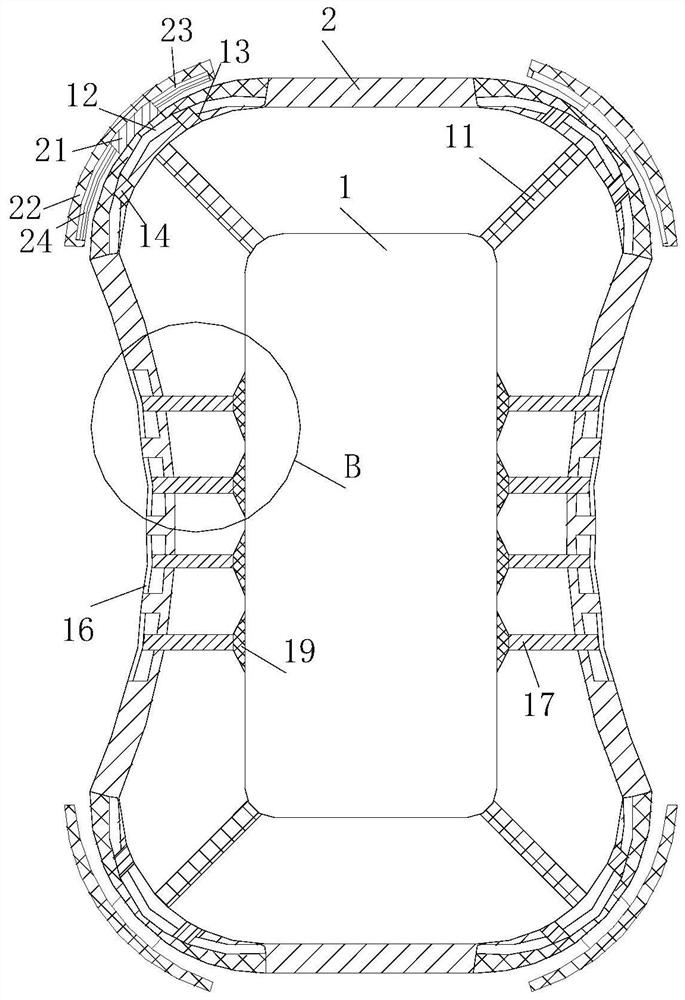
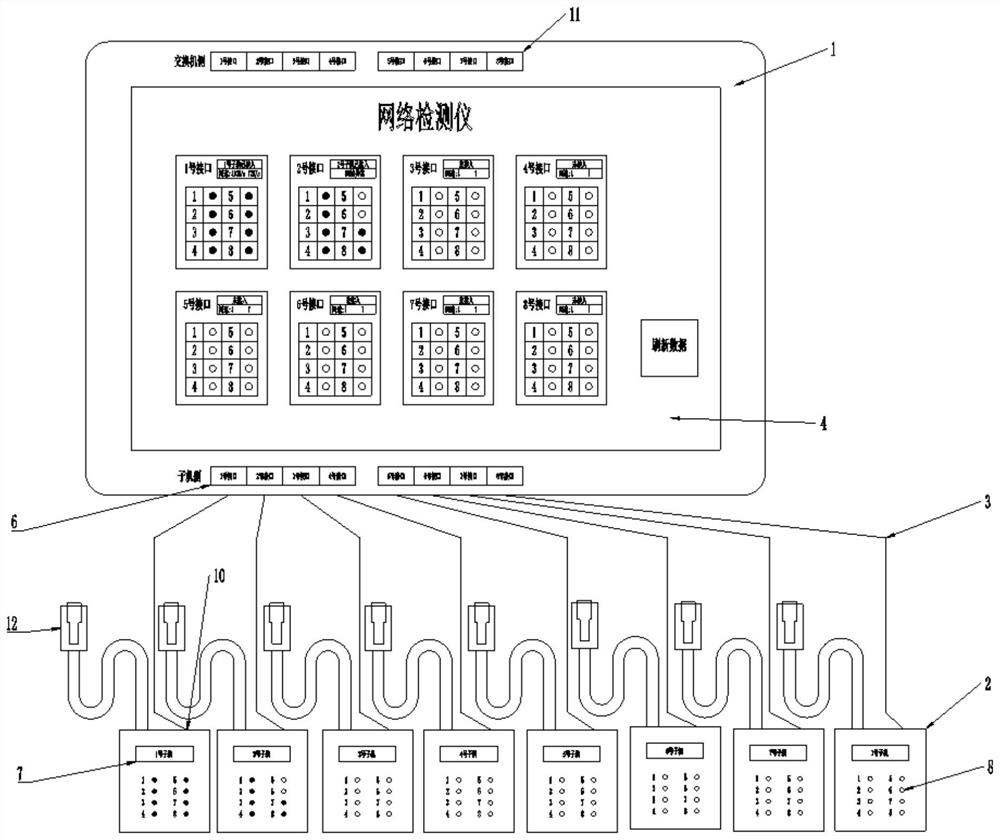
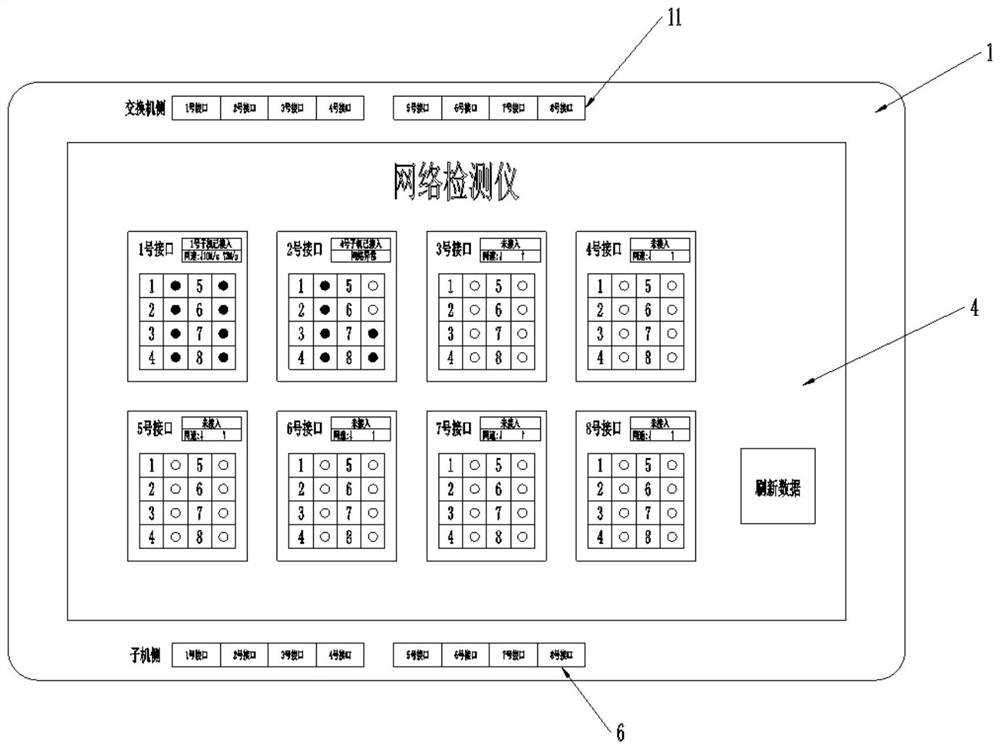
Network detector
PendingCN112468374ADetect continuityDoes not affect normal useData switching networksSelection arrangementsNetwork detectorStation
The invention relates to a network detector, which comprises a network monitor host and a plurality of network monitor submachines, wherein the network monitor host is connected with a port at one side of a switch of a to-be-detected network connection wire, and the network monitor sub-machine is connected with a port at one side of a computer terminal of the to-be-detected network connection wire; the plurality of network monitor sub-machines can transmit on-off signals and digital coding signals to the network monitor main machine through a to-be-detected network connection wire, and code recognition is performed on the network monitor main machine and the on-off condition is displayed. According to the invention, the on-off condition of network wiring between multiple stations and the switch can be rapidly detected, the detection efficiency is high, and time and labor are saved; and meanwhile, numbering and identification can be performed on to-be-detected network connection wires so that disordered network connection wires