Networked numerical control system man-in-the-middle attack detection method based on Gaussian radial basis function classifier
A Gaussian radial basis, numerical control system technology, applied in transmission systems, instruments, characters and pattern recognition, etc., can solve the problems of lack, time lag, no safety management system, etc., to achieve easy implementation, simple theoretical framework, The effect of good generalization ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
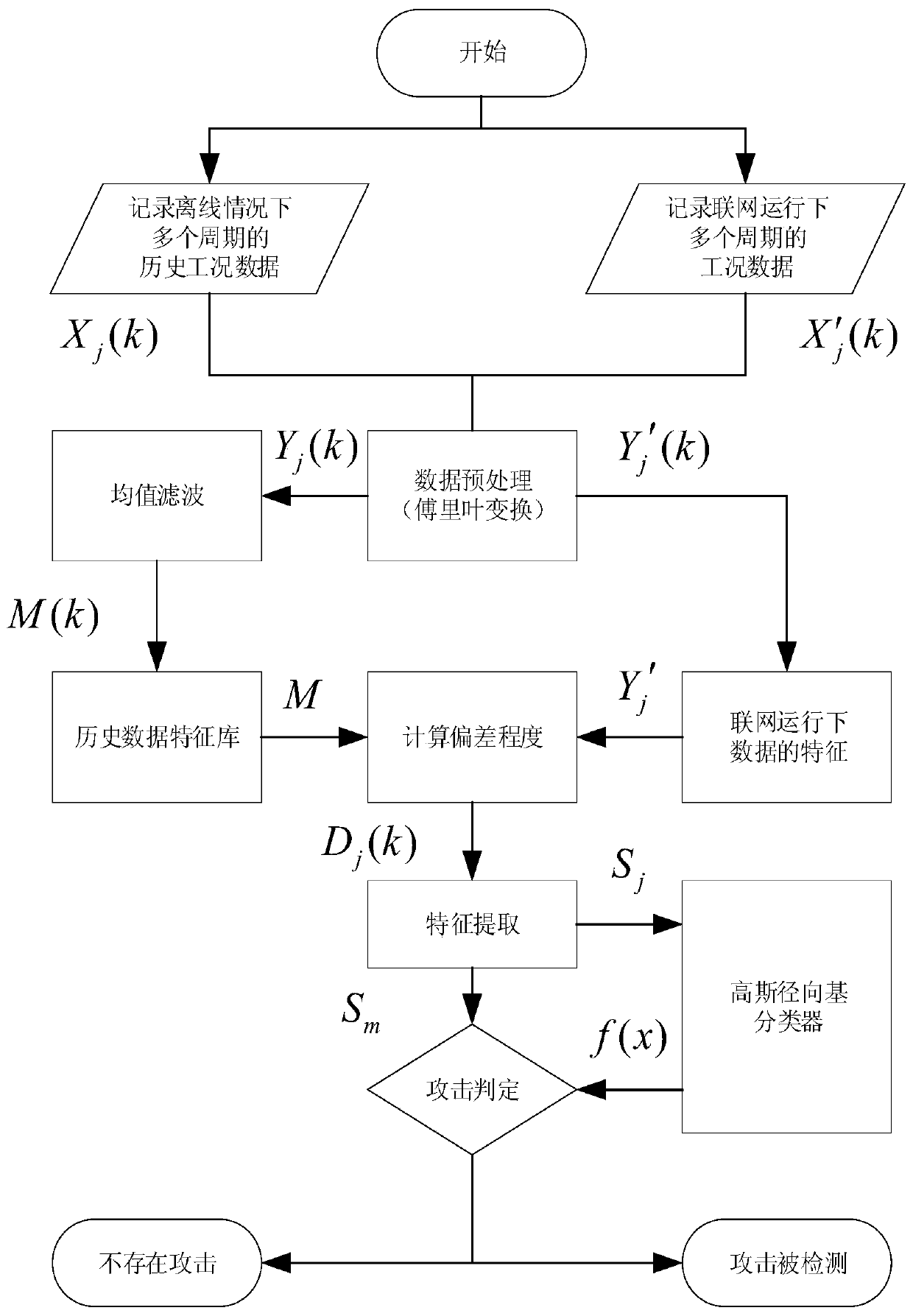
[0046] In order to make the technical solutions and design ideas of the present invention clearer, a detailed description will be given below in conjunction with the accompanying drawings.
