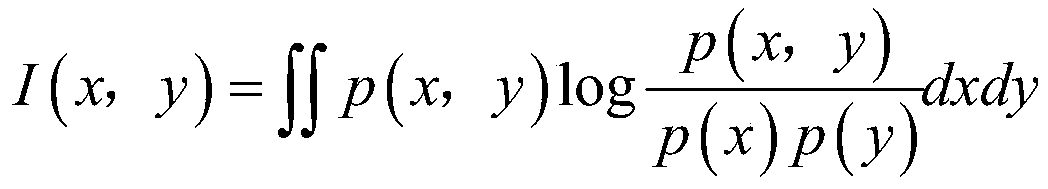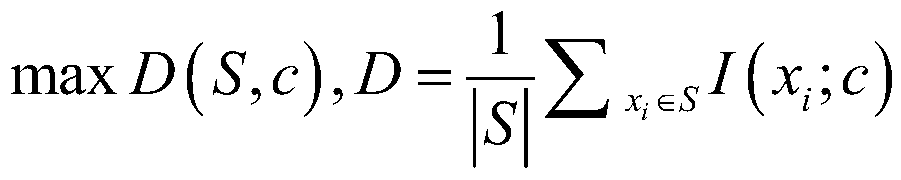Identity authentication method based on multi-behavior feature selection
A feature selection and identity authentication technology, applied in the field of information security, can solve the problems of legal users being wrongly judged as illegal users, poor identity authentication performance, poor classifier performance, etc., to achieve wide security and applicability, high accuracy, The effect of high hardware equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
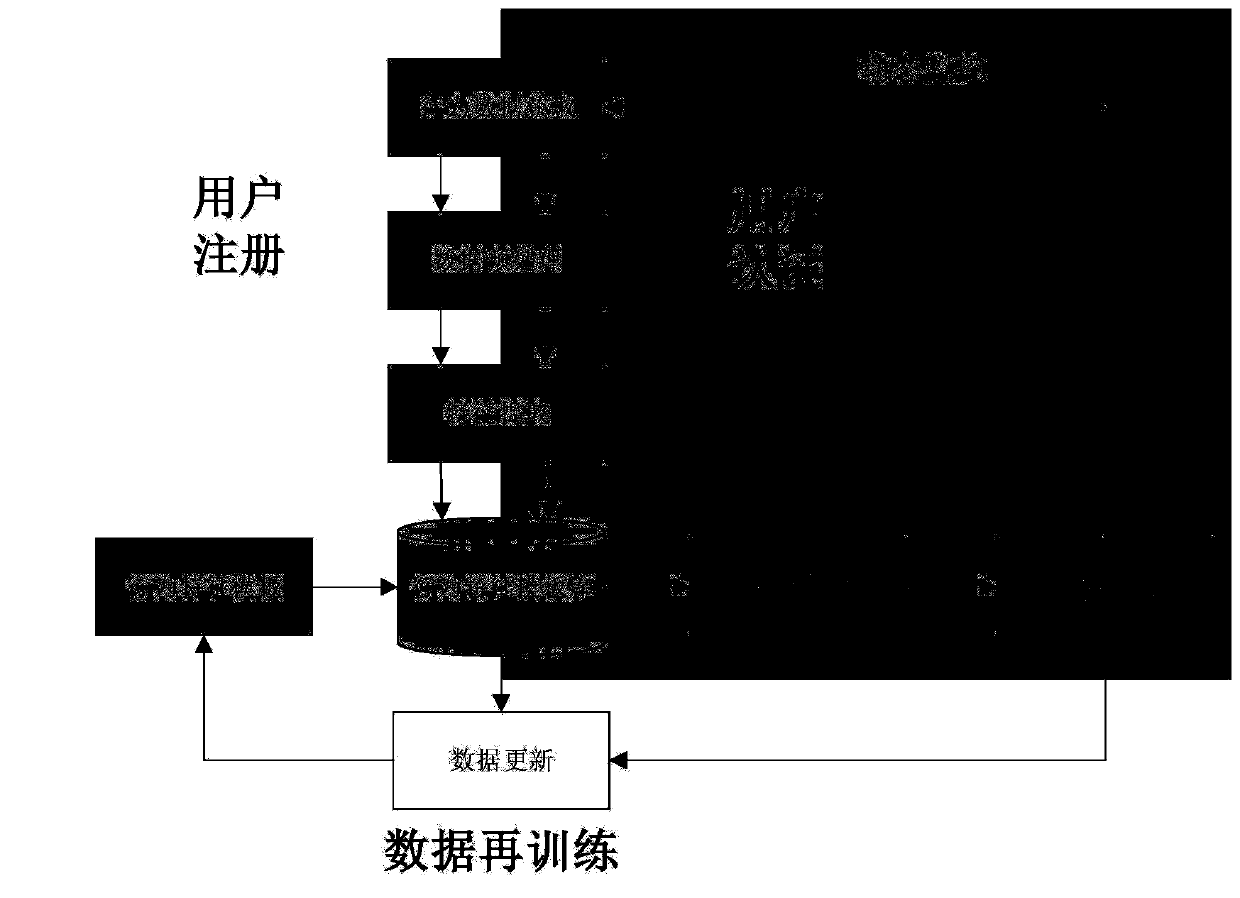
[0026] An identity authentication method and technical process based on multi-behavior feature selection are as follows: figure 1 As shown, the whole process includes three sub-processes: user registration, user authentication, and data retraining. In the user registration stage, the user operates the keyboard and mouse according to the prompt operation of the small game designed by the system. This process mainly extracts the user's keyboard behavior and mouse behavior, and the physical address and IP address of the device information are obtained through some software. As for some habits of the user The behavior does not exist during the registration phase, but is obtained after logging in to the system for a period of time. This process of collecting data is hidden from the user. After collecting the behavioral data, preprocess the data to get rid ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com