between the switch and the ports of the stations can be identified. In addition, the use of the computer terminal of each station is not influenced, and theEthernet running speed can be detected.
Owner:YUNNAN POWER GRID CO LTD KUNMING POWER SUPPLY BUREAU
Special network detector for relay protection
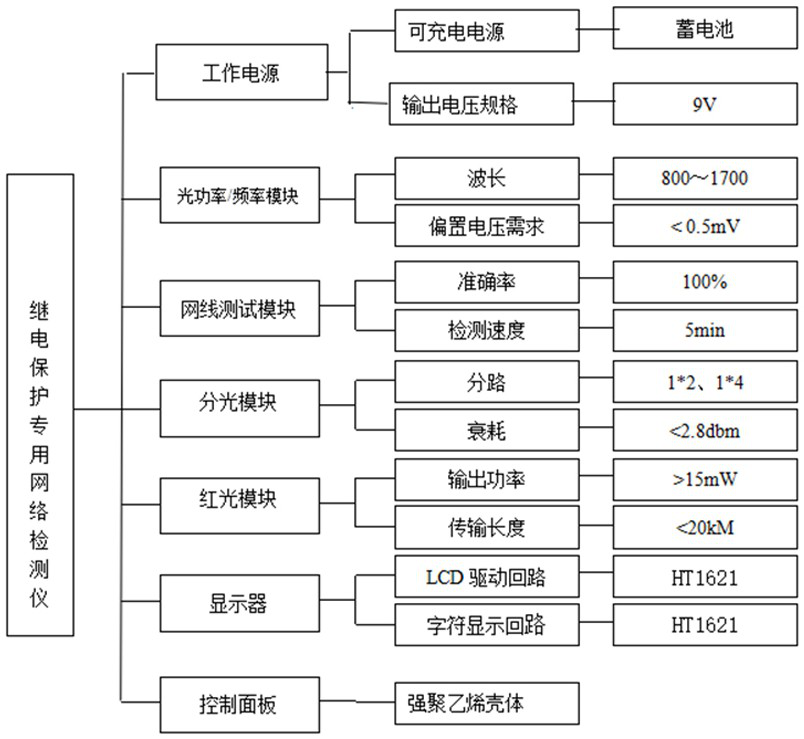
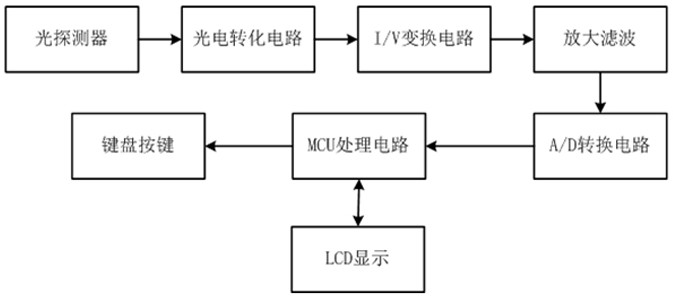
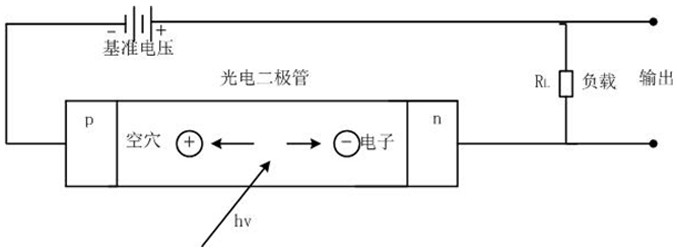
PendingCN113959680APowerfulSimple structureTesting fibre optics/optical waveguide devicesNetwork detectorDisplay device
The invention discloses a special network detector for relay protection, which belongs to the technical field of relay protection tools and structurally comprises a working power supply module, an optical power / frequency module, a network cable test module, a light splitting module, a red light module, a display and a control panel. The special network detector for relay protection has the advantages that the structure is simple, carrying is convenient, the functions of all network operation inspection tools are integrated, the possibility that all network operation inspection is achieved through a single tool is achieved, and the tool which is powerful in function, rapid and efficient is provided for relay protection network operation inspection work.