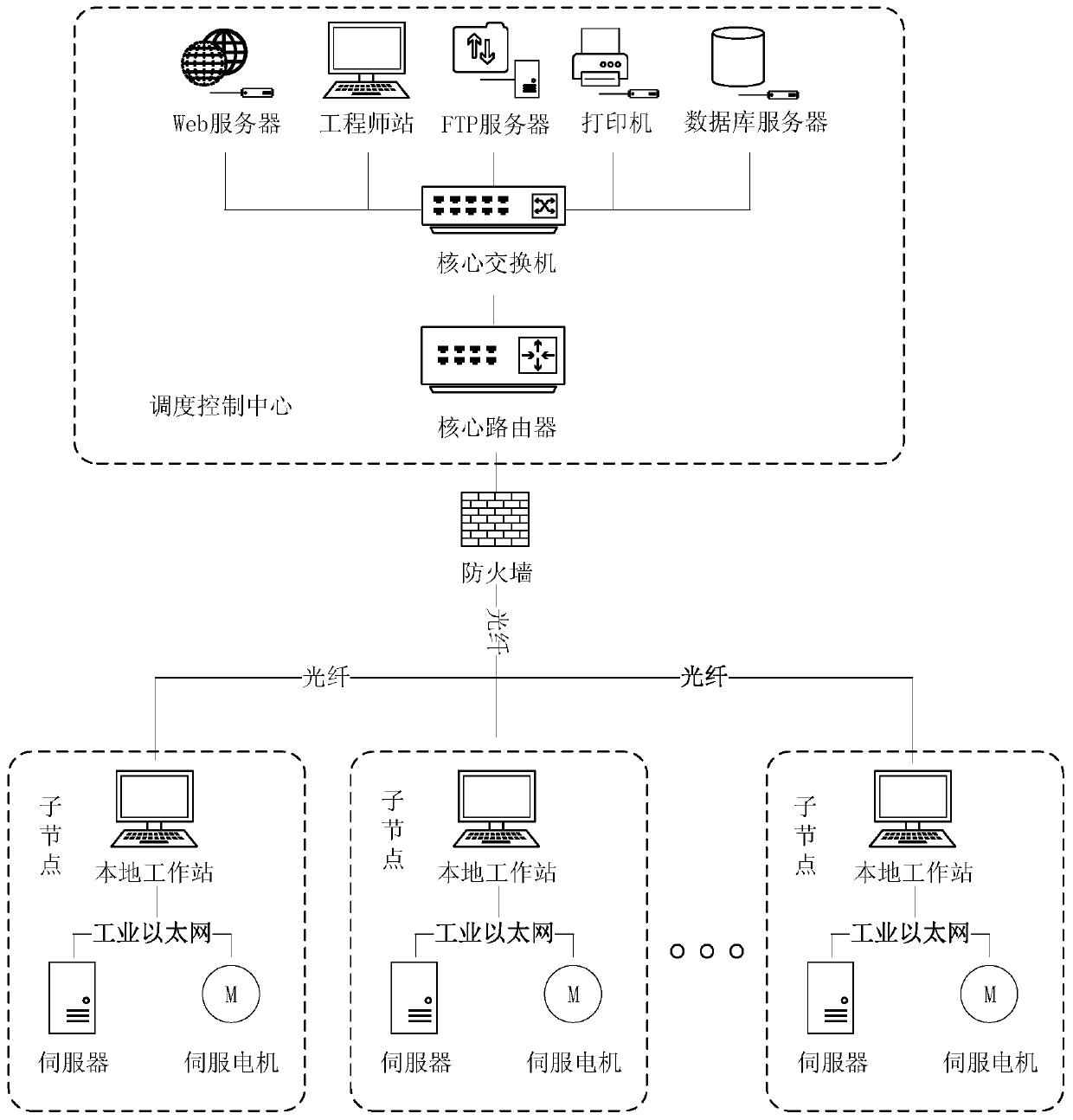
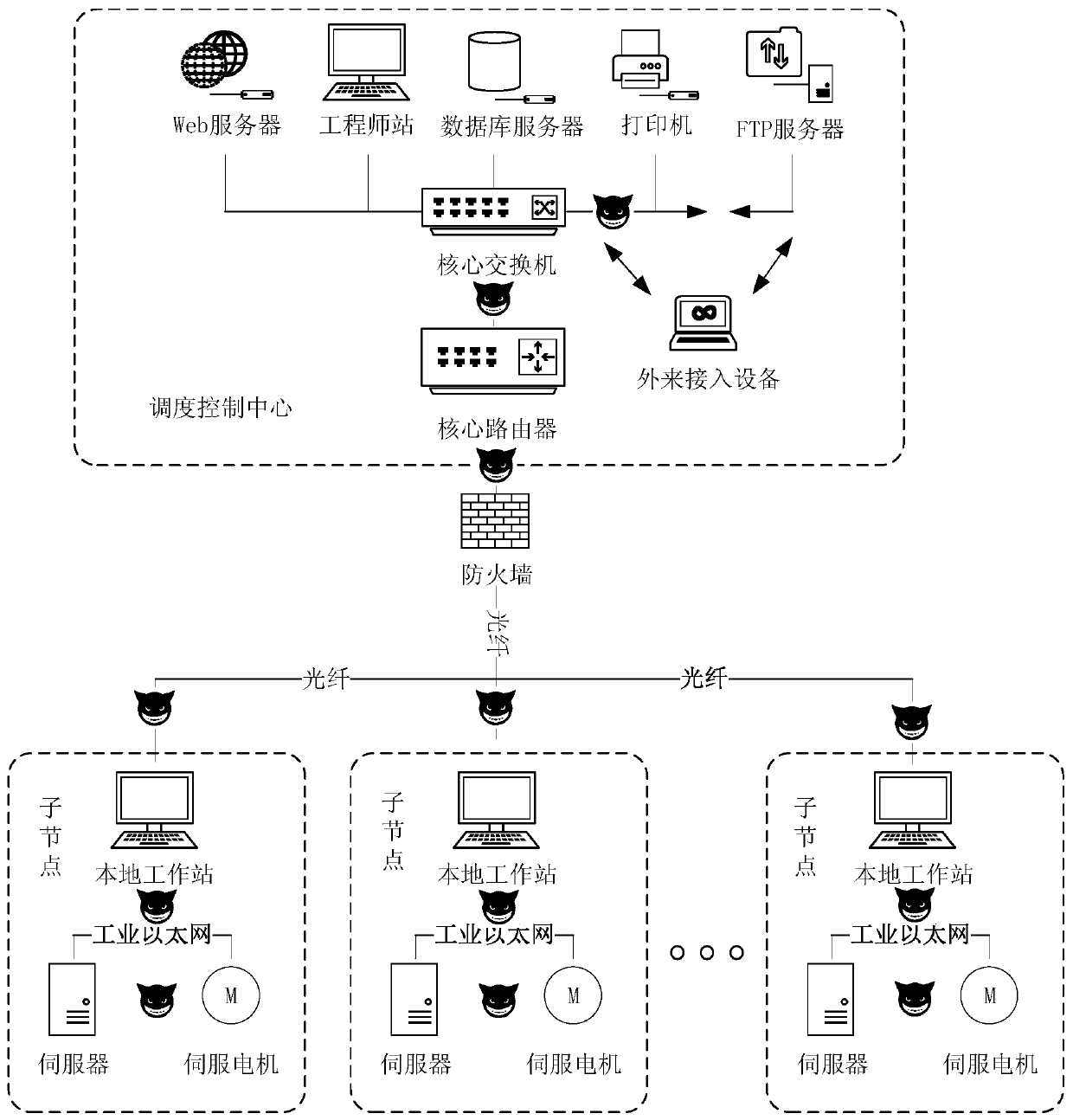
[0047] refer to figure 1, most of the existing networked CNC systems can be divided into three parts: dispatch control center, IT security detection and protection part, and industrial site. There are many ways to realize NC technology at present, but the present invention only considers the networked numerical control system which realizes the management and control of numerical control program with the FTP file transfer protocol as the core. Under normal working conditions, the FTP protocol will send the NC program to each sub-node of the industrial site in the form of a file, and the local workstation in the sub-node will execute the program, and finally respond to the normal operation of the server and servo motor. However, the traditional FTP protocol has a large number of potential ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com