Owner:MAINTENANCE CO STATE GRID QINGHAI ELECTRIC POWER +2
Web browser security
InactiveUS20100036938A1Multiple digital computer combinationsPlatform integrity maintainanceNetwork detectorWeb browser
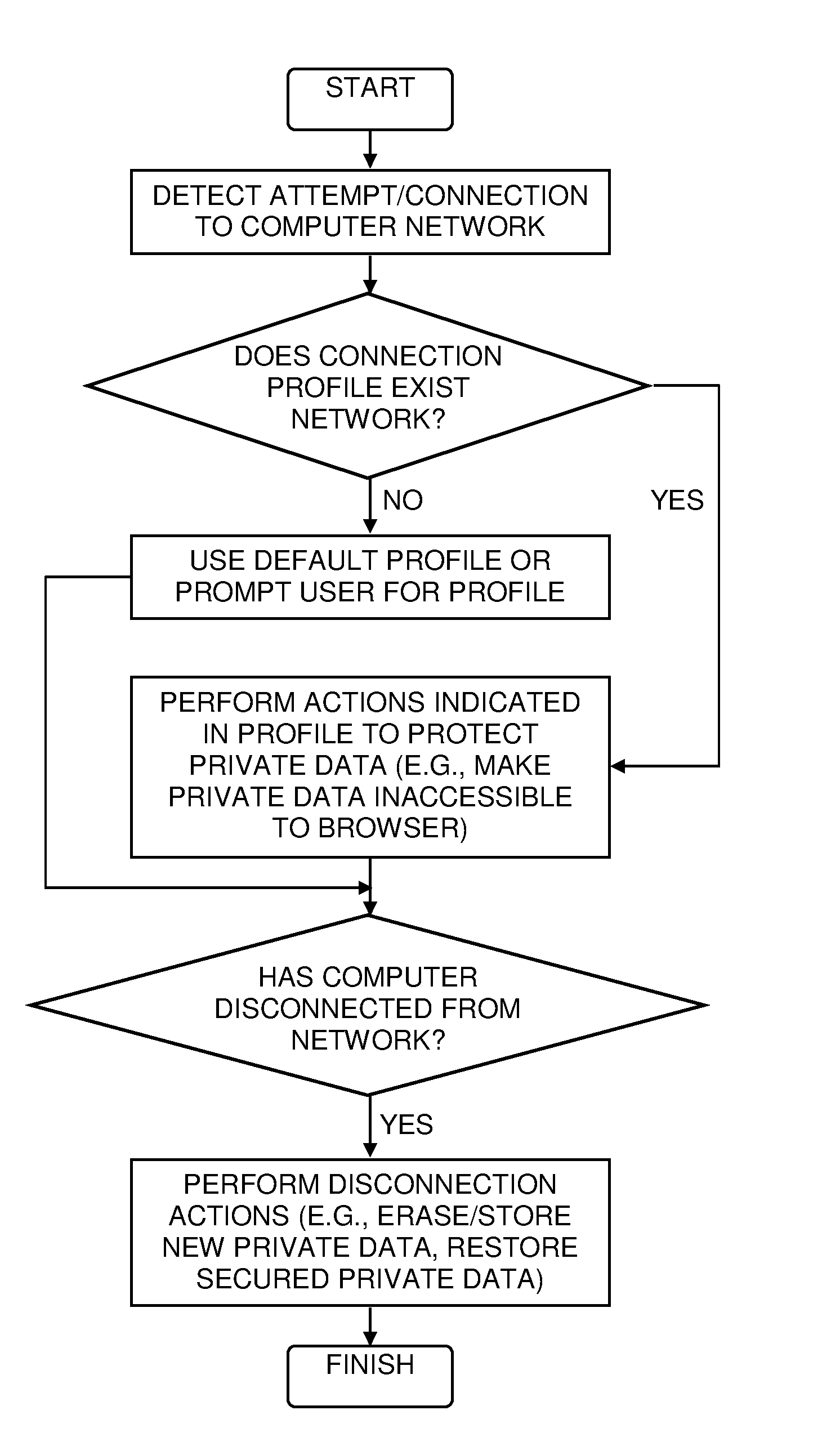
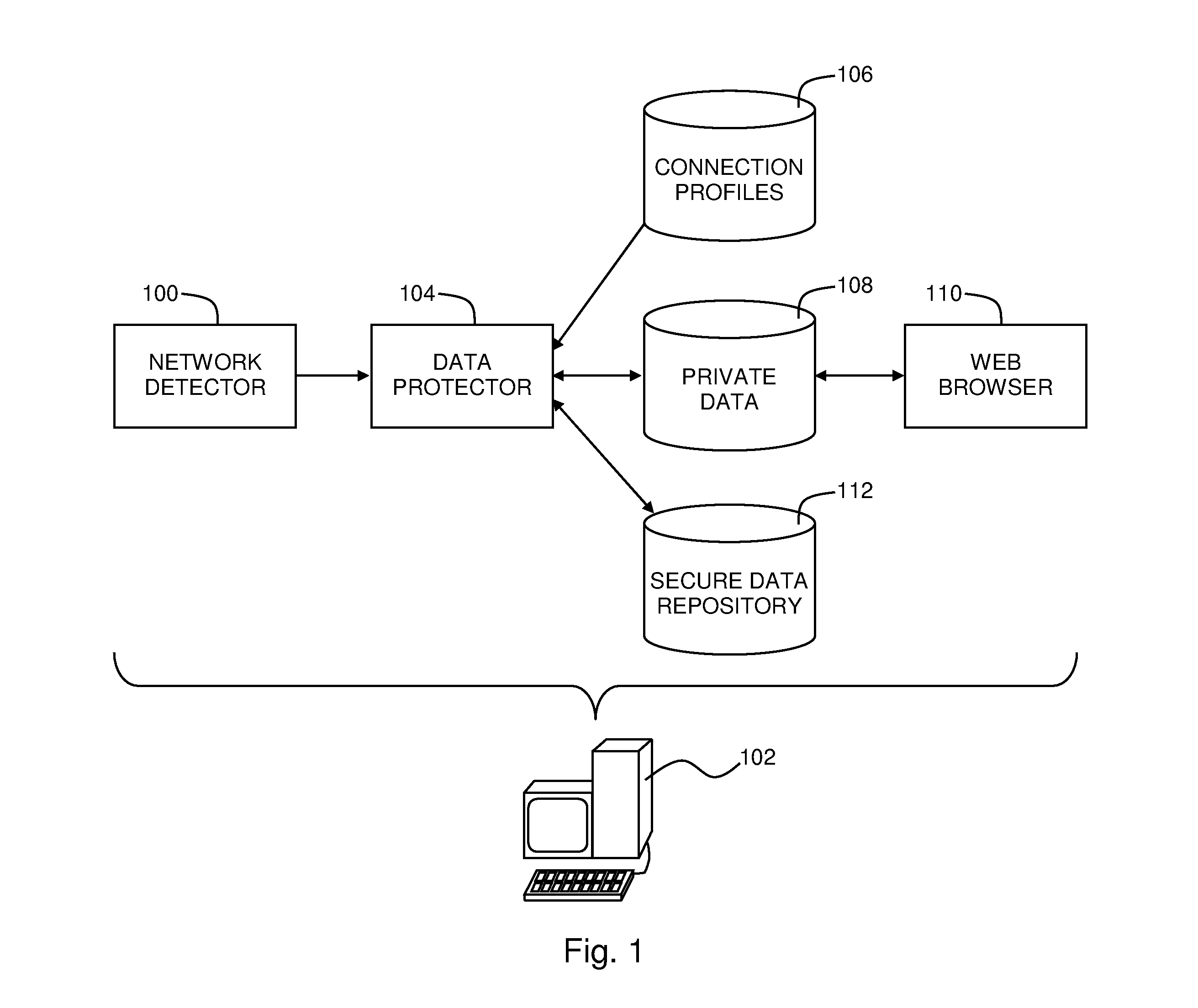
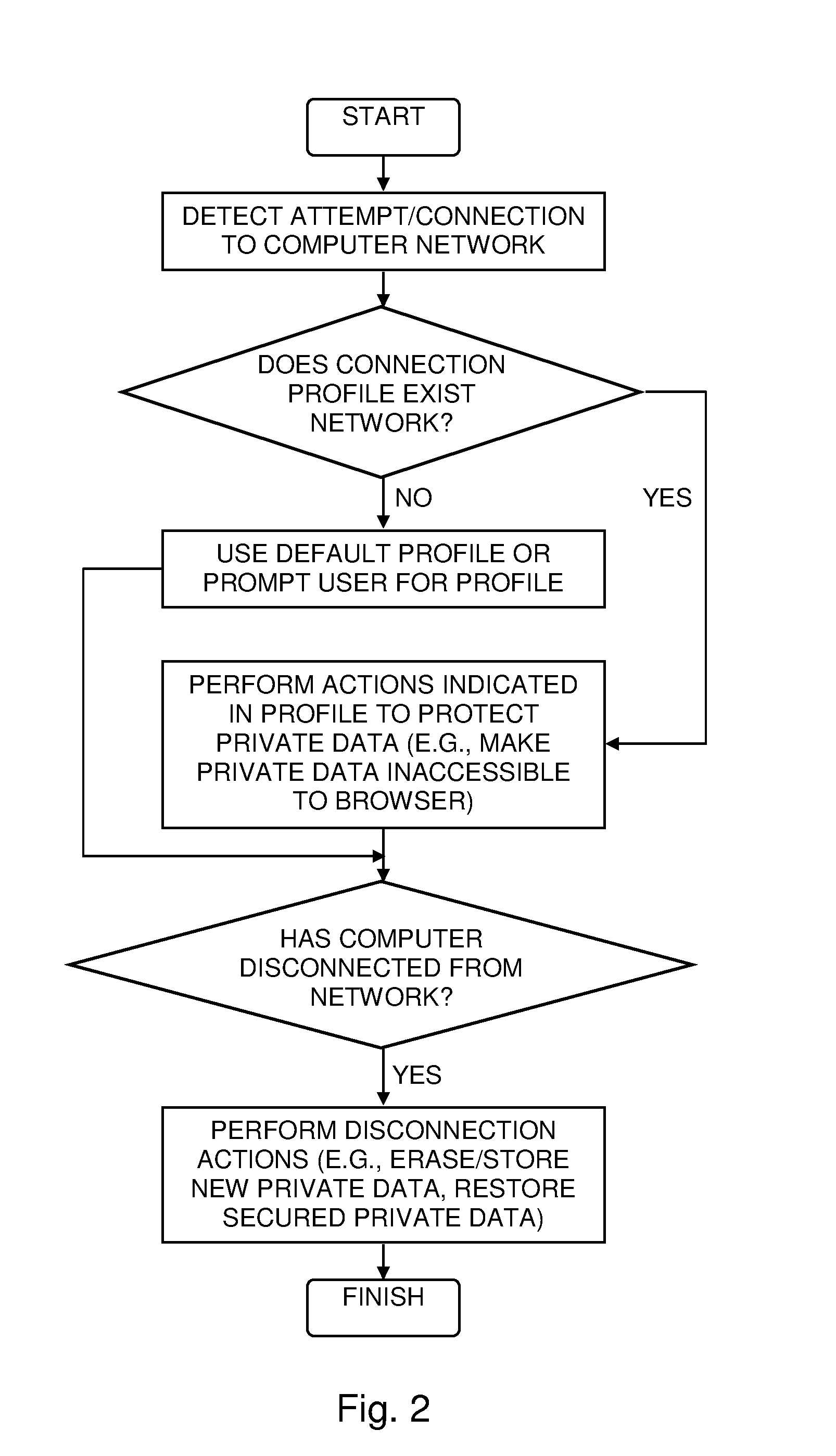
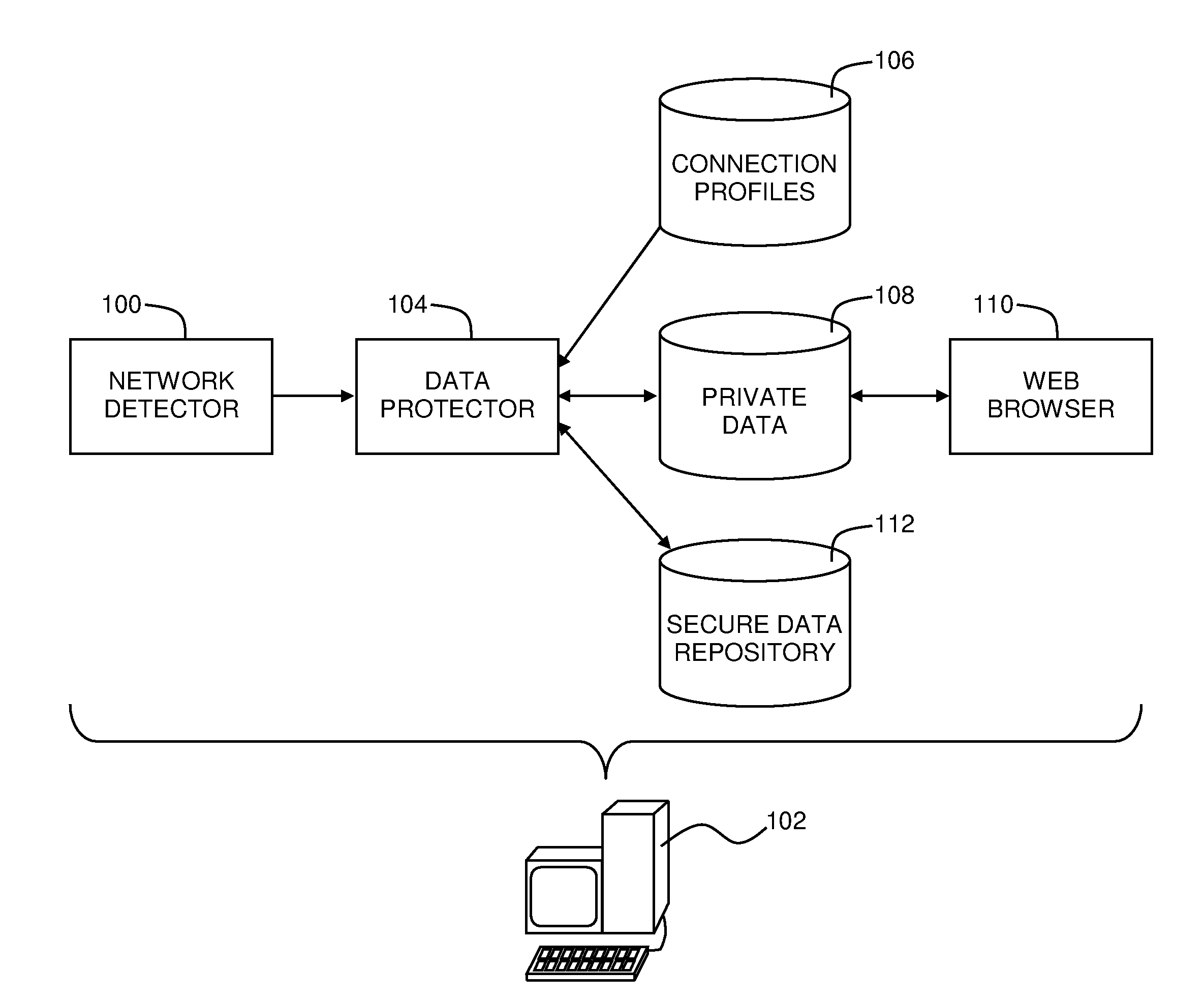
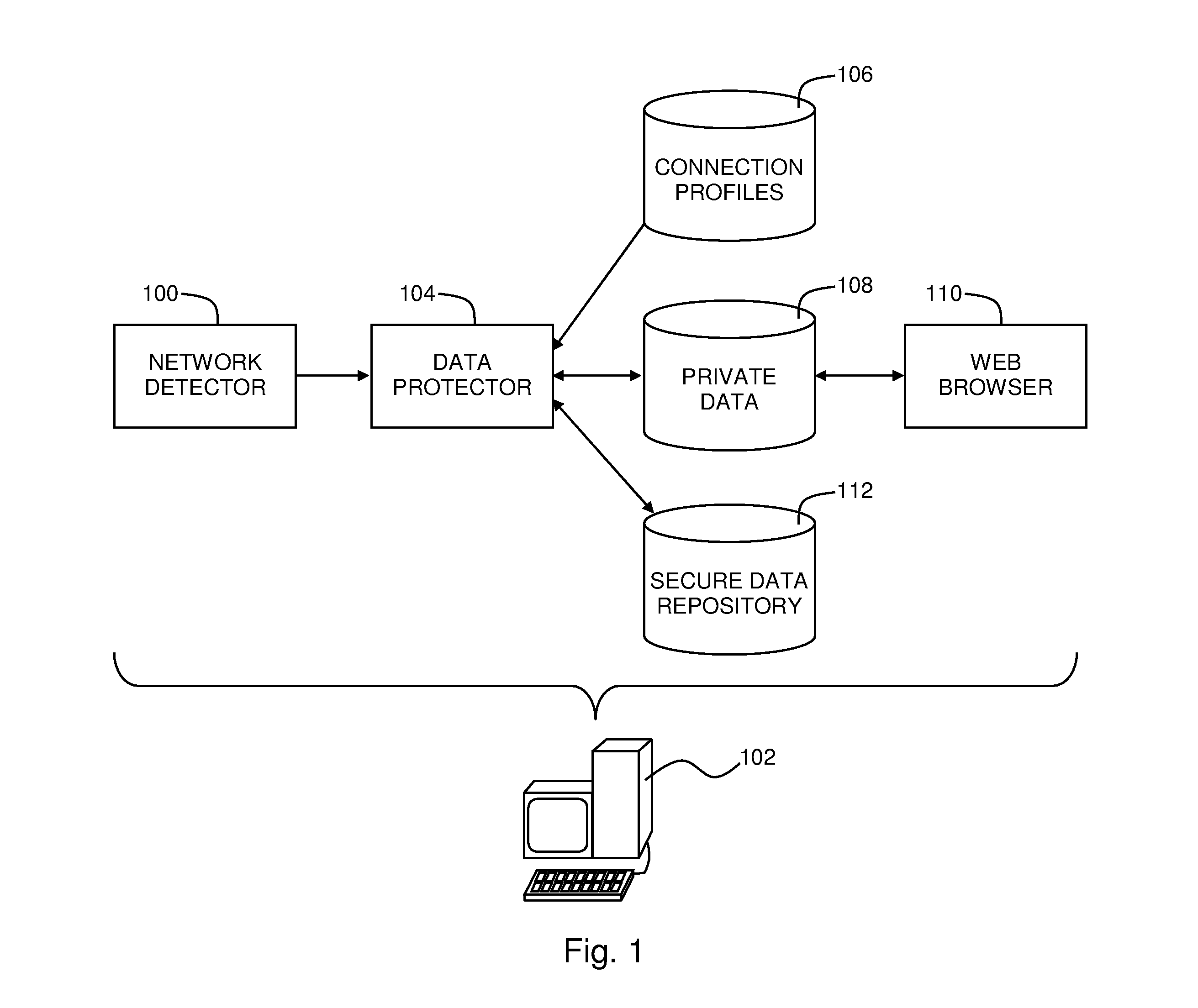
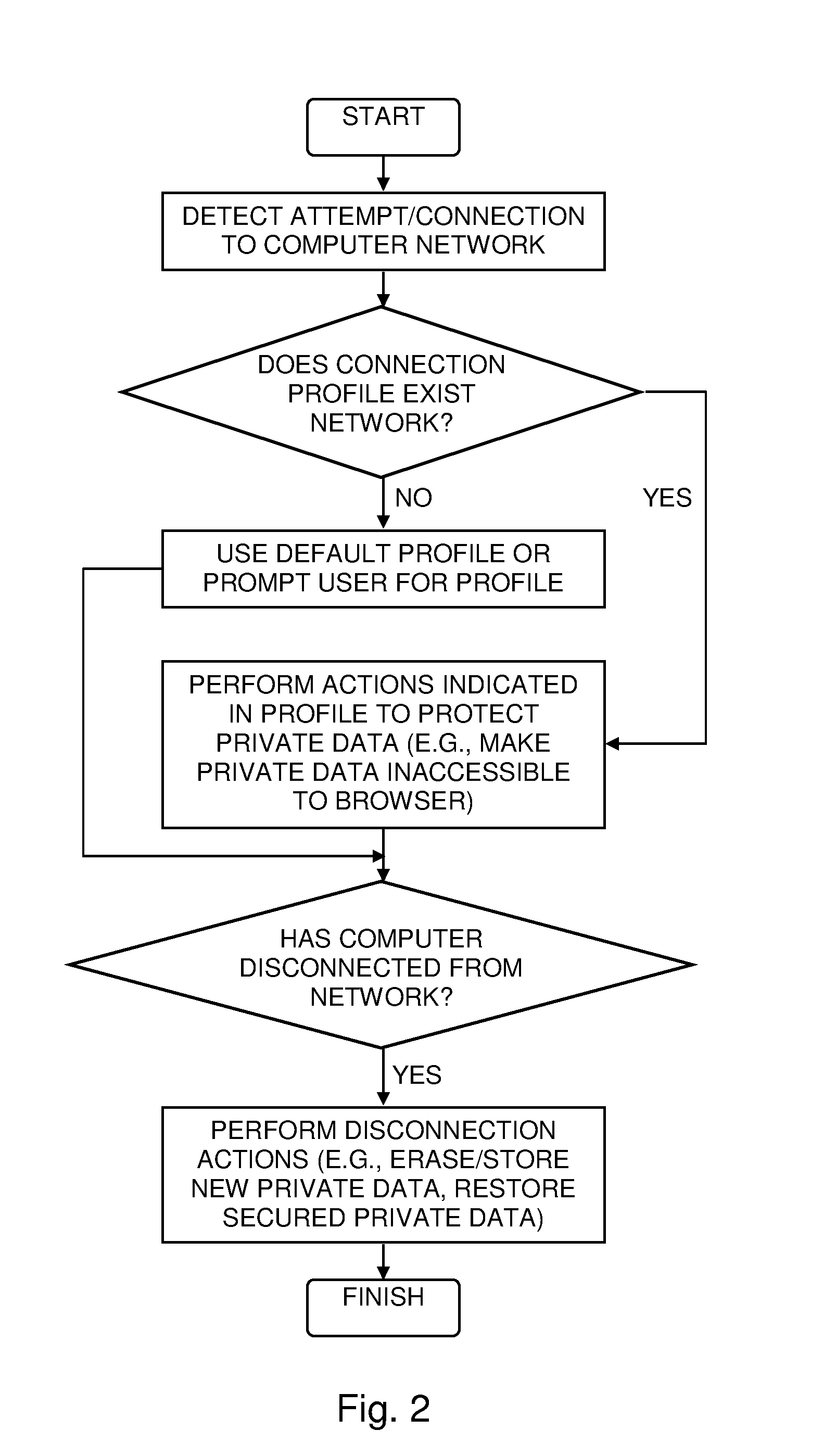
A web browser security system including a network detector configured to detect when a computer attempts to connect to a computer network, and a data protector configured to move any data predefined as being private data from any private data areas that are accessible to a web browser on the computer to a secure data repository that is not accessible to the web browser, where any of the network detector and the data protector are implemented in either of computer hardware and computer software and embodied in a computer-readable medium.
Owner:IBM CORP
Method for detecting network agent based on instant messaging software
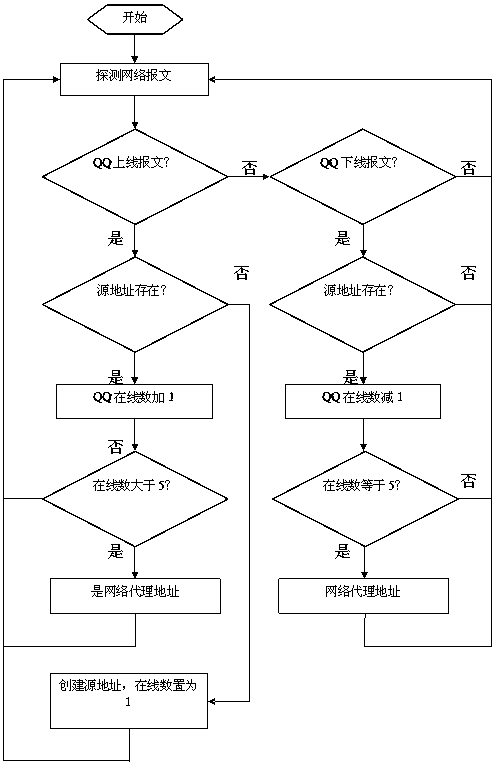
InactiveCN103401736AIncrease usageExtend online timeData switching networksNetwork detectorNetwork agent
The invention discloses a method for detecting a network agent based on instant messaging software. The method comprises the steps that a message of the instant messaging software is detected by a serial network detector in real time and the type of the message is judged; if the detected message is an on-line message or an off-line message, a source address of the on-line message or the off-line message of the instant messaging software is analyzed and acquired; the on-line number of the instant messaging software under the source address is recorded; and if the number of the instant messaging software under the source address is greater than a preset value, the source address is an address of the network agent. The instant messaging software is QQ messaging software. The method pays close attention to an application layer, so that modification of acting equipment in a network layer and a transmission layer is avoided, and the detection accuracy is ensured; and the detection misjudgment is corrected intelligently by the on-line and off-line feature detection of the instant messaging software, so that the detection timeliness and the accuracy are high.
Owner:SOUTHEAST UNIV
Monitoring instrument of vehicle control system CAN/LIN network and its test method
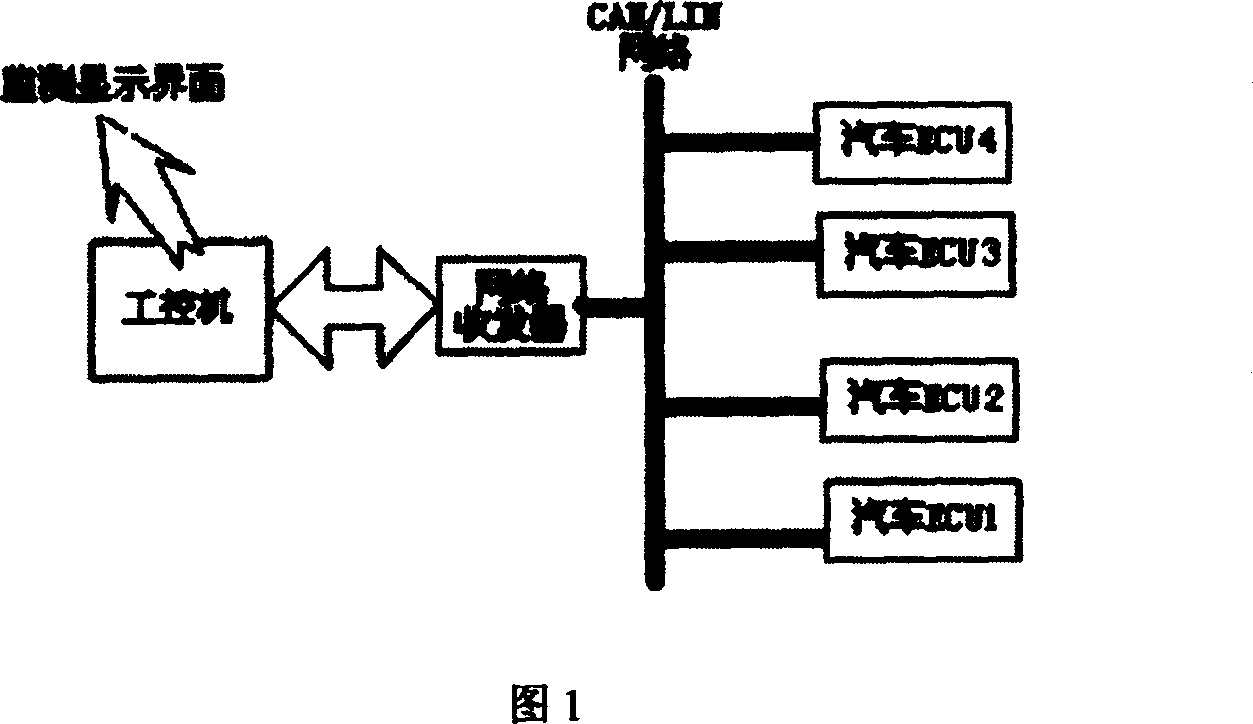
InactiveCN1304909CReal-time accurate node work efficiencyAccurate analysisElectric testing/monitoringData switching networksNetwork detectorTransceiver
A CAN / LIN network detector of vehicle control system is prepared as using industrial control computer to form detector, connecting CAN / LIN network transceiver to vehicle electric interface for collecting network message information and sending it to industrial control computer through serial bus interface or USB interface; applying modularization structure on industrial control computer to analyze node working efficiency, network node state, network load state and so on in real time accurately.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A load-independent method for detecting network abuse
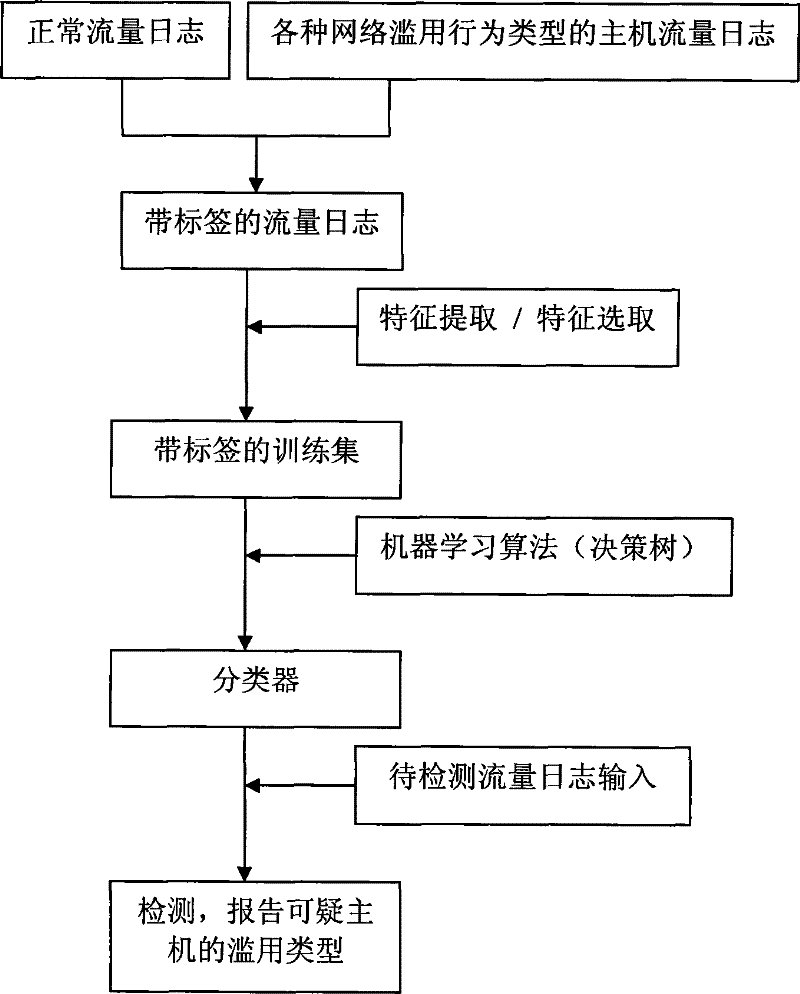
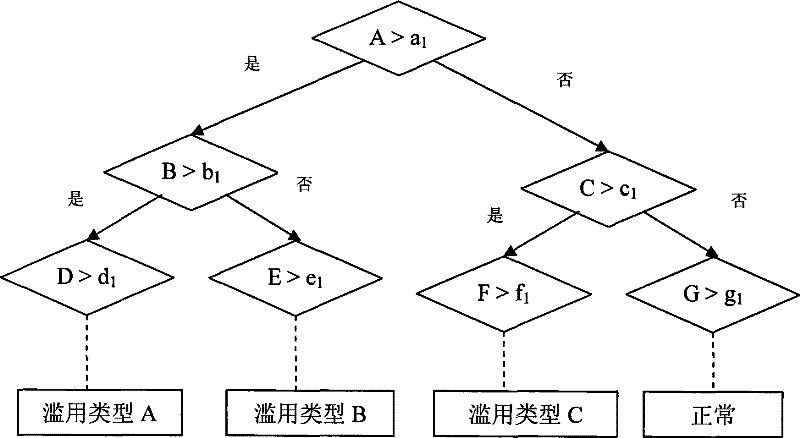
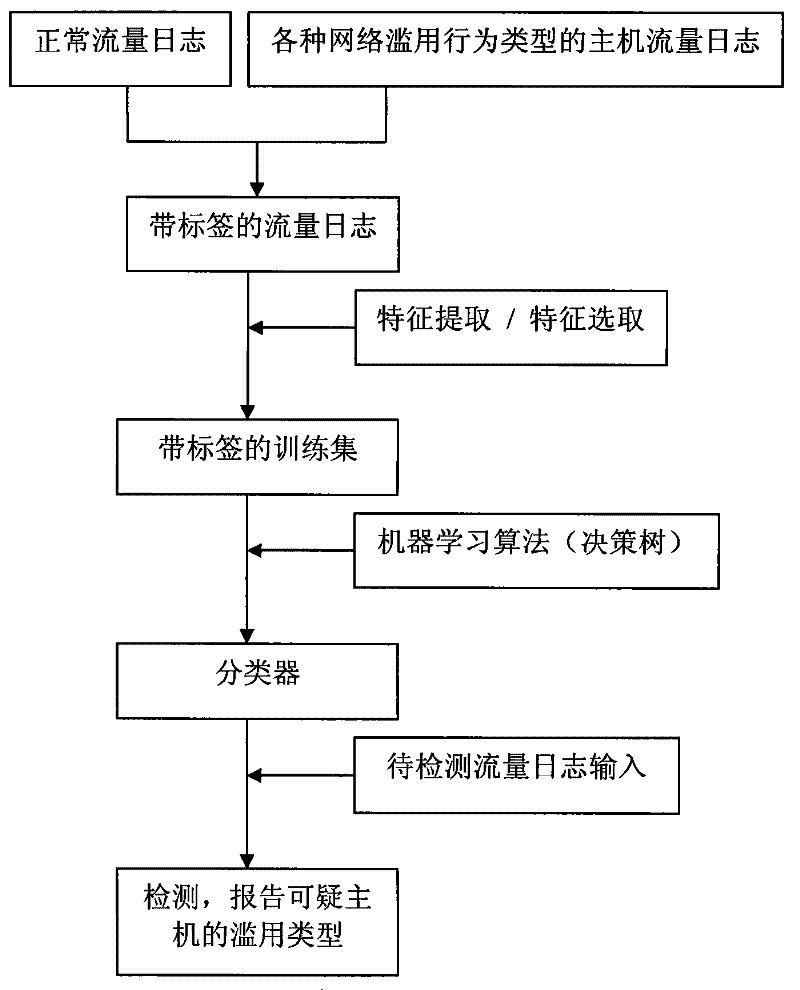
InactiveCN101267353BSmall amount of calculationSave computing resourcesData switching networksFeature vectorNetwork detector
The invention discloses a load-independent method for detecting network abuse, which belongs to the technical field of computer network and data communication. The method of the present invention is as follows: first collect the normal traffic log and the traffic log with network abuse behavior to form the traffic log information training set; extract the feature vector of the network abuse behavior from the traffic log information training set to form the feature vector set; then use the machine learning algorithm The feature vector set is learned to obtain the abuse detection classifier; finally, the network abuse detection classifier is arranged to detect the traffic log online and detect the network abuse. Compared with the prior art, the present invention has the advantages of small calculation amount, less calculation resource occupation, no influence of data encryption and legal problems of privacy infringement, and can timely and accurately discover network abuse.
Owner:PEKING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com